
- Security Services and Remediation
- Security Assessments
- Assets and Tools
- Current Asset Versions
- Compliance Automation Reporting Tool (CART)
- Team Members
- Upload Data to our Team
- Statement of Good Security Practices
- IBM PowerSC
- IBM i Security Documentation
- IBM i Security Enhancements
- IBM i Security with SQL Services
Learn about Ransomware and IBM i with our Security Thought Leader Robert Andrews!
In order to develop a proper baseline, the IBM i Security Assessment (Video Intro) scans your system for a wide range of security settings and risks. Our review of the core operating system, settings, user profiles, and permissions include:
- Investigate privileged user profiles, command line access, and other significant aspects of the user profiles on the system
- Investigate password practices
- Investigate the use of Group Profiles and Authorization Lists
- Analyze the use of adopted authority and profile swapping
- Examine communications and TCP/IP exposures (Open Ports and Exit Points)
- Examine current system value settings
- Examine current System Service Tools (SST) security settings
- Examine the subsystem descriptions, job descriptions, output queues, and job queues
- Analyze access control for Library system objects
- Analyze access control for IFS directories
- Analyze file shares for ransomware exposure
- Examine current Security PTF levels and determine whether CUSTOMER is within those current levels
- Document the findings and recommendations for securing the system based on findings
- Examine the IBM i auditing and logging practices used by CUSTOMER and provide recommendations for improvement if determined to be insufficient
- Review user, programmer, and admin access to data from application
- Recommend application security design or changes to meet security requirements
- Provide recommendations on proper development security best practices
- Syslog Reporting Manager [Manual] [Video Demo] [Download]
- Single Sign On (SSO) Suite [EPT Manual] [Video Demo] [Download (password required)]
- Certificate Expiration Manager [Manual] [Download]
*Note: All assets have a cost associated with them!! While you are able to download the code and user guides, these assets do not work without a purchased licensed key. To inquire, get a quote, or purchase assets, contact Ron Bibby at ronbibby@us.ibm.com.
On January 1, 2026, the IBM i Security Expert Labs team withdrew from marketing (WFM) the following assets:
- Compliance Automation Reporting Tool (CART) [Presentation] [Video Demo] [Download]
- Compliance Automation Reporting Tool (CART) Express [Presentation] [Download]
- Advanced Authentication (formerly Multi Factor Authentication) [Manual] [Video Demo] [Download]
- Network Firewall (Exit Point Security) [Manual] [Video Demo] [Download]
- Privileged Elevation Tool (Fire Call) [Manual] [Video Demo] [Download]
This means that no new purchases of these assets are possible. Any existing software maintenance (SWMA) contracts will be honored until their current end date. Any SWMA contracts expiring by December 31, 2026, will be able to renew for one additional year only. The end of support (EOS) for all these assets will be at the end of the SWMA contract, but no later than December 31, 2027. All support for these assets will end on December 31, 2027. This gives our existing clients two years to determine how they would like to proceed.
For clients looking for a general IBM i Security and Compliance tool, please consider using IBM PowerSC or the tools built into IBM Navigator for i. For prior CART clients and those with large and complex IBM i enterprises, Expert Labs recommends moving to IBM Database Expert Orchestrate for i featuring Expert Query. For clients looking to implement MFA on IBM i, please move to the no cost integrated MFA features introduced in IBM i 7.6. For specific tactical needs such as exit point application firewalls and privilege elevation tools, please contact one of the many IBM i Security Business Partners (BPs) which have many offerings in this space.
All existing assets will continue to work in their current form on the currently supported operating systems (up to IBM i 7.6). There are no plans to enhance or build versions of these tools that are compatible with future versions of the OS. Licenses purchased are perpetual and will still be valid. Expert Labs does have the ability to generate new license keys for new serial numbers if a client has already purchased these assets. Contact systems-expert-labs@ibm.com if you need a new key for existing licenses.
For a list of the current versions of the Security and Compliance Tools for IBM i, click here.
