Notification
Risk classification
Informational
Risk categories
Function Loss
Subcategories for Informational notifications
Product Information & Documentation
Affected Domain
All IBM b-type (Brocade) SAN switches that utilize Web Tools running on any Brocade FOS version prior to v8.2.1.
Abstract
Brocade Web Tools JAR files are signed by a code signing certificate to protect against illegal tampering. This certificate is
validated by Java before launching the Java Client.
validated by Java before launching the Java Client.
When the Java code signing certificate expires, any attempts to connect to a Brocade SAN switch via Web Tools will be
blocked by the Java security code.
blocked by the Java security code.
Description
All Brocade SAN switches with FOS versions released before this fix contain a Java code signing certificate that will
expire on November 13, 2020. Once this certificate expires, Web Tools launches will be blocked by Java security.
expire on November 13, 2020. Once this certificate expires, Web Tools launches will be blocked by Java security.
Switches will continue to operate without failure. There is no interruption to traffic or any other operation of the switch.
Only Web Tools access will be blocked.
Only Web Tools access will be blocked.
Switches running FOS v8.2.1 and higher versions (including 8.2.2x and 9.x) are not at risk of having their Web
Tools launch blocked by Java code signing certification expiry due to an enhanced code signing algorithm present in all
versions of FOS starting with v8.2.1.
Tools launch blocked by Java code signing certification expiry due to an enhanced code signing algorithm present in all
versions of FOS starting with v8.2.1.
Switches can continue to be managed via the CLI, SSH, and other means. Only Web Tools access will be blocked.
Switches can also be managed by Network Advisor, provided that the selected operations do not require the
launching of a Web Tools interface.
launching of a Web Tools interface.
Recommended Action
Upgrade to FOS v8.2.1 or higher versions of firmware to obtain the enhanced code signing algorithm that will not
block the launch of Web Tools.
block the launch of Web Tools.
For customers running on versions of FOS prior to v8.2.1, a new Java code signing certificate must be installed. You must upgrade to one of the following versions. After upgrading, a new valid certificate will be in use and the launching of Web Tools will not be blocked by Java security:
- FOS v8.1.2k and higher
- FOS v7.4.2g and higher for devices that cannot run FOS v8
After upgrading to FOS v8.1.2k, v7.4.2g or higher patch levels on the 8.1.2x and 7.4.2x code streams, Web Tools
launch will not be blocked by Java code signing certificate expiry due to an enhanced code signing algorithm. This
new algorithm, originally introduced with FOS v8.2.1, has been added to these patch versions.
launch will not be blocked by Java code signing certificate expiry due to an enhanced code signing algorithm. This
new algorithm, originally introduced with FOS v8.2.1, has been added to these patch versions.
Users who wish to continue using Web Tools on a switch with an expired certificate can perform the following
workaround for Java 8:
workaround for Java 8:
- Add the Web Tools URLs of all the managed switches to the Exception Site List under the Security tab of the Java Control Panel.
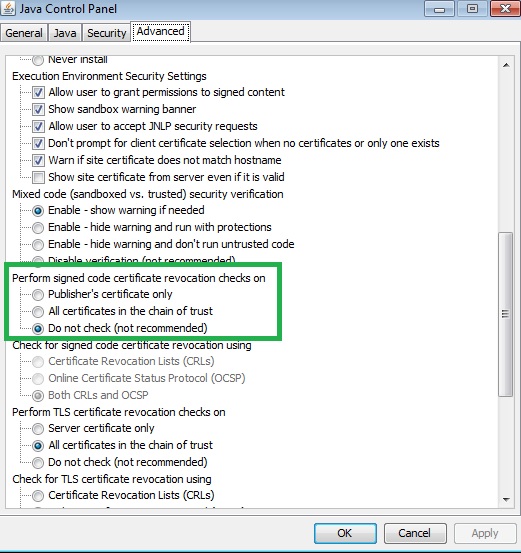
- Disable signed code certificate revocation checks.
This will allow Web Tools to run after presenting some security warnings.
Both of these workaround steps must be performed to prevent the Java client launch from being blocked by the Java
security code:
security code:
- How to manage and configure the Exception Site List: https://www.java.com/en/download/faq/exception_sitelist.xml
- Disable signed code certificate revocation checks under the Advanced tab on the Java Control Panel, as follows:
Date first published
01 October 2020
[{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STQPPK","label":"IBM Storage Networking SAN512B-6"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STQPPB","label":"IBM Storage Networking SAN18B-6"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STNNL8","label":"IBM Storage Networking SAN24B-5"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STNNL8","label":"IBM Storage Networking SAN24B"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STQPLH","label":"IBM Storage Networking SAN256B-6 (8961-F04)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"","label":""},"Business Unit":{"code":"BU054","label":"Systems w\/TPS"},"Product":{"code":"STMSBR","label":"Storage area network (SAN)->SAN384B-2 Fabric Backbone (2499-416)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"","label":""},"Business Unit":{"code":"BU054","label":"Systems w\/TPS"},"Product":{"code":"STMN38","label":"Storage area network (SAN)->SAN42B-R (2498-R42)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"","label":""},"Business Unit":{"code":"BU054","label":"Systems w\/TPS"},"Product":{"code":"STMSCJ","label":"Storage area network (SAN)->SAN48B-5 Switch (2498-F48)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"LOB26","label":"Storage"},"Business Unit":{"code":"BU058","label":"IBM Infrastructure w\/TPS"},"Product":{"code":"STQPJB","label":"SAN64B-6 Switch (8960-F64-N64)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"","label":""},"Business Unit":{"code":"BU054","label":"Systems w\/TPS"},"Product":{"code":"STMSAD","label":"Storage area network (SAN)->SAN768B-2 Fabric Backbone (2499-816)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"},{"Risk Classification":"Informational","Line of Business":{"code":"","label":""},"Business Unit":{"code":"BU054","label":"Systems w\/TPS"},"Product":{"code":"STNNAB","label":"Storage area network (SAN)->SAN96B-5 Switch (2498-F96, N96)"},"ARM Category":[],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Version(s)"}]
Was this topic helpful?
Document Information
Modified date:
27 February 2023
UID
ibm16340047