Troubleshooting
Problem
When an event for the Microsoft Windows Security DSM has a user ending with dollar sign "$", this user is not extracted.
Symptom
For example, in this Windows Security event:
<13>Jun 23 12:03:29 MyServerName AgentDevice=WindowsLog AgentLogFile=Security
PluginVersion=7.3.0.41 Source=Security Computer=Server OriginatingComputer=x.x.x.1
User=SYSTEM Domain=NT AUTHORITY EventID=540 EventIDCode=540 EventType=8
EventCategory=2 RecordNumber=27741234 TimeGenerated=1656000205
TimeWritten=1656000205 Level=0 Keywords=0 Task=0 Opcode=0
Message=Successful Network Logon: User Name: SERVERFLOW2$ Domain:…
The username SERVERFLOW$ is not extracted, even if the event is open with the DSM Editor:
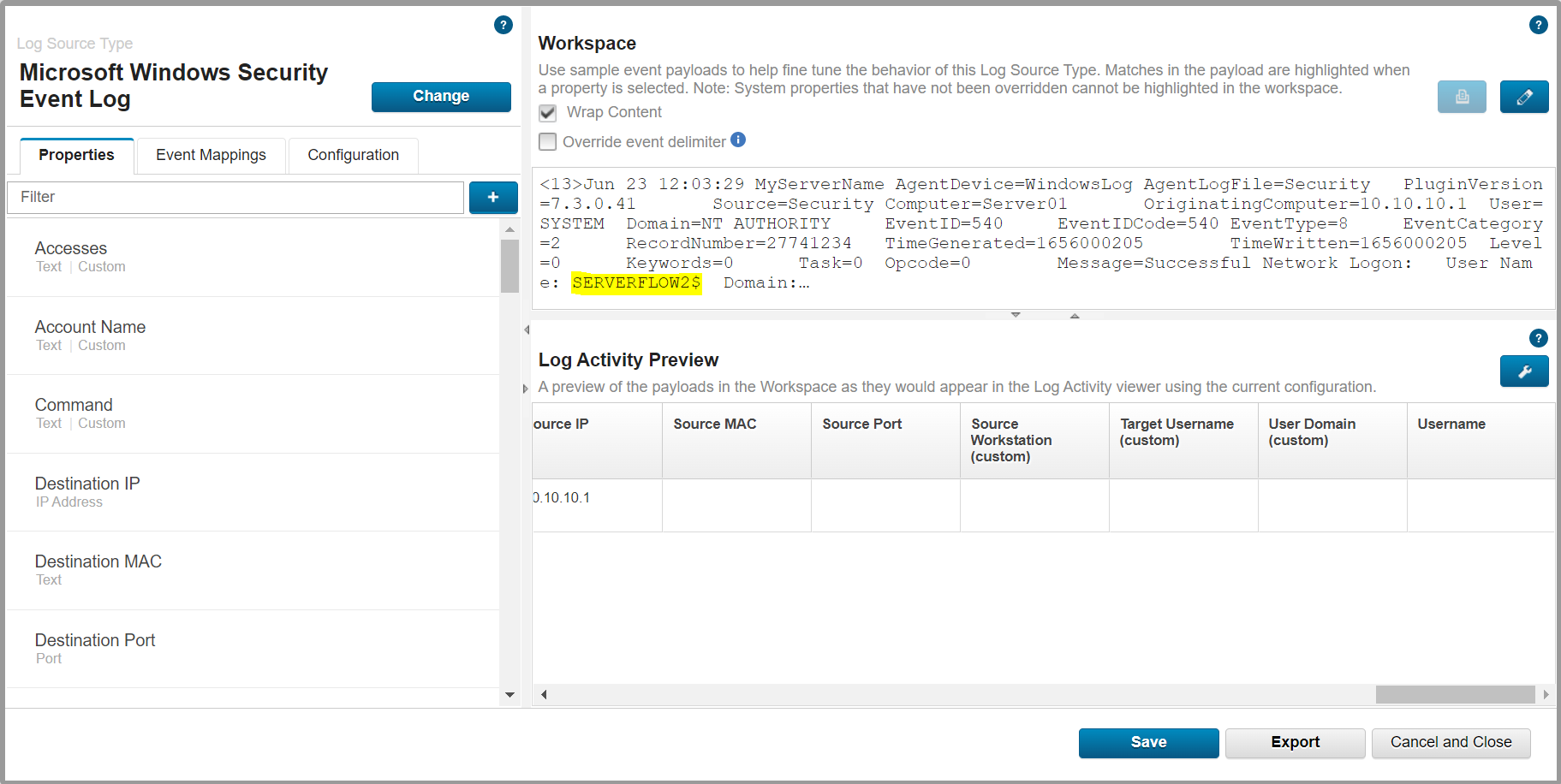
Note: By default the Microsoft Windows Security DSM extracts the username information from the "Message" field and not from the "User" metadate field, which usually says SYSTEM when the user is a system account.
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB77","label":"Automation Platform"},"Business Unit":{"code":"BU048","label":"IBM Software"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000cwtSAAQ","label":"DSM Editor"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions"}]
Log InLog in to view more of this document
This document has the abstract of a technical article that is available to authorized users once you have logged on. Please use Log in button above to access the full document. After log in, if you do not have the right authorization for this document, there will be instructions on what to do next.
Was this topic helpful?
Document Information
Modified date:
20 February 2024
UID
ibm16602735