IBM i configuration objects for integrated servers
IBM® i uses objects to represent and control integrated server hardware, software, and virtual storage.
The following figure shows the objects that IBM i (IBM i) uses to configure iSCSI-attached integrated servers.
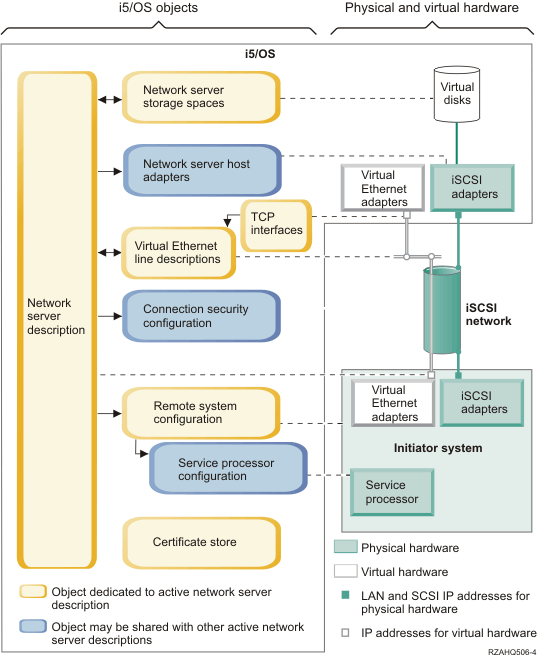
Network server description
The network server description (NWSD) object is the main configuration object for an integrated server.
- It contains a reference to a remote system configuration.
- It contains references to the iSCSI and virtual Ethernet data
paths for the integrated server.
- You can define one or more storage paths. These storage paths reference the network server host adapter (NWSH) objects that are associated with the iSCSI target adapters that are used by the integrated server. You can choose which storage path is used for the SCSI data flows for each virtual disk drive. By associating your virtual disk drives with different storage paths, you can spread the overall server SCSI data flow workload across the storage path iSCSI target adapters for greater bandwidth. See Multipath I/O for integrated servers.
- You can define one or more virtual Ethernet paths. These virtual Ethernet paths also reference the NWSH objects that are used by the integrated server. You can choose which NWSH is used for each virtual Ethernet port that the integrated server uses. By associating different virtual Ethernet ports with different NWSHs, you can spread the overall server virtual Ethernet data flow workload across the virtual Ethernet path iSCSI target adapters for greater bandwidth.
- The iSCSI-attached System
x or BladeCenter hardware is controlled
by IBM i.
- An iSCSI-attached server is turned on and off by starting or stopping the NWSD for that server.
- IBM i uses an Ethernet network to communicate with the service processor for the System x hardware or the BladeCenter management module for a BladeCenter server to perform the start and shut down tasks.
Note: In case of a hardware failure, you can change the remote system configuration name that is specified in the NWSD and restart the server using spare hardware. See Hot spare support for integrated servers.
Network server host adapters
A network server host adapter (NWSH) device description object represents the iSCSI target adapter that is used by the IBM i side of the iSCSI connection.- It identifies the iSCSI target adapter port.
- For a hardware target (iSCSI HBA), it identifies the IBM i Network Server Host Port resource name (for example, CMNxx) for the iSCSI HBA port.
- For a software target (Ethernet NIC), the NWSH uses a virtual port and also identifies the IBM i TCP/IP interface that is associated with the line description for the Ethernet NIC port.
- It defines how communications errors are logged and communications recovery information.
- It defines the IP addresses, ports, and so on. for the SCSI and LAN interfaces on the iSCSI target adapter.
IBM i can have multiple iSCSI target adapters. Each port on an iSCSI target adapter has an associated NWSH object.
- Each NWSH can be shared by multiple integrated servers. In configurations where bandwidth is not a concern, this results in a lower-cost solution.
- Each integrated server can use multiple NWSHs. Multiple NWSHs allow multiple SCSI and virtual Ethernet data paths between IBM i and the System x or blade system. Multiple NWSHs can provide greater bandwidth and connection redundancy.
An iSCSI target adapter is started and stopped using the NWSH for that iSCSI target adapter.
