How To
Summary
Secret Server allows the use of SAML Identity Provider (IDP) authentication instead of the normal authentication process for single sign-on (SSO). To do this, SS acts as a SAML Service Provider (SP) that can communicate with any configured SAML IDP.
Objective
Secret Server allows the use of SAML Identity Provider (IDP) authentication instead of the normal authentication process for single sign-on (SSO). To do this, SS acts as a SAML Service Provider (SP) that can communicate with any configured SAML IDP.
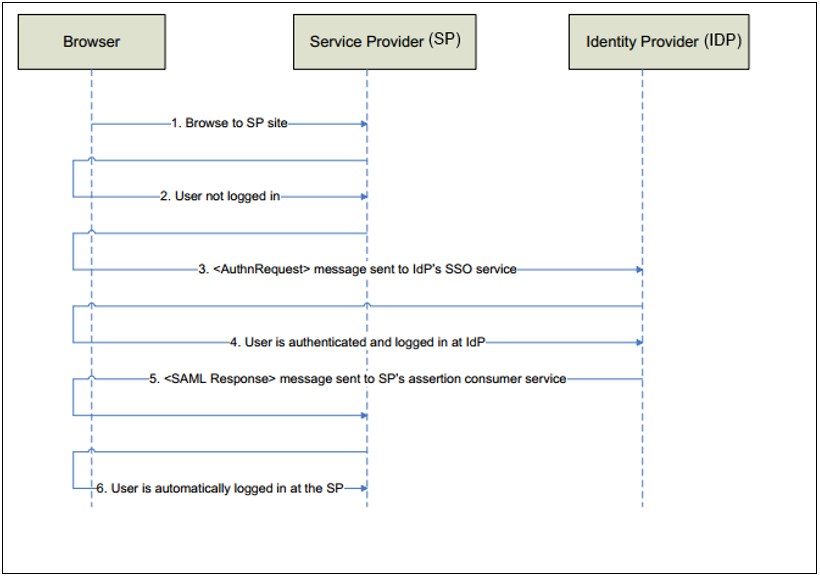
In the diagram below, SS acts as the service provider.
Figure: Secret Server as a SAML Identity Provider
Prerequisites
Licensing and Version
Secret Server Professional Edition or higher, upgraded to version 10.5 or later. To install a new SAML license, go to Admin > Licenses > Install New License.
.NET Framework 4.6.2+
To use SAML 2.0, you must install .NET Framework 4.6.2 or higher on your Web server. This allows SS to use Microsoft’s “next generation” CryptoNG API for signing SAML requests, instead of being limited to the much older CryptoAPI. This is often necessary to use modern SSL certificates and is strongly recommended as a security best practice.
To download and install the latest version of .NET Framework: See Microsoft .NET Framework 4.8 offline Installer for Windows for the latest version as of when this topic was written. If you have already installed SS on the same Web server, you have already done this.
Steps
Administer Configuration SAML Role Permission
The “Administer Configuration SAML” role permission is required to use SAML to access SS. To grant a user this permission from an administrator account:
-
Go to Admin > Roles. The Roles page appears.
-
Click the Create New button. The Role Edit page appears:
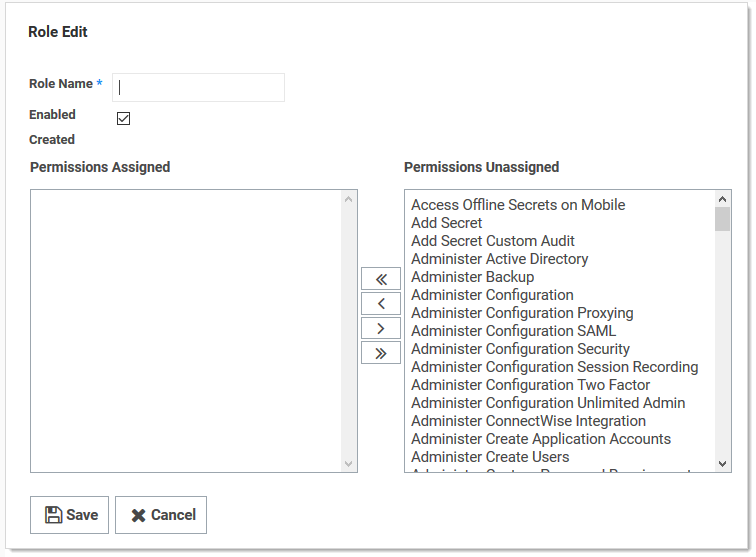
-
Type the name, such as
SAML, in the Role Name text box. -
Click to select the Enabled check box.
-
Click Administer Configuration SAML in the right side Permissions Unassigned list box.
