Minimize disruptions and keep doing you
A CISO’s Journey
In cybersecurity, each new day brings unexpected challenges. As the CISO, it’s part of the job. Try as you might to do higher value work and spend time with loved ones, an attack can happen without warning, exposing your enterprise to a data breach. IBM Security X-Force Threat Management (XFTM) Services keeps you protected and in the know—day or night—to minimize life’s disruptions.
Insights
Click the blue highlighted area to explore
Begin your day with a healthy dose of insights, reviewing current attack activity and the latest threat intelligence.
Protection
Click the blue highlighted area to explore
While focusing on the upcoming phishing awareness training, you receive a ransomware alert. What’s the remedy?
Detection
Click the blue highlighted area to explore
You’re taking a ride share to meet the CIO and CTO for lunch before today’s board meeting—it’s time to prepare them for the next round of budget asks. Almost there, and you get a priority 2 alert from your team.
Response
Click the blue highlighted area to explore
You’re up next on the agenda at the quarterly board meeting to present on the “state of security” when you’re suddenly notified that a laptop in finance is infected with ransomware.
Recovery
Click the blue highlighted area to explore
The attack is contained—without paying ransom—before the kids hit the field. As you cheer for the goal, the IBM mobile app buzzes with more good news. The source of the breach has been detected.

At the end of the day, get back to doing you.
Cyber criminals never rest, but you certainly can. Don’t let security threats disrupt your day. Sign up for an IBM Security X-Force Threat Management workshop and start your journey to mature enterprise security.
Begin with insights.
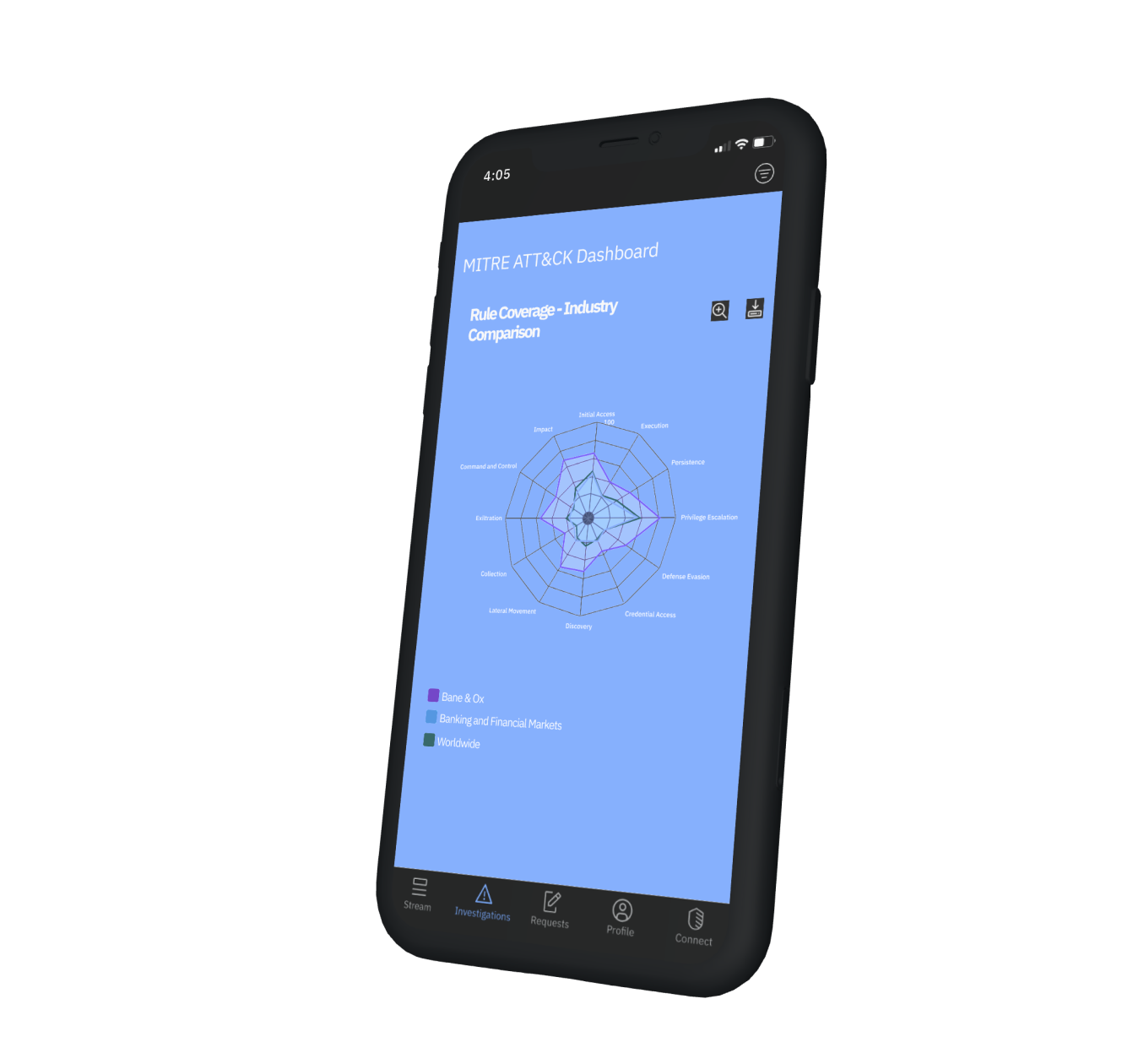
As you browse the day’s threat intelligence on the IBM Security Services mobile app, you can stay up-to-date with security alerts. The latest penetration test results are in, providing insight into vulnerabilities at a new acquisition’s locations.
With XFTM, you’re already aware of the new unit’s crown jewels, data and devices, and privileged and power users. You can call up the report on the risk profiles of each to get the full picture.
XFTM brings cybersecurity frameworks like NIST and MITRE ATT&CK to life by integrating offensive security services, managed security services, incident response, managed detection and response (MDR), and AI across IT, OT, IoT and IoMT domains.
Protect assets with technology, policies and practices
