What's new and changed in Data Refinery
The Data Refinery release and subsequent refreshes can include new features, bug fixes, and security updates. Refreshes appear in reverse chronological order, and only the refreshes that contain updates for Data Refinery are shown.
You can see a list of the new features for the platform and all of the services at What's new in IBM Cloud Pak for Data?
Installing or upgrading Data Refinery
Data Refinery is not separately installable. Data Refinery is installed or upgraded when you install or upgrade Watson™ Knowledge Catalog or Watson Studio.
- Watson Knowledge Catalog
-
- Related documentation:
- Watson Studio
-
- Related documentation:
Refresh 16 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in October 2022.
Assembly version: 3.5.11
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2022-33099, CVE-2022-33068, CVE-2022-31813, CVE-2022-30522, CVE-2022-30115, CVE-2022-29404, CVE-2022-29155, CVE-2022-28615, CVE-2022-28614, CVE-2022-27781, CVE-2022-27780, CVE-2022-27779, CVE-2022-27778, CVE-2022-27406, CVE-2022-27405, CVE-2022-27404, CVE-2022-27337, CVE-2022-26377, CVE-2022-25310, CVE-2022-25309, CVE-2022-25308, CVE-2022-24765, CVE-2022-23990, CVE-2022-23943, CVE-2022-2344, CVE-2022-2343, CVE-2022-2289, CVE-2022-2288, CVE-2022-2287, CVE-2022-2286, CVE-2022-2285, CVE-2022-22844, CVE-2022-2284, CVE-2022-22721, CVE-2022-22719, CVE-2022-2257, CVE-2022-2231, CVE-2022-2210, CVE-2022-2208, CVE-2022-2207, CVE-2022-2206, CVE-2022-2183, CVE-2022-2182, CVE-2022-2175, CVE-2022-2129, CVE-2022-2126, CVE-2022-2125, CVE-2022-2124, CVE-2022-2058, CVE-2022-2057, CVE-2022-2056, CVE-2022-1720, CVE-2022-1629, CVE-2022-1621, CVE-2022-1619, CVE-2022-1355, CVE-2022-1154, CVE-2022-1122, CVE-2022-0924, CVE-2022-0908, CVE-2022-0891, CVE-2022-0865, CVE-2022-0563, CVE-2022-0562, CVE-2022-0561, CVE-2022-0530, CVE-2022-0529, CVE-2022-0359, CVE-2022-0351
CVE-2021-46822, CVE-2021-46195, CVE-2021-45949, CVE-2021-45944, CVE-2021-45346, CVE-2021-45078, CVE-2021-43818, CVE-2021-43618, CVE-2021-43519, CVE-2021-4217, CVE-2021-4209, CVE-2021-4193, CVE-2021-4192, CVE-2021-4189, CVE-2021-4166, CVE-2021-4069, CVE-2021-40330, CVE-2021-4019, CVE-2021-3997, CVE-2021-3984, CVE-2021-3974, CVE-2021-39537, CVE-2021-3927, CVE-2021-3903, CVE-2021-3872, CVE-2021-38185, CVE-2021-3796, CVE-2021-3778, CVE-2021-3737, CVE-2021-3733, CVE-2021-37322, CVE-2021-36978, CVE-2021-3618, CVE-2021-36160, CVE-2021-3601, CVE-2021-3575, CVE-2021-3487, CVE-2021-3468, CVE-2021-3426, CVE-2021-33197, CVE-2021-33193, CVE-2021-31879, CVE-2021-3177, CVE-2021-3115, CVE-2021-3114, CVE-2021-30641, CVE-2021-29338, CVE-2021-28957, CVE-2021-27918, CVE-2021-27212, CVE-2021-26690, CVE-2021-25317, CVE-2021-24032, CVE-2021-23336, CVE-2021-22570, CVE-2021-21300, CVE-2021-20294, CVE-2021-20197, CVE-2021-20193
