Preparing your business for takeoff
01
01
Treat Your Organization
Like an Airport
Treat Your Organization
Like an Airport
3 min read
The best security measures clear the way for business growth.
Much like an airport safely moves travelers to their desired destinations, your IT infrastructure is a vital hub between users and data.
An airport verifies the identity of everyone within its walls—from passengers and pilots to vendors and baggage handlers. These groups of individuals have varying levels of security clearance based on responsibilities, roles and unique attributes, such as airline status or members of the flight crew. And no matter what, they all expect a seamless and safe experience.
The same applies to your users. They’re unique individuals who need to get their jobs done without interruption or difficulty. At the same time, they expect you to enforce sufficient levels of security to safeguard them and your systems against data breaches and malicious attacks. That means you have to keep a watchful eye over potential security threats while efficiently guiding users to the data and resources they need.
Your organization can provide both strong security and a positive digital experience without compromising one for the other.
Your organization can provide both strong security and a positive digital experience without compromising one for the other.
Fortunately, your organization can provide both strong security and a positive digital experience without compromising one for the other. IBM’s Identity & Access Management (IAM) solutions give the right people access to the right resources in a seamless and secure way.
02
02
Identity Governance
& Administration
Identity Governance
& Administration
5 min read
Efficiently and intelligently manage digital identities.

When you purchase a plane ticket, the details you provide—like your identity, destination and seating preference—are used to automatically create a ticket. Your ticket entitles you to access everything you’ll need to get from point A to point B.
Your ticket grants certain levels of access and comes with guarantees, like compensation in case your flight is canceled, your baggage is lost, or your flight is overbooked. If you change your itinerary, the airline modifies your reservation and adjusts your ticket as necessary.
Identity Governance & Administration solutions work in the same way. When users join your organization, they’ll need access to certain IT systems and applications. Good identity governance ensures that these entitlements are provided appropriately, securely and without delay.
Good identity governance ensures that entitlements are provided appropriately, securely and without delay.
Good identity governance ensures that entitlements are provided appropriately, securely and without delay.
Identity Governance & Administration is the fundamental building block of any strong and comprehensive IAM strategy. It helps support enterprise IT security and regulatory compliance by managing digital identities and their corresponding “appropriate” access levels to a variety of resources. These resources require routine validation and certification processes to ensure access is valid and only on a need-to-know basis.
IBM Security Identity Governance & Intelligence (IGI)
While traditional Identity Management focuses on IT processes such as user provisioning and authorization, IBM Security Identity Governance & Intelligence (IGI) goes further to address the business requirements of line of business owners, risk and compliance managers and auditors through comprehensive compliance and analytics capabilities.
IGI manages the lifecycle of identities and corresponding entitlements. This enables you to confidently and securely grant and revoke access rights within your organization and provides a system of checks and balances around identity and access to prevent users from having excessive access to data.
With IGI you’ll be able to improve visibility into how access is deployed, prioritize compliance actions with risk-based insights and gain actionable intelligence for better decision-making.

