 Networking on z/OS
Networking on z/OS
 Networking on z/OS
Networking on z/OS
|
Previous topic |
Next topic |
Contents |
Glossary |
Contact z/OS |
PDF
Connection networks Networking on z/OS |
|
|
A connection network is a representation of a shared access transport facility (SATF), enabling dynamic direct connectivity between any pair of link stations attaching to the facility. An example of a shared access transport facility is a local area network (LAN) where two nodes can communicate directly with each other without the need to use a router. In Figure 1 there are end nodes and one network node connected to a LAN. If you do not implement a connection network, you have two options. The first option is to define links only from each end node to the network node (the left side of the figure); the second option is to implement a meshed topology by defining links between each pair of nodes (the right side of the figure). The first option requires fewer link definitions (each end node must define only one link to the network node, and the network node must define a link to each end node, resulting in 2*(n-1) link definitions for a network consisting of n nodes); but sessions between any two end nodes must traverse the network node, which can cause performance problems in the network node if there are a large number of nodes on the LAN. The second option requires more link definitions (each node must define links to every other node, resulting in n*(n-1) definitions for a network of n nodes); but sessions between any two nodes always use a direct link between the session endpoints. Also notice that, as more nodes are added to the shared access transport facility, the number of link definitions required grows exponentially with option 2, while the number of link definitions grows linearly with option 1. Another problem with option 2 is that, as more nodes are added to the LAN, new links must be defined on every other node on the LAN in order to exploit direct connectivity to the nodes being added. The administrative task of defining new links is considerably reduced (and the overhead of routing session traffic through an intermediate network node is completely eliminated) by using a connection network to represent the shared access transport facility. Using a connection network allows nodes attached to the shared access transport facility to exploit direct connectivity over the LAN without defining a direct link to every other node on the LAN. A connection network is implemented by defining a virtual routing node (VRN) to represent the shared access transport facility; see Example of a virtual routing node (VRN). Each end node on the LAN defines a link to the real network node (for sending searches) and a link to the VRN which identifies the end node's connectivity to the shared access transport facility. Figure 2. Example of a virtual routing node (VRN)
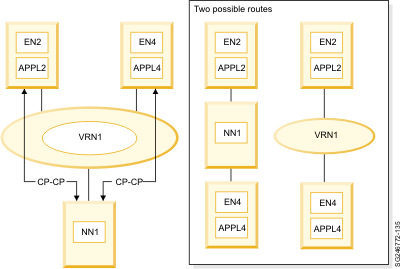 The links to the VRN provide the appearance of a second path between any two end nodes on the same shared access transport facility--but this second path is preferred over the path through the network node because the VRN is a virtual network node rather than a real intermediate network node. The VRN link definitions are used during session establishment to dynamically activate a new link directly between the session endpoints. When the last session traversing a dynamic VRN link ends, the dynamic link is inactivated until it is needed again for another session. Because each end node attached to the connection network defines only 2 links, the number of link definitions required for a network with n nodes is 2*n. This is very comparable to option 1 above, but avoids the overhead of routing sessions through real intermediate network nodes. Furthermore, when new end nodes are added to the connection network, new link definitions may be required on the network node; but no additional link definitions are required on any of the existing end nodes in order to exploit direct connectivity to the new end nodes. |
 Copyright IBM Corporation 1990, 2010 Copyright IBM Corporation 1990, 2010 |