CVE-2020-8492, CVE-2020-7595, CVE-2020-36230, CVE-2020-36229, CVE-2020-36228, CVE-2020-36227, CVE-2020-36226, CVE-2020-36225, CVE-2020-36224, CVE-2020-36223, CVE-2020-36222, CVE-2020-36221, CVE-2020-35524, CVE-2020-35523, CVE-2020-35522, CVE-2020-35512, CVE-2020-35507, CVE-2020-35496, CVE-2020-35495, CVE-2020-35494, CVE-2020-35493, CVE-2020-35452, CVE-2020-35448, CVE-2020-28367, CVE-2020-28366, CVE-2020-28362, CVE-2020-27845, CVE-2020-27844, CVE-2020-27843, CVE-2020-27842, CVE-2020-27841, CVE-2020-27824, CVE-2020-27823, CVE-2020-27814, CVE-2020-27783, CVE-2020-27778, CVE-2020-27748, CVE-2020-27619, CVE-2020-26137, CVE-2020-26116, CVE-2020-24553, CVE-2020-21674, CVE-2020-1968, CVE-2020-19131, CVE-2020-17541, CVE-2020-17538, CVE-2020-1752, CVE-2020-17049, CVE-2020-16845, CVE-2020-16599, CVE-2020-16593, CVE-2020-16592, CVE-2020-16591, CVE-2020-16590, CVE-2020-16310, CVE-2020-16309, CVE-2020-16308, CVE-2020-16307, CVE-2020-16306, CVE-2020-16305, CVE-2020-16304, CVE-2020-16303, CVE-2020-16302, CVE-2020-16301, CVE-2020-16300, CVE-2020-16299, CVE-2020-16298, CVE-2020-16297, CVE-2020-16296, CVE-2020-16295, CVE-2020-16294, CVE-2020-16293, CVE-2020-16292, CVE-2020-16291, CVE-2020-16290, CVE-2020-16289, CVE-2020-16288, CVE-2020-16287, CVE-2020-16156, CVE-2020-15719, CVE-2020-15389, CVE-2020-15095, CVE-2020-14422, CVE-2020-14373, CVE-2020-14344, CVE-2020-14145, CVE-2020-13790, CVE-2020-13631, CVE-2020-13529, CVE-2020-12413, CVE-2020-10001
CVE-2019-9937, CVE-2019-9936, CVE-2019-9923, CVE-2019-9674, CVE-2019-9543, CVE-2019-9077, CVE-2019-9075, CVE-2019-9074, CVE-2019-8906, CVE-2019-8905, CVE-2019-8457, CVE-2019-6988, CVE-2019-6462, CVE-2019-6461, CVE-2019-6128, CVE-2019-6111, CVE-2019-6110, CVE-2019-6109, CVE-2019-5068, CVE-2019-3860, CVE-2019-3859, CVE-2019-2201, CVE-2019-20807, CVE-2019-20795, CVE-2019-20388, CVE-2019-20218, CVE-2019-19956, CVE-2019-19924, CVE-2019-19906, CVE-2019-19880, CVE-2019-19645, CVE-2019-19244, CVE-2019-19204, CVE-2019-19203, CVE-2019-19012, CVE-2019-18348, CVE-2019-17567, CVE-2019-17543, CVE-2019-17451, CVE-2019-16866, CVE-2019-16777, CVE-2019-16775, CVE-2019-16276, CVE-2019-16163, CVE-2019-1563, CVE-2019-14250, CVE-2019-13753, CVE-2019-13752, CVE-2019-13565, CVE-2019-1349, CVE-2019-1348, CVE-2019-13224, CVE-2019-13118, CVE-2019-13117, CVE-2019-13115, CVE-2019-13057, CVE-2019-13050, CVE-2019-12973, CVE-2019-12972, CVE-2019-12900, CVE-2019-12360, CVE-2019-11360, CVE-2019-11026, CVE-2019-1010204, CVE-2019-1010180, CVE-2019-10092
