Networks are the foundation of today’s connected world, making them a prime target of cyberattackers looking to cause disruption and a key source of data for threat detection and analysis.
IBM Security® QRadar® Network Detection and Response (NDR) helps your security teams by analyzing network activity in real time. It combines depth and breadth of visibility with high-quality data and analytics to fuel actionable insights and response.
In 2023, 70% of cyberattacks targeted critical infrastructure industries. Check out the new report for deeper insight into attackers’ tactics.
Get comprehensive, real-time visibility for improved network detection and response by combining event and flow data across on-prem and cloud environments.
Use machine-learning based analytics to help determine a baseline of normal network activity to identify suspicious behavior quickly before attackers cause disruption.
Enable broad threat visibility, detection and response in a unified solution that helps eliminate pivot between tools while optimizing and scaling security investments.
How it's used
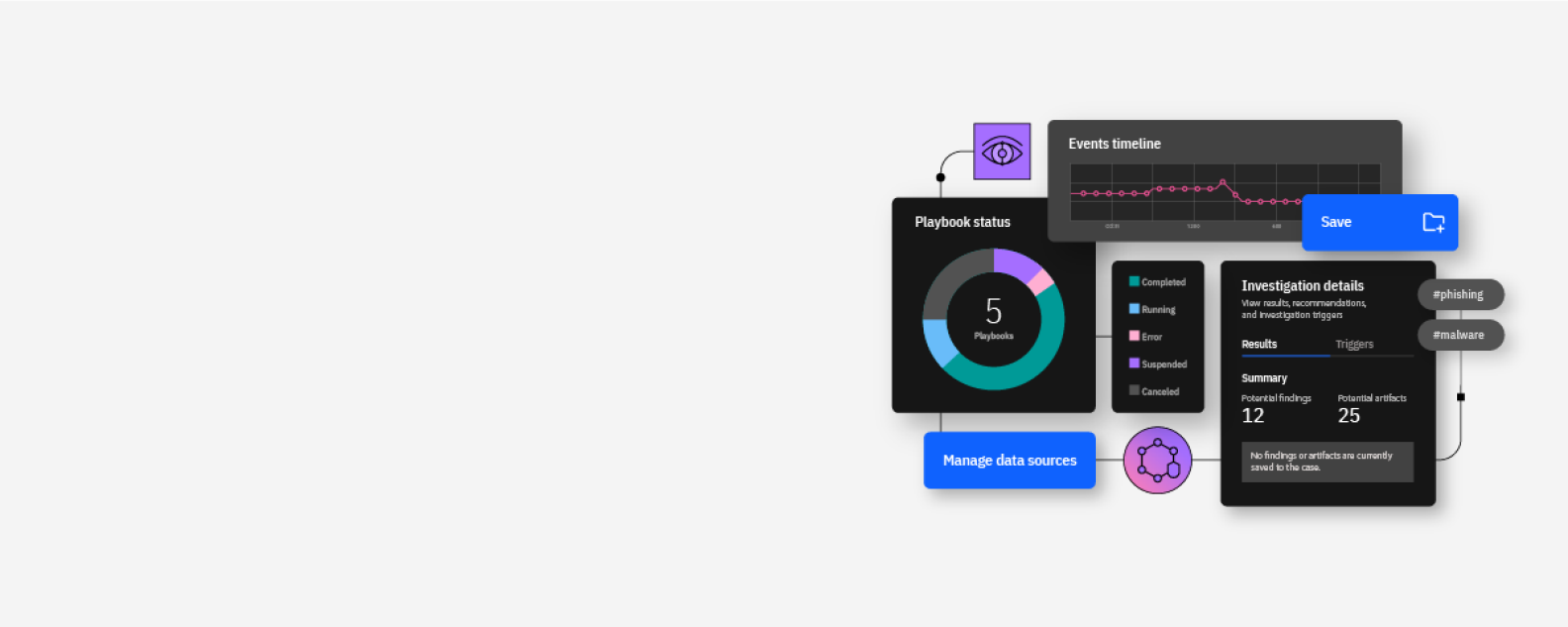
Threats hide within the volume of normal traffic on your network. Get a broad network view across a wide range of network devices.
Analyze and correlate network data in real time. Network Insights offers session reconstruction, full packet capture, extraction of key metadata and application analysis.
Detect slight changes in user or system behavior that might have gone unnoticed by baselining for normal network activity, scouting for anomalies and identifying suspicious behavior.
Get insights into your local DNS traffic by identifying malicious activity and enabling your security team to detect domain generated algorithm (DGA), tunneling, or squatting domains that are being accessed from within your network.
Retrace the step-by-step actions of cyber criminals by rebuilding data and retracing actions. Incident Forensics captures, reconstructs and replays the entire event chain.
Use an optional appliance to store and manage data used by QRadar Incident Forensics when no other network packet capture (Network PCAP) device is deployed.
NDR uses machine learning, AI and behavioral analytics to detect and respond to suspicious or malicious activity on an enterprise network.
See how these two products come together to accelerate response times and reduce analyst workload.
Detect and eliminate threats faster with a modernized product suite designed to unify the security analyst experience.
IBM Security® QRadar® EDR
QRadar EDR, formerly ReaQta, provides security analysts with deep visibility across the endpoint ecosystem. You can integrate QRadar EDR with QRadar SIEM with no impact to your EPS count.
IBM Security® QRadar® Log Insights
QRadar Log Insights helps ease the security analyst’s workload with a cloud-native log management and security observability solution that can handle an enterprise workload.
IBM Security® QRadar® SOAR
QRadar SOAR lorchestrates and automates responses to the high-fidelity alerts that SIEM identifies and provides actionable insight on remediating threats.
IBM Security® QRadar® SIEM
QRadar SIEM lets you run your business in the cloud and on premises with visibility and security analytics built to rapidly investigate and prioritize critical threats.