Tutorial: Implementing OAuth Security
This tutorial shows you how to create a native OAuth provider using API Manager.
About this tutorial
In this tutorial you will complete the following lessons:
Before you begin
In this tutorial you will implement and test OAuth security. To complete this tutorial, you must have the following available:
- An existing published API. If you do not have an API available, complete the Tutorial: Importing an API tutorial.
- An existing client application. If you do not have a client application available, complete Tutorial: Creating a Client Application.
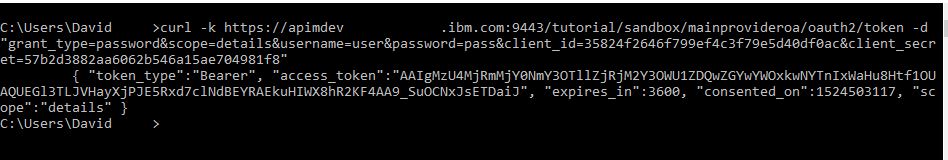
- An external application, such as cURL, used to send requests to the OAuth token provider endpoint.
Note: The Sandbox catalog must be configured to use either a DataPower® Gateway (v5
compatible) or a DataPower API
Gateway or both. See Creating and configuring Catalogs.
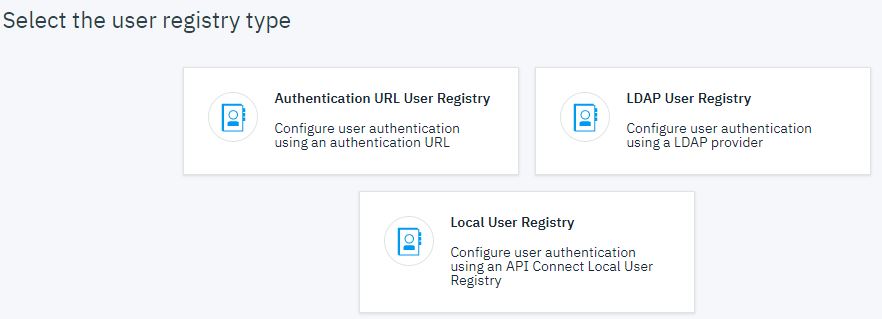
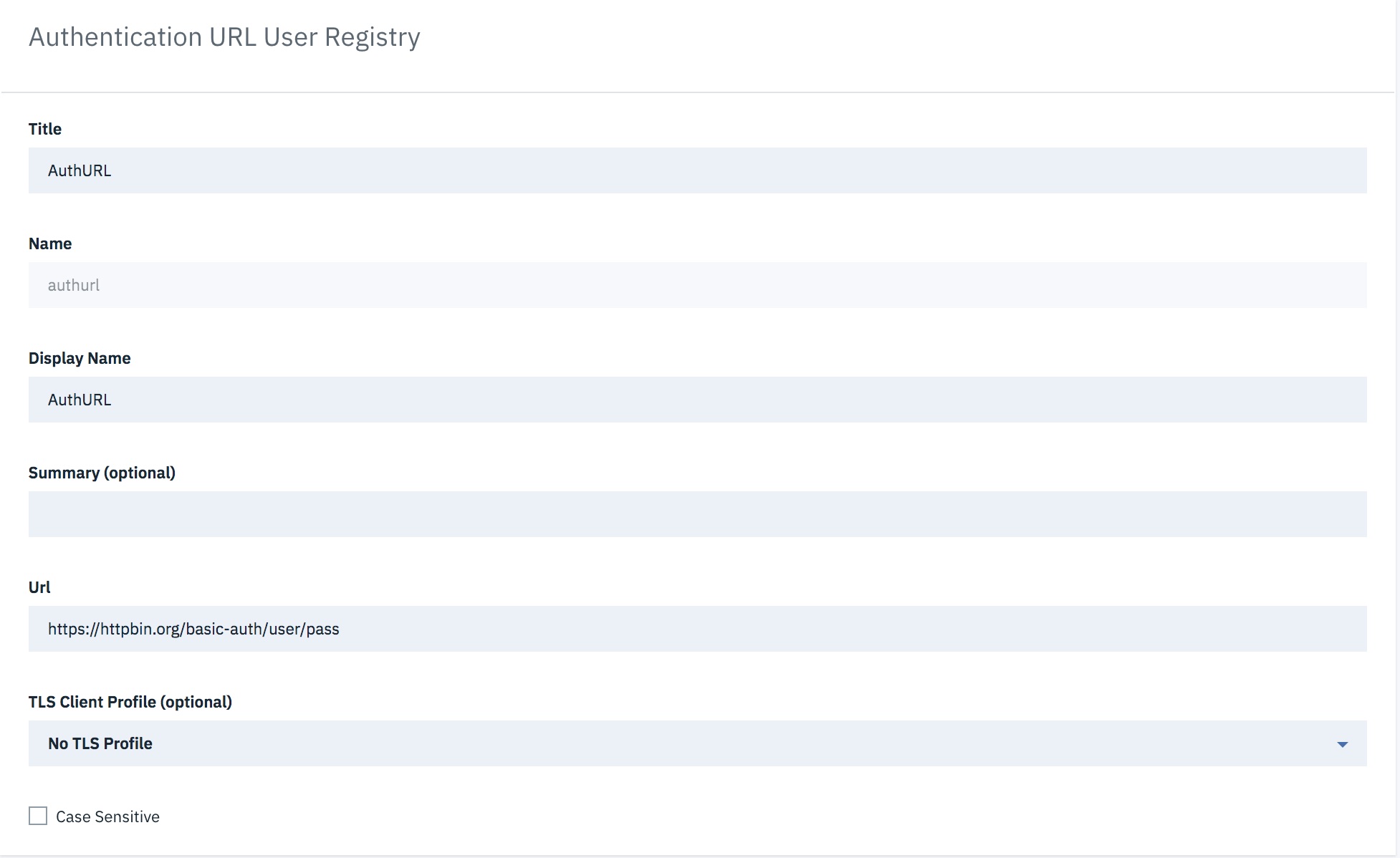
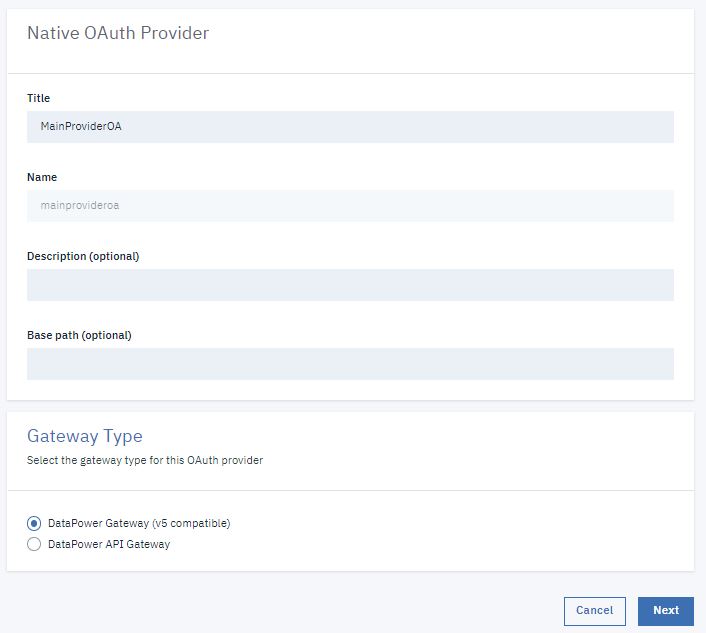
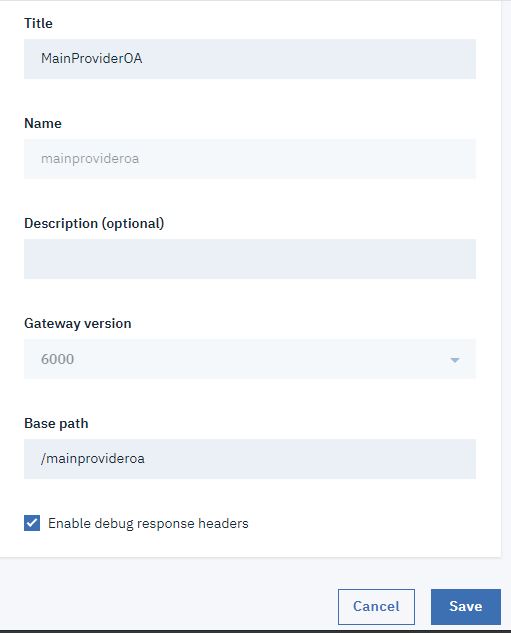
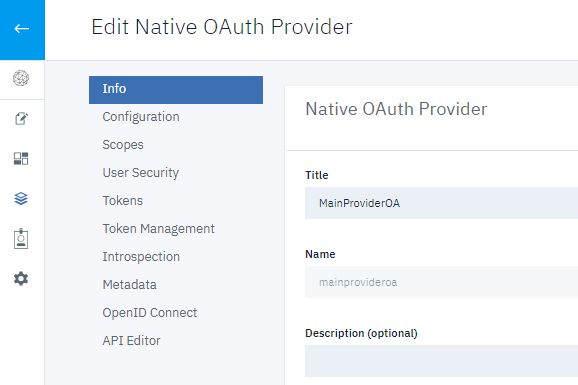