CVE-2018-9918, CVE-2018-9234, CVE-2018-8740, CVE-2018-7999, CVE-2018-6954, CVE-2018-6942, CVE-2018-6872, CVE-2018-6869, CVE-2018-6759, CVE-2018-6540, CVE-2018-6484, CVE-2018-6381, CVE-2018-6323, CVE-2018-6003, CVE-2018-5784, CVE-2018-5764, CVE-2018-5360, CVE-2018-20846, CVE-2018-20839, CVE-2018-20685, CVE-2018-20657, CVE-2018-20483, CVE-2018-20482, CVE-2018-20406, CVE-2018-20002, CVE-2018-19932, CVE-2018-19787, CVE-2018-19478, CVE-2018-19211, CVE-2018-19210, CVE-2018-18701, CVE-2018-18700, CVE-2018-18607, CVE-2018-18606, CVE-2018-18605, CVE-2018-18508, CVE-2018-18484, CVE-2018-18483, CVE-2018-18064, CVE-2018-17985, CVE-2018-17794, CVE-2018-17360, CVE-2018-16435, CVE-2018-16429, CVE-2018-16428, CVE-2018-16376, CVE-2018-16335, CVE-2018-15919, CVE-2018-14567, CVE-2018-14404, CVE-2018-12934, CVE-2018-12699, CVE-2018-12698, CVE-2018-1125, CVE-2018-1123, CVE-2018-1121, CVE-2018-10801, CVE-2018-1000880, CVE-2018-1000879, CVE-2018-1000654, CVE-2018-1000035, CVE-2018-1000030, CVE-2018-1000021
CVE-2017-9955, CVE-2017-9954, CVE-2017-9937, CVE-2017-9936, CVE-2017-9935, CVE-2017-9865, CVE-2017-9835, CVE-2017-9815, CVE-2017-9814, CVE-2017-9778, CVE-2017-9756, CVE-2017-9755, CVE-2017-9754, CVE-2017-9753, CVE-2017-9752, CVE-2017-9751, CVE-2017-9750, CVE-2017-9749, CVE-2017-9748, CVE-2017-9747, CVE-2017-9746, CVE-2017-9745, CVE-2017-9744, CVE-2017-9743, CVE-2017-9742, CVE-2017-9740, CVE-2017-9739, CVE-2017-9727, CVE-2017-9726, CVE-2017-9620, CVE-2017-9619, CVE-2017-9618, CVE-2017-9614, CVE-2017-9612, CVE-2017-9611, CVE-2017-9610, CVE-2017-9408, CVE-2017-9406, CVE-2017-9403, CVE-2017-9233, CVE-2017-9216, CVE-2017-9210, CVE-2017-9209, CVE-2017-9208, CVE-2017-9147, CVE-2017-9117, CVE-2017-9083, CVE-2017-9050, CVE-2017-9049, CVE-2017-9048, CVE-2017-9047, CVE-2017-9044, CVE-2017-9043, CVE-2017-9042, CVE-2017-9041, CVE-2017-9040, CVE-2017-9039, CVE-2017-9038, CVE-2017-8908, CVE-2017-8872, CVE-2017-8871, CVE-2017-8834, CVE-2017-8817, CVE-2017-8786, CVE-2017-8421, CVE-2017-8398, CVE-2017-8397, CVE-2017-8396, CVE-2017-8395, CVE-2017-8394, CVE-2017-8393, CVE-2017-8392, CVE-2017-8287, CVE-2017-8105, CVE-2017-7975, CVE-2017-7960, CVE-2017-7885, CVE-2017-7867, CVE-2017-7781, CVE-2017-7614, CVE-2017-7613, CVE-2017-7612, CVE-2017-7611, CVE-2017-7610, CVE-2017-7609, CVE-2017-7608, CVE-2017-7607, CVE-2017-7602, CVE-2017-7601, CVE-2017-7600, CVE-2017-7599, CVE-2017-7598, CVE-2017-7597, CVE-2017-7596, CVE-2017-7595, CVE-2017-7594, CVE-2017-7593, CVE-2017-7592, CVE-2017-7526, CVE-2017-7515, CVE-2017-7511, CVE-2017-7501, CVE-2017-7500, CVE-2017-7475, CVE-2017-7407, CVE-2017-7375, CVE-2017-7304, CVE-2017-7303, CVE-2017-7302, CVE-2017-7301, CVE-2017-7300