Troubleshooting
Problem
Instructions to create certificate and private key from DCM for CIMOM server.
Resolving The Problem
These steps use the Digital Certificate Manager (DCM) to create certificates and private keys in PEM format for Pegasus (CIMOM Server) to use. A Certificate Authority (CA) is created, and then used to issue a server certificate.
This document is presented 'as-is'. We recommend us self-signed certificate. With last PTFs for CIMOM Server, the self-signed certificate has last security settings.
We suggest other options instead, as manipulating certificate is sensitive.
We suggest other options instead, as manipulating certificate is sensitive.
Additional information can be found in document CIMOM server certificate
Note: These steps need to be done only ONCE for all the tests. Additional information about DCM could be found in document Digital Certificate Manager (DCM) - Frequently Asked Questions and Common Tasks
1) Starting up DCM in your browser
1) Starting up DCM in your browser
1. Make sure that 5770SS1 Option 34 - Digital Certificate Manager is installed.
2. Start the HTTP admin server if not already:
STRTCPSVR SERVER(*HTTP) HTTPSVR(*ADMIN)
3. In your browser, go to http://<system’s name or IP address>:2001
4. Log in with your IBM i user profile (should be a *SECOFR user profile)
5. Click IBM i Tasks Page.

6. Select Digital Certificate Manager in I5/OS tasks

7. Log in with your IBM i credentials
2) Creating a Local Certificate Authority (CA)
2) Creating a Local Certificate Authority (CA)
Note: *SYSTEM certificate store should exist before to follow the steps. If it doesn't, will need to create that one first. Check steps in document How to Create the *SYSTEM Store in DCM
1. Press “Select a Certificate Store” in the left frame. If you already have a Local Certificate Authority (CA), skip to Step 3.
2. Click “Create a Certificate Authority (CA)” in the left menu.

3. Fill the information as following:
Key algorithm: RSA
Key size: 2048 bits (or 4096 if available)
Hash algorithm: SHA512
Fill the rest such CA password/label and Company information. Also set Validity period of Certificate Authority (CA). Click Continue.

4. Skip the step that installs the CA certificate in your browser. Click Continue.

5. On "Certificate Authority (CA) Policy Data" screen, set a validity period of certificates. Default is 365 days. Click Continue.

6. On the “Select Applications to Trust this Certificate Authority (CA)” screen, select nothing and click Continue.

7. On "Application Status" screen click Cancel.
With this, will have created a local CA, a certificate store to store the CA’s certificate and the CA’s certificate. Now you should see the “Local Certificate Authority (CA)” in the “Select a Certificate Store” screen.
3) Creating a CIM Server application that will be assigned a certificate
3) Creating a CIM Server application that will be assigned a certificate
1. Press “Select a Certificate Store” in the left frame
2. Choose *SYSTEM. Put store's password and click Continue.
3. Expand “Manage Applications” in the left frame and click on “Add Application”

4. Choose “Server” on the first screen. Click continue.

5. Complete Application ID as “QUMECIMOM”, Application Description as “CIM Server”,
Exit program as "QSY_NOPGM", Exit program library as "QSY_NOLIB" and
Multithreaded job action as "Run program and send message".
Click Add button at the bottom.

4) Creating a certificate issued by the Local Certificate Authority (CA) and assigning it to the CIM Server application
4) Creating a certificate issued by the Local Certificate Authority (CA) and assigning it to the CIM Server application
1. Press “Select a Certificate Store” in the left frame
2. Choose *SYSTEM. Put store's password and click Continue.
3. Choose “Create Certificate” in the left frame.

4. On "Create Certificate" screen, select “Server or client certificate” and click Continue.

5. On "Select a Certificate Authority (CA)" screen, select “Local Certificate Authority (CA)” and click Continue.

6. On "Create Certificate" screen fill the information to create the certificate:
Key algorithm: RSA
Key size: 2048 bits (or 4096 if available. Should match what selected for CA)
Fill the rest such 'Certificate label' and 'Common name' (shouldn't be the same) and Company information. Click Continue.

