Question & Answer
Question
Where is the behavioral tree referenced on the dashboard? Also, what are the details of the behavioral tree?
Answer
This document discusses regarding details of behavioral tree on the dashboard.
What is the behavioral tree?
The behavioral tree widget displays a graphical visualization of the malicious behavior with the participating process and suspicious actions performed by the processes.
How to view the behavioral tree
- This can view from the User Interface (UI): Alerts > Select the alert > Analyze alert > Behavioral tree
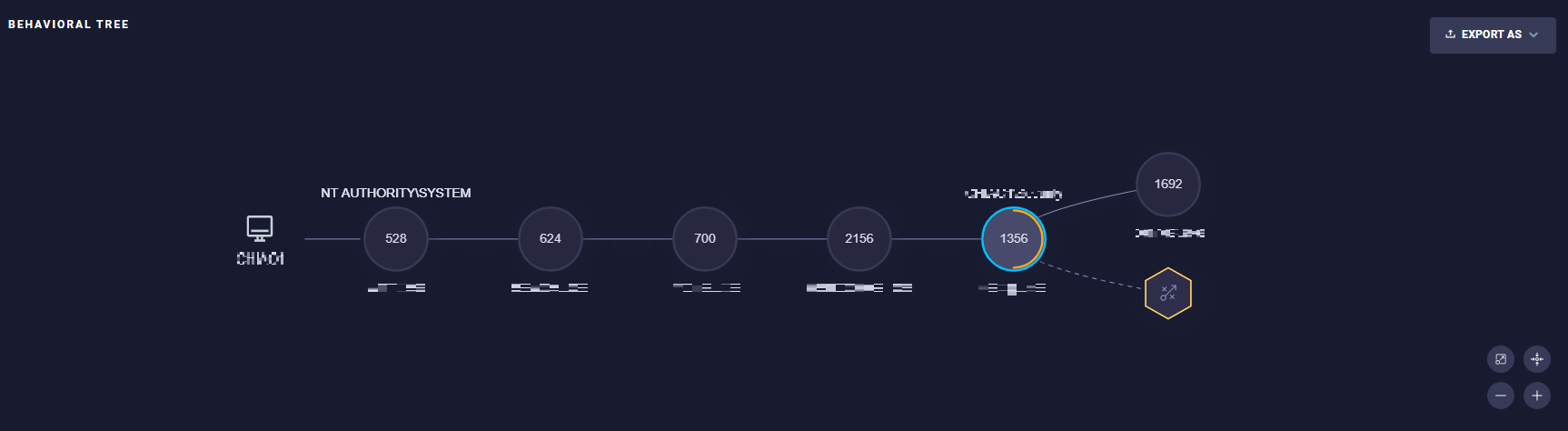
Components of behavioral tree
The Behavioral Tree consists of the following components:
<Shapes>
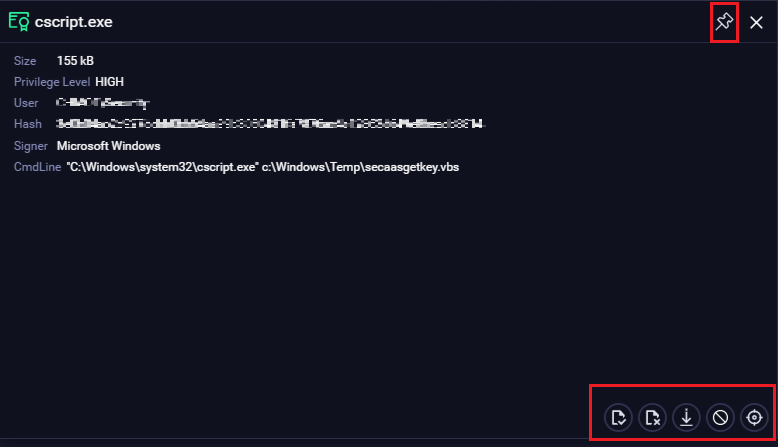
Circle:
Represents a process with the name of the user account running the process on the top, process ID in the center, and name of the process on the bottom.
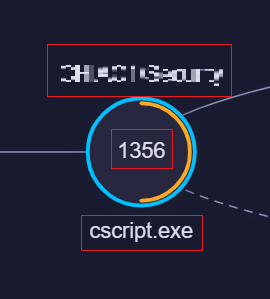
Click a process, and following details about the process can be confirmed:
Circle:
Represents a process with the name of the user account running the process on the top, process ID in the center, and name of the process on the bottom.

Click a process, and following details about the process can be confirmed:
- Digital Signature validity - green(valid), amber(expired), grey(not present).
- Size - the size of the executable.
- Privilege Level - privilege level used by the process.
- User - the user who ran the process.
- Hash - the SHA256 value of the executable.
- Signer - signer of the certificate, if any available.
- Cmd Line - the exact command line executed by the process.
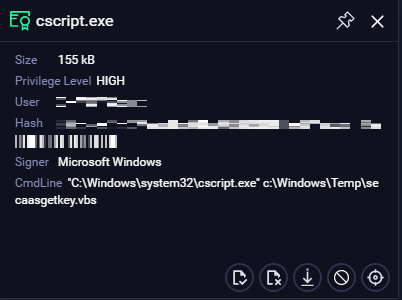
An open circle inside a process circle is only present if the process performed malicious activities. The color indicates the severity level of the detected behavior.
- Filled line - connects the parent process to the child process.
- Dotted line - connects the process to the key events.
