How To
Summary
In this document, we discuss how to configure Object Structure Security depending on how you want to use it.
Objective
Environment
Maximo 7.6.x
Steps
There are two ways to implement Object Structure Security.
The first is to use Application Authorization.
The second is to configure security directly on the object structure.
You can also configure object structure access based on the logged in user's application authorization.
The steps to configure application authorization are:
1. Navigate to an object structure you want to secure. For example, MXASSET
2. In the menu pane, select Configure Object Structure Security
3. Ensure "Use Object Structure for Authorization Name?" is not checked
4. In the Authorization Name field, enter the name of the application that provides the privileges. For example, Asset
The screen capture shows this example:
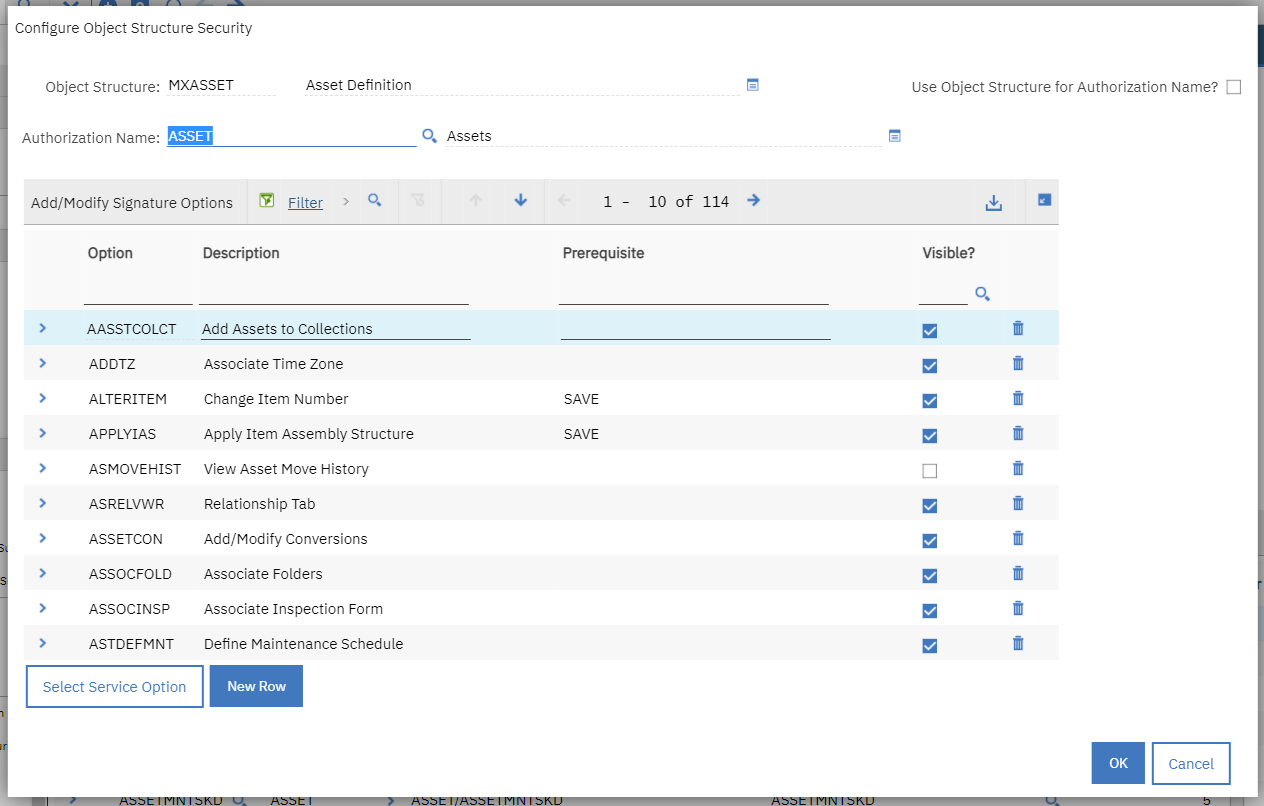
5. Click OK to save the changes
6. In the Security Groups application, navigate to your security group and grant access to the Asset application. Any user belonging to a group that has privileges to perform actions in the Asset application can perform actions on the object structure.
Now any user who belongs to a group that has access to the Asset application can access the MXASSET object structure.
The second is to configure security directly on the object structure.
