What's new and changed in Watson Studio
The Watson™ Studio release and subsequent refreshes can include new features, bug fixes, and security updates. Refreshes appear in reverse chronological order, and only the refreshes that contain updates for Watson Studio are shown.
You can see a list of the new features for the platform and all of the services at What's new in IBM® Cloud Pak for Data.
Installing or upgrading Watson Studio
- Related documentation:
Refresh 16 of Cloud Pak for Data Version 3.5
A new version of Cloud Pak for Data was released in October 2022.
Operand version: 3.5.10
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2022-34903, CVE-2022-33099, CVE-2022-32208, CVE-2022-32206, CVE-2022-30115, CVE-2022-29824, CVE-2022-29155, CVE-2022-28506, CVE-2022-27782, CVE-2022-27781, CVE-2022-27780, CVE-2022-27779, CVE-2022-27778, CVE-2022-27776, CVE-2022-27774, CVE-2022-26691, CVE-2022-25878, CVE-2022-25314, CVE-2022-25313, CVE-2022-24765, CVE-2022-23990, CVE-2022-2289, CVE-2022-2288, CVE-2022-22576, CVE-2022-2257, CVE-2022-2231, CVE-2022-2097, CVE-2022-2068, CVE-2022-1927, CVE-2022-1897, CVE-2022-1785, CVE-2022-1720, CVE-2022-1629, CVE-2022-1621, CVE-2022-1619, CVE-2022-1586, CVE-2022-1354, CVE-2022-1292, CVE-2022-1271, CVE-2022-0563, CVE-2022-0530, CVE-2022-0529, CVE-2022-0391, CVE-2022-0351
CVE-2021-46822, CVE-2021-46195, CVE-2021-45346, CVE-2021-45078, CVE-2021-44906, CVE-2021-43618, CVE-2021-43519, CVE-2021-4217, CVE-2021-4209, CVE-2021-4166, CVE-2021-4069, CVE-2021-40528, CVE-2021-40330, CVE-2021-3997, CVE-2021-3974, CVE-2021-39537, CVE-2021-3927, CVE-2021-3903, CVE-2021-38185, CVE-2021-3800, CVE-2021-3796, CVE-2021-3778, CVE-2021-37322, CVE-2021-36222, CVE-2021-3601, CVE-2021-35942, CVE-2021-3541, CVE-2021-3537, CVE-2021-3520, CVE-2021-3518, CVE-2021-3517, CVE-2021-3516, CVE-2021-3487, CVE-2021-3468, CVE-2021-3467, CVE-2021-3426, CVE-2021-3421, CVE-2021-33574, CVE-2021-33560, CVE-2021-33197, CVE-2021-31879, CVE-2021-3177, CVE-2021-3115, CVE-2021-3114, CVE-2021-28153, CVE-2021-27218, CVE-2021-27212, CVE-2021-25317, CVE-2021-24032, CVE-2021-23980, CVE-2021-23336, CVE-2021-22947, CVE-2021-22925, CVE-2021-22924, CVE-2021-22898, CVE-2021-22876, CVE-2021-21300, CVE-2021-20294, CVE-2021-20266, CVE-2021-20197, CVE-2021-20193
CVE-2020-8492, CVE-2020-8285, CVE-2020-8284, CVE-2020-8231, CVE-2020-7595, CVE-2020-36230, CVE-2020-36229, CVE-2020-36228, CVE-2020-36227, CVE-2020-36226, CVE-2020-36225, CVE-2020-36224, CVE-2020-36223, CVE-2020-36222, CVE-2020-36221, CVE-2020-35524, CVE-2020-35523, CVE-2020-35522, CVE-2020-35512, CVE-2020-35507, CVE-2020-35496, CVE-2020-35495, CVE-2020-35494, CVE-2020-35493, CVE-2020-35448, CVE-2020-29362, CVE-2020-29361, CVE-2020-28367, CVE-2020-28366, CVE-2020-28362, CVE-2020-28196, CVE-2020-27619, CVE-2020-27618, CVE-2020-26154, CVE-2020-26137, CVE-2020-26116, CVE-2020-25219, CVE-2020-24977, CVE-2020-24553, CVE-2020-21674, CVE-2020-1968, CVE-2020-17541, CVE-2020-1752, CVE-2020-17049, CVE-2020-16845, CVE-2020-16599, CVE-2020-16593, CVE-2020-16592, CVE-2020-16591, CVE-2020-16590, CVE-2020-16156, CVE-2020-15719, CVE-2020-15095, CVE-2020-14422, CVE-2020-14155, CVE-2020-14145, CVE-2020-13790, CVE-2020-13776, CVE-2020-13645, CVE-2020-13631, CVE-2020-13529, CVE-2020-13435, CVE-2020-12762, CVE-2020-12413, CVE-2020-12401