, CVE-2017-7299, CVE-2017-7246, CVE-2017-7245, CVE-2017-7244, CVE-2017-7227, CVE-2017-7226, CVE-2017-7225, CVE-2017-7224, CVE-2017-7223, CVE-2017-7210, CVE-2017-7209, CVE-2017-7000, CVE-2017-6969, CVE-2017-6966, CVE-2017-6965, CVE-2017-6891, CVE-2017-6512, CVE-2017-6508, CVE-2017-6350, CVE-2017-6004, CVE-2017-5981, CVE-2017-5980, CVE-2017-5979, CVE-2017-5978, CVE-2017-5977, CVE-2017-5976, CVE-2017-5975, CVE-2017-5974, CVE-2017-5953, CVE-2017-5951, CVE-2017-5563, CVE-2017-5225, CVE-2017-18258, CVE-2017-18186, CVE-2017-18185, CVE-2017-18184, CVE-2017-18183, CVE-2017-18078, CVE-2017-18018, CVE-2017-17942, CVE-2017-17479, CVE-2017-17434, CVE-2017-17433, CVE-2017-17126, CVE-2017-17125, CVE-2017-17124, CVE-2017-17123, CVE-2017-17122, CVE-2017-17121, CVE-2017-17095, CVE-2017-17087, CVE-2017-17080, CVE-2017-16932, CVE-2017-16931, CVE-2017-16879, CVE-2017-16832, CVE-2017-16831, CVE-2017-16830, CVE-2017-16829, CVE-2017-16828, CVE-2017-16827, CVE-2017-16826, CVE-2017-16612, CVE-2017-16548, CVE-2017-15996, CVE-2017-15994, CVE-2017-15939, CVE-2017-15938, CVE-2017-15671, CVE-2017-15565, CVE-2017-15422, CVE-2017-15412, CVE-2017-15298, CVE-2017-15286, CVE-2017-15232, CVE-2017-15225, CVE-2017-15088, CVE-2017-15025, CVE-2017-15024, CVE-2017-15023, CVE-2017-15022, CVE-2017-15021, CVE-2017-15020, CVE-2017-14977, CVE-2017-14976, CVE-2017-14975, CVE-2017-14974, CVE-2017-14952, CVE-2017-14940, CVE-2017-14939, CVE-2017-14938, CVE-2017-14934, CVE-2017-14933, CVE-2017-14932, CVE-2017-14930, CVE-2017-14929, CVE-2017-14928, CVE-2017-14927, CVE-2017-14926, CVE-2017-14867, CVE-2017-14745, CVE-2017-14729, CVE-2017-14617, CVE-2017-14529, CVE-2017-14520, CVE-2017-14519, CVE-2017-14518, CVE-2017-14517, CVE-2017-14164, CVE-2017-14152, CVE-2017-14151, CVE-2017-14130, CVE-2017-14129, CVE-2017-14128, CVE-2017-14062, CVE-2017-14041, CVE-2017-14040, CVE-2017-14039, CVE-2017-13757, CVE-2017-13734, CVE-2017-13733, CVE-2017-13732, CVE-2017-13731, CVE-2017-13730, CVE-2017-13729, CVE-2017-13728, CVE-2017-13727, CVE-2017-13726, CVE-2017-13716, CVE-2017-13710, CVE-2017-13685, CVE-2017-12982, CVE-2017-12967, CVE-2017-12944, CVE-2017-12799, CVE-2017-12618, CVE-2017-12595, CVE-2017-12458, CVE-2017-12457, CVE-2017-12456, CVE-2017-12455, CVE-2017-12454, CVE-2017-12453, CVE-2017-12452, CVE-2017-12451, CVE-2017-12449, CVE-2017-11714, CVE-2017-11627, CVE-2017-11626, CVE-2017-11625, CVE-2017-11624, CVE-2017-11462, CVE-2017-11335, CVE-2017-11164, CVE-2017-11113, CVE-2017-11112, CVE-2017-11109, CVE-2017-10989, CVE-2017-10790, CVE-2017-10688, CVE-2017-10685, CVE-2017-10684, CVE-2017-10140, CVE-2017-1000456, CVE-2017-1000383, CVE-2017-1000382, CVE-2017-1000254, CVE-2017-1000158, CVE-2017-1000100, CVE-2017-0663, CVE-2017-0553