- Compliance Automation Reporting Tool (CART)
- Syslog Reporting Manager (SRM)
- Network Interface Firewall (XPT)
- Privileged Elevation Tool (FIRECALL)
- Advanced Authentication (formerly Multi-Factor Authentication)
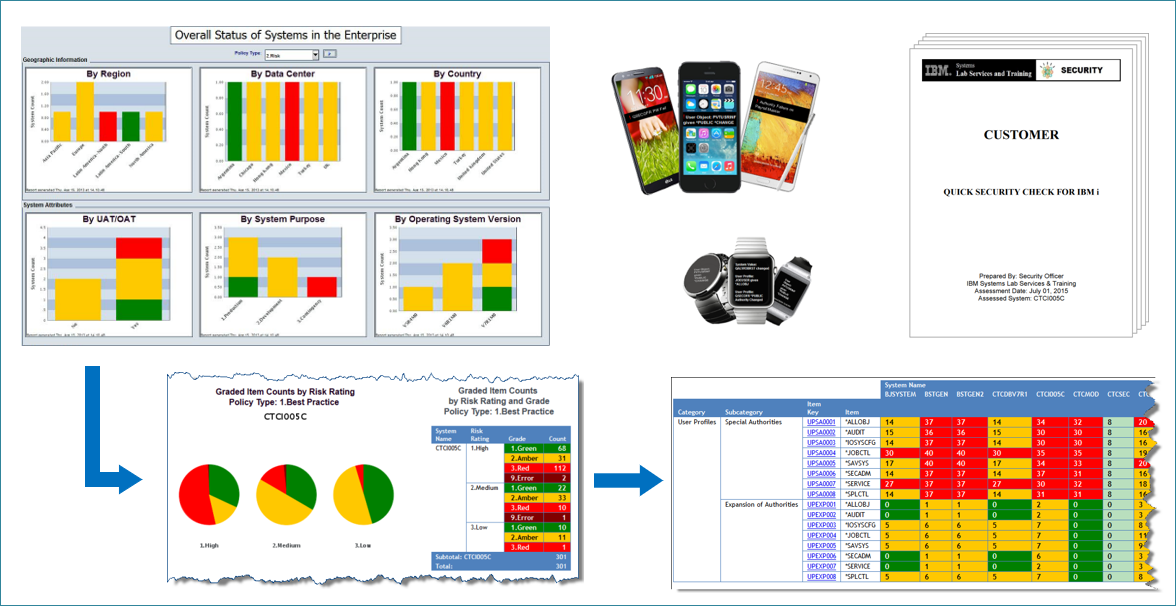
- Special Authorities / Inherited Privileges
- Group Profiles / Ambiguous Profiles
- Default Passwords / Password Expiration
- Inactive Accounts
- *PUBLICly Authorized Profiles
- Privately Authorized Profiles
- Initial Programs, Menus, and Attention Programs
- Command Line Access
- System Values / Audit Control Settings
- Invalid Signon attempts
- Work Management Analysis
- Service Tools (SST) Security
- DDM Password Requirements
- Registered Exit Points / Exit Programs
- Function Usage
- Library Analysis / *ALLOBJ Inheritance
- PTF Currency
- Customer Defined Events and Items
- CPU/DASD Utilization and Availability
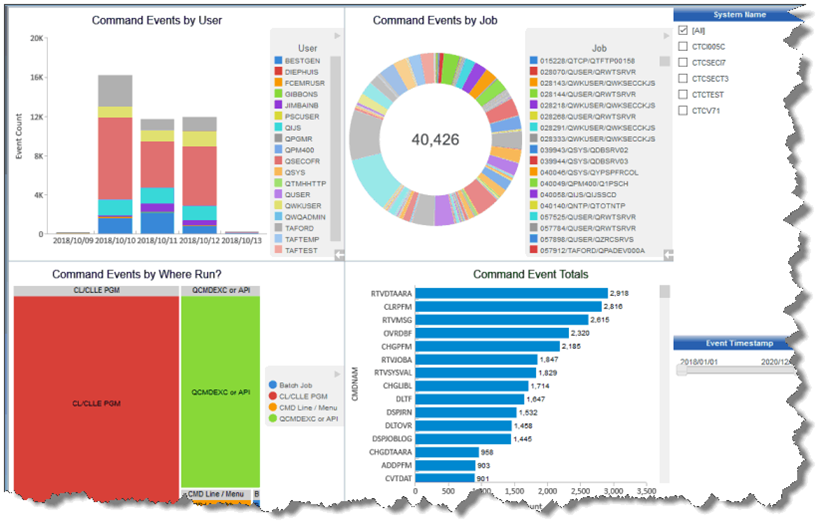
- Actionable Security Events in near real time!
- Network attributes / Time Server
- NetServer Configuration
- TCP/IP servers / Autostart values
- Digital Certificate Expiration
- SNMP / SSH / SSL Configuration
- Listening ports / Network Encryption
- IP Datagram Forwarding
- IP Source Routing
- APPN Configuration
- Server Authentication Entries
Read more about CART in this article.