Automate lifecycle management
Provisioning and deprovisioning the access rights for “joiners, movers and leavers” becomes automatic. This means your users are up and running seamlessly with immediate access to the applications they need.
Prevent “rubber stamp” approvals
Give managers business-friendly information to help with the approval and attestation processes, freeing them from cryptic IT jargon that could otherwise result in increased risk through bulk approvals. Leverage identity analytics to consume identity-related risk insights that empower managers with decision support by highlighting users, entitlements, and applications that should go through recertification.
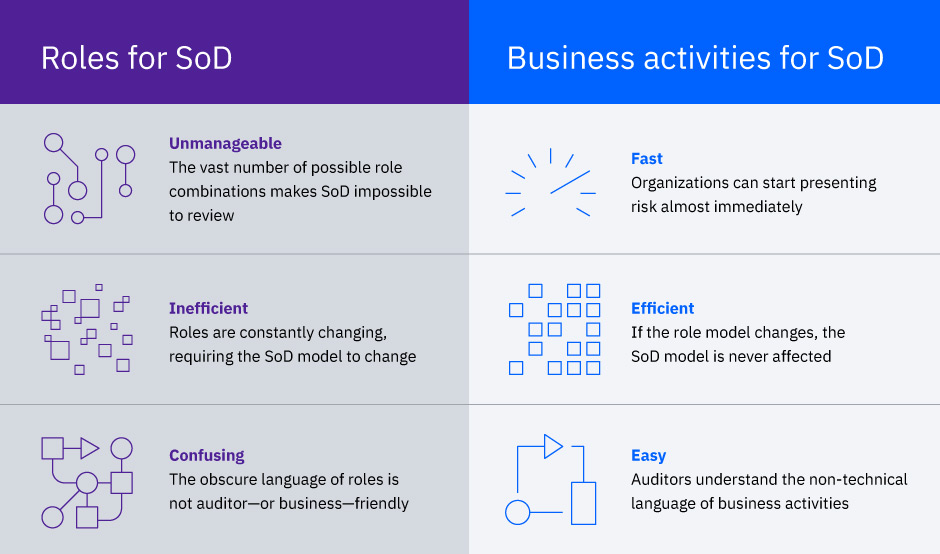
Implement separation of duties (SoD)
Enable a business activity-based approach to risk modeling. Traditional SoD relies on role-based risk models, but IGI offers a more efficient process to help auditors make sense of SoD.
A business activity is a specific task such as creating a purchase order or updating a client account. Business activities can be directly associated with specific business processes within industries, such as banking, retail or healthcare. Compared to the content within roles, business activities are more permanent in nature and are considered to be a more reliable base for implementing SoD policies. When you move risk modeling from roles to business activities, you provide an auditor-friendly view of SoD policies and violations. This translates entitlements into easily understandable risk identifiers that an auditor or a compliance officer can make sense of and act upon.
03
03
Authentication & Access Management
Authentication & Access Management
5 min read
Provide seamless access for users while securing your organization.

After arriving at the airport it’s time to meet with a TSA agent. The agent takes your ID and scans your boarding pass, which contains vital information needed to confirm your identity: booking reference number, your name, destination, class, seat, frequent flyer number and so on.
A TSA agent then checks to make sure the name on your physical ID matches the one on your boarding pass before granting you entry.
Single sign-on (SSO)
Once the TSA agent authenticates your boarding pass at the first security checkpoint, it becomes your de facto key granting you access to enter any area you’re authorized to visit, such as an airline lounge or the jetway when boarding your plane.
SSO functions the same way for your IT systems. Users log in initially with a single ID and password and in turn gain access to several related systems. This is a core component of effective Authentication and Access Management processes, which unify your organization’s applications under one secure platform.
User authentication
SSO makes it easy for users to access multiple different applications with the same set of user credentials. If they successfully authenticate into one service, they will be authenticated into other connected services without having to re-enter their credentials. This means external customers and internal employees can securely access your business services without having to repeatedly enter their credentials.
IBM Security Verify
Through its cloud-delivered SSO, multi-factor authentication and lifecycle management capabilities, Verify helps secure user productivity and makes identity consumable and business-friendly. It comes with thousands of pre-built connectors for commonly used SaaS applications and connector templates – for legacy and custom applications – to help you quickly provide access to employee and consumer-facing apps.
Deployed as a standalone or in combination with other access management tools, Verify helps you deliver trusted authentication with a frictionless user experience that balances security and convenience.
Verify helps you deliver trusted authentication with a frictionless user experience that balances security and convenience.
Verify helps you deliver trusted authentication with a frictionless user experience that balances security and convenience.

Provide seamless access to thousands of apps
Verify provides you with a unified application launchpad and SSO platform, so your employees can securely access approved applications with one set of credentials, whether the applications are running on-premises or in the cloud. It also gives you the ability to grant your consumers access to your organization’s external applications via developer-friendly APIs, which can be easily tailored to your unique brand.
Enable flexible multi-factor authentication everywhere
Protect your systems from compromise with advanced authentication capabilities. Verify enables multi-factor authentication and password-free login (such as logging in via thumbprint or Face ID). Verify also allows you to apply MFA everywhere in your IT environment, including virtual protocol networks (VPNs), Red Hat Enterprise Linux (RHEL), Microsoft Windows, Linux, IBM AIX® and IBM Z®.
Protect your systems from real-time threats
Verify comes embedded with IBM Trusteer® to provide real-time analytics and risk detection. Together, they provide adaptive access, so you can create a better experience for your users with authentication that adapts based on the level of risk. Through Verify, you'll be able to visualize your IAM environment, helping you make better informed decisions and prioritize actions related to real-time identity risks.
04
04
Privileged Access Management
Privileged Access Management
5 min read
Secure passwords, protect endpoints and keep privileged accounts safe.
Secure passwords, protect endpoints and keep privileged accounts safe.

