Installing MaaS360 VPN and configuring the MaaS360 VPN TAP Adapter on Windows Server 2016+
Follow these steps to install MaaS360® VPN, including the MaaS360 VPN TAP Adapter, on Windows Server 2016+.
About this task
- Installing the Cloud Extender® software on Windows Server 2016+.
- Installing the MaaS360 VPN TAP Adapter on Windows Server 2016+.
- Enabling Network Address Translation (NAT) on the outgoing interface for the MaaS360 VPN server.
Procedure
-
Log in to the MaaS360
Portal, select Setup > Services, and confirm that the MaaS360 VPN service is enabled.
 Note: Contact IBM® Support if the MaaS360 VPN feature is not enabled.
Note: Contact IBM® Support if the MaaS360 VPN feature is not enabled. - Download the Cloud Extender and obtain the license key.
-
Follow the steps in the installation wizard to install the Cloud
Extender on your Windows Server 2016+.
The MaaS360 VPN module is automatically downloaded to the end user agents.
-
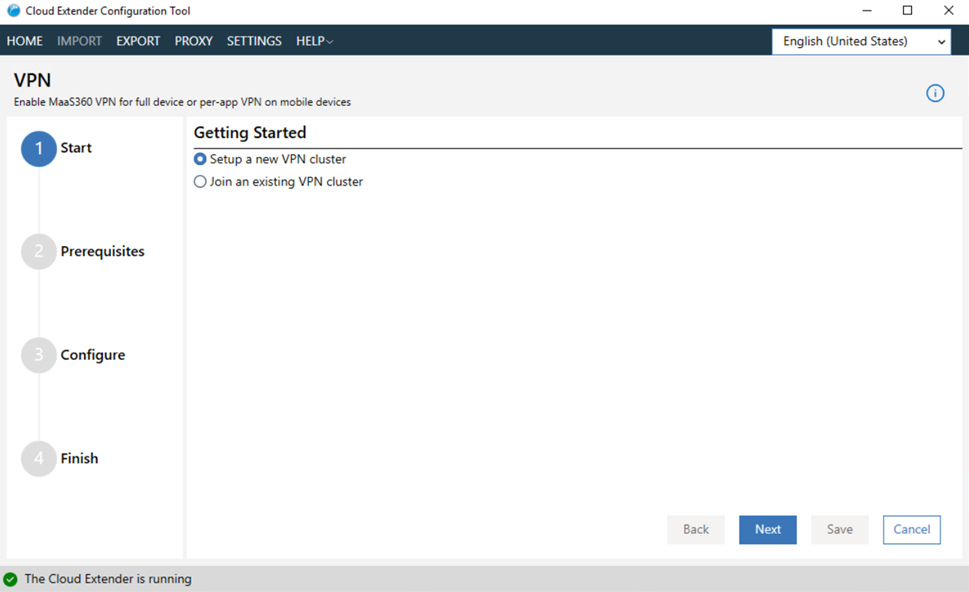
From the Cloud Extender
Configuration Tool, select
VPN, and then select Setup a new VPN cluster.
 Note: After you install the Cloud Extender, the MaaS360 VPN module might take a few minutes to download. If the VPN option is not displayed in the Cloud Extender Configuration Tool window, close the Cloud Extender Configuration Tool, wait a few minutes, and then start the Cloud Extender Configuration Tool again.