7. On “Select Applications” screen, choose the “CIM Server” application that was created before and click Append. The following should be displayed. Click OK.

Note: If you get the below issue when create certificate:
The validity period does not contain today or does not fall within its issuer's validity period.
The certificate is either not yet valid or it is no longer valid.
Be sure that the date, time, offset from GMT, and Daylight Savings Times (if applicable) are correct on your system, the browser, and the CA.
You can check expiration of the CA in 'Work with CA certificates'

5) Exporting the certificate to IFS
5) Exporting the certificate to IFS
1. Press “Select a Certificate Store” in the left frame.
2. Choose *SYSTEM. Put store's password and click Continue.
3. Expand “Manage Certificates” in the left frame and click “Export certificate”.

4. On "Export Certificate" screen, select “Server or Client”. Click continue.

5. Select the certificate created for CIM server (in Step 4) and press “Export”.
6. On "Export Destination" screen, select “File” and click Continue.

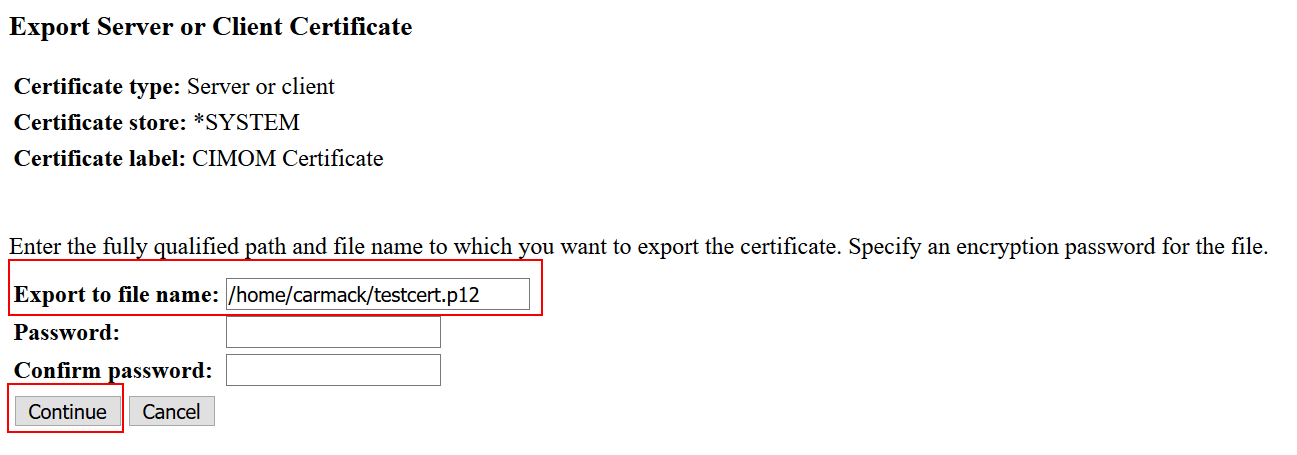
7. On the "Export Server or Client Certificate" fill the information requested and click Continue.
Export to file name: > Need to specify the entire IFS path. Example: /home/carmack/testcert.p12 where carmack is your home's profile.
Password: & Confirm password: > set any password for the file to be exported.
Note: Use testcert.p12 as the file name. DCM puts the CA certificate, the CIM Server certificate, and the CIM Server private key into the file testcert.p12.
6) Converting the certificate to a format that Pegasus (CIMOM server) can use
6) Converting the certificate to a format that Pegasus (CIMOM server) can use
1. On the IBM i system command line, start PASE using.
Example:
CALL QP2TERM
2. Change to the directory where the certificate was exported.
Example:
CD /home/carmack
3. Convert the certificate to a PEM file without an encrypted private key. The PEM file will be called testca_nopass.pem.
Run:
openssl pkcs12 -in testcert.p12 -out testca_nopass.pem -passin pass:xxx -nodes
Where xxx is the password set when exported the file.

4. Convert the certificate to a PEM file with an encrypted private key. The PEM file will be called testca_pass.pem.
Run:
openssl pkcs12 -in testcert.p12 -out testca_pass.pem -passin pass:xxx -passout pass:testpw
Where xxx is the password set when exported the file. The passout password is testpw. This is the password to decrypt the private key.