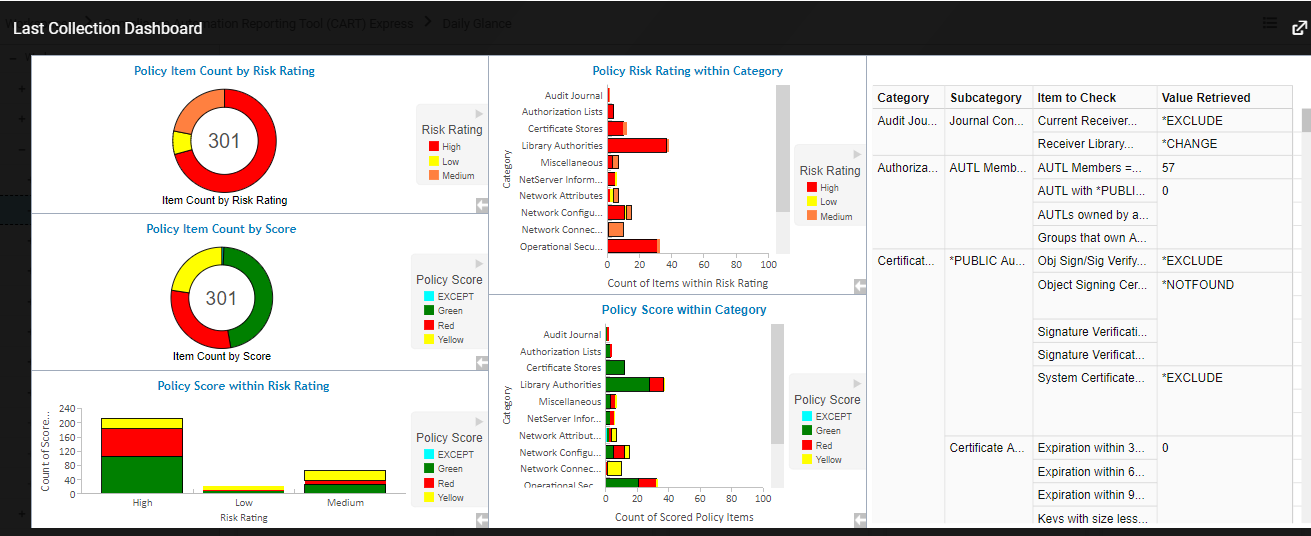
Auditing Changes (AD)
- ATADA001 - CHGUSRAUD changed AUDLVL of Profile to *NONE
Authority Failures (AF)
- ATAFA001 - Not authorized to Object
- ATAFA002 - Restricted Instruction
- ATAFA003 - Validation Failure
- ATAFA004 - Use of Unsupported Interface
- ATAFA005 - HW STG Protection Error
- ATAFA006 - ICAPI Authorization Error
- ATAFA007 - ICAPI Authentication Error
- ATAFA008 - Scan Exit PGM Action
- ATAFA009 - Java Inheritance not Allowed
- ATAFA010 - SBMJOB Profile Error
- ATAFA011 - Special Authority Violation
- ATAFA012 - Profile Token not a Regenerable Token
- ATAFA013 - Optical Object Authority Failure
- ATAFA014 - Profile Swap Error
- ATAFA015 - Hardware Protection Error
- ATAFA016 - Default Sign-on Attempt
- ATAFA017 - Not authorized to TCP/IP port
- ATAFA018 - User Permission Request not Valid
- ATAFA019 - Profile Token not Valid for Creating New Token
- ATAFA020 - Profile Token not valid for Swap
- ATAFA021 - System Violation
- ATAFA022 - Not Authorized to JUID During JUID CLEAR
- ATAFA023 - Not Authorized to JUID During JUID SET
Authority Changes (CA)
- ATCAA001 - *PUBLIC Authority on Profile <> *EXCLUDE
- ATCAA002 - Private Authority on Profile Granted
Profile Creates / Changes (CP)
- ATCPA001 - CHGUSRPRF PWD by Self does not conform to *SYSVAL
- ATCPA002 - CHGUSRPRF PWD by Self does not conform to *EXITPGM
- ATCPA003 - CxxUSRPRF used to set PWD Expiry to *NOMAX
- ATCPA004 - CxxUSRPRF used to give *ALLOBJ privilege
- ATCPA005 - CxxUSRPRF used to give *JOBCTL privilege
- ATCPA006 - CxxUSRPRF used to give *SAVSYS privilege
- ATCPA007 - CxxUSRPRF used to give *SECADM privilege
- ATCPA008 - CxxUSRPRF used to give *SPLCTL privilege
- ATCPA009 - CxxUSRPRF used to give *SERVICE privilege
- ATCPA010 - CxxUSRPRF used to give *AUDIT privilege
- ATCPA011 - CxxUSRPRF used to give *IOSYSCFG privilege
- ATCPA012 - CHGUSRPRF sets QSECOFR as Group Profile
- ATCPA013 - CxxUSRPRF gives Profile full CMD Line ability
- ATCPA014 - CxxUSRPRF sets Profile as *SECOFR class
- ATCPA015 - Initial Menu *SIGNOFF & LMTCPB *NE *YES
- ATCPA016 - Initial Program QCMD & LMTCPB *NE *YES
- ATCPA017 - QSECOFR Password Reset using DST
- ATCPA018 - PWD Expired not set on CRTUSRPRF
LDAP-Related (DI)
- ATDIA001 - LDAP Authority Failure
- ATDIA002 - LDAP Password Change
- ATDIA003 - LDAP Password Failure
System Environment Variable Changes (EV)
- ATEVA001 - Environment Variable Change
Exit Point Changes (GR)
- ATGRA001 - Exit Point Program Added
- ATGRA002 - Exit Point Program Deleted
- ATGRA003 - Exit Point Program Replaced
Function Changes (GR)
- ATGRB001 - Function Usage Changed