CVE-2019-9937, CVE-2019-9936, CVE-2019-9923, CVE-2019-9674, CVE-2019-9169, CVE-2019-9077, CVE-2019-9075, CVE-2019-9074, CVE-2019-9071, CVE-2019-8906, CVE-2019-8905, CVE-2019-8457, CVE-2019-6462, CVE-2019-6461, CVE-2019-6128, CVE-2019-6111, CVE-2019-6110, CVE-2019-6109, CVE-2019-5827, CVE-2019-3860, CVE-2019-3859, CVE-2019-3842, CVE-2019-2708, CVE-2019-2201, CVE-2019-20807, CVE-2019-20388, CVE-2019-20218, CVE-2019-19956, CVE-2019-19924, CVE-2019-19906, CVE-2019-19880, CVE-2019-19645, CVE-2019-19603, CVE-2019-19244, CVE-2019-19204, CVE-2019-19203, CVE-2019-19012, CVE-2019-18348, CVE-2019-18276, CVE-2019-17595, CVE-2019-17594, CVE-2019-17543, CVE-2019-17451, CVE-2019-16866, CVE-2019-16777, CVE-2019-16775, CVE-2019-16276, CVE-2019-16163, CVE-2019-1563, CVE-2019-14250, CVE-2019-13753, CVE-2019-13752, CVE-2019-13751, CVE-2019-13565, CVE-2019-1349, CVE-2019-1348, CVE-2019-13224, CVE-2019-13115, CVE-2019-13057, CVE-2019-13050, CVE-2019-13012, CVE-2019-12972, CVE-2019-12900, CVE-2019-1010204, CVE-2019-1010180
CVE-2018-9252, CVE-2018-9234, CVE-2018-9055, CVE-2018-8740, CVE-2018-6954, CVE-2018-6872, CVE-2018-6759, CVE-2018-6323, CVE-2018-6003, CVE-2018-5784, CVE-2018-5764, CVE-2018-5360, CVE-2018-20839, CVE-2018-20786, CVE-2018-20685, CVE-2018-20673, CVE-2018-20671, CVE-2018-20657, CVE-2018-20651, CVE-2018-20623, CVE-2018-20622, CVE-2018-20570, CVE-2018-20483, CVE-2018-20482, CVE-2018-20406, CVE-2018-20002, CVE-2018-19932, CVE-2018-19876, CVE-2018-19543, CVE-2018-19542, CVE-2018-19541, CVE-2018-19540, CVE-2018-19539, CVE-2018-19211, CVE-2018-19210, CVE-2018-19139, CVE-2018-18873, CVE-2018-18701, CVE-2018-18607, CVE-2018-18606, CVE-2018-18605, CVE-2018-18508, CVE-2018-18484, CVE-2018-18483, CVE-2018-18309, CVE-2018-18064, CVE-2018-17985, CVE-2018-17794, CVE-2018-17360, CVE-2018-17101, CVE-2018-16435, CVE-2018-16429, CVE-2018-16428, CVE-2018-16335, CVE-2018-15919, CVE-2018-15209, CVE-2018-14567, CVE-2018-14404, CVE-2018-12934, CVE-2018-12699, CVE-2018-12698, CVE-2018-12697, CVE-2018-12641, CVE-2018-1125, CVE-2018-1123, CVE-2018-1121, CVE-2018-10801, CVE-2018-10779, CVE-2018-1000880, CVE-2018-1000879, CVE-2018-1000876, CVE-2018-1000654, CVE-2018-1000035, CVE-2018-1000030, CVE-2018-1000021
CVE-2017-9955, CVE-2017-9954, CVE-2017-9937, CVE-2017-9936, CVE-2017-9935, CVE-2017-9815, CVE-2017-9782, CVE-2017-9778, CVE-2017-9756, CVE-2017-9755, CVE-2017-9754, CVE-2017-9753, CVE-2017-9752, CVE-2017-9751, CVE-2017-9750, CVE-2017-9749, CVE-2017-9748, CVE-2017-9747, CVE-2017-9746, CVE-2017-9745, CVE-2017-9744, CVE-2017-9743, CVE-2017-9742, CVE-2017-9614, CVE-2017-9403, CVE-2017-9233, CVE-2017-9147, CVE-2017-9117, CVE-2017-9050, CVE-2017-9049, CVE-2017-9048, CVE-2017-9047, CVE-2017-9044, CVE-2017-9043, CVE-2017-9042, CVE-2017-9041, CVE-2017-9040, CVE-2017-9039, CVE-2017-9038, CVE-2017-8872, CVE-2017-8817, CVE-2017-8421, CVE-2017-8398, CVE-2017-8397, CVE-2017-8396, CVE-2017-8395, CVE-2017-8394, CVE-2017-8393, CVE-2017-8392, CVE-2017-7781, CVE-2017-7614, CVE-2017-7613, CVE-2017-7612, CVE-2017-7611, CVE-2017-7610, CVE-2017-7609, CVE-2017-7608, CVE-2017-7607, CVE-2017-7602, CVE-2017-7601, CVE-2017-7600, CVE-2017-7599, CVE-2017-7598, CVE-2017-7597, CVE-2017-7596, CVE-2017-7595, CVE-2017-7594, CVE-2017-7593, CVE-2017-7592, CVE-2017-7526, CVE-2017-7501, CVE-2017-7500, CVE-2017-7407, CVE-2017-7375, CVE-2017-7304, CVE-2017-7303, CVE-2017-7302, CVE-2017-7301, CVE-2017-7300, CVE-2017-7299, CVE-2017-7246, CVE-2017-7245, CVE-2017-7244, CVE-2017-7227, CVE-2017-7226, CVE-2017-7225, CVE-2017-7224, CVE-2017-7223, CVE-2017-7210, CVE-2017-7209, CVE-2017-7000, CVE-2017-6969, CVE-2017-6966, CVE-2017-6965, CVE-2017-6891, CVE-2017-6512, CVE-2017-6508, CVE-2017-6350, CVE-2017-6004, CVE-2017-5953, CVE-2017-5563, CVE-2017-5505, CVE-2017-5504, CVE-2017-5503, CVE-2017-5499, CVE-2017-5225, CVE-2017-18258, CVE-2017-18078, CVE-2017-18018, CVE-2017-17942, CVE-2017-17434, CVE-2017-17433, CVE-2017-17126, CVE-2017-17125, CVE-2017-17124, CVE-2017-17123, CVE-2017-17122, CVE-2017-17121, CVE-2017-17095, CVE-2017-17087, CVE-2017-17080, CVE-2017-16932, CVE-2017-16931, CVE-2017-16879, CVE-2017-16832, CVE-2017-16831, CVE-2017-16830, CVE-2017-16829, CVE-2017-16828, CVE-2017-16827, CVE-2017-16826, CVE-2017-16548, CVE-2017-15996, CVE-2017-15994, CVE-2017-15939, CVE-2017-15938, CVE-2017-15671, CVE-2017-15412, CVE-2017-15298, CVE-2017-15286, CVE-2017-15232, CVE-2017-15225, CVE-2017-15088, CVE-2017-15025, CVE-2017-15024, CVE-2017-15023, CVE-2017-15022, CVE-2017-15021, CVE-2017-15020, CVE-2017-14974, CVE-2017-14940, CVE-2017-14939, CVE-2017-14938, CVE-2017-14934, CVE-2017-14933, CVE-2017-14932, CVE-2017-14930, CVE-2017-14867, CVE-2017-14745, CVE-2017-14729, CVE-2017-14529, CVE-2017-14130, CVE-2017-14129, CVE-2017-14128, CVE-2017-14062, CVE-2017-13757, CVE-2017-13734, CVE-2017-13733, CVE-2017-13732, CVE-2017-13731, CVE-2017-13730, CVE-2017-13729, CVE-2017-13728, CVE-2017-13727, CVE-2017-13726, CVE-2017-13716, CVE-2017-13710, CVE-2017-13685, CVE-2017-12967, CVE-2017-12944, CVE-2017-12799, CVE-2017-12458, CVE-2017-12457, CVE-2017-12456, CVE-2017-12455, CVE-2017-12454, CVE-2017-12453, CVE-2017-12452, CVE-2017-12451, CVE-2017-12449, CVE-2017-11462, CVE-2017-11335, CVE-2017-11164, CVE-2017-11113, CVE-2017-11112, CVE-2017-11109, CVE-2017-10989, CVE-2017-10790, CVE-2017-10688, CVE-2017-10685, CVE-2017-10684, CVE-2017-10140, CVE-2017-1000382, CVE-2017-1000254, CVE-2017-1000158, CVE-2017-1000100, CVE-2017-0663, CVE-2017-0553
CVE-2016-9844, CVE-2016-9586, CVE-2016-9574, CVE-2016-9539, CVE-2016-9538, CVE-2016-9532, CVE-2016-9453, CVE-2016-9318, CVE-2016-9297, CVE-2016-9273, CVE-2016-9074, CVE-2016-8625, CVE-2016-8624, CVE-2016-8623, CVE-2016-8622, CVE-2016-8621, CVE-2016-8619, CVE-2016-8618, CVE-2016-8617, CVE-2016-8616, CVE-2016-8615, CVE-2016-7091, CVE-2016-6349, CVE-2016-6321, CVE-2016-6318, CVE-2016-6263, CVE-2016-6262, CVE-2016-6261, CVE-2016-6223, CVE-2016-6185, CVE-2016-6153, CVE-2016-5323, CVE-2016-5321, CVE-2016-5319, CVE-2016-5318, CVE-2016-5300, CVE-2016-5131, CVE-2016-5102, CVE-2016-4984, CVE-2016-4493, CVE-2016-4492, CVE-2016-4491, CVE-2016-4490, CVE-2016-4489, CVE-2016-4488, CVE-2016-4487, CVE-2016-4484, CVE-2016-4483, CVE-2016-4472, CVE-2016-4429, CVE-2016-4074, CVE-2016-4008, CVE-2016-3631, CVE-2016-3624, CVE-2016-3622, CVE-2016-3191, CVE-2016-3189, CVE-2016-2781, CVE-2016-2779, CVE-2016-2381, CVE-2016-2226, CVE-2016-2183, CVE-2016-2037, CVE-2016-1951, CVE-2016-1938, CVE-2016-1238, CVE-2016-1234, CVE-2016-10371, CVE-2016-10272, CVE-2016-10271, CVE-2016-10270, CVE-2016-10269, CVE-2016-10268, CVE-2016-10267, CVE-2016-10266, CVE-2016-10255, CVE-2016-10254, CVE-2016-10228, CVE-2016-10094, CVE-2016-10093, CVE-2016-10092, CVE-2016-0755
CVE-2015-8948, CVE-2015-8865, CVE-2015-8853, CVE-2015-8538, CVE-2015-8391, CVE-2015-8388, CVE-2015-8386, CVE-2015-8385, CVE-2015-8382, CVE-2015-8035, CVE-2015-7697, CVE-2015-7696, CVE-2015-7036, CVE-2015-5276, CVE-2015-5218, CVE-2015-5186, CVE-2015-5073, CVE-2015-3217, CVE-2015-3153, CVE-2015-2697, CVE-2015-2696, CVE-2015-2695, CVE-2015-2613, CVE-2015-2328, CVE-2015-2327, CVE-2015-2059, CVE-2015-20107, CVE-2015-1607, CVE-2015-1606, CVE-2015-1572, CVE-2015-1197, CVE-2015-0837, CVE-2015-0247, CVE-2015-0245
Refresh 15 of Cloud Pak for Data Version 3.5
A new version of Cloud Pak for Data was released in July 2022.
Operand version: 3.5.9
- Bug fixes
-
This release includes the following fixes:
- Issue: The DSX-HI pod log no longer provides up-to-update logging of jobs
submitted to Hadoop.
