Secure by design, smarter with AI

Key takeaways
- AI has changed the nature of intrusion—making secure-by-design (SbD) principles essential.
Attacks now move, hide, and learn at machine speed, and 91% of security executives say defending against them requires fusing architecture, operations, and culture into a unified design. - Most leaders believe in secure by design — but few practice it at scale.
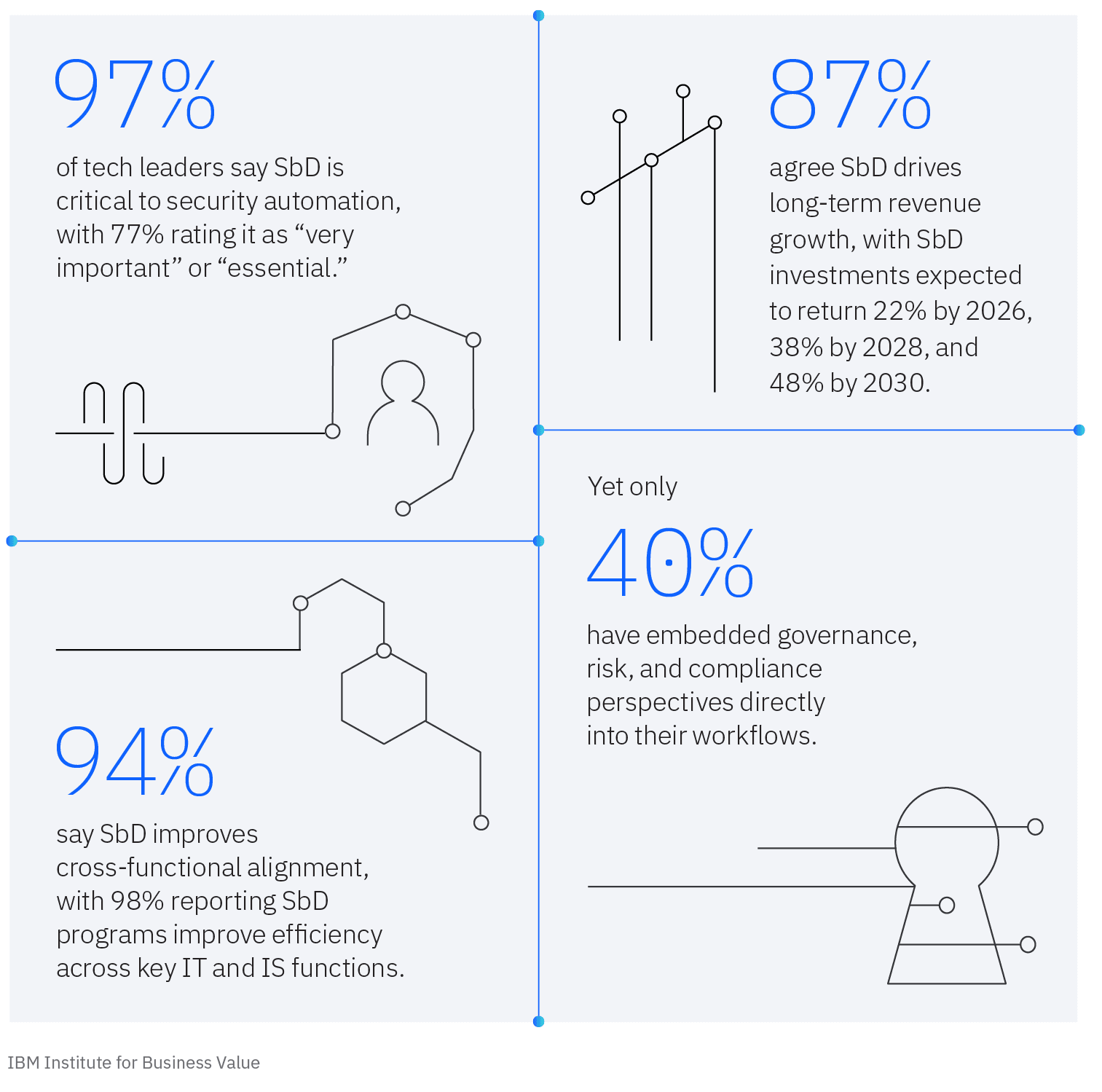
While 97% of tech leaders call SbD critical and 87% link it to long term revenue growth, only 40% have embedded governance, risk, and compliance directly into innovation workflows — leaving a gap between aspiration and execution. - Combining secure by design with AI delivers measurable performance gains.