-
Click the < button to move the permission to the other side.
-
Click the Save button. The Roles page returns.
-
Click the Assign Roles button.name link of the newly created role. The View Role Assignment page appears:
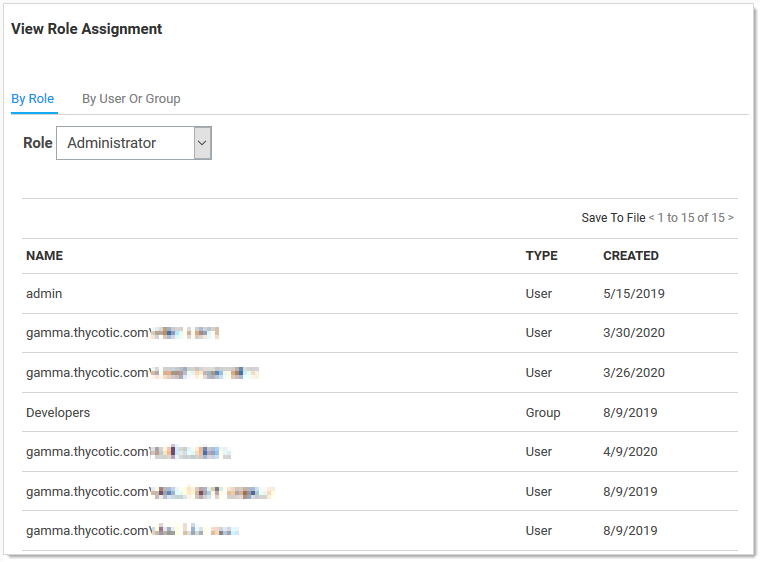
-
Click the Role dropdown list to select the role you just created.
-
Click the Edit button. The Role Assignment page appears:
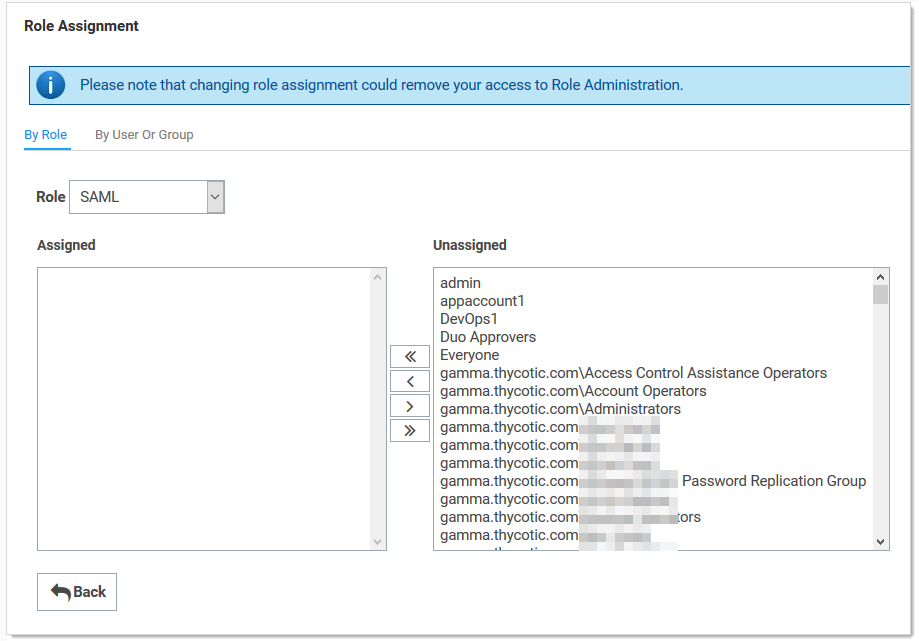
-
Move the desired users to the Assigned list using the same method as before.
-
Click the Save Changes button.
Setting up Secret Server
-
Navigate to Admin > Configuration.