Note: After you install the Cloud Extender, the MaaS360 VPN module might take a few minutes to download. If the VPN option is not displayed in the Cloud Extender Configuration Tool window, close the Cloud Extender Configuration Tool, wait a few minutes, and then start the Cloud Extender Configuration Tool again. -
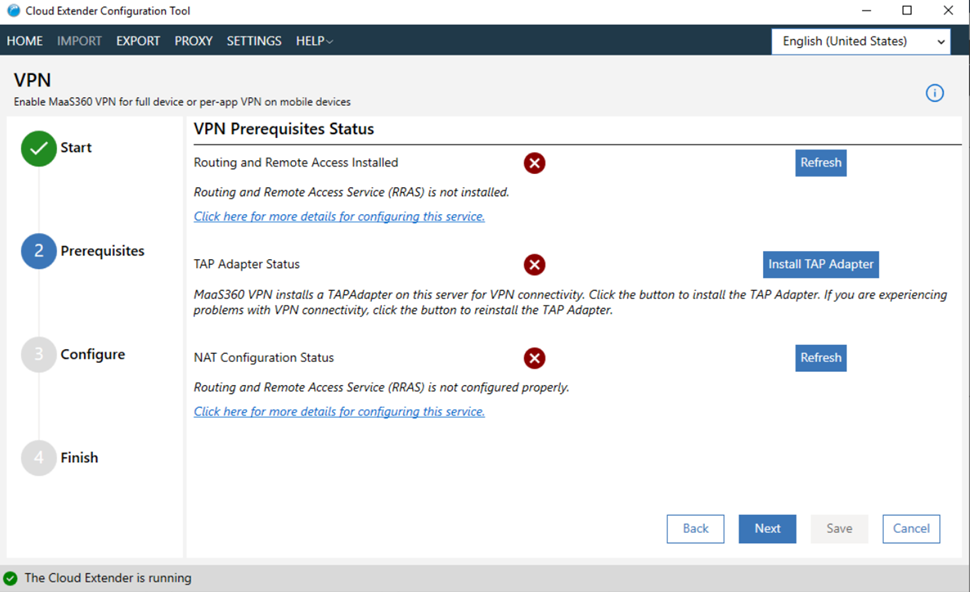
Click Install Tap Adapter to install the MaaS360
VPN TAP Adapter.
Important: You must install the MaaS360 VPN TAP Adapter before you configure settings for MaaS360 VPN.
-
Select Yes to any security prompt.
The adapter might take a few minutes to install on your system.Note:
- If Windows Server 2016+ updates are pending on your system, reboot your system, and then apply those updates before you install the MaaS360 VPN TAP Adapter.
- If you receive an error message during installation of the MaaS360 VPN TAP Adapter, follow the steps in Troubleshooting issues with MaaS360 VPN to remove the TAP adapter from your system. Reboot your system, and if necessary, apply any updates, and then try to install the TAP adapter again.
After you install the MaaS360 VPN TAP Adapter, the following window displays a warning message that the Routing and Remote Access Service (RRAS) is not configured properly. You must enable Network Address Translation (NAT) on the outgoing interface of the MaaS360 VPN to configure the Routing and Remote Access Service (RRAS).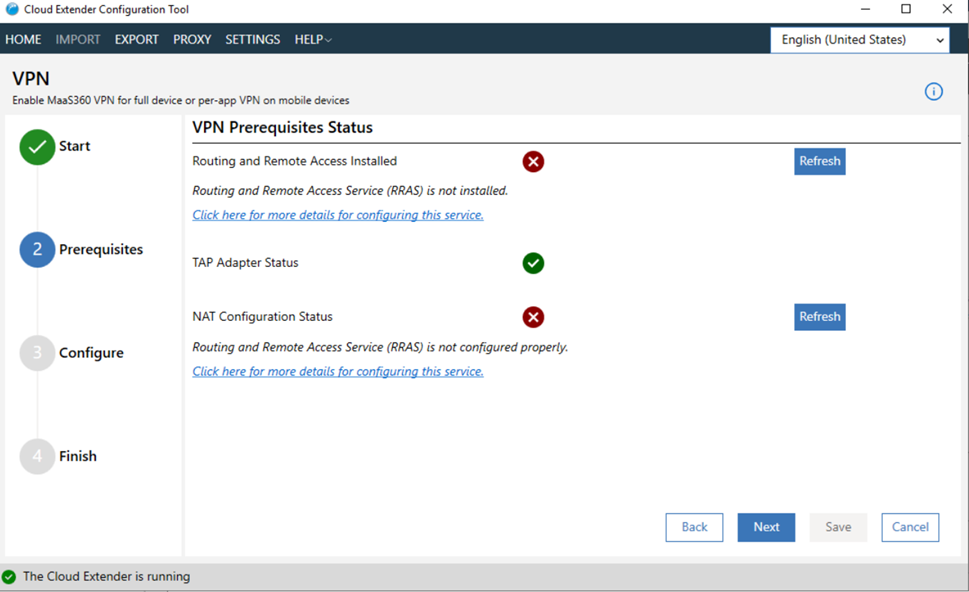 Follow these steps to enable Network Address Translation (NAT) on the outgoing interface for the MaaS360 VPN:
Follow these steps to enable Network Address Translation (NAT) on the outgoing interface for the MaaS360 VPN:-
From the Windows Start menu, select Routing and Remote
Access.