Resolution: The issue is now resolved.
- Issue: The DSX-HI pod log no longer provides up-to-update logging of jobs
submitted to Hadoop.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2017-9404, CVE-2020-10543, CVE-2020-10878, CVE-2020-12723, CVE-2021-23358, CVE-2021-3580, CVE-2021-44569, CVE-2021-44570, CVE-2021-44571, CVE-2021-44573, CVE-2021-44574, CVE-2021-44575, CVE-2021-44576, CVE-2021-44577, CVE-2022-1210, CVE-2022-1616, CVE-2022-1620, CVE-2022-1622, CVE-2022-1623, CVE-2022-26280
This release includes fixes for the following security issues for Jupyter Notebooks Python 3.7:
CVE-2018-25032, CVE-2020-10878, CVE-2020-12723, CVE-2020-17541, CVE-2020-19131, CVE-2020-35492, CVE-2020-35521, CVE-2020-35524, CVE-2021-23222, CVE-2021-3634, CVE-2021-3733, CVE-2021-41617, CVE-2021-44569, CVE-2021-44570, CVE-2021-44573, CVE-2021-44574, CVE-2021-44575, CVE-2021-44576, CVE-2021-44577, CVE-2022-1154, CVE-2022-1616, CVE-2022-1620, CVE-2022-1623, CVE-2022-21434, CVE-2022-21476, CVE-2022-21496, CVE-2022-22822, CVE-2022-22824, CVE-2022-22825, CVE-2022-29155
Refresh 14 of Cloud Pak for Data Version 3.5
A new version of Cloud Pak for Data was released in May 2022.
Operand version: 3.5.8
- New features
-
The 3.5.8 release of Watson Studio includes the following features and updates:
- Deprecation notice of Spark 2.4 Notebook environments
- Spark 2.4 is deprecated and will be removed in an upcoming release. Start using environments with Spark 3.0 in Watson Studio.
- Bug fixes
-
This release includes the following fixes:
- Issue: After deleting a notebook with a notebook job scheduled, the
notebook is still listed under the Assets tab of the project.
Resolution: The issue is now fixed.
- Issue: Notebook names including spaces cause an error 500 after syncing the
notebook with the project.
Resolution: Notebook names can now include spaces.
- Issue: After deleting a notebook with a notebook job scheduled, the
notebook is still listed under the Assets tab of the project.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2021-23566, CVE-2021-23841, CVE-2021-42694
Refresh 12 of Cloud Pak for Data Version 3.5
A new version of Cloud Pak for Data was released in March 2022.
Operand version: 3.5.7
- Bug fixes
-
This release includes the following fixes:
- Issue: Error appears when saving a JupyterLab file that uses the word
cellsin a.py/.txt/.mdfile.Resolution: The issue is now fixed.
- Issue: Error appears when saving a JupyterLab file that uses the word
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2016-9398, CVE-2019-13750, CVE-2016-7943, CVE-2016-1841, CVE-2015-7674, CVE-2020-23922, CVE-2021-26927, CVE-2021-27645, CVE-2016-9395, CVE-2017-2870, CVE-2017-6314, CVE-2016-7949, CVE-2021-42574, CVE-2018-7999, CVE-2016-6352, CVE-2017-13748, CVE-2015-9019, CVE-2021-33910, CVE-2021-41495, CVE-2017-13749, CVE-2016-7946, CVE-2016-2149, CVE-2016-7945, CVE-2021-20231, CVE-2019-20386, CVE-2021-20232, CVE-2016-3711, CVE-2021-23840, CVE-2015-7995, CVE-2016-10087, CVE-2020-25709, CVE-2017-13747, CVE-2020-27828, CVE-2016-4608, CVE-2019-18218, CVE-2021-3200, CVE-2016-2160, CVE-2021-44832, CVE-2015-8875, CVE-2017-13752, CVE-2020-14344, CVE-2016-4609, CVE-2016-2052, CVE-2016-7944, CVE-2016-3977, CVE-2015-7673, CVE-2021-27291, CVE-2016-9082, CVE-2016-7942, CVE-2019-5068, CVE-2016-7951, CVE-2017-13751, CVE-2016-4610, CVE-2016-10109, CVE-2021-20270, CVE-2019-20838, CVE-2016-7952, CVE-2017-14132, CVE-2016-9399, CVE-2016-9397, CVE-2020-24370, CVE-2016-10244, CVE-2017-9814, CVE-2021-37750, CVE-2018-19787, CVE-2016-1683, CVE-2017-18248, CVE-2021-26926, CVE-2020-16135, CVE-2018-14645, CVE-2017-7475, CVE-2017-15137, CVE-2020-1712, CVE-2016-8886, CVE-2016-7948, CVE-2016-1684, CVE-2016-7947, CVE-2016-4607, CVE-2021-3272, CVE-2016-7950, CVE-2015-8947, CVE-2020-25710, CVE-2021-33203, CVE-2020-10001, CVE-2018-14632, CVE-2019-13117, CVE-2020-3898, CVE-2015-7555, CVE-2017-8287, CVE-2017-16612, CVE-2017-6312, CVE-2019-13118, CVE-2017-8105, CVE-2021-3445, CVE-2021-41496, CVE-2018-6942, CVE-2017-6313, CVE-2017-15138, CVE-2016-4738
Refresh 10 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in January 2022.
Assembly version: 3.5.6
This release includes the following changes:
- Bug fixes
-
This release includes the following fixes:
- Issue: Excel files cannot be imported to a notebook that is stored in a
storage volume.
Resolution: Fixed importing Excel files to a notebook when it's stored in storage volume.
