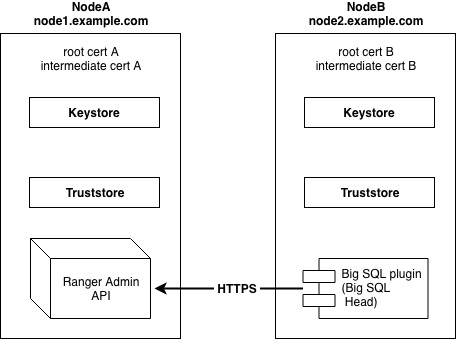
Overview
Ranger plugins interact with Ranger Admin via HTTP calls to its REST API.
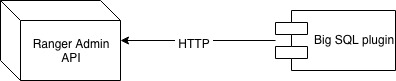
For security reasons, you may want to set up SSL to encrypt that communication. This article will discuss how to set up the Ranger Admin and Big SQL Ranger plugin for SSL using public CA certificates using an example scenario.
Scenario
For the purpose of this demonstration, we will assume Ranger Admin runs on NodeA and Big SQL Head on NodeB.
Step 1: Obtain CA-signed SSL certificates for each FQDN
An SSL Certificate is issued to a Fully Qualified Domain Name. Thus, if NodeA, for example, has FQDN node1.example.com and NodeB has node2.example.com, you will need to issue two CA-signed SSL certificates, one per FQDN. If Ranger Admin and Big SQL Head are collocated under the same FQDN, you will need only one certificate. For the purpose of the example below, we will demonstrate a two-node setup, where Big SQL Head and Ranger Admin are hosted on separate nodes.
Step 2: Install root and intermediate certificate on your hosts
Make sure root and intermediate certificates (usually issued with your SSL certificate) are installed on your hosts or you have added root and intermediate certificates to the default java keystore “cacerts” on the hosts for Ranger Admin and Big SQL Head.
Example:
keytool -import -file carootcert.der -alias carootcert -keystore /usr/jdk64/jdk1.8.0_112/jre/lib/security/cacerts -storepass changeit
keytool -import -file caintermediatecert.der -alias caintermediatecert -keystore /usr/jdk64/jdk1.8.0_112/jre/lib/security/cacerts -storepass changeit
Step 3: Generate keystores
For SSL traffic exchange between Ranger Admin and Big SQL we will need to set up keystores and truststores for each. The keystores are used to store your own certificates and keys. The certificate from the keystore will be presented to the client on connection.
The truststores are used to store the certificates of the other parties that the application shall trust and to verify the presented certificate in an SSL Connection.
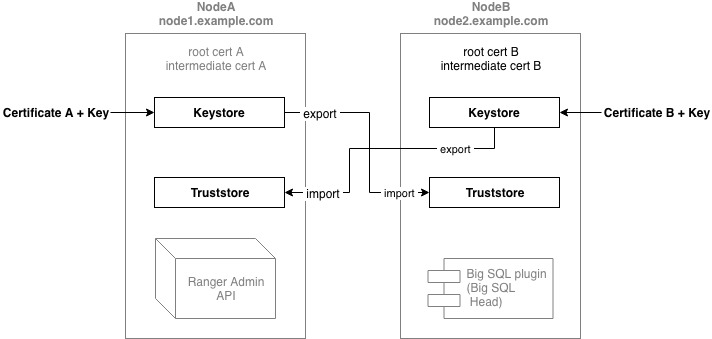
Example: Set up Ranger Admin keystore
- Download the PKCS7b (.pem) certificate file (for example, cert.pem) from your certificate provider
scpit to the node hosting Ranger Admincp cert.pem cert.p7bopenssl pkcs7 -print_certs -in cert.p7b -out cert.ceropenssl pkcs12 -export -in cert.cer -inkey <certificate key file> -out rangeradmin.p12 -name rangeradmin- Create a keystore for Ranger Admin Service from the certificate:
keytool -importkeystore -deststorepass temp4now -destkeypass temp4now -srckeystore rangeradmin.p12 -srcstoretype PKCS12 -destkeystore ranger-admin-keystore.jks -deststoretype JKS -alias rangeradmin
You should now have the ranger-admin-keystore.jks keystore file generated. cp ranger-admin-keystore.jks /etc/ranger/admin/conf/cd /etc/ranger/admin/conf/- Set permissions:
chown ranger:ranger ranger-admin-keystore.jkschmod 400 ranger-admin-keystore.jks
You will need to perform similar steps on the Big SQL node side, using the SSL certificate for that node, to generate Big SQL plugin keystore and place the .jks file in /etc/bigsql/conf.
Step 4: Generate truststores
As mentioned before, the truststores are used to store the certificates of the other parties that shall be trusted in an SSL Connection.
Example: Set up Big SQL plugin truststore
- From the Ranger Admin host, export rangeradmin certificate:
keytool -export -keystore ranger-admin-keystore.jks -alias rangeradmin -file rangeradmin.cer -storepass temp4now - Get (scp) rangeradmin.cer on the master node for Big SQL
- Create truststore for Big SQL. On Big SQL Head node:
keytool -import -file rangeradmin.cer -alias rangeradmin -keystore /etc/bigsql/conf/bigsql-plugin-truststore.jks -storepass temp4now
You will need to perform similar steps to set up Ranger Admin truststore to trust the Big SQL node certificate. This time, you will need to export the certificate from the Big SQL keystore, scp it to the Ranger Admin host, and create the truststore using keytool -import -file bigsqlplugin.cer.
Step 5: Configure Ranger Admin for SSL
For instructions see Configuring Ranger Admin for your HDP version.
Step 6: Configure Big SQL for SSL
See the “Procedure” section on the Configuring the Db2 Big SQL Ranger plugin for SSL using public CA certificates Big SQL knowledge article.
server-keystore.jksin our example is Ranger keystore (/etc/ranger/admin/conf/ranger-admin-keystore.jks)agent-keystore.jksis the Big SQL keystoreagent-truststore.jksis the Big SQL truststore
As a result, your Big SQL Ranger plugin will be communicating with the Ranger Admin API via a secure SSL connection.