-
Click the SAML tab:
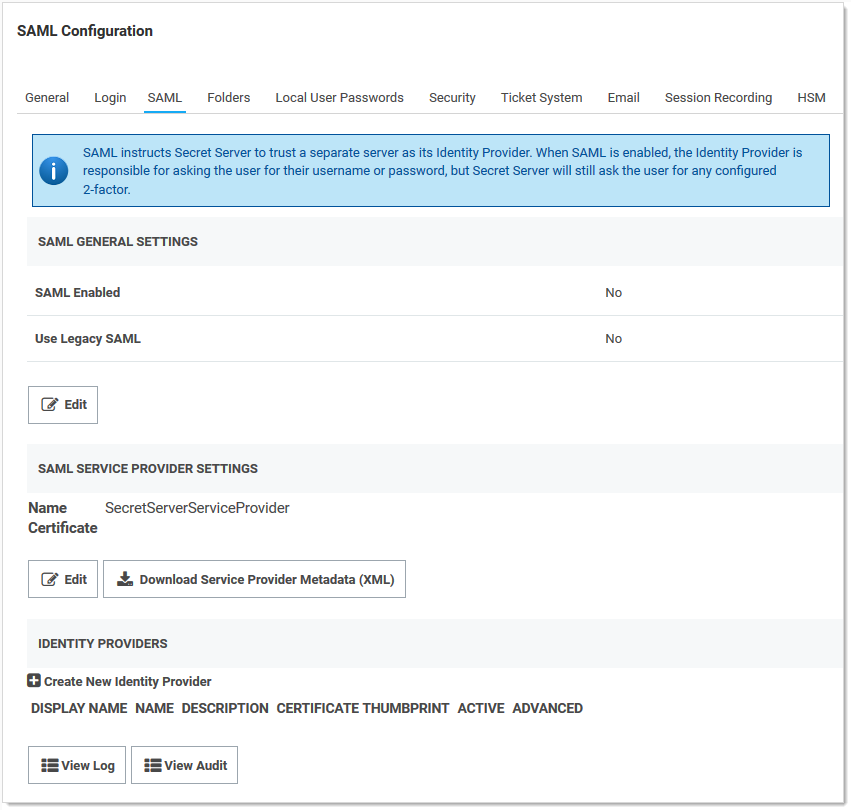
-
Click the Edit button in the SAML General Settings section.
-
Click to select the SAML Enabled check box.
-
Click the Save button.
-
Under General Settings, click Edit, then check the SAML Enabled checkbox. Save changes.
-
Click the Edit button in the SAML Service Providers section.
-
Type a name for your SS service provider, such as
SecretServerServiceProvider, in the Name text box. -
Click the Select Certificate link. The Upload Certificate popup appears:
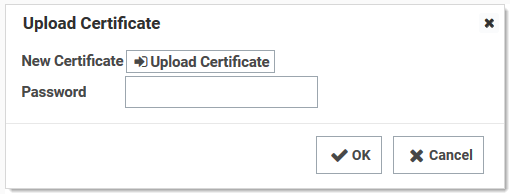
-
Choose your certificate:
- For on-premises instances: the uploaded certificate should match the one used for Secret Server’s HTTPS configuration, or you can create it as a self-signed certificate using this PowerShell script.
- For Secret Server Cloud users: Generate your own certificate using this PowerShell script.
Note: Run the referenced PowerShell script as an admin on a machine with .NET 4.5 or above, and replace the variables in the script as directed. Your certificate will be created in the directory from which you run the script. The subject name on the certificate is irrelevant, though for on-premises instances it typically will match the URL of the instance.
-
Click the Upload Certificate button.
-
Locate your certificate
.pfxfile and select it. -
Click the Open button. The new certificate appears.
-
Type the access password for the private key of the certificate in the Password text box.
-
Click the OK button. The certificate is uploaded and tested, and the popup disappears. The certificate now appears in the SAML Service Provider Settings section.
Note: If you have an outdated version .NET Framework (earlier than 4.6.2), you may see an error recommending you upgrade to fix the error. Reload the certificate after you do so. -
Click the Save button.
-
Click the Create New Identity Provider link. An Identity Provider popup appears.
-
Click the Import IDP from XML Metadata link.
-
Navigate to your
SecretServerSAMLMetadata.xmlfile and select it. This is used for uploading into your IDP, which varies by provider. Follow instructions in the following section.. -
Click the Open button.
Additional Information
Setting up IDPs
IDP setup varies by provider:
Note: The username returned from the IDP to SS within the SAML Response/Assertion’s subject statement must match the desired format. The format of the username passed depends upon how the user was created within SS.
Note: If AD Sync was used to create SS users, the username returned from the IDP must match this format:
SecretServerUsername@ADsyncDomainorADsyncDomain\SecretServerUsername. If using SLO, ensure that the NameID is set correctly in the IDP as an outgoing claim for the Secret Server Service Provider. If a user has different sAMAccountName and userPrincipalName in Active Directory, custom rules in the IDP can be created.
Lockout Workaround
Locked Out? Here’s how you get around SSO. If during the configuration process for SAML you lock yourself (as an administrator or a user) out of SS, you can log on SS without using the SSO workflow by using this URL string:
[YourSecretServerInstanceName]/login.aspx?preventautologin=true
The role permission needed for this is “Bypass SAML Login,” which admins have by default.
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
08 February 2021
UID
ibm16233424