- Issue: Framework SKLearn is deprecated for versions of Cloud Pak for Data.
Resolution: Upgrade to the newest version of the platform. To learn about available frameworks on Cloud Pak for Data on different versions, see our frameworks documentation.
- Issue: The DSX-HI pod log no longer provides up-to-update logging of jobs
submitted to Hadoop.
Resolution: The issue is now resolved.
- Issue: Excel files cannot be imported to a notebook that is stored in a
storage volume.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2021-33574, CVE-2019-9633, CVE-2020-35448, CVE-2020-12762, CVE-2021-35588, CVE-2020-24370, CVE-2020-10001, CVE-2019-9924, CVE-2021-35567, CVE-2021-26927, CVE-2017-18018, CVE-2021-35564, CVE-2021-3572, CVE-2021-35565, CVE-2021-20231, CVE-2020-14155, CVE-2021-22922, CVE-2021-3796, CVE-2021-20284, CVE-2021-31535, CVE-2018-20673, CVE-2021-35561, CVE-2021-35586, CVE-2021-36084, CVE-2021-36087, CVE-2019-13751, CVE-2021-23440, CVE-2021-3778, CVE-2021-37714, CVE-2020-12399, CVE-2021-22947, CVE-2019-19603, CVE-2021-23840, CVE-2021-3733, CVE-2021-3426, CVE-2021-26926, CVE-2018-10237, CVE-2018-16429, CVE-2021-35578, CVE-2021-3200, CVE-2021-23841, CVE-2021-22925, CVE-2019-5827, CVE-2020-8908, CVE-2021-41617, CVE-2021-35550, CVE-2021-20266, CVE-2020-27828, CVE-2018-12700, CVE-2021-29425, CVE-2021-33197, CVE-2019-18218, CVE-2021-3272, CVE-2019-17594, CVE-2021-33503, CVE-2021-22923, CVE-2021-20232, CVE-2021-28153, CVE-2019-20838, CVE-2019-17595, CVE-2021-35556, CVE-2020-13435, CVE-2021-36086, CVE-2021-20271, CVE-2021-22876, CVE-2021-22946, CVE-2021-27645, CVE-2021-35603, CVE-2019-13750, CVE-2021-3114, CVE-2021-22898, CVE-2021-33560, CVE-2021-36085, CVE-2021-35942, CVE-2021-35559, CVE-2021-3445, CVE-2020-13956, CVE-2020-14145, CVE-2021-37750, CVE 2021-45105, CVE 2021-45046
Refresh 9 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in October 2021.
Assembly version: 3.5.5
This release includes the following changes:
- Bug fixes
-
This release includes the following fixes:
- Issue: Publishing a notebook to a catalog fails.
Resolution: The issue is now fixed.
- Issue: The notebook performance on Power is slower than the notebook
performance on x86.
Resolution: The issue is now fixed.
- Issue: When you create a notebook and run a cell using Plotly, you cannot
see the graph from the notebook view.
Resolution: The issue is now fixed.
- Issue: Notebook performance decreases on an Open-CE
environment.
Resolution: The issue is now fixed.
- Issue: Permission issues occur when installing packages within a
notebook.
Resolution: The issue is now fixed.
- Issue: Jobs that are in a pending state with the event
FailedSchedulingare deactivated.Resolution: The issue is now fixed.
- Issue:
Jupyter Notebooks with R 3.6 are unable to use the readr library
because the Jupyter Notebooks with R 3.6 environment is missing the
tzdata system package. Missing the zdata system package prevents the library from functioning.
Resolution: The issue is now fixed.
- Issue: After multiple jobs are launched, jobs that are pending aren't
completed.
Resolution: The timeout can now be increased. It is configurable through the
APP_ENV_JOB_TIMEOUT_INTERVAL_SECSenvironment variable which defaults to 600 (seconds).
- Issue: Publishing a notebook to a catalog fails.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2021-31535, CVE-2021-20271, CVE-2021-27290, CVE-2020-7774, CVE-2021-3541, CVE-2021-27218, CVE-2021-2341, CVE-2021-3518, CVE-2021-3537, CVE-2021-32723, CVE-2019-19246, CVE-2021-33910, CVE-2021-2388, CVE-2020-25648, CVE-2021-3517, CVE-2020-15945, CVE-2020-13956, CVE-2021-22918, CVE-2021-3516, CVE-2021-3520, CVE-2021-33503, CVE-2021-23362, CVE-2021-2369, CVE-2021-23343, CVE-2021-3421, CVE-2021-31879
Refresh 7 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in July 2021.
Assembly version: 3.5.4
- Bug fixes
-
This release includes the following fix:
- Issue: The
application/zipMIME type is the only MIME type that's validated when model types are created. Other MIME types weren't validated.Resolution: Multiple MIME types are now validated.
- Issue: Critical and high vulnerability issues were
found.
Resolution: Critical and high vulnerability issues are now resolved.
- Issue: The Legacy
runtime-definition name is incorrect.
Resolution: The Legacy runtime-definition name is now correct.
- Issue: Notebooks cannot install the LightGBM
package.
Resolution: Notebooks can now install the LightGBM package.