Airports have multiple layers of security. Passenger status and airline employee role dictate clearance into certain sections of the airport and grant specific privileges on a plane. For example, pilots and flight attendants go through special security checkpoints and use different security passes. These passes have a longer lifecycle (i.e., an employee’s pass will work for the duration of their employment while a passenger can only use their boarding pass at a specific time and date). They even look different from the boarding passes used by passengers.
Because of the sensitivity of these resources, varying levels of clearance must be handled properly to ensure everyone is who they claim to be, and that they have the appropriate clearances.
When not protected, managed and monitored properly, privileged accounts can pose significant security risks.
When not protected, managed and monitored properly, privileged accounts can pose significant security risks.
Your users also have different access needs, depending on their roles within your organization or customer status. This is part of Privileged Access Management (PAM), a crucial solution necessary to maintain the integrity and guarantee the rights of privileged accounts that exist in many forms across your IT environment. When not protected, managed and monitored properly, privileged accounts can pose significant security risks. Just imagine a disgruntled airline employee entering a control room because they had excessive access; they could shut down an entire airport!
IBM Security Secret Server
IBM Security Secret Server is a full-featured PAM solution that allows you to protect and manage all privileged access and accounts within your organization. This includes individual users as well as shared accounts such as administrative or service accounts. IBM Secret Server lets you quickly discover, control, manage and protect privileged accounts and store credentials confidently in a secure password vault.
IBM Security Secret Server makes it easy to manage privileges throughout their lifecycle, automating manual processes through policy-based controls. Credentials are stored in a secure password vault, and built-in password changing and expiration schedules ensure critical passwords are changed automatically without manual intervention.
Meanwhile, you’re able to get ahead of compliance and evolving regulations while ensuring authorized users have access to the tools and information they need.
IBM Security Privilege Manager
IBM Security Privilege Manager is a comprehensive endpoint privilege management and application control solution that prevents malware from exploiting applications on endpoints through least privilege policies. IBM Privilege Manager removes local administrative rights from endpoints at once without causing any friction to slow productivity. It uses policy-based controls to elevate applications users need to do their jobs, without requiring administrative credentials or requesting IT support. By doing this, you’ll tighten your attack surface and avoid spending time and resources on reactive detection and remediation. Enterprises and fast-growing teams can manage hundreds of thousands of machines through IBM Privilege Manager, with built-in application control and actionable reporting that demonstrates value to executives and auditors.

Run discovery and remain in control
The first step in managing privileged accounts is finding accounts you don’t know exist. IBM Secret Server’s Discovery quickly scans your network to find and take over unmanaged privileged, shared and service accounts.
Monitor and control privileged accounts
Maintain a full audit trail for your critical systems by recording remote sessions. IBM Secret Server provides real-time session monitoring and control including proxying, session recording, and keystroke logging.
Implement a least privilege model
With IBM Security Privilege Manager, least privilege via application control reduces the attack surface by restricting the applications allowed to run, the devices allowed to connect, and the actions a system can perform.
05
05
Security Without
the Slowdown
Security Without
the Slowdown
3 min read
When security works silently in the background, your organization is clear for takeoff.
When security works silently in the background, your organization is clear for takeoff.
With IBM solutions for IAM, your organization will reach new heights—without the barriers of security protocols that can negatively impact user experiences. Let IBM work behind the scenes to secure your organization and ensure the right people have the right access to what they need, when they need it.
The benefits of IBM solutions for IAM
- Eliminate username/password hassles with SSO, so users log in once and are automatically authenticated with as many levels of clearance as they need.
- Create a seamless user experience with password-less authentication options like biometrics (touch ID, face ID), QR codes, and FIDO2.
- Detect insider threats with real-time behavioral analytics and enforce least privilege permissions to defend against malware attacks.
- Eliminate the friction from step-up authentication when not necessary while protecting your data and your network with multi-factor authentication when risks present themselves.
- Drive business growth by improving the user experience through seamless risk-based authentication.
- Continuously and reliably prove compliance to stay ahead of audits and evolving regulatory mandates.