The assigned SOC analyst determines that your security controls don't have the coverage for this new threat. She notifies your security vendor and follows up to ensure they add the new signatures and IOCs to their product as soon as possible.
Patching, vulnerability management and ID governance fall under threat protection services, along with network security tools and robust threat prevention security policies and procedures for users and devices.
With continuous policy optimization, you can rest assured that proactive measures are in place to protect your assets and stop exploitation attempts quickly.
Detect threats quickly and accurately
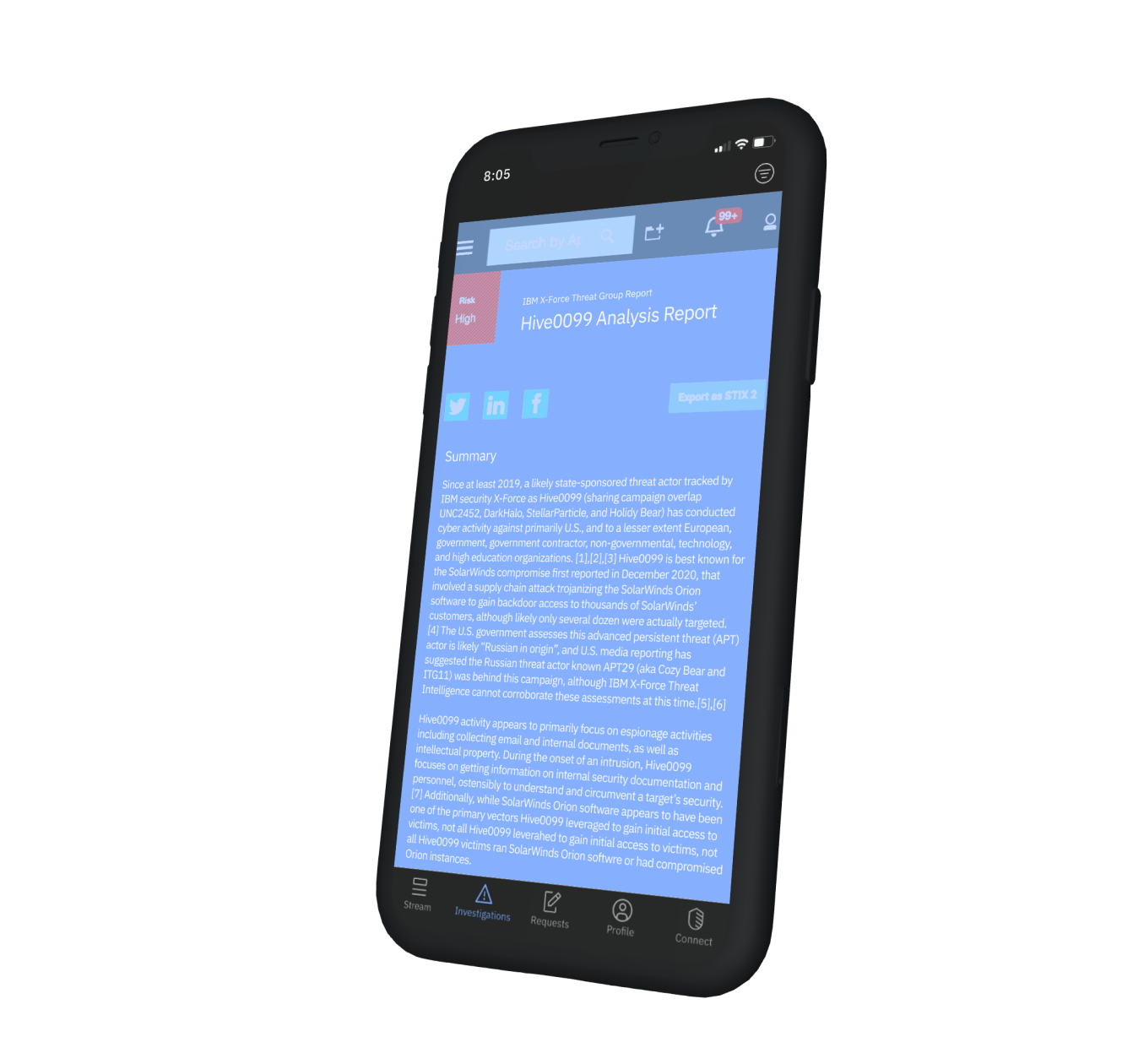
You are a week into your SIEM detecting infiltration from a priority 2 alert focused on data exfiltration, and 90% of the kill chain has already been executed by the attacker. Data is about to go out the door. An IBM Security L2 analyst, armed with threat data from the MITRE ATT&CK Framework, is already investigating the alert, and IBM Security’s AI is helping get to the root cause.
With XFTM providing 24x7 SOC operations, patented AI, machine learning, automated analysis and deep expertise, you can elevate the continuous monitoring of your SIEM or MDR for rapid, precise threat detection. Time-tested use cases help optimize rules, increase accuracy and recommend actions.

