About encryption keys
The encryption keys that are used to encrypt data are described.
An encryption key is typically a random string of bits generated specifically to scramble and unscramble data. Encryption keys are created with algorithms designed to ensure that each key is unique and unpredictable. The longer the key constructed this way, the harder it is to break the encryption code. Both the IBM and T10 methods of encryption use 256-bit AES algorithm keys to encrypt data. 256-bit AES is the encryption standard that is recognized and recommended by the US government, which allows three different key lengths. 256-bit keys are the longest allowed by AES.
Two types of encryption algorithms can be used by the encryption key server: symmetric algorithms and asymmetric algorithms. Symmetric, or secret key encryption, uses a single key for both encryption and decryption. Symmetric key encryption is used for encrypting large amounts of data efficiently. 256-bit AES keys are symmetric keys. Asymmetric, or public/private encryption, uses a pair of keys. Data encrypted with one key are decrypted only with the other key in the public/private key pair. When an asymmetric key pair is generated, the public key is typically used to encrypt, and the private key is typically used to decrypt.
The encryption key server uses both symmetric and asymmetric keys; symmetric encryption for high-speed encryption of user or host data, and asymmetric encryption (which is necessarily slower) for protecting the symmetric key.
Encryption keys can be generated by the encryption key server, by applications such as Tivoli Storage Manager, or by a utility such as keytool. The responsibility for generating AES keys and the manner in which they are transferred to the tape drive depends on the tape drive type and the method of encryption management. However, it can be helpful to understand the difference between how the encryption key server uses encryption keys and how other applications use them.
How the encryption key server processes encryption keys
TS1120 and later tape drives
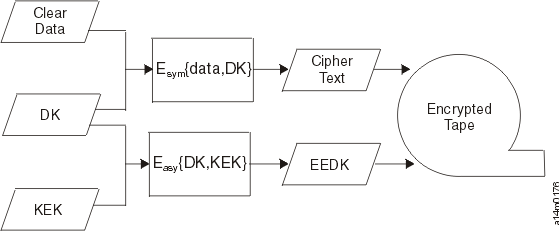
In system-managed and library-managed tape encryption, unencrypted data (clear text) is sent to the tape drive and converted to ciphertext with a symmetric 256-bit AES Data Key (DK) generated by the encryption key server. The ciphertext is then written to tape. The encryption key server uses a single, unique data key for each 3592 tape cartridge. This data key is also encrypted, or wrapped, by the encryption key server with the public key from an asymmetric Key Encrypting Key (KEK) pair. This process creates an Externally Encrypted Data Key (EEDK). The EEDK is written to the cartridge memory and to three more places on the tape media in the cartridge. The tape cartridge now holds both the encrypted data and the means to decrypt it for anyone that is holding the private part of the KEK pair. Figure 1 illustrates this process.
The data key is also wrapped a second time, possibly with the public key of another party, to create an extra EEDK. Both EEDKs can be stored on the tape cartridge. In this way, the tape cartridge can be shipped to a Business Partner that is holding the corresponding private key that would allow the data key to be unwrapped and the tape that is decrypted by the Business Partner.
Encryption key processing by other applications (an encryption key server not used)
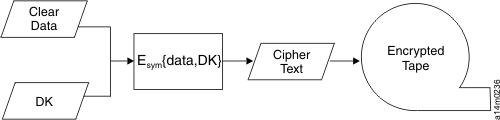
In application-managed tape encryption, unencrypted data (clear text) is sent to the tape drive and converted to ciphertext with a symmetric Data Key (DK) provided by the application, and is then written to tape. The data key is not stored anywhere on the tape cartridge. When the encrypted volume is written, the data key must be in a location available to the application, a server database, for example, in order for the volume to be read.
TS1120 and later tape drives can use applications such as Tivoli Storage Manager for application-managed encryption. Tivoli Storage Manager uses a single, unique data key for each tape cartridge.
Alternatively, the tape drives can be used by applications that use the T10 command set to complete encryption. The T10 command set uses symmetric 256-bit AES keys that are provided by the application. T10 can use multiple, unique data keys per tape cartridge, and even write encrypted data and clear data to the same tape cartridge. When the application encrypts a tape cartridge, it selects or generates a data key with a method determined by the application and sends it to the tape drive. The key is not wrapped with an asymmetric public key and it is not stored on the tape cartridge. When the encrypted data is written to tape, the data key must be in a location available to the application in order for the data to be read.
The process for application-managed tape encryption is shown in Figure 2.