5. Verify the PEM with the unencrypted private key. Run the following command from PASE environment (CALL QP2TERM).
Run:
cat testca_nopass.pem
You should see the information of the file. This has the CA certificate, followed by the CIM server certificate, followed by the unencrypted private key. Scroll the screen to check the information is correct.
6. Verify the PEM with the encrypted private key. Run the following command from PASE environment (CALL QP2TERM).
Run:
cat testca_pass.pem
You should see the information of the file. This has the CA certificate, followed by the CIM server certificate, followed by the encrypted private key. Scroll the screen to check the information is correct.
7. From IBM i command line, copy testca_pass.pem to testprivkey_pass.pem to extract the encrypted private keys from the PEM file.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testca_pass.pem' ) TOOBJ('/home/carmack/testprivkey_pass.pem')
8. Edit testprivkey_pass.pem and delete all the lines except the lines starting at "-----BEGIN ENCRYPTED PRIVATE KEY-----" and ending
at "----END ENCRYPTED PRIVATE KEY-----" (should be the last section of the file)
Example:
EDTF STMF('/home/carmack/testprivkey_pass.pem')
From the EDTF screen, put a 'DD' at the first line and a 'DD' the line before "BEGIN ENCRYPTED PRIVATE KEY" section. Hit enter and will delete all the lines between 'DDs'
Press F3 twice to save the changes.

Note: Not all the information is displayed. It's just for example purpose.
9. From IBM i command line, copy testca_pass.pem to testservercert_pass.pem to extract the encrypted server certificate issued by the CA from the PEM file.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testca_pass.pem') TOOBJ('/home/carmack/testservercert_pass.pem')
10. Edit testservercert_pass.pem and delete all the lines except the second certificate section lines starting at "-----BEGIN CERTIFICATE-----" and ending
at "-----END CERTIFICATE-----" for the certificate with CIM Server as the subject (for example: 'friendlyName: CIMOM Certificate')
Example:
EDTF STMF('/home/carmack/testservercert_pass.pem')
Note: May see 2 certificate sections. One is like "friendlyName: LOCAL_CERTIFICATE_AUTHORITY_XXX", and other is like "friendlyName: testcert" where testcert is the name you used when created it. That section is the one that should keep.
From the EDTF screen, put a 'DD' at the first line and a 'DD' the line before the second "BEGIN CERTIFICATE" section.
Also, put a 'DD' the line after the "END CERTIFICATE" for the second section and a 'DD' at the end of the file.
Hit enter and will delete all the lines between 'DDs' keeping the section needed.
Press F3 twice to save the changes.

Note: Not all the information is displayed. It's just for example purpose.
11. From IBM i command line, copy testca_nopass.pem to testprivkey_nopass.pem to extract the unencrypted private keys from the PEM file.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testca_nopass.pem') TOOBJ('/home/carmack/testprivkey_nopass.pem')
12 Edit testprivkey_nopass.pem and delete all the lines except the lines starting at "-----BEGIN PRIVATE KEY-----" and ending at "-----END PRIVATE KEY-----"
Example:
EDTF STMF('/home/carmack/testprivkey_nopass.pem')
From the EDTF screen, put a 'DD' at the first line and a 'DD' the line before "BEGIN PRIVATE KEY" section. Hit enter and will delete all the lines between 'DDs'
Press F3 twice to save the changes.

Note: Not all the information is displayed. It's just for example purpose.
13. From IBM i command line, copy testca_nopass.pem to testservercert_nopass.pem to extract the unencrypted server certificate issued by the CA from the PEM file.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testca_nopass.pem') TOOBJ('/home/carmack/testservercert_nopass.pem')
14. Edit testservercert_nopass.pem and delete all the lines except the second certificate section lines starting at "-----BEGIN CERTIFICATE-----" and ending
at "-----END CERTIFICATE-----" for the certificate with CIM Server as the subject (for example: 'friendlyName: CIMOM Certificate')
Example:
EDTF STMF('/home/carmack/testservercert_nopass.pem')
Note: May see 2 certificate sections. One is like "friendlyName: LOCAL_CERTIFICATE_AUTHORITY_XXX", and other is like "friendlyName: testcert" where testcert is the name you used when created it. That section is the one that should keep.
From the EDTF screen, put a 'DD' at the first line and a 'DD' the line before the second "BEGIN CERTIFICATE" section.
Also, put a 'DD' the line after the "END CERTIFICATE" for the second section and a 'DD' at the end of the file.
Hit enter and will delete all the lines between 'DDs' keeping the section needed.
Press F3 twice to save the changes.