1. Navigate to an object structure you want to secure. For example, MXASSET
2. In the menu pane, select Configure Object Structure Security
3. Check the "Use Object Structure for Authorization Name?" check box
4. The Authorization Name field is automatically populated with the name of the associated object structure
The screen capture shows this example:
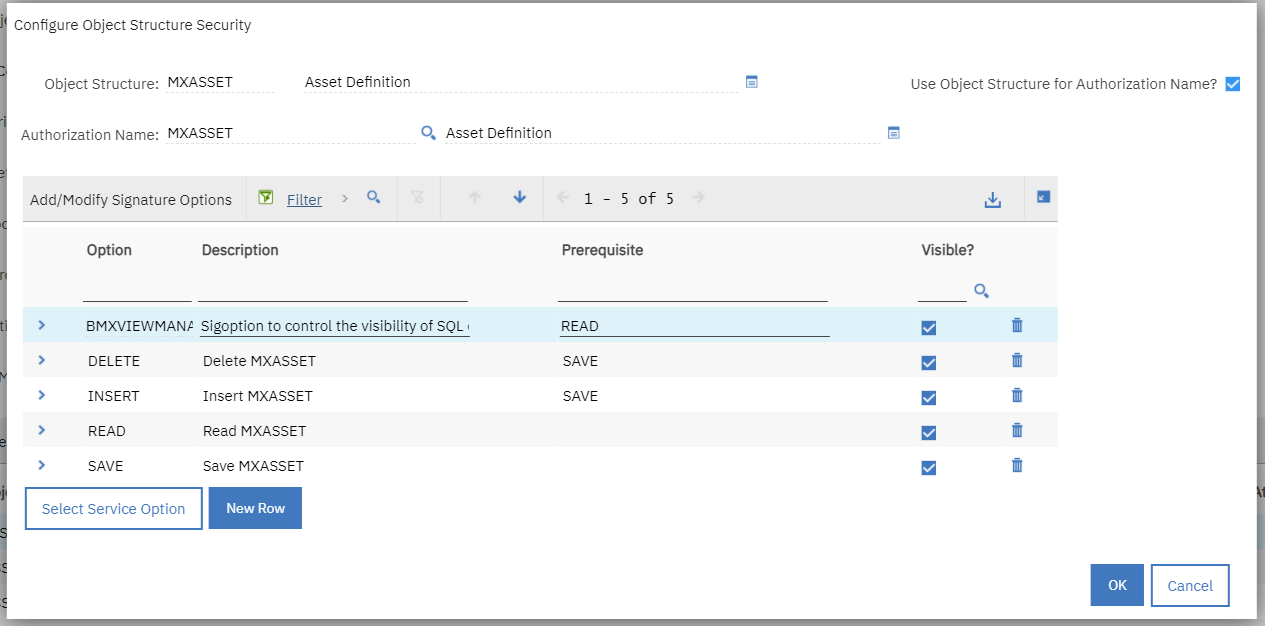
Notice that signature options Delete, Insert, Read, Save, and some others are provided for the object structure itself.
5. Click the Select Service Option button to include any service signature options.
6. Click OK to save the changes.
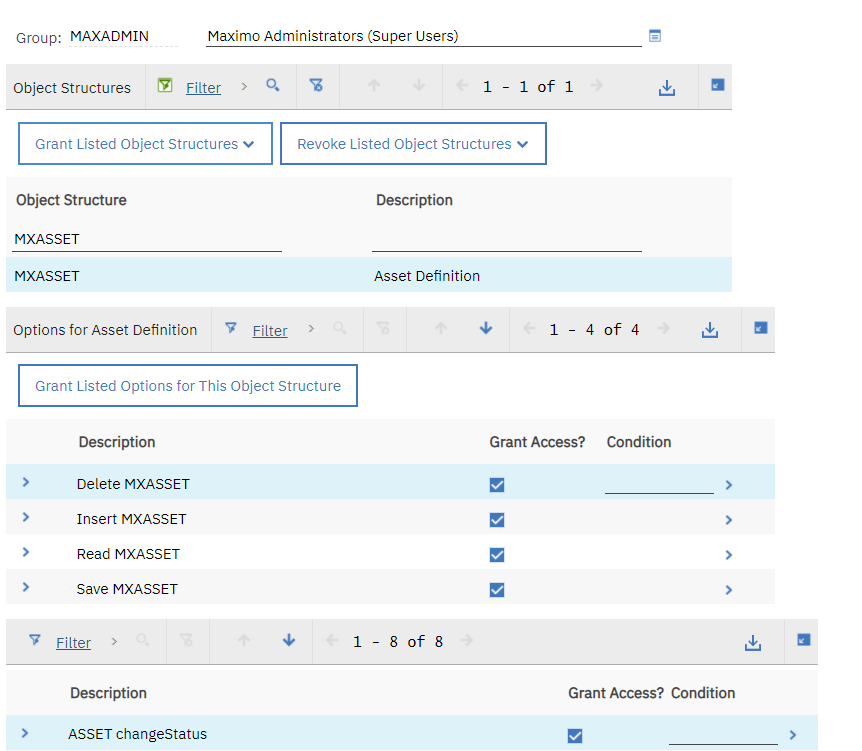
7. In the Security Groups application, navigate to your security group and click the Object Structures tab. Filter for the MXASSET object structure name and grant access to the options listed. Any user belonging to a group that is granted access to the object structure itself is able to access it.
Contact IBM Support for any questions or assistance with this topic.
Document Location
Worldwide
[{"Line of Business":{"code":"LOB59","label":"Sustainability Software"},"Business Unit":{"code":"BU048","label":"IBM Software"},"Product":{"code":"SSLKT6","label":"IBM Maximo Asset Management"},"ARM Category":[{"code":"a8m50000000CbFGAA0","label":"Integration"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"7.6.0;7.6.1"}]
Was this topic helpful?
Document Information
Modified date:
11 April 2024
UID
ibm16417041