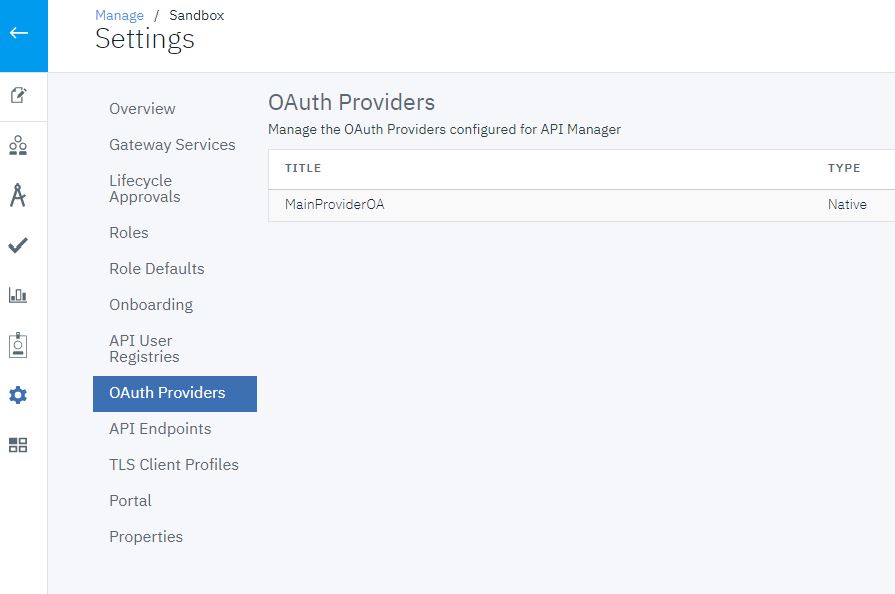
Create a Native OAuth Provider
To create a native OAuth provider by using API Manager, complete the following steps:
Verify or create test application credentials
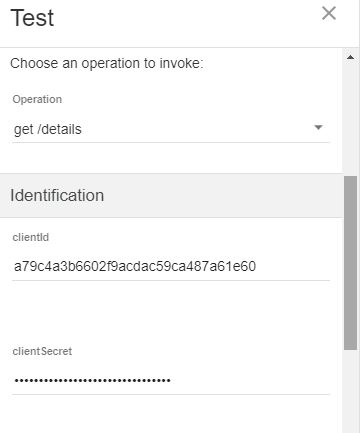
You will need the client ID and client secret for an application to test the OAuth functionality. You obtained this information during the
completion of the Tutorial: Creating a Client Application tutorial listed in the Prerequisites.
