Integration and authentication with a reverse proxy
You can use a reverse proxy to enable enterprise connectivity within a MobileFirst environment and to provide authentication to IBM MobileFirst™ Platform Foundation.
General architecture
Reverse proxies typically front MobileFirst instances as part of the deployment, as shown in Figure 1, and follow the gateway pattern.
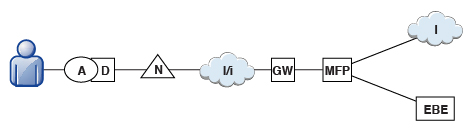
The MFP icon represents an instance of MobileFirst Server. The GW icon represents a reverse-proxy gateway, such as IBM® WebSphere® DataPower® or IBM Security Access Manager. In addition to protecting MobileFirst resources from the Internet, the reverse proxy provides termination of HTTPS (SSL) connections and authentication. The reverse proxy can also act as a policy enforcement point (PEP).
When a gateway is used, an application (A) on a device (D) uses the public URI that is advertised by the gateway instead of the internal MobileFirst Server URI. The public URI can be exposed as a setting within the application, or can be built in during promotion of the application to production, before the application is published to public or private application stores.
Authentication at the gateway
If authentication ends at the gateway, IBM MobileFirst Platform Foundation can be informed of the authenticated user by a shared context, such as a custom HTTP header or a cookie. By using the extensible authentication framework, you can configure IBM MobileFirst Platform Foundation to use the user identity from one of these mechanisms and establish a successful log in. Figure 2 shows a typical authentication flow for this gateway topology.
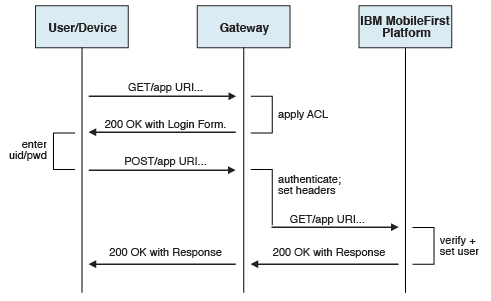
- Header-based authentication
-
- On successful authentication, the gateway forwards a custom HTTP header with the user name or ID to IBM MobileFirst Platform Foundation.
- IBM MobileFirst Platform Foundation is configured to use HeaderAuthenticator and HeaderLoginModule on either Tomcat or WebSphere Application Server.
- LTPA-based authentication
- On successful authentication, the gateway forwards an LTPA token (in the form of an HTTP cookie) to IBM MobileFirst Platform Foundation, which validates the LTPA token and creates a caller principal.
- IBM MobileFirst Platform Foundation on WebSphere Application Server is configured to use the WebSphereFormBasedAuthenticator and WebSphereLoginModule classes. See LTPA authenticator and WASLTPAModule login module.
Hybrid applications note
The client's registration with MobileFirst Server, including any challenge that is sent during the registration stage, is executed only in native code. To ensure that a hybrid application's challenge handler is called during the client's registration with the server, the challenge handler must be implemented and registered within the application's native code. For more information, see Challenge handling in a gateway topology.