- Issue: The
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2015-2059, CVE-2017-15708, CVE-2017-18869, CVE-2017-7656, CVE-2017-7657, CVE-2017-7658, CVE-2017-9735, CVE-2018-0734, CVE-2018-0735, CVE-2018-1000168, CVE-2018-1002204, CVE-2018-1109, CVE-2018-12116, CVE-2018-12121, CVE-2018-12122, CVE-2018-12123, CVE-2018-14718, CVE-2018-20834, CVE-2018-7489, CVE-2019-10742, CVE-2019-10906, CVE-2019-11236, CVE-2019-11324, CVE-2019-13173, CVE-2019-15604, CVE-2019-15605, CVE-2019-15606, CVE-2019-16775, CVE-2019-16776, CVE-2019-16777, CVE-2019-17195, CVE-2019-20330, CVE-2019-25013, CVE-2019-5737, CVE-2020-10672, CVE-2020-10673, CVE-2020-10968, CVE-2020-10969, CVE-2020-11111, CVE-2020-11112, CVE-2020-11113, CVE-2020-11619, CVE-2020-11620, CVE-2020-12399, CVE-2020-12400, CVE-2020-12403, CVE-2020-12723, CVE-2020-12762, CVE-2020-13776, CVE-2020-14060, CVE-2020-14061, CVE-2020-14062, CVE-2020-14195, CVE-2020-14344, CVE-2020-14363, CVE-2020-15095, CVE-2020-15138, CVE-2020-15168, CVE-2020-1971, CVE-2020-24025, CVE-2020-24616, CVE-2020-24750, CVE-2020-25648, CVE-2020-25649, CVE-2020-25692, CVE-2020-26137, CVE-2020-27618, CVE-2020-28168, CVE-2020-28469, CVE-2020-28472, CVE-2020-28477, CVE-2020-28481, CVE-2020-28493, CVE-2020-28498, CVE-2020-28499, CVE-2020-28500, CVE-2020-29361, CVE-2020-29362, CVE-2020-29363, CVE-2020-35490, CVE-2020-35491, CVE-2020-35728, CVE-2020-36179, CVE-2020-36180, CVE-2020-36181, CVE-2020-36182, CVE-2020-36183, CVE-2020-36184, CVE-2020-36185, CVE-2020-36186, CVE-2020-36187, CVE-2020-36188, CVE-2020-36189, CVE-2020-36242, CVE-2020-6802, CVE-2020-6816, CVE-2020-6817, CVE-2020-6829, CVE-2020-7598, CVE-2020-7608, CVE-2020-7661, CVE-2020-7754, CVE-2020-7774, CVE-2020-7788, CVE-2020-7789, CVE-2020-8116, CVE-2020-8174, CVE-2020-8175, CVE-2020-8231, CVE-2020-8252, CVE-2020-8265, CVE-2020-8284, CVE-2020-8285, CVE-2020-8286, CVE-2020-8287, CVE-2020-8840, CVE-2020-8927, CVE-2020-9546, CVE-2020-9547, CVE-2020-9548, CVE-2021-20066, CVE-2021-20190, CVE-2021-20271, CVE-2021-20305, CVE-2021-21366, CVE-2021-22883, CVE-2021-22884, CVE-2021-23337, CVE-2021-23341, CVE-2021-23840, CVE-2021-23841, CVE-2021-24033, CVE-2021-27219, CVE-2021-27290, CVE-2021-3326, CVE-2021-3449, CVE-2021-3450
CVE-2019-12402, CVE-2019-25013, CVE-2020-12399, CVE-2020-12762, CVE-2020-13956, CVE-2020-14344, CVE-2020-14363, CVE-2020-26137, CVE-2020-27618, CVE-2020-27783, CVE-2020-28493, CVE-2020-29361, CVE-2020-29362, CVE-2020-29363, CVE-2020-7754, CVE-2020-7774, CVE-2020-7788, CVE-2020-8116, CVE-2020-8231, CVE-2020-8284, CVE-2020-8285, CVE-2020-8286, CVE-2020-8927, CVE-2021-20271, CVE-2021-27219, CVE-2021-28957, CVE-2021-3326
CVE-2019-25013, CVE-2020-12399, CVE-2020-12762, CVE-2020-14344, CVE-2020-14363, CVE-2020-26137, CVE-2020-27618, CVE-2020-27783, CVE-2020-28493, CVE-2020-29361, CVE-2020-29362, CVE-2020-29363, CVE-2020-7754, CVE-2020-7774, CVE-2020-7788, CVE-2020-8116, CVE-2020-8231, CVE-2020-8284, CVE-2020-8285, CVE-2020-8286, CVE-2020-8927, CVE-2021-20271, CVE-2021-27219, CVE-2021-28957, CVE-2021-3326
Refresh 5 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in April 2021.
Assembly version: 3.5.3
- New features
-
The 3.5.3 release of Watson Studio includes the following features and updates:
- The Default Python 3.7 environment includes new open source library versions
- The Default Python 3.7 environment now includes the latest open source versions of many popular
machine learning libraries like TensorFlow, XGBoost and PyTorch.