Note: These steps are necessary only if you did not make note of the credentials for the client application you previously created.
- Click the Applications icon
 in the side bar.
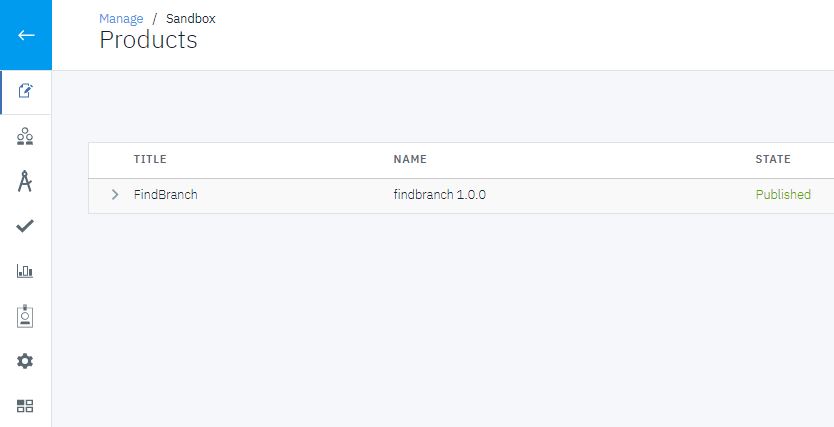
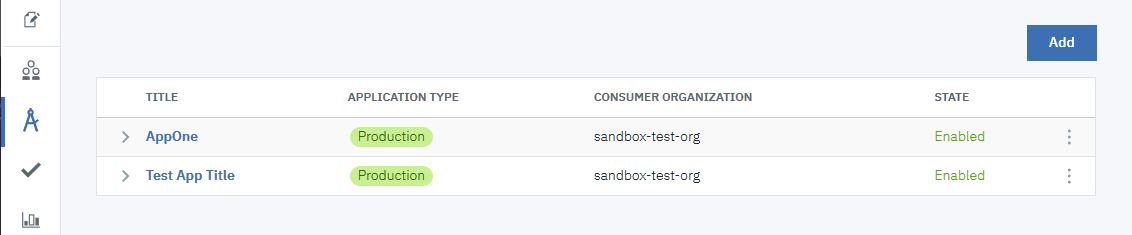
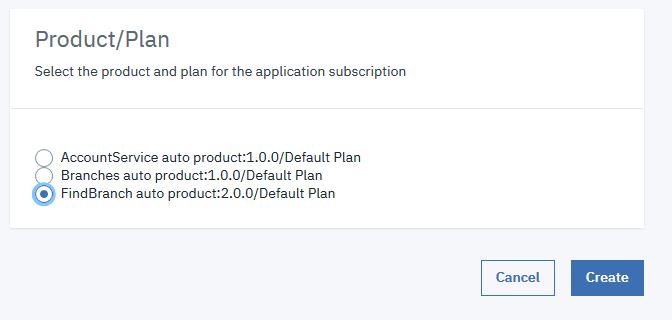
in the side bar. - Click the Down arrow icon alongside the AppOne
application. The findbranch product should be listed.
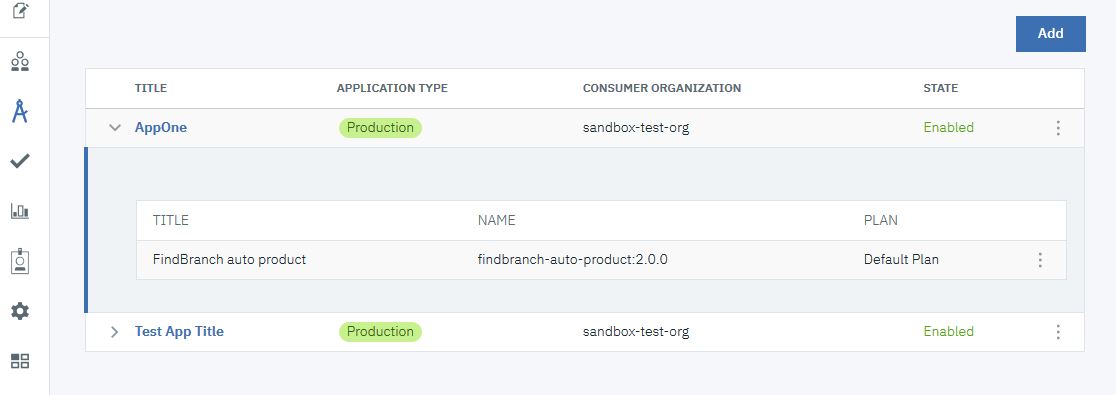
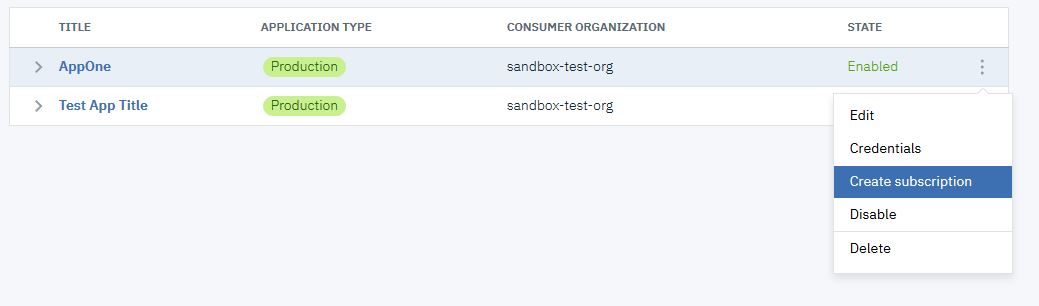
- Click the Options icon
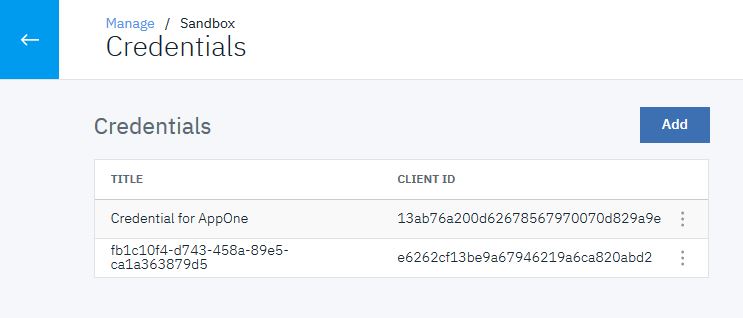
 alongside AppOne. Select Credentials.
