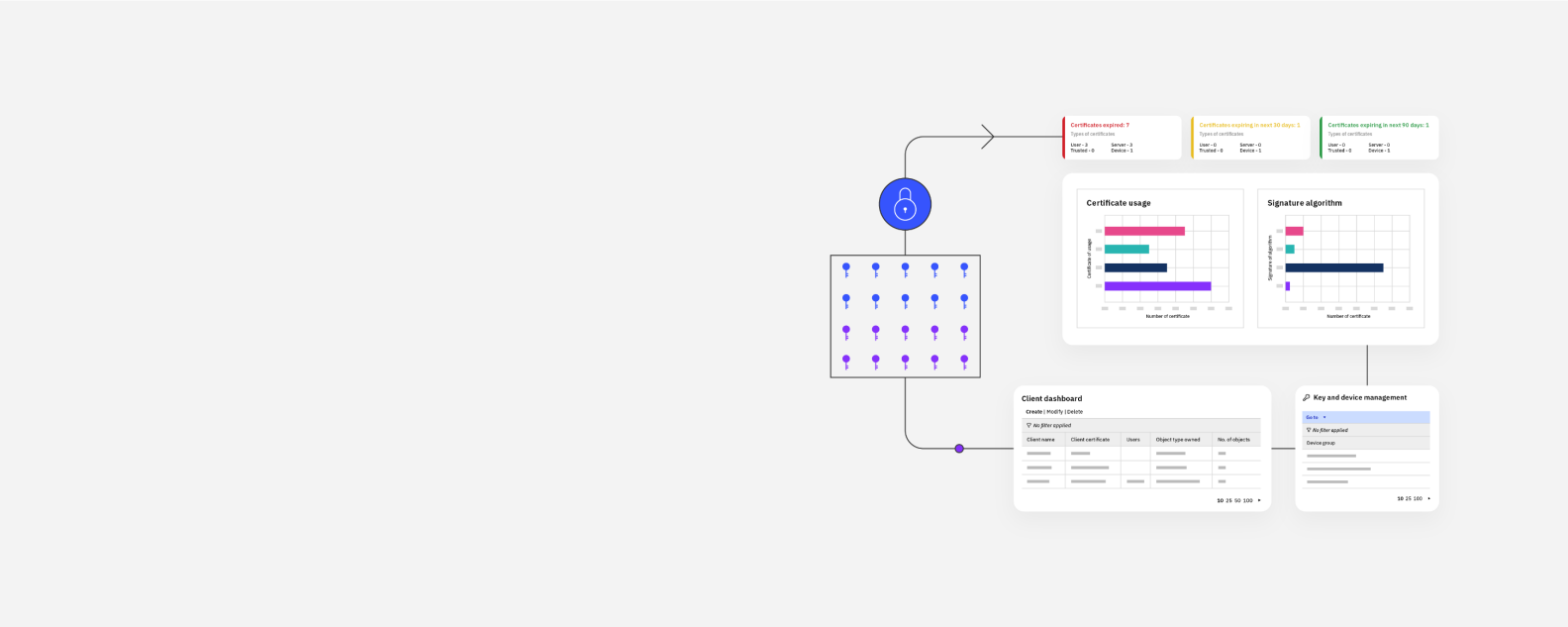
IBM Security® Guardium® Key Lifecycle Manager is software for encryption key creation, storage, backup and management. It is part of the IBM Guardium family of data security software.
IBM Security Guardium Key Lifecycle Manager is an encryption key management tool that centralizes, simplifies and automates the key management process. It offers robust and security-rich key storage, key serving and key lifecycle management for self-encrypting applications and solutions by using interoperability protocols, including KMIP, IPP and REST, and interfaces such as PKCS#11. Guardium Key Lifecycle Manager helps clients meet regulations such as PCI DSS, Sarbanes-Oxley and HIPAA by providing access control, key rotation and other automated key lifecycle management processes.
Check out the X-Force Threat Intelligence Index 2024 for deeper insight into attackers’ tactics and recommendations to safeguard identities
Learn why Omdia ranks IBM Security Guardium Key Lifecycle Manager #1 in encryption key management
See what's new in our latest release, including endpoint certificate insights, support for Oracle TDE databases and more
Provides centralized, simplified, and transparent key management through the secure storage of key material and the serving of keys at the time of use.
Offers simple, secure integration with supported protocols, including KMIP, IPP and REST, and interfaces such as PKCS#11.
Reduces key management costs by automating the assignment and rotation of keys.
Offers multiple deployment options, including on bare-metal servers, as a virtual machine or as a container.
Guardium Key Lifecycle Manager requires a combination of both software and usage entitlements.
Eligible software license types:
- GKLM Basic Edition
- GKLM Container Edition for Distributed Platforms
- GKLM Container Edition for zCX
Eligible usage license types:
- Resource Value Units based on raw or usable decimal terabytes or petabytes of storage
- Device-type licenses for certain endpoints (Transparent Data Encryption Databases, VMware and others)
Learn how to improve your data security and compliance posture.
Learn about device certificates and why you need a system in place to monitor their health and status.
Learn how an encryption key management system keeps data secure from unauthorized use, alteration, exfiltration or deletion.
See the IBM Security Guardium Key Lifecycle Manager supported devices.
See the latest on all IBM Security Guardium Key Lifecycle Manager version 4 and 3 releases.
See the support matrix for hardware, operating systems, browsers, hypervisors, middleware, HSMs, and KMIP.
Get centralized visibility, monitoring, compliance, advanced analytics and data source flexibility. Simplify data security and analytics.
Looking to identify shadow data and its movement across applications? Read about the Data Security Posture Management (DSPM) capabilities in Guardium Insights.
Monitor data activity and accelerate compliance reporting for data stored anywhere. Discover and classify data and data sources, monitor user activity, and respond to threats in near real time.
Scan your data to detect vulnerabilities, threats and security gaps to help safeguard your data.
Enable zero-trust based discovery and classification of sensitive and regulated data, wherever it resides, structured or unstructured, at rest or in motion.
Encrypt sensitive data in all states and across environments for different types of data, including your files, databases and applications. Address data security and privacy regulations, and control encryption keys for cloud-based data.