Question & Answer
Question
Why is the DSM Editor not highlighting a correct Regex match? Furthermore, my Custom Event Property populates the value correctly when I examine the event in Log Activity.
Example payload, the objective is to capture "SourceUser":
<13>Jun 02 13:23:53 10.10.10.10 EventFormatter=WindowsSplunkEventFormatter AgentDevice=WindowsLog AgentLogFile=Security Source=Microsoft Windows security auditing. Computer=HOSTNAME.ABC.LOCAL User= Domain= EventID=4738 EventIDCode=4738 EventType=8 EventCategory= RecordNumber=1355409588 TimeGenerated=1622633033 TimeWritten=1622633033 Message=A user account was changed. Subject: Security ID: S-1-5-21-752214896-4175829826-419224292-1112 Account Name: SourceUser Account Domain: ABC Logon ID: 0x6C236BB9 Target Account: Security ID: S-1-5-21-752214896-4175829826-419224292-181733 Account Name: DestinationUser Account Domain: ABC Changed Attributes: SAM Account Name: - Display Name: - User Principal Name: - Home Directory: - Home Drive: - Script Path: - Profile Path: - User Workstations: - Password Last Set: 02.06.2021 13:23:53 Account Expires: - Primary Group ID: - AllowedToDelegateTo: - Old UAC Value: - New UAC Value: - User Account Control: - User Parameters: - SID History: - Logon Hours: - Additional Information: Privileges: -
Regex 1, which highlights a match (note, the Override is selected and marked with a thin blue frame):
Message=.*?Account Name:\s+(.*?)\s+
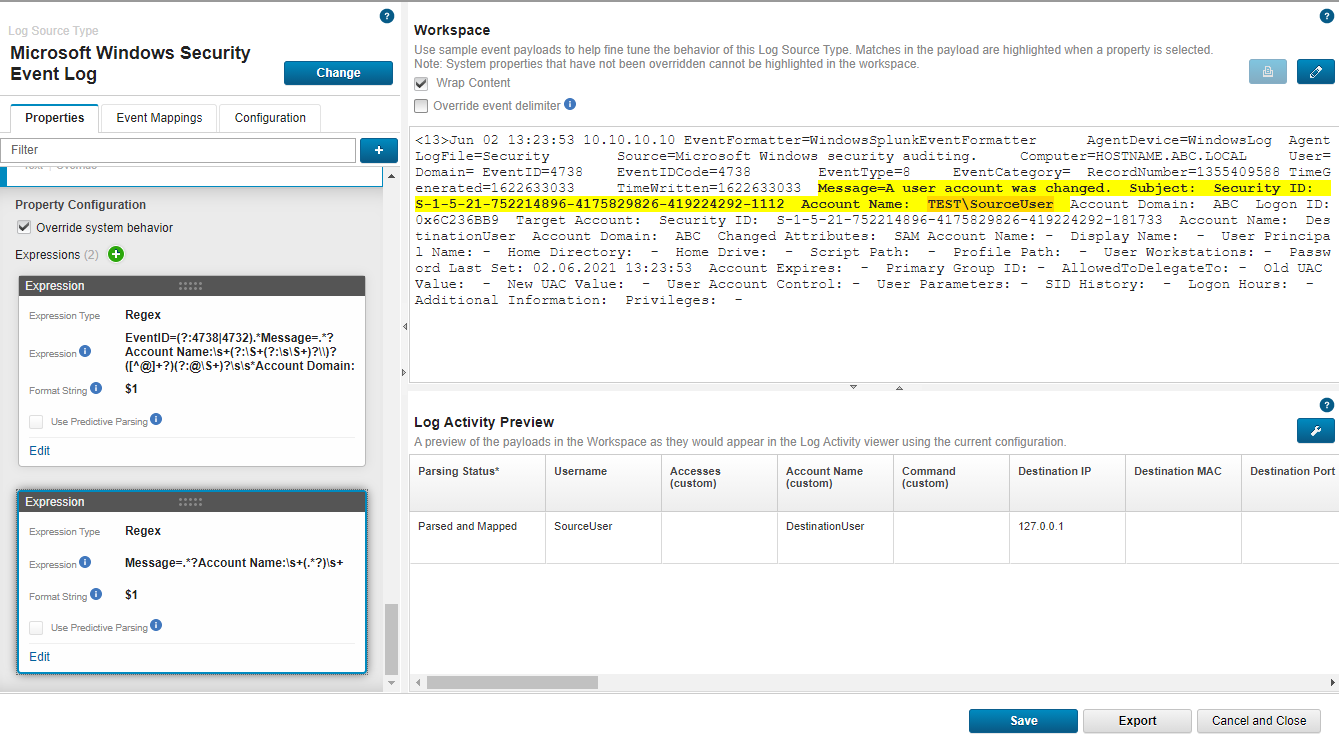
Regex 2, which does not highlight a match (note, the Override is selected and marked with a thin blue frame):
EventID=(?:4738|4732).*Message=.*?Account Name:\s+(?:\S+(?:\s\S+)?\\)?([^@]+?)(?:@\S+)?\s\s*Account Domain:

[{"Type":"MASTER","Line of Business":{"code":"LOB77","label":"Automation Platform"},"Business Unit":{"code":"BU048","label":"IBM Software"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000cwtSAAQ","label":"DSM Editor"}],"ARM Case Number":"TS005327651","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions"}]
Log InLog in to view more of this document
This document has the abstract of a technical article that is available to authorized users once you have logged on. Please use Log in button above to access the full document. After log in, if you do not have the right authorization for this document, there will be instructions on what to do next.
Was this topic helpful?
Document Information
Modified date:
19 July 2021
UID
ibm16473087