alongside AppOne. Select Credentials.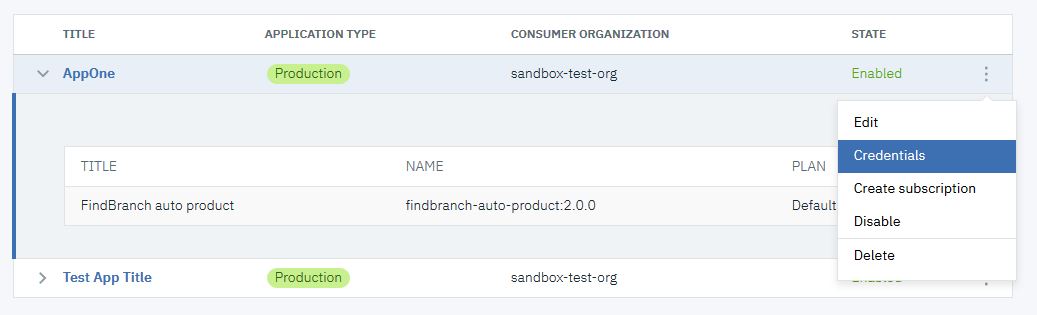
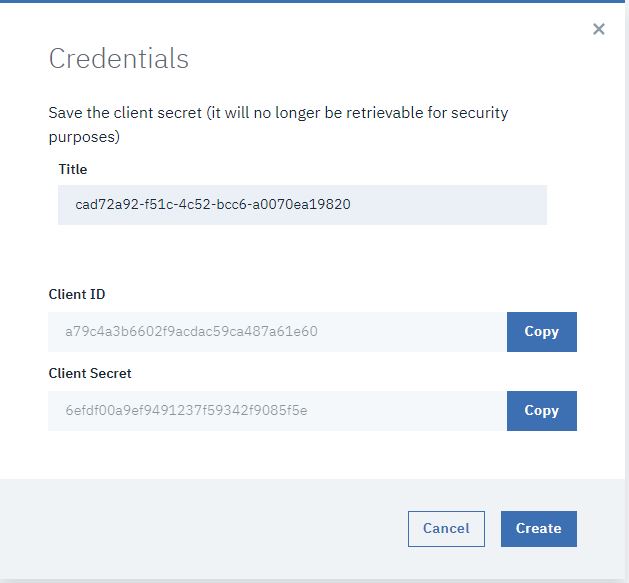
- Click Add.
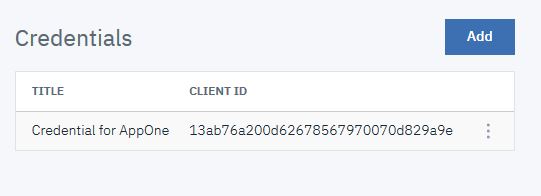
- Copy both the Client ID and client Secret. You will need these values to obtain an OAuth token.
Click Create.
- Click the Back arrow until you see the Manage page.
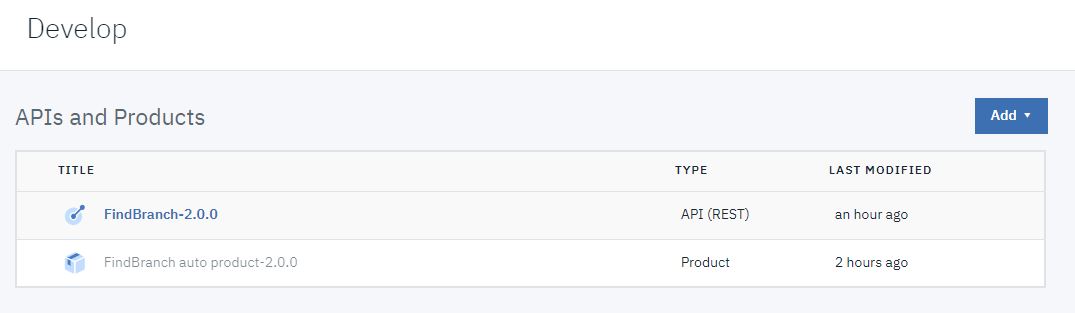
- Click Develop
 in the side bar.
in the side bar.
