IBM Security® Trusteer® Pinpoint Assure is SaaS to detect and predict identity risk for guest users and during digital account creation. It is part of the Trusteer family of products in the IBM Security® portfolio.
What happens when you need to validate a new customer or a guest user? Without prior information or customer records—and when the information you rely on is publicly available—it can be a challenging task to determine whether an account was created by a true user or by a cybercriminal.
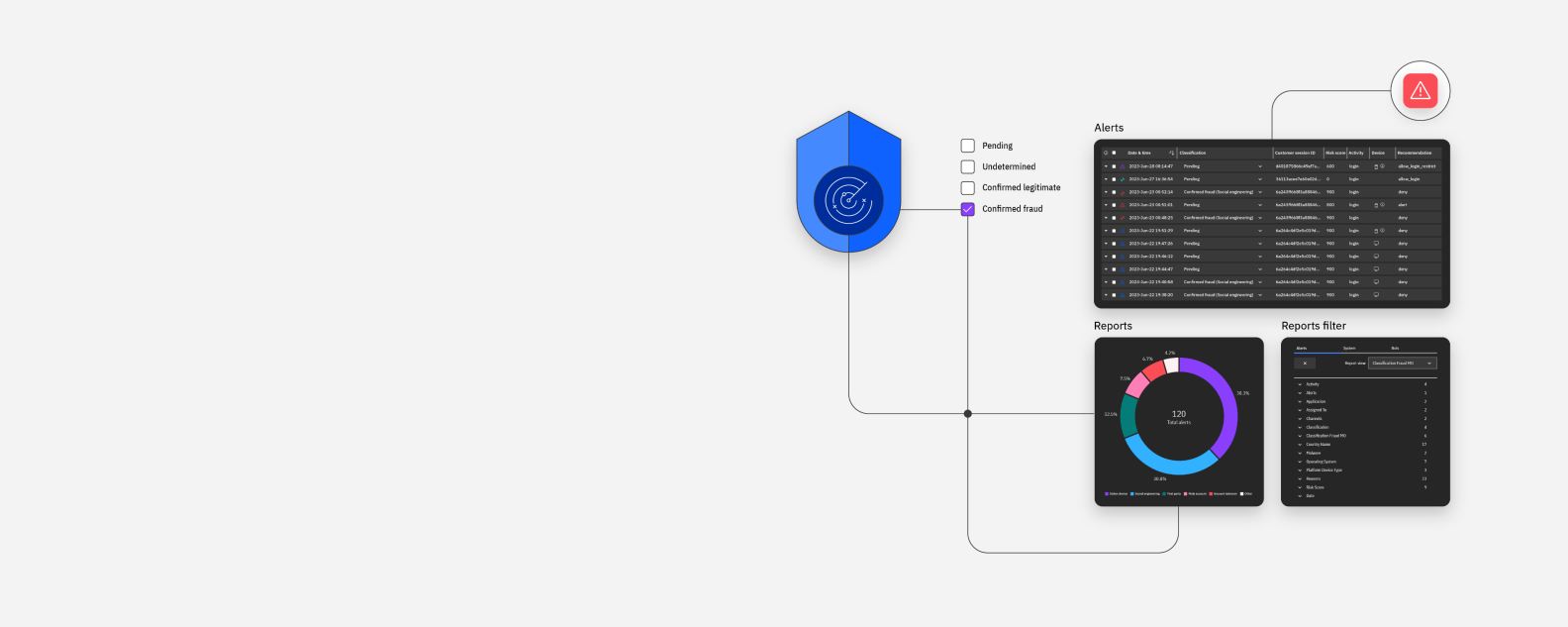
IBM Security Trusteer Pinpoint Assure is real-time, cloud-based identity risk software that detects and predicts the risk of fraudulent intent, which allows you to establish a trusted digital relationship early in the new digital account creation process.
In 2023, organizations saw a 71% spike in cyberattacks caused by exploiting identities. Check out the new report to learn how to best safeguard identities.
KuppingerCole Leadership Compass - See why Trusteer was named an overall leader in the latest Leadership Compass: Fraud Reduction Intelligence Platforms (FRIP).
Trusteer correlates advanced intelligence with our global fraud evidence database to assess digital identities.
Trusteer uses rich proprietary insights and advanced analytics across the omnichannel customer journey.
Trusteer seamlessly assesses new account creation risk for a personalized and improved customer experience.
Analyze patterns early in the new account creation process, including data reputation, using global consortium data.
Use mobile carrier intelligence to assess the risk of fraudulent intent.
Identify linkages in a multitude of data to detect fraudulent patterns.
Detect patterns across protected banks as fast as known fraudsters.
Share insights on account opening risk with account takeover risk assessment.
Detect re-use of data and mismatches between data provided during account opening.
Detect account opening by malicious bots, including velocity patterns.
Detect device hygiene risks, including malware, spoofing, virtual machine and emulated devices.
Get insights about potential mule account creation in the account opening process.
Use cases
Through cloud-based intelligence, backed by AI and patented machine learning, Trusteer provides a holistic approach to identifying new and existing customers, without negatively impacting user experience.
Forrester studied the potential ROI that enterprises may capture by deploying IBM Security Trusteer.
When using IBM Cloud® offerings, your company can scale and adapt quickly to changing business needs without compromising security, privacy or risk levels. Learn more about IBM Cloud security.
This offering meets the following industry and global compliance standards, depending on the edition you choose.
- EU-US Privacy Shield and Swiss-US Privacy Shield Framework
- FFIEC for Financial USA
- ISO 27001
- SOC2 Type 2 (SSAE 16)
To learn about the compliance and certifications for a specific offering edition, consult the Cloud Services data security and privacy data sheets.
Outsmart account takeover attempts with AI, behavioral biometrics and machine learning.
Access an embedded security library for native mobile web applications.
Detect and remediate malware and identify phishing attacks within minutes.
Frequently asked questions
Get answers to the most commonly asked questions about this product.
Companies often have to make tradeoffs between security and customer experience in today's threat landscape. Digital identity trust technology lets companies measure both risk and trust to keep the customer’s digital journey secure while still offering a better digital experience.
In general, software as a service (SaaS) solutions offer the ability to deploy quickly and easily. The SaaS deployment also allows Trusteer to employ agile, ongoing threat protection that uses AI and analytics to identify new threats and patterns.
IBM Security Trusteer Pinpoint Assure assesses the risk of new or anonymous users. IBM Security Trusteer Pinpoint Detect continuously assesses the digital identities of known or enrolled users.
IBM Security Trusteer products are primarily used by banks, financial institutions, insurers, retailers, telecommunications, travel and transportation industries.
Launch the interactive demo for a step-by-step walkthrough or get more detailed implementation techniques at the Security Learning Academy.