- ATGRB002 - Function De-Registered
- ATGRB003 - Function Updated
Network ATTR Change (NA)
- ATNAA001 - Network Attribute Change
- ATNAB001 - TCP/IP Attribute Change
Change PGM to Adopt (PA)
- ATPAA001 - Program set to ADOPT *OWNER Authority
Passwords Fails > 5 (PW)
- ATPWA001 - APPC BIND Failure
- ATPWA002 - User AUTH with CHKPWD Failure
- ATPWA003 - Service Tools USERID Name not valid
- ATPWA004 - Service Tools USERID PWD not valid
- ATPWA005 - Password not valid
- ATPWA006 - SIGNON Failed - Profile disabled
- ATPWA007 - SIGNON Failed - User PWD expired
- ATPWA008 - SQL Decryption PWD not valid
- ATPWA009 - User Name not valid
- ATPWA010 - Service Tools USERID disabled
- ATPWA011 - Service Tools USERID not valid
- ATPWA012 - Service Tools USERID PWD not valid
- ATPWx013 - PASSWORD FAILURE UNKNOWN - x
Journal Receiver Deleted (RD)
- AJRDA001 - A QAUDJRN Journal Receiver was Deleted
Restore Adopt PGMs (RP)
- ATRPA001 - Program that adopts *OWNER restored
Service Tools Use (ST)
- ATSTA001 - STG changed by Display/Alter/Dump used
- ATSTA002 - STRCPYSCN used
- ATSTA003 - DMPDLO used
- ATSTA004 - DMPMEMINF used
- ATSTA005 - DMPOBJ used
- ATSTA006 - DMPSYSOBJ, QTADMPTS, QTADMPDV, or QWTDMPLF used
- ATSTA007 - DMPUSRPRF used
- ATSTA008 - Operations Console used
- ATSTA009 - STRCMNTRC or QSCCHGCT used
- ATSTA010 - STRRMTSPT used
- ATSTA011 - STRSST used
- ATSTA012 - TRCTCPAPP used
- ATSTA013 - TRCINT or TRCCNN w/ SET(ON/OFF/END) used
- ATSTA014 - STRTRC, STRPEX, or TRCJOB(*ON) used
- ATSTA015 - Change to System Value Lock
System Value Changes (SV)
- ATSVA001 - QALWOBJRST changed
- ATSVA002 - QALWUSRDMN changed
- ATSVA003 - QAUDCTL changed
- ATSVA004 - QAUDENDACN changed
- ATSVA005 - QAUDFRCLVL changed
- ATSVA006 - QAUDLVL changed
- ATSVA007 - QAUDLVL2 changed
- ATSVA008 - QCRTAUT changed
- ATSVA009 - QCRTOBJAUD changed
- ATSVA010 - QDSPSGNINF changed
- ATSVA011 - QFRCCVNRST changed
- ATSVA012 - QINACTITV changed
- ATSVA013 - QINACTMSGQ changed
- ATSVA014 - QLMTDEVSSN changed
- ATSVA015 - QLMTSECOFR changed
- ATSVA016 - QMAXSGNACN changed
- ATSVA017 - QMAXSIGN changed
- ATSVA018 - QPWDCHGBLK changed
- ATSVA019 - QPWDEXPITV changed
- ATSVA020 - QPWDEXPWRN changed
- ATSVA021 - QPWDLMTAJC changed
- ATSVA022 - QPWDLMTCHR changed
- ATSVA023 - QPWDLMTREP changed
- ATSVA024 - QPWDLVL changed
- ATSVA025 - QPWDMAXLEN changed
- ATSVA026 - QPWDMINLEN changed
- ATSVA027 - QPWDPOSDIF changed
- ATSVA028 - QPWDRQDDGT changed
- ATSVA029 - QPWDRQDDIF changed
- ATSVA030 - QPWDRULES changed
- ATSVA031 - QPWDVLDPGM changed
- ATSVA032 - QRETSVRSEC changed
- ATSVA033 - QRMTSIGN changed