Adding OAuth Security to an API
You add OAuth security enforcement to an existing API by creating a security definition for OAuth and
then including that definition in the security applied to the API. Follow these steps.
- Click the existing API to which you want to add OAuth security. This tutorial uses the
FindBranch API. Note: The gateway type used by this API must match the gateway type used by the OAuth Provider you just created. The gateway type for the API is shown at the foot of the API Setup page.
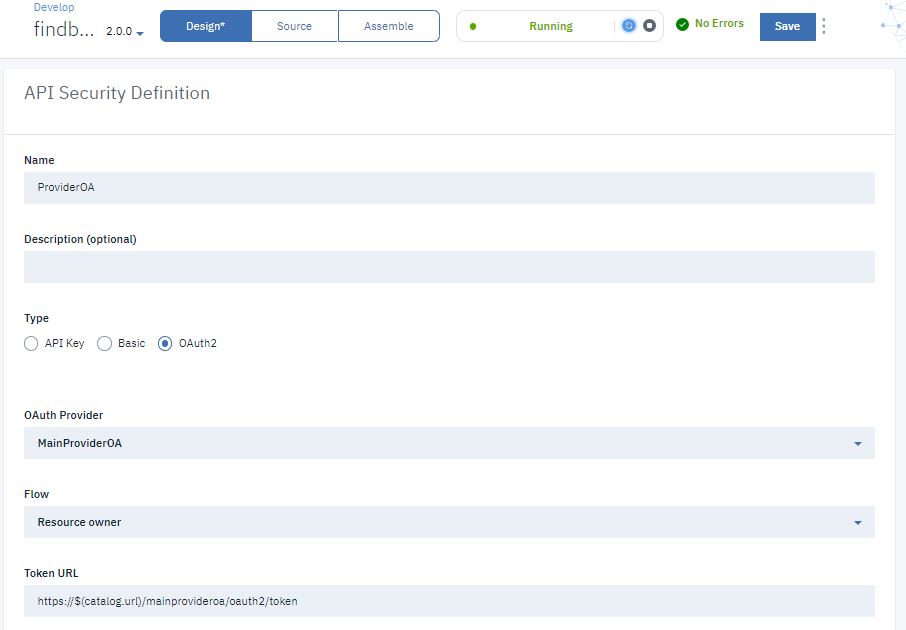
- Click Security Definitions.
- Click Add.
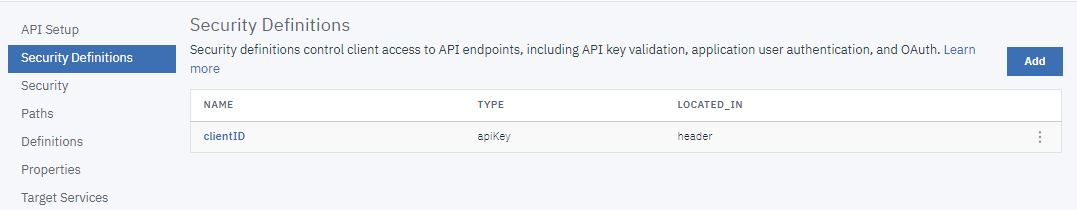
- Enter ProviderOA in the Name field.
- Under Type, click OAuth2.