Enterprises deploying both report faster response times, stronger cross functional alignment, and efficiency improvements of up to 25%—proving that AI can turn SbD from static policy into an adaptive, real time defense.
Introduction
As AI transforms attacks, defense starts at design
AI has changed the nature of cyber intrusion—how it moves, hides, and learns. The malware that used to crash systems now studies them. It blends into the operational hum of a company’s daily life: scanning invoices, mimicking emails, cloning credentials. Attacks now evolve in milliseconds, and the same automation that accelerates your business also accelerates your adversary.
When everything looks legitimate, defense becomes a design problem. The message from the latest IBM Institute for Business Value (IBM IBV) research: 91% of security executives say they need a new approach to cybersecurity that fuses architecture, operations, and culture.
The IBM IBV surveyed more than 1,000 senior security and business executives across 20 industries and 18 countries to identify the essential elements of effective cybersecurity in the age of AI. Our findings: some enterprises are reanimating an established approach, secure by design (SbD), 2 with new AI capabilities. The result is a holistic approach organizations need to combat new intelligent threats.
Secure by design involves embedding security and privacy practices into the entire product and service life cycle, from initial design stages through development, deployment, operations, and support. Once a phrase tucked into policy manuals and architecture decks, secure by design has been applied unevenly and rarely at scale in most organizations. The good news is, even though AI is what renders SbD essential now, AI can also help address the challenges it brings—in other words, the problem is also the cure.
In this report, we explore the three key advantages of a SbD approach when supplemented by AI. In part one, we’ll explain how innovation and security can become allies rather than rivals. Part two shows how AI can close a gap that often plagues security approaches. In part three, we delve into transforming ecosystems for collective resilience.
Secure by design involves embedding security and privacy practices into the entire product and service life cycle, from initial design stages through development, deployment, operations, and support.
Missed opportunity
While most leaders in our research say they believe in secure by design, far fewer have built it into how they operate
Part one
Innovation and security become codesigners—no more sacrificing one for the other.
AI has made intrusion a design problem. Systems now adapt in real time—sometimes under your control, sometimes not—and threats exploit that adaptability to blend in. The only viable defense is to make security and intelligence inseparable from the start.
The only viable defense is to make security and intelligence inseparable from the start.
The challenge isn’t commitment; it’s cadence. Governance frameworks were designed for periodic oversight, not for systems that update themselves in real time. In fact, in our research, 42% of executives rank “our own operational shortcomings” among their top threats—second only to cybercriminals and ahead of nation-state actors.
Organizations’ top threats to cybersecurity

Secure-by-design protocols, amplified by AI, change the equation. With structural safeguards baked into architectures and workflows, and AI-driven agents monitoring live data, correlating signals, and flagging exceptions, agility becomes the norm. Nearly three out of four organizations (72%) using SbD report significant improvements in governance, risk, and compliance (GRC). By automating governance work that previously required human intervention, AI-driven policy engines can detect anomalies and trigger corrective workflows without waiting for a manual escalation.
Fixing the innovation weak spot
Historically, security controls have often come at the expense of innovation: dampening new ideas for fear of hidden vulnerabilities. Even today, most enterprises in our research struggle to see their entire operational landscape.
But for those implementing SbD with AI, the script flips. Controls become code, not checkpoints; security runs in parallel with innovation sprints. The critical metric: 69% of organizations using SbD report enhanced ROI for new products and services.
When governance moves at the same speed as innovation, the old tradeoff between the two disappears. What’s left is a competitive advantage: synchronized agency and accountability across the enterprise. Resources are already following this opportunity, with leaders estimating that their combined spending on AI security and SbD accounts for more than one quarter of their current cybersecurity budget. Enterprises with mature SbD programs also report 11%–25% efficiency gains across IT and security functions, with incident response times shrinking as teams work from a shared playbook.