Respond to incidents with tested action plans
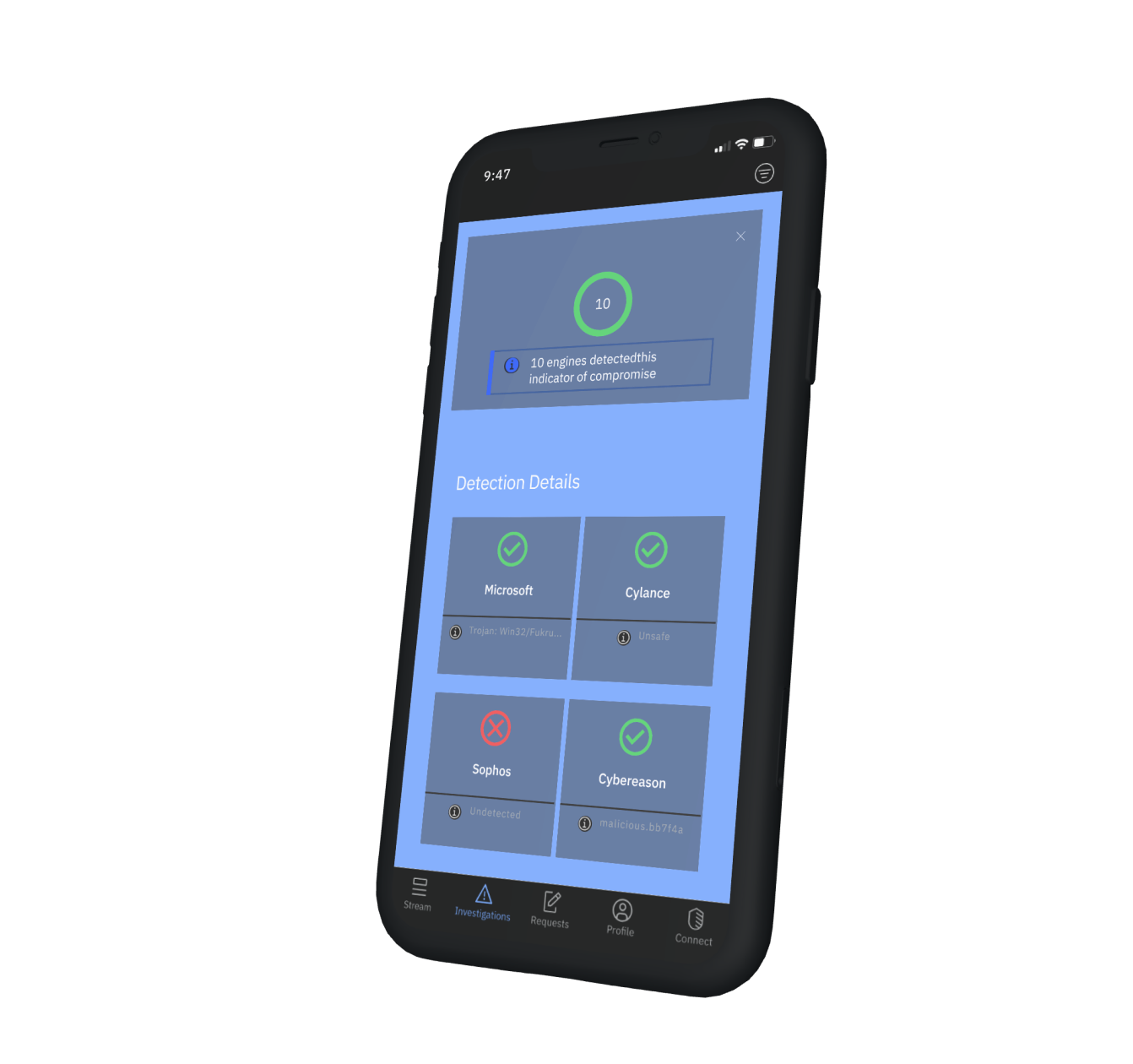
Endpoint Detection and Response (EDR) picked up the activity on the laptop. Through the IBM Security Services mobile app you invoke IBM Security SOAR and Ansible response capabilities. When EDR and the SIEM make it clear that this activity goes beyond one laptop, you get a Priority 1 alert that you are under attack.
You immediately activate the IBM Security X-Force Incident Response team via the mobile app. The team begins working with your SOC team to identify the malicious code and contain the problem. XFTM manages the incident and communicates with stakeholders. When incidents are complex—like this one—IBM Security SOAR orchestrates a response across multiple analysts and tasks to speed investigations.
When the situation is resolved, IBM Security will help you build playbooks and simulate malware incidents just like this one so you are prepared to act.
Recover, remediate and learn for continuous improvement
Thanks to a rapid response, recovery from this incident was straightforward. Your endpoint protection has been bolstered so you know this attack can be prevented. And because your integrated BC/DR program covers endpoint data, restoring affected devices to pre-infection state and reconnecting them to the network doesn’t take long.
Working with your IBM Security X-Force Advise consultant, you decide to update your internal response plans to mature your SOC and improve your risk exposure. You also make a mental note to update the training program you reviewed earlier.
A quick check on the status of open cases confirms that the five-phase programmatic framework and end-to-end threat management approach from XFTM are working to protect your company.