MaaS360 VPN deployment scenarios
Information about deploying MaaS360® VPN in your environment.
MaaS360 VPN deployment example: Single interface server with NAT mode or IP forward mode (one-arm mode)
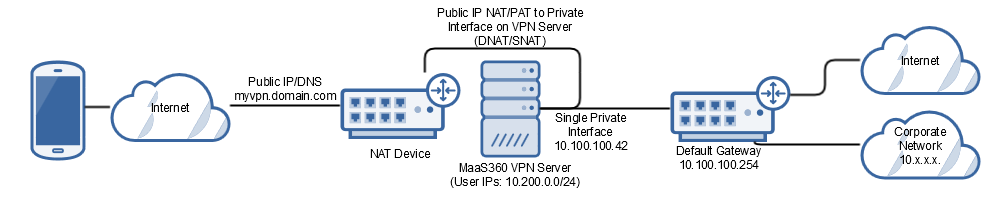
In this example, the MaaS360 VPN server uses a single physical interface to connect to the internal network. A Network Address Translation (NAT) device (for example, firewall or load balancer) maps the public address of the MaaS360 VPN to the internal address and port of the MaaS360 VPN server.
Depending on your network setup, the NAT device and default gateway router might be the same device. If you are not using the same device for the NAT device and the default gateway, the Source NAT (SNAT) is applied to the public IP and to the private interface NAT; otherwise return traffic from the VPN server to the endpoint might be sent to the default gateway instead of the NAT device, resulting in routing failures.
MaaS360 VPN deployment example: Multiple interface VPN server with NAT mode or IP forward mode (multi-arm mode)
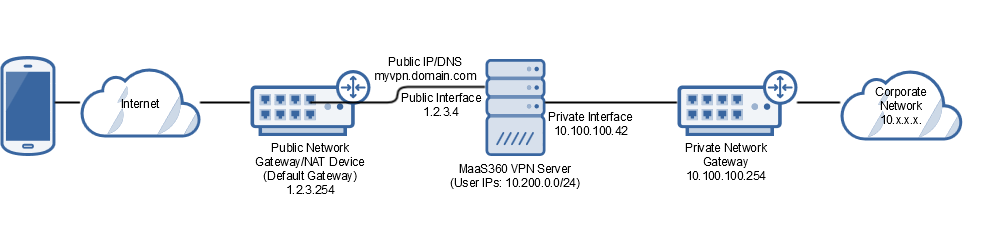
In this example, the MaaS360 VPN server uses two interfaces: one interface for incoming connections to the VPN server and one interface to access the corporate network resources. The public IP is assigned directly to the incoming interface on the VPN server, however this setup can also use a separate private IP address, assuming that the public IP is translated to this private IP by using Network Address Translation (NAT) or Private Address Translation (PAT) (see the single interface server deployment example).
Since Windows does not support multiple default gateways, the default gateway is set on the public side interface to facilitate the return traffic to the endpoints during the creation of the VPN tunnel. If the default gateway is assigned to the private interface on the VPN server, the VPN connection process fails since inbound requests arrive on a different interface than the reply request. If you applied a source NAT on the incoming traffic to the VPN server, you can define a persistent static route on the public interface of the VPN for the Source NAT IPs to make sure that the return traffic uses the same interface that is used for new tunnel connections. Set the default gateway to the private interface on the VPN server.