The old Default Python 3.7 environment is deprecated and was renamed as Default Python 3.7 (legacy). You should start using the new Default Python 3.7 environment to run your existing notebooks.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2017-15095,CVE-2019-14540,CVE-2019-14893, CVE-2019-16335, CVE-2019-16942, CVE-2019-17267, CVE-2019-20330, CVE-2020-10672, CVE-2020-10673, CVE-2020-10968, CVE-2020-10969, CVE-2020-11111, CVE-2020-11112, CVE-2020-11113, CVE-2020-11619, CVE-2020-11620, CVE-2020-14060, CVE-2020-14061, CVE-2020-14062, CVE-2020-14195, CVE-2020-15138, CVE-2020-24616, CVE-2020-24750, CVE-2020-26137, CVE-2020-28472, CVE-2020-28493, CVE-2020-7212, CVE-2020-7788, CVE-2020-8116, CVE-2020-8265, CVE-2020-8277, CVE-2020-8287, CVE-2020-8840, CVE-2020-9546, CVE-2020-9547, CVE-2020-9548
CVE-2017-18869, CVE-2018-0734, CVE-2018-0735, CVE-2018-1000168, CVE-2018-12116, CVE-2018-12121, CVE-2018-12122, CVE-2018-12123, CVE-2018-20834, CVE-2019-10906, CVE-2019-11236, CVE-2019-11324, CVE-2019-12402, CVE-2019-13173, CVE-2019-15604, CVE-2019-15605, CVE-2019-15606, CVE-2019-16775, CVE-2019-16776, CVE-2019-16777, CVE-2019-20838, CVE-2019-25013, CVE-2019-5737, CVE-2020-12399, CVE-2020-12400, CVE-2020-12401, CVE-2020-12403, CVE-2020-12723, CVE-2020-12762, CVE-2020-13776, CVE-2020-13956, CVE-2020-14155, CVE-2020-14343, CVE-2020-14344, CVE-2020-14363, CVE-2020-15095, CVE-2020-15945, CVE-2020-1971, CVE-2020-25648, CVE-2020-25658, CVE-2020-26137, CVE-2020-26266, CVE-2020-26268, CVE-2020-26270, CVE-2020-26271, CVE-2020-27618, CVE-2020-27783, CVE-2020-28493, CVE-2020-29361, CVE-2020-29362, CVE-2020-29363, CVE-2020-35521, CVE-2020-35522, CVE-2020-35523, CVE-2020-35524, CVE-2020-35653, CVE-2020-35654, CVE-2020-35655, CVE-2020-36242, CVE-2020-6802, CVE-2020-6816, CVE-2020-6817, CVE-2020-6829, CVE-2020-7598, CVE-2020-7608, CVE-2020-7754, CVE-2020-7774, CVE-2020-7788, CVE-2020-8116, CVE-2020-8174, CVE-2020-8231, CVE-2020-8252, CVE-2020-8265, CVE-2020-8284, CVE-2020-8285, CVE-2020-8286, CVE-2020-8287, CVE-2020-8927, CVE-2021-20197, CVE-2021-20231, CVE-2021-20232, CVE-2021-20271, CVE-2021-20305, CVE-2021-22876, CVE-2021-22883, CVE-2021-22884, CVE-2021-23362, CVE-2021-23840, CVE-2021-23841, CVE-2021-25289, CVE-2021-25290, CVE-2021-25291, CVE-2021-25292, CVE-2021-25293, CVE-2021-27218, CVE-2021-27219, CVE-2021-27290, CVE-2021-27921, CVE-2021-27922, CVE-2021-27923, CVE-2021-28153, CVE-2021-28957, CVE-2021-3326, CVE-2021-3449, CVE-2021-3450, CVE-2021-3487
Refresh 3 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in February 2021.
Assembly version: 3.5.2
This release includes the following changes:
- Bug fixes
-
This release includes the following fixes:
- Issue: The
page
for the Generic JDBC connection and the SAP HANA connection incorrectly contains a “jdbc” selection.
Resolution: This problem is fixed.
- Issue: Jupyter
notebook runtimes, including those started for JupyterLab, and the GPU runtimes are not shutdown
automatically, although the default idle timeout or the user configured idle timeout was reached.
Resolution: This problem is fixed.
- Issue:After customizing the Jupyter Notebooks with R 3.6 pod idle timeout
setting, the Jupyter Notebooks with R 3.6 pod doesn't close.
Resolution: The Jupyter Notebooks with R 3.6 pod now closes according to the idle timeout setting.
- Issue: The
page
for the Generic JDBC connection and the SAP HANA connection incorrectly contains a “jdbc” selection.
Refresh 2 of Cloud Pak for Data Version 3.5
A new version of Watson Studio was released in January 2021.
Assembly version: 3.5.1
This release includes the following changes:
- New features
-
You must install Version 3.5.1 of the Watson Studio service if you want to install the service on Red Hat® OpenShift® 4.6.
In addition this release also includes the following features and updates:
- CPDCTL for notebook lifecycle management
- You can now use CPDCTL
command-line interface to manage the lifecycle of notebooks. By using the notebook CLI, you
can automate the flow for creating notebooks or scripts and running jobs, moving notebooks between
projects in Watson Studio, and adding
custom libraries to notebook runtime environments.
For details on using the CPCTL commands in a notebook, see Notebooks.
- Bug fixes
-
This release includes the following fixes:
- Issue:
Jupyter Notebooks with R 3.6 are unable to use the readr library from
tidyverse. The Jupyter R environment is missing the tzdata system package, which is preventing the
library from functioning.
Resolution: Jupyter Notebooks with R 3.6, using the readR library should correctly parse the CSV file into an R data frame.
- Issue: Customized branding doesn't support multi-byte characters.
Resolution: Customized branding now supports multi-byte characters.
- Issue: Collaborators who are assigned an editor role cannot edit the configuration of
jobs that other users created.
Resolution: Collaborators who are assigned an editor role can now edit the configuration of jobs that other users created.
- Issue:
Jupyter Notebooks with R 3.6 are unable to use the readr library from
tidyverse. The Jupyter R environment is missing the tzdata system package, which is preventing the
library from functioning.
Initial release of Cloud Pak for Data Version 3.5
A new version of Watson Studiowas released as part of Cloud Pak for Data Version 3.5.
Assembly version: 3.5.0
This release includes the following changes:
- New features
-
- New jobs interface for running and scheduling notebooks and Data Refinery flows
- The user interface gives you a unified view of the job information.