CVE-2016-9844, CVE-2016-9601, CVE-2016-9586, CVE-2016-9574, CVE-2016-9539, CVE-2016-9538, CVE-2016-9532, CVE-2016-9453, CVE-2016-9318, CVE-2016-9297, CVE-2016-9273, CVE-2016-9112, CVE-2016-9082, CVE-2016-9074, CVE-2016-8625, CVE-2016-8624, CVE-2016-8623, CVE-2016-8622, CVE-2016-8621, CVE-2016-8619, CVE-2016-8618, CVE-2016-8617, CVE-2016-8616, CVE-2016-8615, CVE-2016-7952, CVE-2016-7951, CVE-2016-7950, CVE-2016-7949, CVE-2016-7948, CVE-2016-7947, CVE-2016-7946, CVE-2016-7945, CVE-2016-7944, CVE-2016-7943, CVE-2016-7942, CVE-2016-7415, CVE-2016-7091, CVE-2016-6349, CVE-2016-6321, CVE-2016-6318, CVE-2016-6293, CVE-2016-6263, CVE-2016-6262, CVE-2016-6261, CVE-2016-6223, CVE-2016-6185, CVE-2016-6153, CVE-2016-5323, CVE-2016-5321, CVE-2016-5319, CVE-2016-5318, CVE-2016-5300, CVE-2016-5131, CVE-2016-5102, CVE-2016-4984, CVE-2016-4738, CVE-2016-4610, CVE-2016-4609, CVE-2016-4608, CVE-2016-4607, CVE-2016-4493, CVE-2016-4492, CVE-2016-4491, CVE-2016-4490, CVE-2016-4489, CVE-2016-4488, CVE-2016-4487, CVE-2016-4484, CVE-2016-4483, CVE-2016-4472, CVE-2016-4429, CVE-2016-4074, CVE-2016-4008, CVE-2016-3631, CVE-2016-3624, CVE-2016-3622, CVE-2016-3191, CVE-2016-3189, CVE-2016-2781, CVE-2016-2779, CVE-2016-2381, CVE-2016-2226, CVE-2016-2183, CVE-2016-2052, CVE-2016-2037, CVE-2016-1951, CVE-2016-1938, CVE-2016-1841, CVE-2016-1684, CVE-2016-1683, CVE-2016-1238, CVE-2016-1234, CVE-2016-10507, CVE-2016-10506, CVE-2016-10505, CVE-2016-10504, CVE-2016-10371, CVE-2016-10317, CVE-2016-10272, CVE-2016-10271, CVE-2016-10270, CVE-2016-10269, CVE-2016-10268, CVE-2016-10267, CVE-2016-10266, CVE-2016-10255, CVE-2016-10254, CVE-2016-10244, CVE-2016-10243, CVE-2016-10220, CVE-2016-10219, CVE-2016-10218, CVE-2016-10217, CVE-2016-10165, CVE-2016-10109, CVE-2016-10094, CVE-2016-10093, CVE-2016-10092, CVE-2016-10087, CVE-2016-0755
CVE-2015-9252, CVE-2015-9019, CVE-2015-8948, CVE-2015-8947, CVE-2015-8865, CVE-2015-8853, CVE-2015-8540, CVE-2015-8538, CVE-2015-8391, CVE-2015-8388, CVE-2015-8386, CVE-2015-8385, CVE-2015-8382, CVE-2015-8035, CVE-2015-7995, CVE-2015-7697, CVE-2015-7696, CVE-2015-7036, CVE-2015-5701, CVE-2015-5700, CVE-2015-5276, CVE-2015-5218, CVE-2015-5186, CVE-2015-5073, CVE-2015-4844, CVE-2015-4840, CVE-2015-4760, CVE-2015-3228, CVE-2015-3217, CVE-2015-3153, CVE-2015-2697, CVE-2015-2696, CVE-2015-2695, CVE-2015-2632, CVE-2015-2613, CVE-2015-2328, CVE-2015-2327, CVE-2015-2059, CVE-2015-1607, CVE-2015-1606, CVE-2015-1572, CVE-2015-1270, CVE-2015-1197, CVE-2015-0837, CVE-2015-0247, CVE-2015-0245
Refresh 15 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in July 2022.