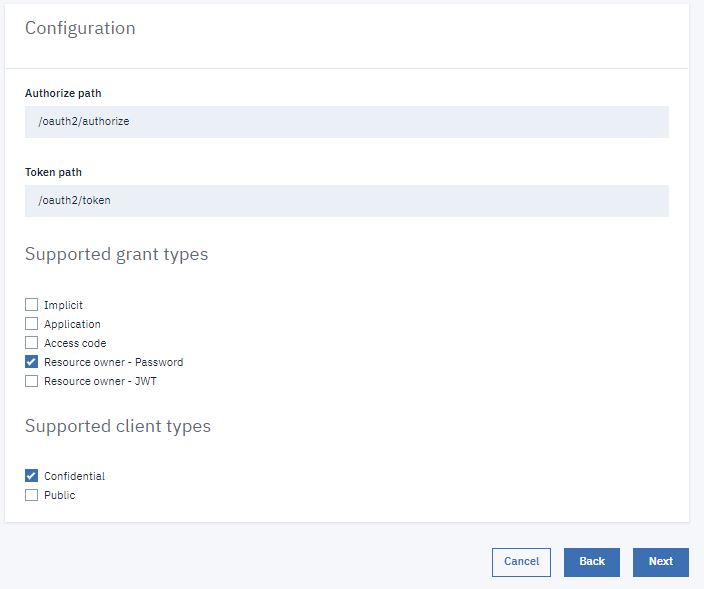
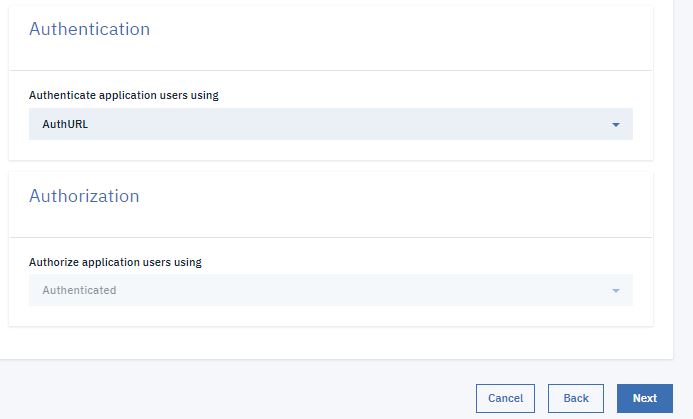
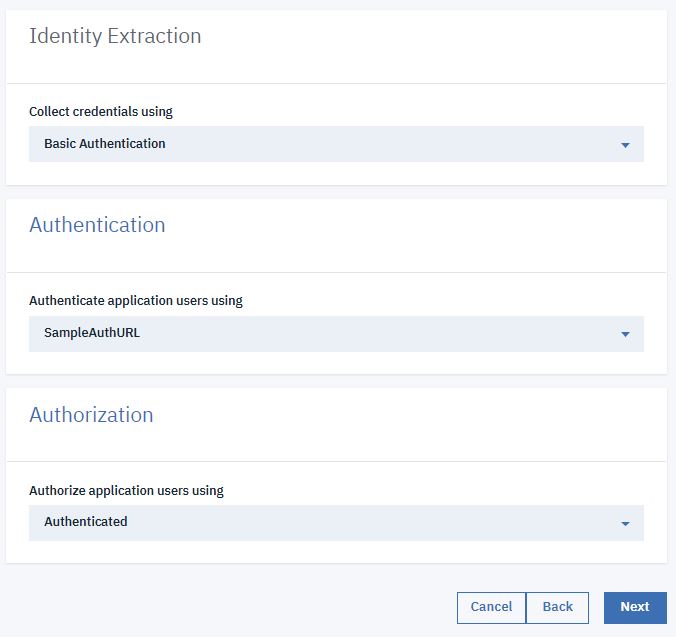
- Select MainProviderOA in the OAuth Provider field.
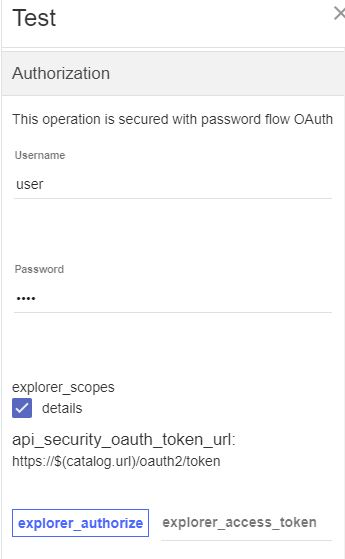
- Select Resource owner in the Flow field.
- Click Save.
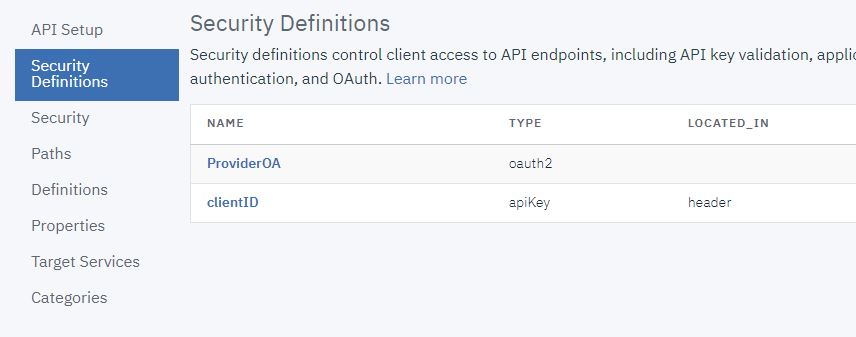
- Click Security.