The next two years will see a wave of continued disruption and cybersecurity risk That means implementing SbD with AI is imperative. When governance and innovation operate in sync, speed stops being a liability. It becomes an asset—one that delivers a security posture as responsive as the business it protects.
Percentage of executives citing notable* efficiency enhancements and performance improvements

* Notable= efficiency enhancements of +11-25% or greater than 25%, and performance improvements of +16-25% or greater than 26%.
Considerations for codesign
Here are key questions to assess whether innovation and security are codesigners of operational safety and success within your enterprise:
- How should you redesign security governance frameworks to align with AI-driven systems that update themselves in real time?
- What strategies and technologies are most important to improving visibility across multicloud and hybrid cloud environments without increasing operational overhead?
- For enterprises that improved ROI through secure-by-design programs, what operational or cultural changes allowed security to support innovation without slowing it down? How can those same changes be applied to improve ROI in AI-related security initiatives?
- How should AI-driven policy engines connect with telemetry data and incident response processes?
- How can we make sure autonomous AI systems remain transparent, accountable, and open to audit when they are used for cyber-risk reporting and documenting major security incidents?
- With AI security and secure by design already consuming 25% of cybersecurity budgets, how should you ensure that spend translates into measurable reductions in risk and improvements in operational efficiency over the next 24 months?
Perspective
AI-powered threats now move faster than most enterprises can patch. Regulators are demanding proof of cyber maturity, not just promises. Microsoft’s Secure Future Initiative (SFI) shows how one global company is trying to meet that moment—by redesigning how its security is built, operated, and owned.
SFI marks a shift from reaction to prevention. The program rests on three pillars: integrating advanced controls into code from day one instead of chasing vulnerabilities later; relying on richer telemetry, threat intelligence, and automation to speed response; and making protection a shared outcome across the enterprise, from engineers to executives.
Microsoft’s blueprint relies on principles critical for any CIO and CISO:
- Standardization and automation tighten control.
- Linking design principles to governance turns aspiration into accountability.
- Transparency—publishing metrics, reporting progress—creates external pressure to improve.
As AI drives deeper integration across systems and partners, secure by design becomes the connective tissue that keeps innovation viable. It’s as much about aligning culture and governance as it is about tools.
Part two
Architectures and operations stay in constant sync, unlocking faster response.
Enterprise security has long lived with a quiet fracture. Architecture defines the blueprint; operations handle the battles. They’ve rarely moved at the same pace.
That was acceptable in a world of fixed infrastructure and predictable threats. Today, generative AI and autonomous agents move too fast for frameworks built to guard yesterday’s networks—sharing telemetry, automating workflows, and connecting across systems and partners.
Two-thirds of the executives say their security, technology, and operations teams still work in silos. Yet with every new API, dataset, and model, integration becomes more important. Without it, visibility erodes and the ability to respond in real time slips away.
Fortunately, the same forces driving heightened exposure also enable enhanced responsiveness. With AI, the distance between architecture and operations is shrinking.
Collapsing the silos
Next-generation security programs, built around SbD principles and AI functionality, weave intelligence into both architecture and operations, keeping the two in continuous dialogue. With AI agents monitoring anomalies and autonomously updating tactics in the face of new threats, the system becomes the solution: adjusting controls, tuning models, and refining policies as it learns.
The results are measurable. As we previously mentioned, organizations with optimized secure-by-design maturity report average efficiency improvements in the 11-25% range—and operational responsiveness was among the metrics measured. By correlating signals across environments, they catch what’s new precisely because it’s unexpected.
Organizations need to look at security through a new lens. Standardization and automation tighten control. Linking design principles to governance turns aspiration into accountability. And transparency (publishing metrics, reporting progress) creates external pressure to improve.
Challenges to scaling a secure-by-design program

Considerations for synchronization
Secure by design can be a kind of choreography that links architecture, operations, and AI into one adaptive system. In a landscape where AI rewrites the operating model daily, that alignment isn’t just technical—it’s a strategic advantage.
Here are key questions to assess if your architecture and operations are in sync:
- What organizational and process changes are most effective for breaking down silos between architecture, security, and operations teams—especially in enterprises where legacy structures resist integration?