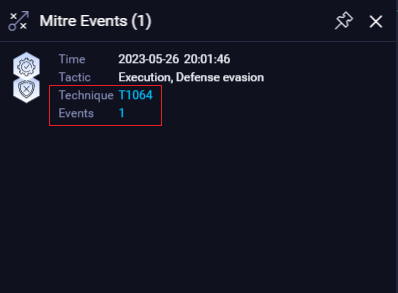
- Hexagon - represents the key events performed by the process grouped by type. Grouping is done by:
・General Event type.
・MITRE Event type.
・ReaQta-Hive NanoOS proprietary detections.
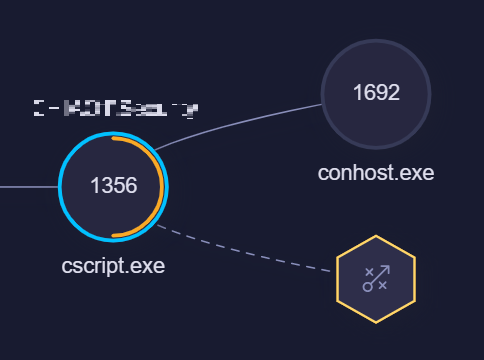
TIP: If the hexagon contains a Red circle overlay with a number, the number lists the amount of events of the same type. Click on the hexagon and use the right/left arrow at the bottom left to browse between the events.
Shape action buttons:
The view of the details of a process or of an event also allows several actions. The actions depend on the type of element and the origin.
The following default actions are available:
・MITRE Event type.
・ReaQta-Hive NanoOS proprietary detections.

TIP: If the hexagon contains a Red circle overlay with a number, the number lists the amount of events of the same type. Click on the hexagon and use the right/left arrow at the bottom left to browse between the events.
Shape action buttons:
The view of the details of a process or of an event also allows several actions. The actions depend on the type of element and the origin.
The following default actions are available:
- Pin to the storyboard creating a sequential line of events.
- Create a allowlist policy.
- Create a blocklist policy.
- Download the executable.
- Perform threat hunt on the specific action.
- Browse between multiple items within the same hexagon.
- Only for the MITRE Events hexagon, view the techniques definitions and mapped events and its details.
IMPORTANT: Policy creation is only available on processes that were the trigger of the malicious process detected by the agent during real time behavior analysis.
<Colors>
- Grey - not actively participating in the triggering of the alert.
- Blue - a blue circle indicates that the process is performing malicious activities and therefore directly participating in the triggering of the alert.
- Red - indicates a High Severity behavior.
- Amber - indicates a Medium Severity behavior.
- Yellow - indicates a Low Severity behavior.
- Green - indicates a Safe Severity behavior.
Ex. In the case of malicious activities and low severity.
TIP: If a circle contains a yellow semicircle, it indicates that the process is a duplicated node of the process and you should look for the badge number of this process in the process tree to find the matching ones.
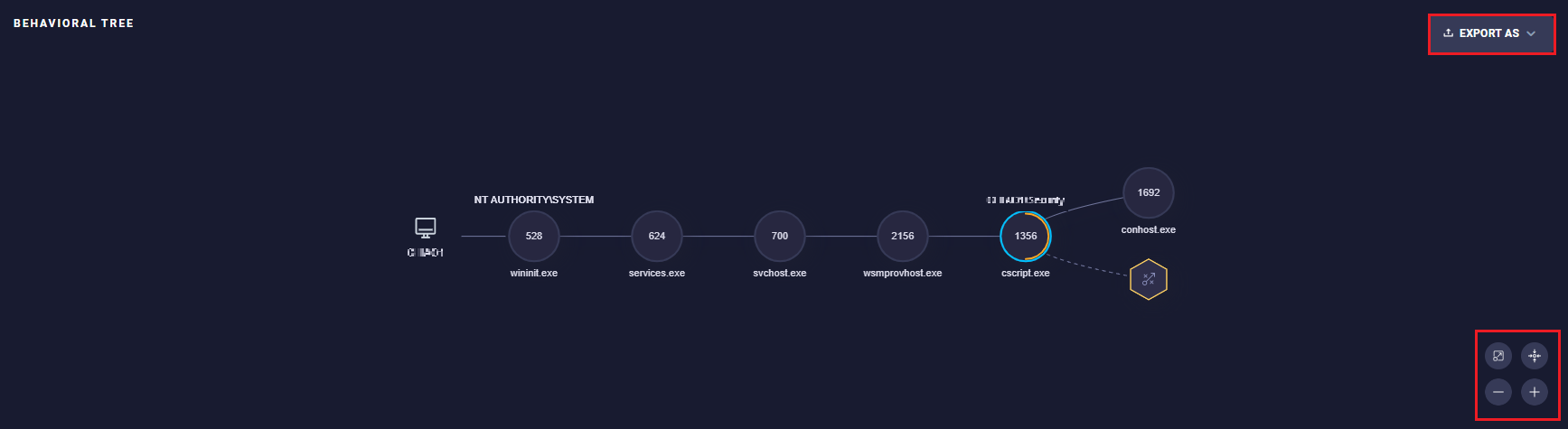
<Export As>
Allows you to export the contents of the screen to file in PNG format.
Allows you to export the contents of the screen to file in PNG format.
<Actionable icons>
- Open the Behavioral Tree in a dedicated widget. This action will close all open widgets.
- Fit the Screen - automatically zooms in to fit the full Behavioral Tree in the current screen.
- Option to Zoom Out.
- Option to Zoom In.
[{"Type":"MASTER","Line of Business":{"code":"LOB24","label":"Security Software"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSVOEH","label":"IBM Security ReaQta"},"ARM Category":[{"code":"a8m3p000000hBSAAA2","label":"Administrative Tasks"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions"}]
Product Synonym
ReaQta
Was this topic helpful?
Document Information
Modified date:
01 June 2023
UID
ibm16999221