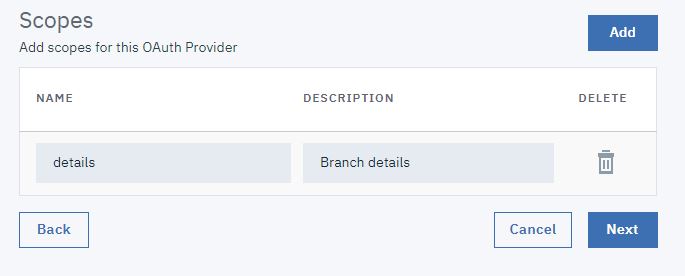
- Under Security Definitions, select ProviderOA, and
select details.
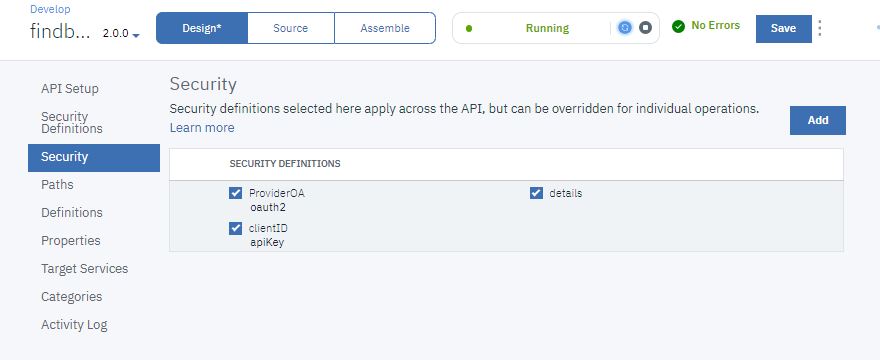
- Click Save.
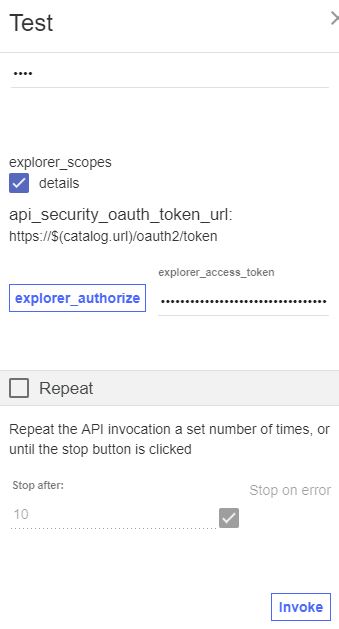
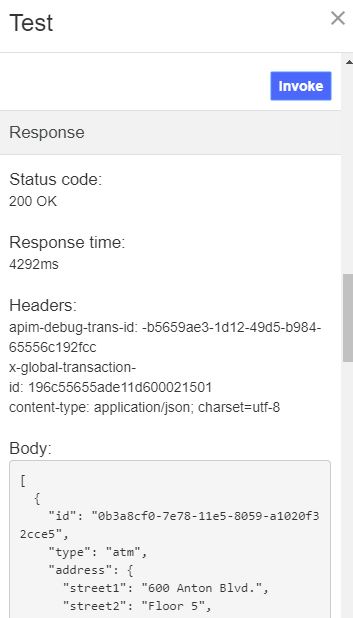
Test OAuth Security
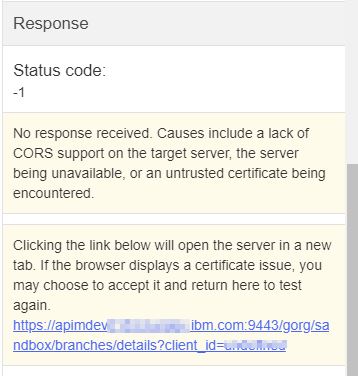
Note: Due to Cross-Origin Resource Sharing (CORS)
restrictions, the assembly test tool cannot be used with the Chrome or Safari browsers on the macOS
Catalina platform.
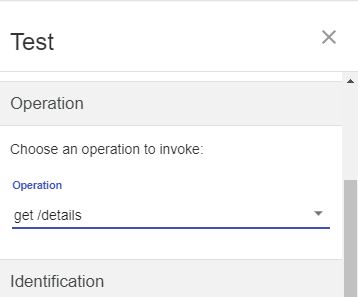
To test the new OAuth security added to the API, complete the following steps:
What you did in this tutorial
In this tutorial, you completed the following activities:
- Created an OAuth Provider.
- Made the OAuth provider available within the catalog.
- Added OAuth security to an existing API.
- Tested the OAuth security.