Microsoft Active Directory Global Catalog
A Global Catalog is a Global Catalog Server. A Global Catalog holds a full set of attributes for the domain in which it resides and a subset of attributes for all objects in the Microsoft Active Directory Forest. The primary two functions of a Global Catalog within the Microsoft Active Directory are logon capability and Microsoft Active Directory queries.
A Global Catalog in a Microsoft Active Directory installation with the product is a single Lightweight Directory Access Protocol (LDAP) repository that contains a subset of user information from all the domains in the forest. This information includes user IDs, authentication information, and groups, but not all the group information.
You can use the Global Catalog on any domain controller in the forest, even in subdomains. The Global Catalog is a solution to the WebSphere® Application Server limitation of a "single registry". There are limitations to the Global Catalog. Users from the local domain controller contain group "memberOf" information. Users from a foreign domain controller contain limited "memberOf" information because the global group information is not replicated to every domain controller.
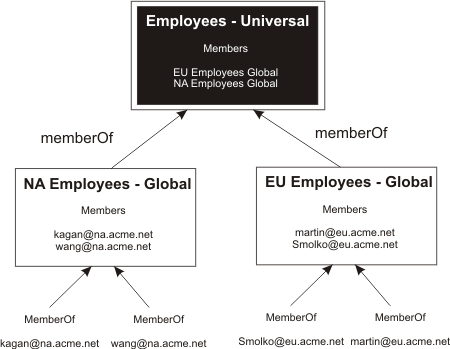
Nested global groups in universal groups
- Users are distributed across domain controllers in a forest containing multiple domain controllers.
- Users are defined in global groups within their own local domain controller.
- A universal group contains the global groups, which reflects a Java™ Platform Enterprise Edition (Java EE) role that maps to a set of users spread across multiple domain controllers.
The following figure illustrates nested global groups in universal groups.
Another method and the simplest approach has universal groups that contain users and uses a Global Catalog, which requires using referrals. The figure that follows illustrates this method.
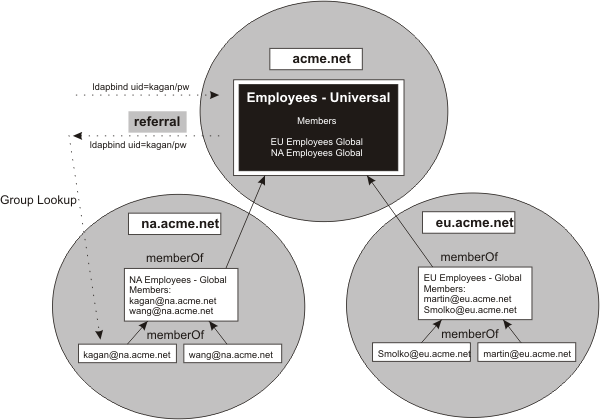
- If you configure WebSphere Application Server to use Global Catalog as its LDAP registry and follow referrals, then individual users are visible in each domain controller. Because a user must exist only once in the registry, all logins fail.
- If you configure WebSphere Application
Server to use Global Catalog as its LDAP registry and do not follow
referrals and the individual users are within global groups, then
group membership is incomplete. See the following figure, which illustrates
this limitation.
Figure 3. Global catalog (without using referrals) . An illustration of a Global Catalog without using referrals 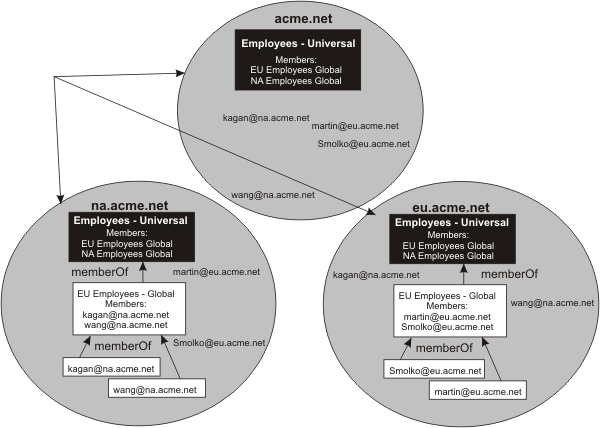
- When you configure WebSphere Application Server to use Global Catalog as its LDAP registry, do not follow referrals, and users are directly contained within universal global groups, then group membership is complete.