Note: Not all the information is displayed. It's just for example purpose.
Now should have the following 7 files in your directory:
testca_nopass.pem - has the CA certificate, server certificate issued by the CA, and the associated unencrypted private key
testca_pass.pem - has the CA certificate, server certificate issued by the CA, and the associated encrypted private key
testcert.p12 - the one exported from DCM
testprivkey_nopass.pem - has the unencrypted private key associated with testservercert_pass.pem
testprivkey_pass.pem - has the encrypted private key associated with testservercert_pass.pem
testservercert_nopass.pem - has the server certificate issued by the CA, associated with the unencrypted private key
testservercert_pass.pem - has the server certificate issued by the CA, associated with the encrypted private key.
7) Use the private key and certificate for CIMOM server
7) Use the private key and certificate for CIMOM server
Note: The private key and certificate which CIMOM server auto create itself are unencrypted. So following steps are for using the unencrypted files created on previous steps ( testprivkey_nopass.pem and testservercert_nopass.pem) Steps to use the encrypted private key and certificate are the same, just use the other files created (testprivkey_pass.pem and testservercert_pass.pem
1. From IBM i command line, end CIMOM server:
ENDTCPSVR *CIMOM
2. From IBM i command line, copy the testservercert_nopass.pem to UME directory, /QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testservercert_nopass.pem') TODIR('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore')
3. From IBM i command line, copy the testprivkey_nopass.pem to UME directory, /QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore.
Example:
Type CPY and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used CPY OBJ('/home/carmack/testprivkey_nopass.pem') TODIR('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore')
4. From IBM i command line, delete the old servercert.pem under UME directory.
Example:
Type RMVLNK and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used RMVLNK OBJLNK('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore/servercert.pem')
5. From IBM i command line, delete the serverkey.pem under UME directory, \QOpenSys\QIBM\UserData\UME\Pegasus\ssl\keystore.
Example:
Type RMVLNK and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used RMVLNK OBJLNK('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore/serverkey.pem')
6. From IBM i command line, rename testservercert_nopass.pem to servercert.pem under UME directory.
Example:
Type RNM and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used RNM OBJ('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore/testservercert_nopass.pem') NEWOBJ('servercert.pem')
7. From IBM i command line, rename testprivkey_nopass.pem to serverkey.pem under UME directory.
Example:
Type RNM and press F4 to prompt. Fill the information as follow and hit Enter:

Note: Used RNM OBJ('/QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore/testprivkey_nopass.pem') NEWOBJ('serverkey.pem')
8. From IBM i command line, start CIMOM server:
STRTCPSVR *CIMOM
9. To view and verify that the files created were assigned correctly to the CIMOM server, run the following command on PASE environment (CALL QP2TERM)
Run:
openssl x509 -in /QOpenSys/QIBM/UserData/UME/Pegasus/ssl/keystore/servercert.pem -noout -text

Scroll up to the to and check that the certificate attributes match what entered into DCM (especially, the subject, issuer, key length and validity dates)
[{"Type":"MASTER","Line of Business":{"code":"LOB57","label":"Power"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"SWG60","label":"IBM i"},"ARM Category":[{"code":"a8m0z0000000COrAAM","label":"CIMOM Server"}],"ARM Case Number":"","Platform":[{"code":"PF012","label":"IBM i"}],"Version":"7.2.0;7.3.0;7.4.0"}]
Was this topic helpful?
Document Information
Modified date:
28 July 2022
UID
nas8N1022274