- ATSVA034 - QSCANFS changed
- ATSVA035 - QSCANFSCTL changed
- ATSVA036 - QSECURITY changed
- ATSVA037 - QSHRMEMCTL changed
- ATSVA038 - QSSLCSL changed
- ATSVA039 - QSSLCSLCTL changed
- ATSVA040 - QSSLPCL changed
- ATSVA041 - QUSEADPAUT changed
- ATSVA042 - QVFYOBJRST changed
- ATSVA043 - QALWJOBITP changed
- ATSVA044 - QALWUSRDMN changed
- ATSVA045 - QASTLVL changed
- ATSVA046 - QATNPGM changed
- ATSVA047 - QAUTOCFG changed
- ATSVA048 - QAUTORMT changed
- ATSVA049 - QAUTOVRT changed
- ATSVA050 - QCTLSBSD changed
- ATSVA051 - QDSCJOBITV changed
- ATSVA052 - QENDJOBLMT changed
- ATSVA053 - QHSTLOGSIZ changed
- ATSVA054 - QIPLDATTIM changed
- ATSVA055 - QIPLSTS changed
- ATSVA056 - QIPLTYPE changed
- ATSVA057 - QLIBLCKLVL changed
- ATSVA058 - QLOGOUTPUT changed
- ATSVA059 - QMLTTHDACN changed
- ATSVA060 - QPASTHRSVR changed
- ATSVA061 - QPFRADJ changed
- ATSVA062 - QPRBFTR changed
- ATSVA063 - QPRBHLDITV changed
- ATSVA064 - QPRCFEAT changed
- ATSVA065 - QPRCMLTTSK changed
- ATSVA066 - QPRTDEV changed
- ATSVA067 - QPWRDWNLMT changed
- ATSVA068 - QPWRRSTIPL changed
- ATSVA069 - QQRYDEGREE changed
- ATSVA070 - QQRYTIMLMT changed
- ATSVA071 - QRCLSPLSTG changed
- ATSVA072 - QRMTIPL changed
- ATSVA073 - QRMTSRVATR changed
- ATSVA074 - QSAVACCPTH changed
- ATSVA075 - QSCPFCONS changed
- ATSVA076 - QSETJOBATR changed
- ATSVA077 - QSFWERRLOG changed
- ATSVA078 - QSPCENV changed
- ATSVA079 - QSPLFACN changed
- ATSVA080 - QSRTSEQ changed
- ATSVA081 - QSRVDMP changed
- ATSVA082 - QSTGLOWACN changed
- ATSVA083 - QSTGLOWLMT changed
- ATSVA084 - QSTRPRTWTR changed
- ATSVA085 - QSTRUPPGM changed
- ATSVA086 - QSTSMSG changed
- ATSVA087 - QSVRAUTITV changed
- ATSVA088 - QSYSLIBL changed
- ATSVA089 - QTHDRSCADJ changed
- ATSVA090 - QTHDRSCAFN changed
- ATSVA091 - QTIMADJ changed
- ATSVA092 - QUPSDLYTIM changed
- ATSVA093 - QUPSMSGQ changed
- ATSVA094 - QUSRLIBL changed
- ATSVA095 - QUTCOFFSET changed
User-Defined Events being Monitored
- UExxy001 - Journal Entries issued on Objects or Users based upon the following journal types: AD,AF,AX,CA,CO,DO,JD,OM,OR,OW,PA,PG,RA,RJ,RO,RP,RZ,SE,ZC,ZR
- Also, for User checks: CD,CP,DS,PS,PW,RU,SO,ST
- Interface LOGON
- Subsystem Active monitoring
Web Query Withdrawn from Marketing… Now What?
- Robert Andrews, Principal Security Consultant / STSM, Team Lead, IBM i Security Expert Labs
- Terry Ford, Team Lead, IBM i Security and Remediation Expert Labs
- Thomas Barlen, European consultant
- Santiago Nunez, Latin America consultant
- Jesus Haro, Latin America consultant
- Jason Tan, Asia Pacific consultant
- Ron Bibby, Contracts and Opportunities
- General IBM Expert Labs Contact