Assembly version: 3.5.10
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2017-9226, CVE-2017-9227, CVE-2017-9228, CVE-2017-9229, CVE-2017-9230, CVE-2017-9231, CVE-2017-9232, CVE-2017-9233, CVE-2017-9234, CVE-2017-9235, CVE-2017-9236, CVE-2017-9237, CVE-2017-9238, CVE-2017-9239, CVE-2017-9240, CVE-2017-9241, CVE-2017-9242, CVE-2017-9243, CVE-2017-9244, CVE-2017-9245, CVE-2017-9246, CVE-2017-9247, CVE-2017-9248, CVE-2017-9249, CVE-2017-9250, CVE-2017-9251, CVE-2017-9252, CVE-2017-9253, CVE-2017-9254
Refresh 14 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in May 2022.
Assembly version: 3.5.9
- New features
-
The 3.5.9 release of Data Refinery includes the following features and updates:
- Deprecation notice for the Spark 2.4 & R 3.6 environment
- The Spark 2.4 & R 3.6 environment is deprecated and will be removed in an upcoming release. Use the Default Data Refinery XS environment in your Data Refinery flow jobs.
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2017-9735, CVE-2020-25709, CVE-2020-25710
Refresh 12 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in March 2022.
Assembly version: 3.5.8
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2016-2149, CVE-2016-2160, CVE-2016-3711, CVE-2017-11164, CVE-2017-12618, CVE-2017-15137, CVE-2017-15138, CVE-2017-3167, CVE-2017-3169, CVE-2017-6004, CVE-2017-7186, CVE-2017-7244, CVE-2017-7245, CVE-2017-7246, CVE-2017-7679, CVE-2017-9788, CVE-2018-14632, CVE-2018-14645, CVE-2019-20916, CVE-2019-9511, CVE-2019-9516, CVE-2019-9517, CVE-2020-9488, CVE-2021-26691, CVE-2021-33909, CVE-2021-34798, CVE-2021-35556, CVE-2021-35559, CVE-2021-35560, CVE-2021-35564, CVE-2021-35565, CVE-2021-35578, CVE-2021-35586, CVE-2021-39275, CVE-2021-41035, CVE-2021-44790
Refresh 11 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in February 2022.
Assembly version: 3.5.7
This release includes the following changes:
- Bug fixes
-
Version 3.5.7 of the Data Refinery service includes various fixes.
Refresh 10 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in January 2022.
Assembly version: 3.5.6
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2021-35588, CVE-2021-3572, CVE-2021-31535, CVE-2019-9924, CVE-2021-20271, CVE-2021-2388, CVE-2021-23840, CVE-2018-16429, CVE-2021-20305, CVE-2021-35561, CVE-2021-2341, CVE-2020-13956, CVE-2021-35567, CVE-2021-23440, CVE-2021-41617, CVE-2021-37750, CVE-2017-18018, CVE-2018-7485, CVE-2021-35603, CVE-2021-23841, CVE-2019-9633, CVE-2021-3114, CVE-2018-7409, CVE-2017-15713, CVE-2020-9492, CVE-2019-20445, CVE-2018-12700, CVE-2021-35550, CVE-2021-29425, CVE-2021-2369, CVE-2018-8029, CVE-2021-22923, CVE-2021-22922, CVE 2021-45105, CVE 2021-45046
Refresh 7 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in July 2021.
