Managing encryption
The encryption key server (EKS) and the three methods for managing encryption.
The EKS uses a keystore to hold the certificates and keys (or pointers to the certificates and keys) required for all encryption tasks. Refer to the appropriate EKS documentation for detailed information about the EKS and the keystores it supports.
- Encrypted or wrapped, with Rivest-Shamir-Adleman (RSA) key pairs. The tape drive writes this copy of the key to the cartridge memory and three extra places on the tape media in the cartridge for redundancy.
- Separately wrapped for secure transfer to the tape drive where it is unwrapped upon arrival and the key inside is used to encrypt the data that is written to tape.
When an encrypted tape cartridge is read by a TS1120 or later tape drive, the protected AES key on the tape is sent to the EKS where the wrapped AES key is unwrapped. The AES key is then wrapped with a different key for secure transfer back to the tape drive, where it is unwrapped and used to decrypt the data that is stored on the tape. The EKS also allows protected AES keys to be rewrapped, or rekeyed, with different RSA keys from the original ones that are used when the tape was written. Rekeying is useful when an unexpected need arises to export volumes to Business Partners whose public keys were not included. It eliminates the need to rewrite the entire tape and enables a tape cartridge's data key to be reencrypted with a Business Partner's public key.
Three methods of encryption management are available to choose from. These methods differ in where the encryption policy engine resides and where key management is completed for your encryption solution, and how the EKS is connected to the drive. Your operating environment determines which is the best for you. Key management and the encryption policy engine can be in any one of the following three environmental layers.
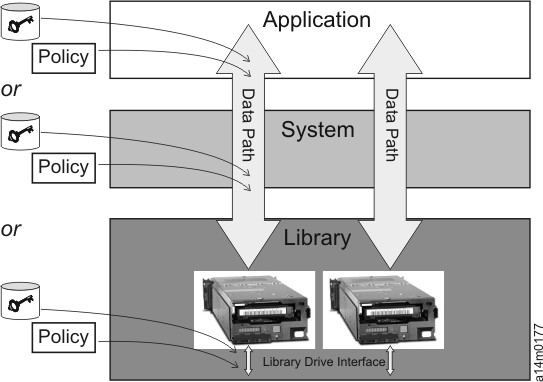
- Application Layer
- Initiates data transfer for tape storage, for example TSM.
- System Layer
- Everything between the application and the tape drives, for example the operating system, z/OS DFSMS, device drivers, and FICON®/ESCON controllers.
- Library Layer
- The enclosure for tape storage, such as the IBM TS3500 tape library. A modern tape library contains an internal interface to each tape drive within it.