If Routing and Remote Access is not listed, make sure that you followed the steps to install this role from the procedure provided in Installing the routing and remote access role on Windows Server 2016+.
-
Right-click on the name of the server, select Configure and Enable Routing and
Remote Access, and then click Next.
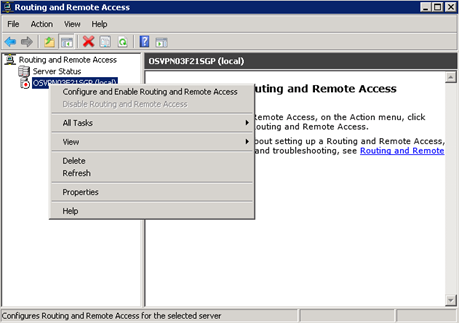 The Routing and Remote Access Server Setup Wizard displays the Configuration window.
The Routing and Remote Access Server Setup Wizard displays the Configuration window.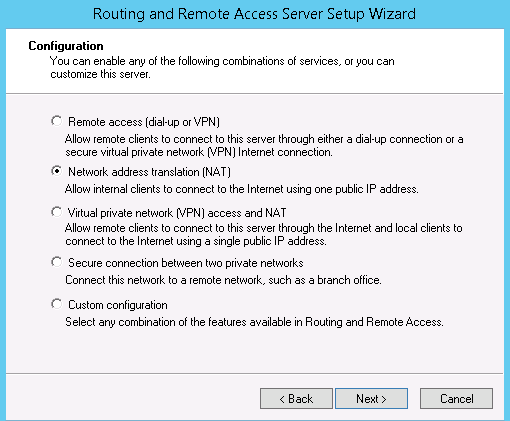
-
Select Network address translation (NAT), and then click
Next.
The Routing and Remote Access Server Setup Wizard displays the NAT Internet Connection window.
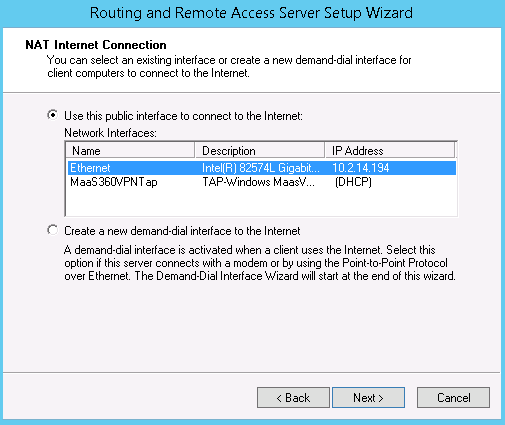
-
Make sure that Use this public interface to connect to the Internet is
enabled.
-
From the Network Interfaces list, select the network adapter that uses NAT
for all outgoing traffic from VPN users.
- This adapter must be an adapter on the server that is connected to a subnet that can reach both internal and external resources that you want your VPN users to access over the MaaS360 VPN.
- Do not select the MaaS360 VPN TAP Adapter. This adapter is listening for traffic only and translates all traffic to the Ethernet adapter.
- If you do not have the option to select an adapter, or if MaaS360VPNTap
is not listed, make sure that you used the Cloud Extender
Configuration Tool to configure
MaaS360
VPN and
installed the MaaS360
VPN TAP Adapter from
that tool. This option is available only if you have more than one adapter on the server (MaaS360 always installs a second virtual adapter for the VPN).
