Troubleshooting
Problem
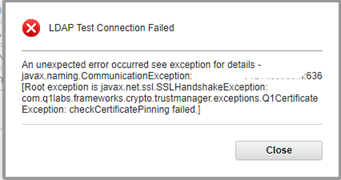
When setting up LDAP authentication using Active Directory, using the Test Connection option causes an SSL handshake exception for connections done via LDAPS.
Symptom
On the LDAP Authentication page, when using the Test Connection option for Active Directory, for connections done via LDAPS, an error message is observed regarding the SSL handshake:
Document Location
Worldwide
[{"Type":"MASTER","Line of Business":{"code":"LOB77","label":"Automation Platform"},"Business Unit":{"code":"BU048","label":"IBM Software"},"Product":{"code":"SSBQAC","label":"IBM Security QRadar SIEM"},"ARM Category":[{"code":"a8m0z000000cwsyAAA","label":"Admin Tasks"}],"ARM Case Number":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"7.3.3;7.4.0;7.4.1;7.4.2;7.4.3;7.5.0"}]
Log InLog in to view more of this document
This document has the abstract of a technical article that is available to authorized users once you have logged on. Please use Log in button above to access the full document. After log in, if you do not have the right authorization for this document, there will be instructions on what to do next.
Was this topic helpful?
Document Information
Modified date:
15 March 2024
UID
ibm16413273