Assembly version: 3.5.5
- New features
-
The 3.5.5 release of Data Refinery includes the following features and updates:
- Short videos showcase the Data Refinery GUI operations
-
The Data Refinery GUI operations topic now includes a short video for each operation to help you learn by example.
If you have feedback on the videos, you can submit it through the Watson Studio and Machine Learning community (You must sign in to leave comments.)
- Bug fixes
-
This release includes the following fix:
- Issue: Unable to add an asset to Data Refinery when the data set contains a
large number of columns and includes special characters or characters from the Chinese, Japanese, or
Korean languages. You receive a
504 Gateway Time-outmessage.Resolution: This problem is fixed.
- Issue: Unable to add an asset to Data Refinery when the data set contains a
large number of columns and includes special characters or characters from the Chinese, Japanese, or
Korean languages. You receive a
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2015-2059, CVE-2020-12399, CVE-2020-25648, CVE-2020-25692, CVE-2019-20372, CVE-2020-12762, CVE-2021-20271
Refresh 5 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in April 2021.
Assembly version: 3.5.4
- Security fixes
-
This release includes fixes for the following security issues:
CVE-2016-6811, CVE-2017-15713, CVE-2017-15718, CVE-2017-3166, CVE-2018-1296, CVE-2018-14718, CVE-2018-7489, CVE-2018-8029, CVE-2019-16869, CVE-2019-20444, CVE-2019-20445, CVE-2020-10673, CVE-2020-25649, CVE-2020-35490, CVE-2020-35491, CVE-2020-9492, CVE-2021-21290, CVE-2021-21295, CVE-2021-21409, CVE-2021-2163, CVE-2021-23368
Refresh 2 of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released in January 2021.
Assembly version: 3.5.2
This release includes the following changes:
- Bug fixes
-
This release includes the following fix:
- Issue: Cannot specify format options after
you change the Data Refinery flow source. When data is read into Data Refinery, you can scroll down
to the SOURCE FILE information at the bottom of the page and click the “Specify data format” icon to
specify format options for CSV or delimited files. However, if you changed the source of a Data
Refinery flow, this feature is not available.
Resolution: This problem is fixed.
- Issue: Cannot specify format options after
you change the Data Refinery flow source. When data is read into Data Refinery, you can scroll down
to the SOURCE FILE information at the bottom of the page and click the “Specify data format” icon to
specify format options for CSV or delimited files. However, if you changed the source of a Data
Refinery flow, this feature is not available.
Initial release of Cloud Pak for Data Version 3.5
A new version of Data Refinery was released as part of Cloud Pak for Data Version 3.5.
Assembly version: 3.5.0
This release includes the following changes:
- New features
-
- Use personal credentials for connections
- If you create a connection and select the Personal credentials option,
other users can use that connection only if they supply their own credentials for the data source.
Users who have credentials for the underlying data source can:
- Select the connection to create a Data Refinery flow
- Edit or change a location when modifying a Data Refinery flow
- Select a data source for the Join operation
For information about creating a project-level connection with personal credentials, see Adding connections to analytics projects.
- Use the Union operation to combine rows from two data sets that share the same schema
-
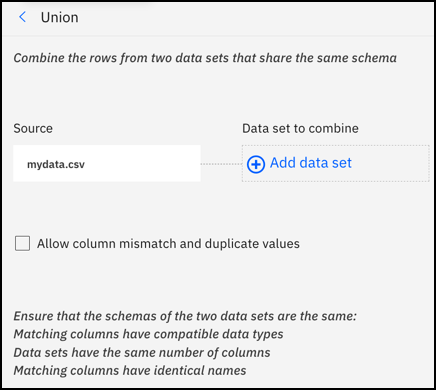
The Union operation is in the ORGANIZE category. For more information, see GUI operations in Data Refinery.
- Perform aggregate calculations on multiple columns in Data Refinery
- You can now select multiple columns in the Aggregate operation. Previously all aggregate
calculations applied to one column.