You can create the jobs from either of the following locations:
- The user interface for the service
- The Assets page of a project
For details, see Jobs in a project.
- New visualization charts
- You can use the following visualization charts with Data Refinery and SPSS® Modeler:
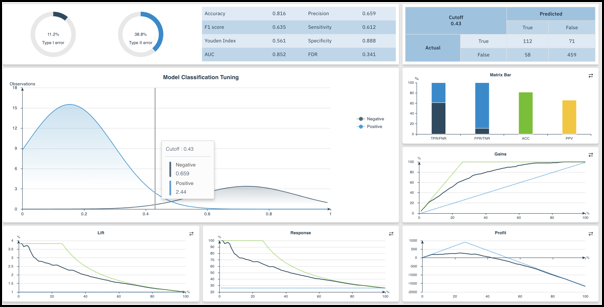
- Evaluation charts
- Evaluation charts are combination charts that measure the quality of a binary classifier. You
need three columns for input: actual (target) value, predict value, and confidence (0 or 1). Move
the slider in the Cutoff chart to dynamically update the other charts. The ROC and other charts are
standard measurements of the classifier.
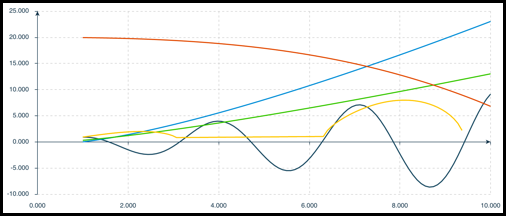
- Math curve charts
- Math curve charts display a group of curves based on equations that you enter. You do not use a
data set with this chart. Instead, you use it to compare the results with the data set in another
chart, like the scatter plot chart.
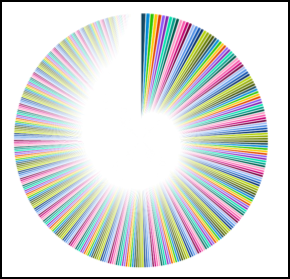
- Sunburst charts
- Sunburst charts display different depths of hierarchical groups. The Sunburst chart was formerly
an option in the Treemap chart.
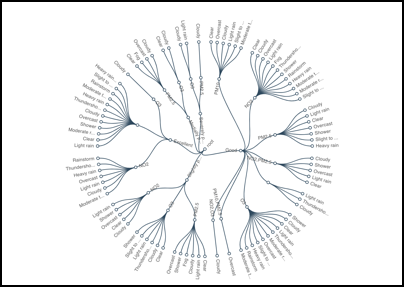
- Tree charts
- Tree charts represent a hierarchy in a tree-like structure. The Tree chart consists of a root
node, line connections called branches that represent the relationships and connections between the
members, and leaf nodes that do not have child nodes. The Tree chart was formerly an option in the
Treemap chart.
For the full list of available charts, see Visualizing your data.
- New project settings
- When you create a project, you can select the following options:
- Mark the project as sensitive
- Marking a project as sensitive prevents members of a project from moving data assets out of the
project.
For details, see Marking a project as sensitive.
- Log all project activities
- Logging all project activity tracks detailed project activity and creates a full activities log,
which you can download to view.
For details, see Logging project activity.
- New connections
- Watson Studio can connect to:
- Amazon RDS for MySQL
- Amazon RDS for PostgreSQL
- Apache Cassandra
- Apache Derby
- Box
- Elasticsearch
- HTTP
- IBM Data Virtualization Manager for z/OS®
- IBM Db2® Event Store
- IBM SPSS Analytic Server
- MariaDB
- Microsoft Azure Blob Storage
- Microsoft Azure Cosmos DB
- MongoDB
- SAP HANA
- Storage volume
In addition, the following connection names have changed:- PureData System for Analytics is now called Netezza® (PureData® System for Analytics).
Your previous settings for the connection remain the same. Only the name for the connection type changed.
- New SSL encryption support for connections
- The following
connections now support SSL encryption in Watson Studio:
- Amazon Redshift
- Cloudera Impala
- IBM Db2 for z/OS
- IBM Db2 Warehouse
- IBM Informix®
- IBM Netezza (PureData System for Analytics)
- Microsoft Azure SQL Database
- Microsoft SQL Server
- Pivotal Greenplum
- PostgreSQL
- Sybase
- Support for Python 3.7
- The default Python environment version in Watson Studio
Watson Studio is now Python 3.7.
Python 3.6 is being deprecated. You can continue to use the Python 3.6 environments; however you will be notified that you should move to a Python 3.7 environment.
When you switch from Python 3.6 to Python 3.7, you might need to update your code if the versions of open source libraries that you use are different in Python 3.7.
- Spark 3.0
- You can run analytical assets from Watson Studio analytics projects in a Spark 3
environment.
If you use the Spark Jobs REST APIs, provided by Analytics Engine Powered by Apache Spark, to run Spark jobs or applications on your Cloud Pak for Data cluster, you can use the Spark 3.0 template.
- Notebook execution progress restored
- If you accidentally close the browser window while your notebook is still running, or if you are logged out by the system during a long running job, the notebook will continue running and all output cells are restored when you open the notebook again. The execution progress of a notebook can be restored only for notebooks that run in a local kernel. If your notebook runs on a Spark or Hadoop cluster, and you open the notebook again, any notebook changes that were not saved are lost.
- Use a self-signed certificate to authenticate to enterprise Git repositories
- If you want to store your analytics project in an enterprise-grade instance of Git, such as GitHub Enterprise, and your instance uses a self-signed certificate for authentication, you can specify the self-signed certificate in PEM format when you add your personal access token to Cloud Pak for Data.