You can organize Liberty servers into collectives to support
clustering, administration, and other operations that act on multiple
Liberty servers at a time in order to efficiently and accurately deliver
application services to your organization.
Before you begin
The collectiveController-1.0 feature
and its capabilities are available only in WebSphere® Application Server Liberty Network
Deployment and WebSphere Application
Server Liberty for z/OS®.  The feature is not available in WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express®, or WebSphere Application Server
Liberty Core. If you have a WebSphere Application
Server Liberty Network Deployment installation, you can use its collectiveController-1.0 feature
to work with collective members from WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express, or WebSphere Application Server
Liberty Core installations.
The feature is not available in WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express®, or WebSphere Application Server
Liberty Core. If you have a WebSphere Application
Server Liberty Network Deployment installation, you can use its collectiveController-1.0 feature
to work with collective members from WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express, or WebSphere Application Server
Liberty Core installations.
About this task
A Liberty collective is a set of Liberty servers that
are configured as part of the same administrative and operational
domain.
Configuration and state data about a Liberty collective
is housed in an active operational repository.
Membership in
a Liberty collective is optional. Liberty servers join a collective
by registering with a collective controller to become members. Members
share information about themselves through the operational repository
of the controller.
The following rules apply:
- A Liberty server can be a member of only one collective.
- Different Liberty servers on the same host can be in different
collectives.
- Liberty servers on the same host that are members of a collective
can coexist with Liberty servers that are not members of a collective.
Procedure
- Create and configure your controller.
- Create a server to act as the collective controller.
bin\server create myController
- Create the collective configuration.
This
consists primarily of the administrative domain security configuration
used for secure communication between controllers and members.
bin\collective create myController --keystorePassword=controllerKSPassword
- Update the server.xml file.
- Copy output from the collective command and paste it into the server.xml file.
- Add a user registry and an administrative user (for the join operation).
In
$WLP_INSTALL_DIR/usr/servers/myController/server.xml for
example:
<server description="controller server">
<!-- Enable features -->
<featureManager>
<feature>jsp-2.2</feature>
</featureManager>
<httpEndpoint id="defaultHttpEndpoint"
host="*"
httpPort="9080"
httpsPort="9443" />
<featureManager>
<feature>collectiveController-1.0</feature>
</featureManager>
<!-- Define the host name for use by the collective.
If the host name needs to be changed, the server should be
removed from the collective and re-joined or re-replicated. -->
<variable name="defaultHostName" value="controllerHostname" />
<!-- TODO: Set the security configuration for Administrative access -->
<quickStartSecurity userName="adminUser" userPassword="adminPassword" />
<!-- clientAuthenticationSupported set to enable bidirectional trust -->
<ssl id="defaultSSLConfig"
keyStoreRef="defaultKeyStore"
trustStoreRef="defaultTrustStore"
clientAuthenticationSupported="true" />
<!-- inbound (HTTPS) keystore -->
<keyStore id="defaultKeyStore" password="yourPassword"
location="${server.config.dir}/resources/security/key.jks" />
<!-- inbound (HTTPS) truststore -->
<keyStore id="defaultTrustStore" password="yourPassword"
location="${server.config.dir}/resources/security/trust.jks" />
<!-- server identity keystore -->
<keyStore id="serverIdentity" password="yourPassword"
location="${server.config.dir}/resources/collective/serverIdentity.jks" />
<!-- collective trust keystore -->
<keyStore id="collectiveTrust" password="yourPassword"
location="${server.config.dir}/resources/collective/collectiveTrust.jks" />
<!-- collective root signers keystore -->
<keyStore id="collectiveRootKeys" password="yourPassword"
location="${server.config.dir}/resources/collective/rootKeys.jks" />
</server>
- Start the server.
bin\server start myController
Figure 1. Collective of one
- Create and configure a member.
The controller
and members can be on separate hosts. In this example, the controller
and member are on the same host.
- Create a member server.
bin\server create myMember
- Join the member.
The join operation requires
a network connection to the collective controller and an administrative
user ID and password for performing MBean operations on the controller.
bin\collective join myMember --host=controllerHostname --port=9443 --user=adminUser --password=adminPassword --keystorePassword=memberKSPassword
Note: The --keystorePassword value
can be different for each server that is joined to the collective.
Refer
to Overriding Liberty server host information for
the information that you must provide so that the collective controller
can establish a connection to the server.
- Update the server.xml file.
- Copy output from the collective command and paste it into the server.xml file.
- Modify the ports so that the server can open its HTTP ports.
In
$WLP_INSTALL_DIR/usr/servers/myMember/server.xml for
example:
<server description="member server">
<!-- Enable features -->
<featureManager>
<feature>jsp-2.2</feature>
</featureManager>
<httpEndpoint id="defaultHttpEndpoint"
host="*"
httpPort="9081"
httpsPort="9444" />
<featureManager>
<feature>collectiveMember-1.0</feature>
</featureManager>
<!-- Define the host name for use by the collective.
If the host name needs to be changed, the server should be
removed from the collective and re-joined or re-replicated. -->
<variable name="defaultHostName" value="memberHostname" />
<!-- Connection to the collective controller -->
<collectiveMember controllerHost="localhost"
controllerPort="9443" />
<!-- clientAuthenticationSupported set to enable bidirectional trust -->
<ssl id="defaultSSLConfig"
keyStoreRef="defaultKeyStore"
trustStoreRef="defaultTrustStore"
clientAuthenticationSupported="true" />
<!-- inbound (HTTPS) keystore -->
<keyStore id="defaultKeyStore" password="yourPassword"
location="${server.config.dir}/resources/security/key.jks" />
<!-- inbound (HTTPS) truststore -->
<keyStore id="defaultTrustStore" password="yourPassword"
location="${server.config.dir}/resources/security/trust.jks" />
<!-- server identity keystore -->
<keyStore id="serverIdentity" password="yourPassword"
location="${server.config.dir}/resources/collective/serverIdentity.jks" />
<!-- collective truststore -->
<keyStore id="collectiveTrust" password="yourPassword"
location="${server.config.dir}/resources/collective/collectiveTrust.jks" />
</server>
- Start the member.
bin\server start myMember
Figure 2. Simple collective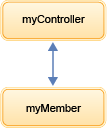
Results
You should see the member publish to the controller. The
messages.log file
should look like this example:
[1/31/13 11:17:47:699 CST] 0000002e nt.repository.member.internal.publisher.ServerPathsPublisher I CWWKX8114I:
The server's paths have been successfully published to the management repository.
[1/31/13 11:17:47:711 CST] 0000002f nt.repository.member.internal.publisher.ServerStatePublisher I CWWKX8116I:
The server STARTED state has been successfully published to the management repository.
[1/31/13 11:17:47:737 CST] 00000028 pository.member.internal.publisher.ServerManagementPublisher I CWWKX8112I:
The server's host information has been successfully published to the management repository.
 The feature is not available in WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express®, or WebSphere Application Server
Liberty Core. If you have a WebSphere Application
Server Liberty Network Deployment installation, you can use its collectiveController-1.0 feature
to work with collective members from WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express, or WebSphere Application Server
Liberty Core installations.
The feature is not available in WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express®, or WebSphere Application Server
Liberty Core. If you have a WebSphere Application
Server Liberty Network Deployment installation, you can use its collectiveController-1.0 feature
to work with collective members from WebSphere Application Server Liberty, WebSphere Application Server
Liberty - Express, or WebSphere Application Server
Liberty Core installations.

 Task topic
Task topic