- How can AI-enabled SbD frameworks be scaled across multicloud, hybrid, and partner ecosystems to maintain continuous synchronization and interoperability without creating new security or compliance risks?
- How do you need to update your governance model to ensure that core design principles—such as standardization, automation, and transparency—translate into measurable accountability for new AI infrastructure and operations?
- Which real-time metrics and telemetry signals should you prioritize to measure the health of your architecture and operations alignment? How should you report these to internal (business and operations) and external (supplier and partner) stakeholders?
- As AI agents achieve greater autonomy, adapting risk and security postures in real time, how should you balance the need for responsiveness with the need for stable, predictable operations—particularly in regulated industries where changes must be auditable?
Part three
AI forces deeper ecosystem dependence—and offers the means to defend it.
AI has redrawn the map of enterprise interdependence. Data, models, and workflows now flow through an expanding ecosystem of platforms, service providers, and shared environments. Business performance depends on that web staying connected—but security often stops at the organizational edge.
That gap is widening. A majority of executives (56%) report they struggle to collaborate across functions and across the operations lifecycle and 40% have suffered a breach involving a key partner in the past three years. Use of Managed Security Service Providers (MSSPs) is climbing—53% of organizations now rely on them—but the integration isn’t complete. Among MSSPs, 86% are tightly linked to the organization’s internal operations, yet just 40% extend that same rigor to suppliers and external collaborators. The result is a patchwork of protection: stronger where enterprises control the stack, more porous where ecosystems connect.
91% of executives agree that security is no longer just a set of technical capabilities but an operational outcome.
The executives in our study are aware of the consequences: 91% agree that security is no longer just a set of technical capabilities but an operational outcome, measured in uptime, responsiveness, and trust across the value chain. Yet despite that recognition, only one in four organizations monitor third-party AI model inputs and outputs. With the growing reliance on external AI services that shape decisions and data quality, that often means the systems informing daily choices are effectively “black boxes.”
Secure-by-design at scale: What organizations are implementing

Extending protection past the edge
What’s needed in this environment is to extend governance and accountability across the ecosystem—standardizing controls, telemetry, and identity frameworks so resilience can be measured in performance, not just in incident counts. SbD provides the framework for meeting that goal, with AI providing the dynamic intelligence necessary to embed adaptive monitoring and validation directly into shared connections.
The next phase of secure by design is federated trust—treating the ecosystem itself as a collective security surface.
When this sort of system is implemented, the ecosystem evolves from a set of external dependencies into a network of shared defense. Early adopters are already seeing the benefits. One in five organizations report performance improvements of 26% or more through deeper ecosystem integration, and 27% have strengthened supply chain resilience. They’re not adding more walls; they’re engineering visibility, automation, and trust into every link.
The next phase of SbD is federated trust—treating the ecosystem itself as a collective security surface. Bringing an AI mentality to that evolution means building intelligence into every connection you depend on, creating defenses that learn, coordinate, and strengthen together.
Considerations for ecosystem security
Cyber defense is no longer about stopping attacks. It’s about shaping the environment they move through. When AI lives inside every workflow and decision across ecosystems, resilience has to live there too. Secure by design, propelled by AI, is a living, learning, evolving system—at machine speed.
Here are key questions to assess the security design of an ecosystem:
- What technology and security governance frameworks can ensure consistent standards across your ecosystem—including suppliers, partners, MSSPs, and external AI service providers—without slowing operational performance? How is your approach to governance responsive to emerging technologies such as multiagent systems and agent-to-agent protocols?
- Given that only 25% of organizations monitor third-party AI model inputs and outputs, what processes and technologies should be prioritized to validate data integrity, decision quality, and bias in AI solutions from third-party providers?
- How can you transition from isolated security controls to a federated trust model—where ecosystem partners share telemetry, identity frameworks, and adaptive defenses—without compromising competitive or sensitive data?
- How can organizations use AI agents for contextual threat modeling and “what‑if” analysis to continuously test, validate, and improve secure‑by‑design architectures before risks emerge?