In NAT mode, you can use one interface for all traffic that accesses any resources from connected
VPN tunnels.
- For one-arm mode setup, the server uses only one physical adapter that is used by all traffic.
- If you have multiple physical adapters (multi-arm mode setup), the adapter selected for the NAT
interface must have routes available to reach any network resources (internal or external) that need
to be accessed over the VPN. This type of setup can cause issues with routing public internet
traffic, since the default gateway is used for routing internet traffic (you should only use one
default gateway in Windows).
If the default gateway is not set on the interface that is selected for NAT, and if there is not an explicit route defined for the resource that is requested, then users cannot access that resource over the VPN. See MaaS360 VPN deployment scenarios for options on how to configure routing and interfaces.
- If your Windows Server 2016+ uses more than two adapters, select the adapter that NAT uses. Select MaaS360VPNTap, and then click Next.
- Click Next, and then click Finish to complete NAT enablement on the MaaS360 VPN server.
-
After you configure the Routing and Remote Access Service (RRAS), click
Refresh.
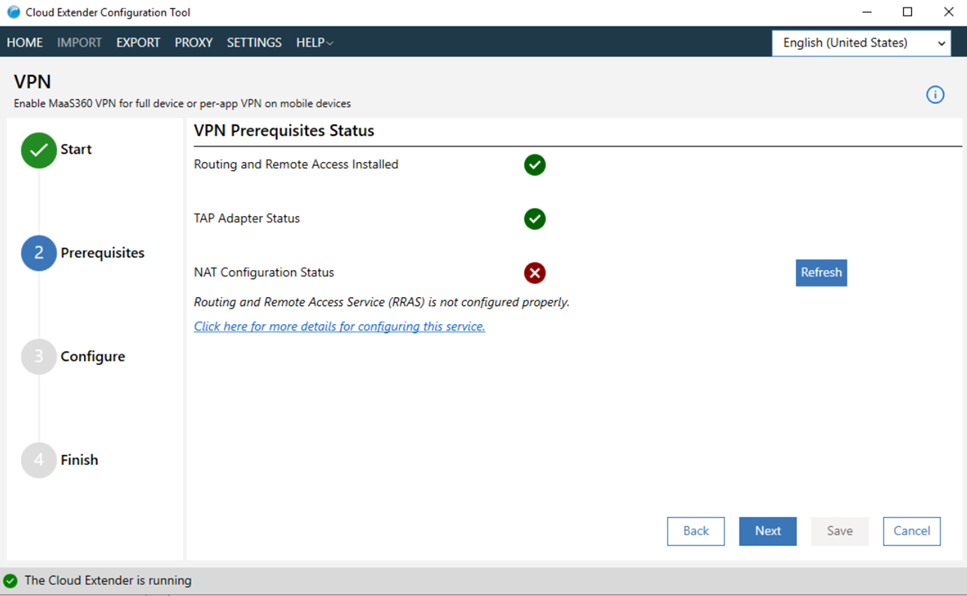 If the configuration is successful, a green checkmark is displayed next to the list of adapters and you can continue with the installation:
If the configuration is successful, a green checkmark is displayed next to the list of adapters and you can continue with the installation: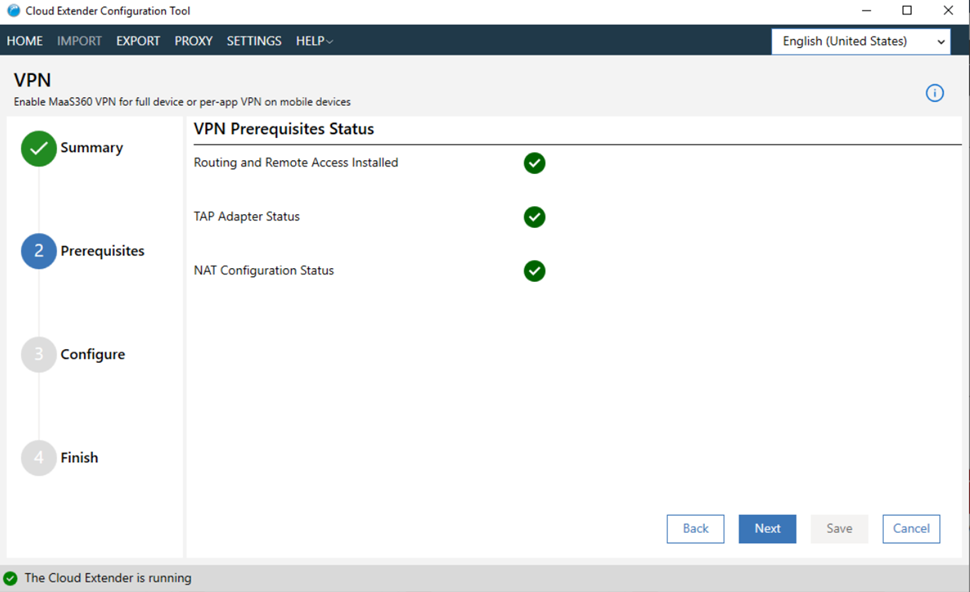
- Provide the following network settings for the MaaS360
VPN:
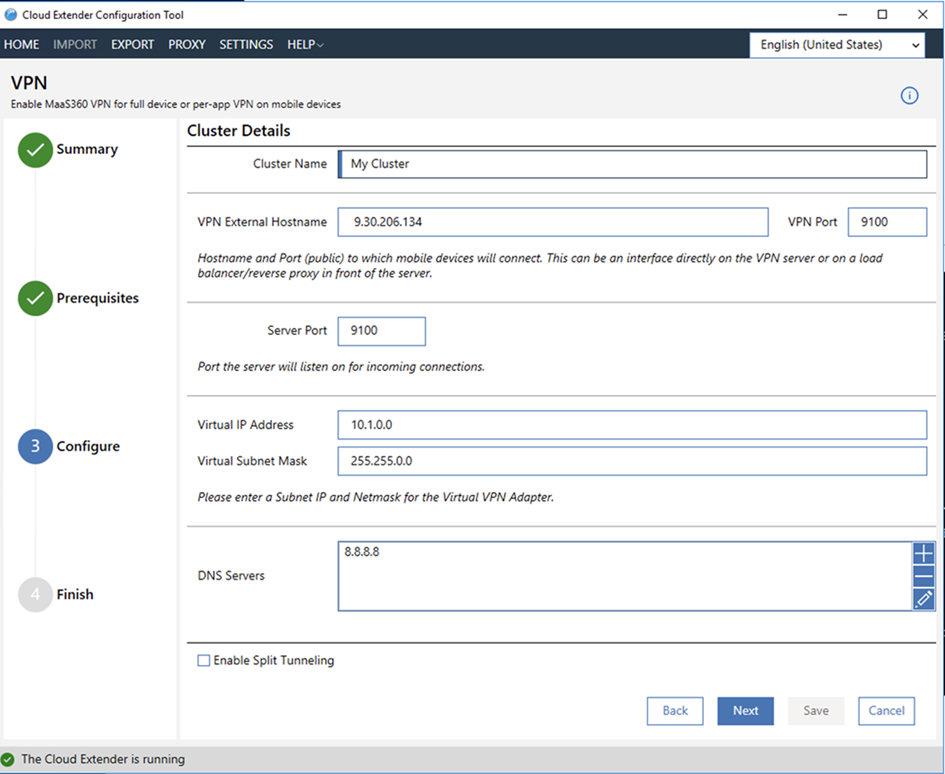
Setting Description Cluster Name The name of the MaaS360 VPN cluster that is available to the MaaS360 policies. VPN External Hostname The external DNS name or the IP address, and the port that is used to configure external user connections to connect to the MaaS360 VPN. The public IP address is assigned directly to an interface on the Windows Server or translated to the private address of the Windows Server by using a router, firewall, load balancer, or reverse proxy (highly recommended).