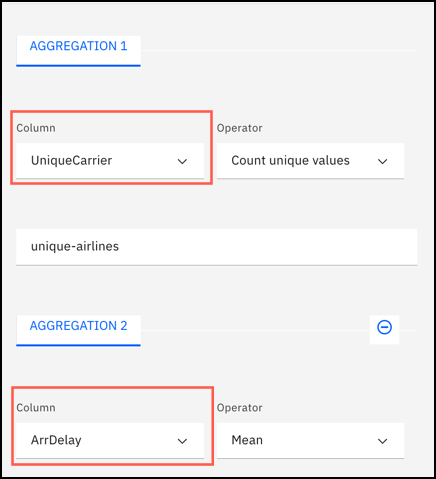
The Aggregate operation is in the ORGANIZE category. For more information, see Aggregate in GUI operations in Data Refinery.
- Automatically detect and convert date and timestamp data types
- When you open a file in Data Refinery, the Convert column type GUI operation is automatically applied as the first step if it detects any non-string data types in the data. In this release, date and timestamp data are detected and are automatically converted to inferred data types. You can change the automatic conversion for selected columns or undo the step. For information about the supported inferred date and timestamp formats, see the FREQUENTLY USED category in Convert column type in GUI operations in Data Refinery.
- Change the decimal and thousands grouping symbols in all applicable columns
- When you use the Convert column type GUI operation to detect and convert
the data types for all the columns in a data asset, you can now also choose the decimal symbol and
the thousands grouping symbol if the data is converted to an Integer data
type or to a Decimal data type. Previously you had to select individual
columns to specify the symbols.
For more information, see the FREQUENTLY USED category in Convert column type in GUI operations in Data Refinery.
- Filter values in a Boolean column
- You can now use the following operators in the Filter GUI operation to
filter Boolean (logical) data:
- Is false
- Is true
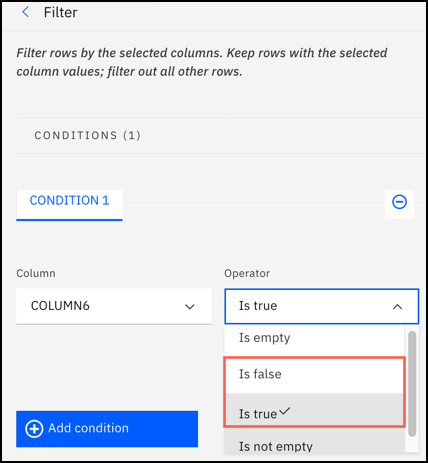
For more information, see the FREQUENTLY USED category in Filter in GUI operations in Data Refinery.
In addition, Data Refinery includes a new template for filtering by Boolean values in thefiltercoding operation:filter(`<column>`== <logical>)For more information about the filter templates, see Interactive code templates in Data Refinery.
- Data Refinery flows are supported in deployment spaces
- You can now promote a Data Refinery
flow from a project to a deployment space. Deployment spaces are used to manage a set of related
assets in a separate environment from your projects. You can promote Data Refinery flows from multiple projects to a
space. You run a job for the Data Refinery
flow in the space and then use the shaped output as input for deployment jobs in Watson Machine Learning.
For instructions, see Promote a Data Refinery flow to a space in Managing Data Refinery flows.
- Support for TSV files
- You can now refine data in files that use the tab-separated-value (TSV) format. TSV files are read-only.
- SJIS encoding available for input and output
- SJIS (short for Shift JIS or Shift Japanese Industrial Standards)
encoding is an encoding for the Japanese language. SJIS encoding is supported only for CSV and
delimited files.
You can change the encoding of input files and output files.
To change the encoding of the input file, click the "Specify data format" icon when you open the file in Data Refinery. See Specifying the format of your data in Data Refinery.
To change the encoding of the output (target) file in Data Refinery, open the Information pane and click the Details tab. Click the Edit button. In the DATA REFINERY FLOW OUTPUT pane, click the Edit icon.
- New jobs user interface for running and scheduling flows
- For more information, see the What's new entry for Watson Studio.
- New visualization charts
- For more information, see the What's new entry for Watson Studio.