- What common metrics should be adopted to measure ecosystem resilience in terms of uptime, responsiveness, and trust—beyond traditional incident counts—and how can AI-driven telemetry make these metrics actionable in real time?
Perspective
If SbD is going to help organizations manage AI-first transformation more effectively, it’s critical to understand why some companies are seeing far greater returns than others. We looked at the alignment between capabilities, performance, and perception and found three gaps that could slow progress if left unchecked.
Practitioner friction
Our analysis reveals a gap between what infrastructure is capable of and how practitioners experience it day to day. In many cases, foundational capabilities are strong—but usability and integration issues keep teams from realizing that value in their workflows.
When practitioners are stuck in the middle of change, efficiency suffers. In AI-first transformation efforts, this reinforces the need to bring security teams along as active participants in the journey, rather than imposing change from the top down.
The perception-versus-performance gap
On the surface, average scores suggest most organizations have a realistic view of their efficiency. But dig deeper, and two extremes appear: one group significantly overestimates its performance, while another underestimates it just as badly.
This matters because SbD programs often function as cultural catalysts. They give stakeholders across the enterprise a common frame of reference—a shared language for security—even before hard efficiency gains show up in the metrics. In some cases, the belief in greater efficiency changes behavior enough to set the stage for real improvement later.
The efficacy gap
We found a consistent mismatch between security capabilities and the performance they deliver. On average, organizations have built capabilities that score five points higher than their current outcomes—meaning they’re leaving significant gains on the table.
In many cases, the tools are there, but practices haven’t caught up. For some organizations, the gap is severe: advanced platforms are producing minimal returns because they’re underutilized. Closing this gap requires investment in training, reskilling, and operational discipline.
The takeaway
Combining SbD and AI-first transformation requires aligning culture, capability, and execution. Done well, it turns perceived gains into real ones, unlocks unused potential, and ensures the people on the front lines of security can work at the same speed as the technology they’re protecting.
Action guide
The organizations pulling ahead aren’t reacting faster—they’re building differently. Secure by design is the shift from defense to architecture, from security as a perimeter to security as a property of everything you create. It’s about constructing systems that assume complexity, anticipate failure, and keep trust intact even as AI rewrites how business operates.
This guide translates that mindset into action. It shows how leaders can fuse strategy, engineering, and accountability to make protection part of the build—not the cleanup. Because in an environment where threats learn as fast as innovation moves, resilience isn’t added later. It’s designed from the start.
To thrive in an AI-driven threat landscape, organizations must shift from reactive security to proactive design. Here’s how leaders can act now:
Embed security requirements in every design and build phase.
- Embed security into every stage of product and service development—from architecture to operations.
- Use AI to automate governance, detect anomalies, and trigger real-time responses.
- Treat resilience as a built-in feature, not a bolt-on fix.
Bridge architecture and operations with shared visibility and automation.
- Integrate AI agents to monitor, adapt, and respond across systems.
- Standardize secure coding practices and automate security testing.
- Ensure telemetry and incident feedback loops inform continuous design improvements.
Integrate partners and providers into a unified security framework.
- Apply secure-by-design principles to suppliers, MSSPs, and external AI services.
- Share telemetry and identity frameworks to build federated trust.
- Monitor third-party AI inputs and outputs to validate data integrity and decision quality.
Tie executive sponsorship to accountable, secure‑by‑design execution.
- Ensure C-level sponsorship for secure-by-design programs.
- Fund integration across business, technology, and security teams.
- Use shared metrics to track resilience, responsiveness, and trust.
Unite AI and secure by design to build self‑defending systems.
- Leverage AI agents for contextual threat modeling and “what-if” analysis.
- Use AI to predict failure points and recommend design adjustments before risks materialize.
- Prioritize transparency, explainability, and auditability in AI-driven security systems.
Meet the authors
Indranil Sircar, Global CTO, Manufacturing and Mobility Industry, MicrosoftDimple Ahluwalia, Global Offering Leader, CyberDefend, IBM Cybersecurity Services
Srinivas Tummalapenta, CTO, IBM Cybersecurity Services, IBM Distinguished Engineer
Gerald Parham, Global Research Leader, Security and CIO, IBM Institute for Business Value
Originally published 13 November 2025