VPN Port The default port is 1194. You can change this port. MaaS360 VPN currently uses the UDP protocol, which you cannot change. Make sure that the port that you entered is open to the server that is provisioning MaaS360 VPN. You should block other ports for security reasons.
VPN Internal URL/IP The private IP address or URL of the MaaS360 VPN server host. Server Port Any available open port on the MaaS360 VPN server host. Virtual IP Address and Virtual Subnet Mask One or more valid subnets (IP address and netmask) that are used to assign IP addresses to inbound user connections for the VPN tunnel. - Use subnets in a private range that include enough IP addresses to handle all users that connect to each MaaS360 VPN server.
- One subnet is needed for each MaaS360 VPN server. The subnet must include enough IP addresses to handle the maximum number of users that can connect to the server at single instance.
- Since Network Address Translation (NAT) is used on outgoing traffic from the server, you can use the same subnet for each MaaS360 VPN server. However, this setup might impede troubleshooting efforts.
- Use unique subnets in the network that do not create overlap or confusion with the network routing.
DNS Servers One or more DNS servers that are used by end user agents. - The DNS server must be accessible from the network interface that the MaaS360 VPN is installed on.
- The DNS server must resolve public and private addresses, even if split tunneling is used (or, add a second public DNS to the list).
Enable Split Tunneling Enable this option if you configured at least one network destination for the VPN client to tunnel traffic to the MaaS360 VPN servers. Note: Make sure that you disable the Enable Split Tunneling check box if you are routing all traffic through the VPN.Networks A list of subnets (IP address and netmask) that are used to route through the MaaS360 VPN (if you are using split tunneling). Note: If you are not using split tunneling, all traffic (private and public) is routed through the tunnel, which might increase the load on the server with non-corporate traffic. - Click Next. When the MaaS360 VPN is configured, a certificate (p12 format) is generated for you to use if you are planning to set up multiple servers in a load-balancing scenario. Click Download VPN Certificate and store the certificate file for future use. Follow the steps in Setting up a cluster for MaaS360 VPN.
-
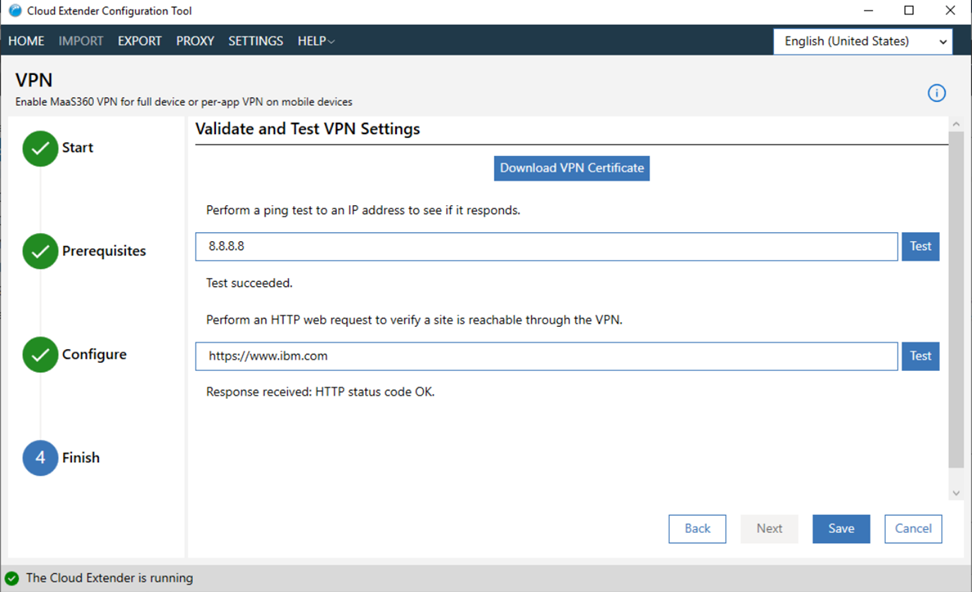
Perform a ping test or an HTTP web request to validate VPN activity:
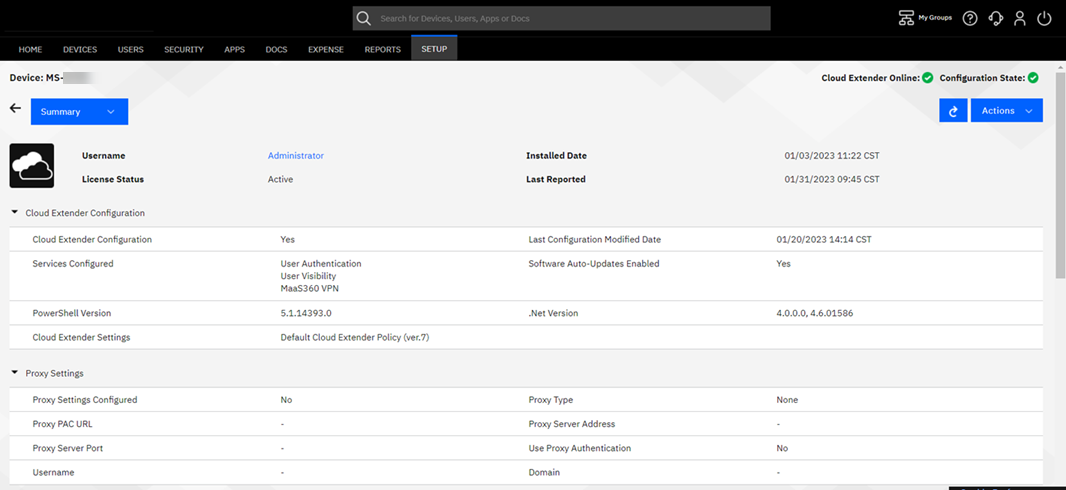
- From the MaaS360 Portal Home page, select
Setup > Cloud Extender, and
then select the Cloud Extender where you installed the MaaS360 VPN service. The Cloud Extender
configuration settings are displayed in the Summary section:
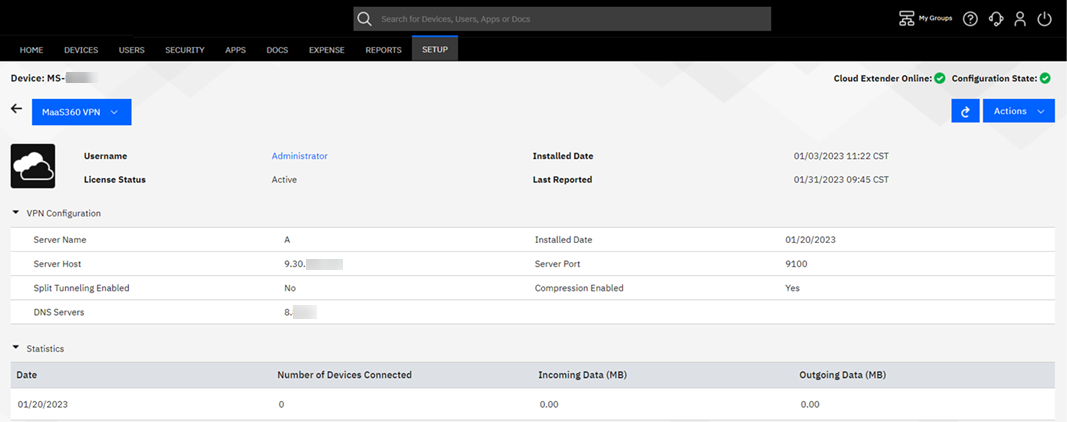
-
From the drop-down list, select MaaS360 VPN. The MaaS360
VPN configuration
settings and the latest statistics (a snapshot of the connected clients and statistics of those
connections) are displayed.
What to do next
You are now ready to define iOS and Android MDM policies in the MaaS360 Portal and use the MaaS360 VPN.