- Alternatively, a software target (Ethernet NIC) can be started and stopped using the TCP/IP interface that is associated with the NWSH. The NWSH and the associated TCP/IP interface are started and stopped together.Notes:
- Do not use the same TCP/IP interface for multiple NWSHs. Only one NWSH that uses a particular TCP/IP interface can be active at a time.
- When starting a software target, the associated line description (LIND) is also started. However, when stopping a software target, the associated LIND remains active.
Remote system configuration
The remote system network server configuration (NWSCFG type RMTSYS) contains information that identifies the integrated server hardware to IBM i.
- It identifies the server hardware by serial number and type and model.
- It contains configuration information for the iSCSI initiator adapters that are used by the System x or blade hardware.
- It contains values required to boot the server.
- It contains a reference to the service processor NWSCFG object that is used to control the System x or blade hardware.
- It contains challenge handshake authentication protocol (CHAP) configuration values that are used to authenticate the remote system when it initially accesses storage.
The System x or blade server can have multiple iSCSI initiator adapters. Multiple iSCSI initiators allow multiple SCSI and virtual Ethernet data paths between IBM i and the System x or blade hardware. Multiple iSCSI initiators can provide greater bandwidth and connection redundancy.
The remote system configuration for an integrated server is referenced from the NWSD.
Service processor configuration
A service processor network server configuration (NWSCFG type SRVPRC) represents the System x service processor or the BladeCenter management module.
The service processor configuration contains the following information:
- It identifies the service processor or management module hardware by serial number and type and model.
- It defines how to find the service processor or management module on the Ethernet network using an IP address or host name.
- It contains a service processor user name and password that are used to sign on to the service processor.
Connection security configuration
A connection security network server configuration (NWSCFG type CNNSEC) is used by the system. The integrated server installation process normally creates a default connection security configuration named QCNNSEC that is shared by all integrated servers on the IBM i system.
Certificate stores
Certificates are used to secure communications between IBM i and the initiator system for various functions. The certificates are kept in the following IBM i certificate store:
- A certificate store that is associated with the network server description.
- This certificate store is created and maintained automatically for you. It is used to store certificates that are generated and used internally by the IBM i Integrated Server Support. For example, certificates that are used when enrolling users to the hosted system. The certificates in this certificate store are used only when communicating with hosted systems that use the corresponding network server description.
Network server storage spaces (virtual storage)
A network server storage space (NWSSTG) represents a virtual disk drive (virtual storage) for an integrated server. Virtual storage can vary in size from 1 MB to 1000 GB each. Up to 64 virtual storage spaces can be linked to a server, depending on the server configuration. The storage capacity of an integrated server can range from several gigabytes to many terabytes. The virtual storage spaces are first created as stand-alone objects and then linked to the integrated server by identifying the NWSD of the integrated server that uses them.
- The system drive (typically the C: drive for Windows servers) contains the integrated server operating system (such as Windows Server or VMware ESX Server).
- For integrated Windows servers, the installation drive is used every time the server is started to pass configuration information from IBM i to the server. It also contains the IBM i Integrated Server Support (5770-SS1 option 29) code that runs on the Windows server. For Windows Server 2003 servers, the installation drive also contains a copy of the Windows server installation media.
- Additional user-defined drives are typically used for server applications and data.
- When linking the virtual disk drive to the NWSD, it is necessary to identify which of the NWSD storage paths to use for the SCSI data flows for that virtual disk drive. You can choose a specific storage path, the multipath group or let the default storage path be used.
The actual disk storage for the virtual disks is allocated from the IBM i integrated file system. The virtual disk drives can be allocated from the default system storage pool (also known as the system auxiliary storage pool, or system ASP), from a user-defined storage pool, or from an independent storage pool (independent ASP).
See Storage management for integrated servers for more information about virtual storage.
- Since virtual disks are objects in the IBM i integrated file system, an entire virtual disk drive image can be backed up and restored using the IBM i Save (SAV) and Restore (RST) commands. You can also do a file-level backup for the Windows operating system. For more information, see Backing up and recovering integrated servers.
- Even though storage spaces are allocated out of the integrated file system, storage operations are not performed by IFS while the integrated server is varied on. Therefore, operations like journaling are not enabled.
