How To
Summary
Customer would like their end users to logon to Controller by using their Windows (domain / active directory) username and password.
How can they achieve this?
NOTE: This Technote specifically relates to the new feature (introduced in Controller 10.4.2) which allows AD authentication directly - without using Cognos Analytics (or Cognos BI) as the authentication mechanism.
* If you still want to use Cognos Analytics, then see separate IBM Technote #302865.
* If you still want to use Cognos BI , then see separate IBM Technote #623043.
Objective

- This is a new feature (since Controller 10.4.2)
Environment
- Controller 10.4.2 (or later)
- Controller application server hosted on Windows 2012 (or later)
- The Controller application server must belong to the same Microsoft AD domain that the end users (who logon to Controller) reside in
Steps
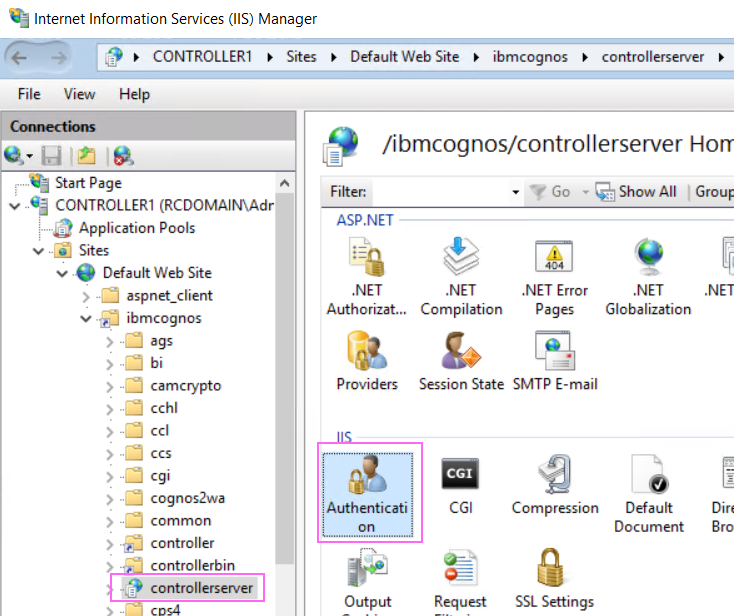
4. Double-click Authentication.
5. Enable both of the following:
- Anonymous Authentication
- Windows Authentication

6. Launch Controller Configuration
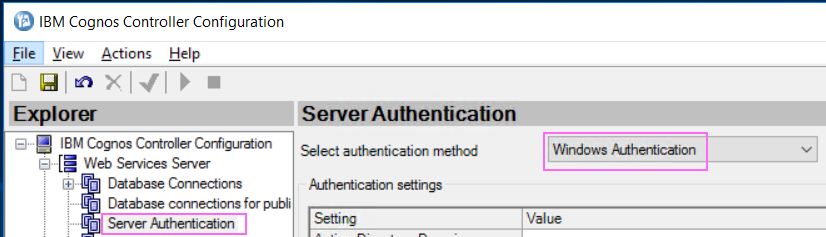
7. Select Server Authentication
8. In the authentication method, select Windows Authentication:
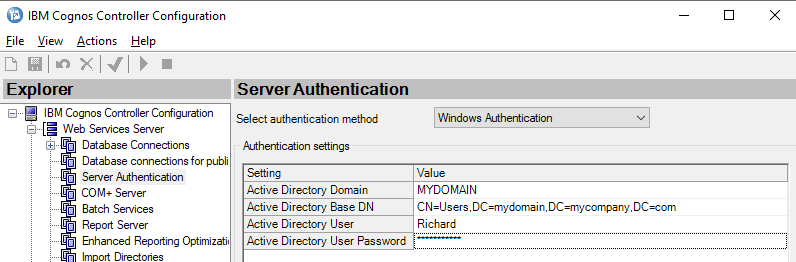
9. Under Authentication settings, set the following values:
- Active Directory Domain <Domain name of the Active Directory>
- You can use the NetBIOS domain name (for example "MYDOMAIN") or the FQDN domain name (for example "mydomain.mycompany.com")
- Active Directory Base DN <Search path from which look up of users is done>
- Active Directory User <User to bind to the Active Directory>
- This can be any user (does not have to be a domain administrator for example). Typically this would be a special 'service' account (for example 'controller_service') created in the Active Directory for just this purpose.
- IMPORTANT: You must make sure that this user's password never expires or changes!
- Active Directory User Password <Password of the Active Directory user>
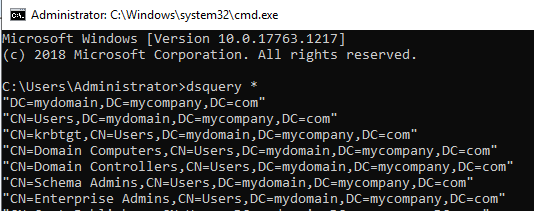
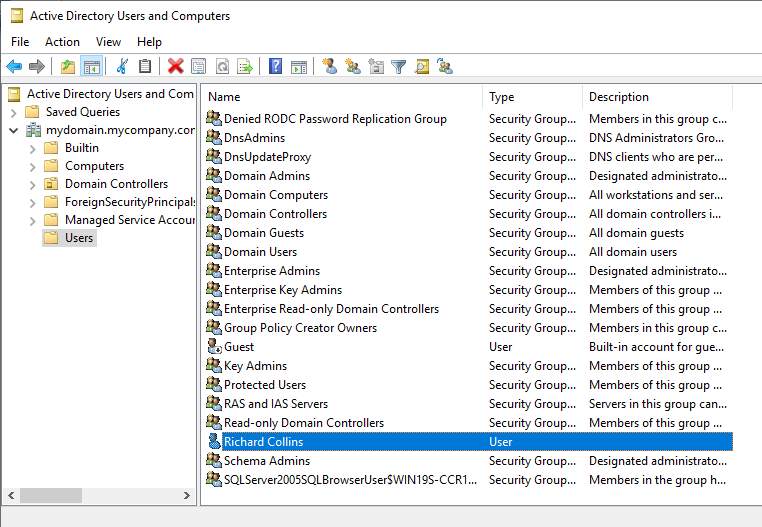
- TIP: By default this is here: C:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web
- loginMode=ACTIVE_DIRECTORY
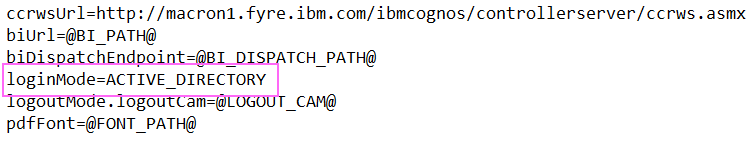
- In this example, I shall choose: MYDOMAIN\Administrator
- This first Windows user will automatically get mapped (during the logon process) to the Controller user 'ADM'
- You can visibly see this by opening the Controller database table "XWINDOWSUSER", for example:
- Select an existing (unmapped) user from the left hand side (for example "Fred" in the below example)
- Click on the browse button (…) in the 'Active Directory User' section:
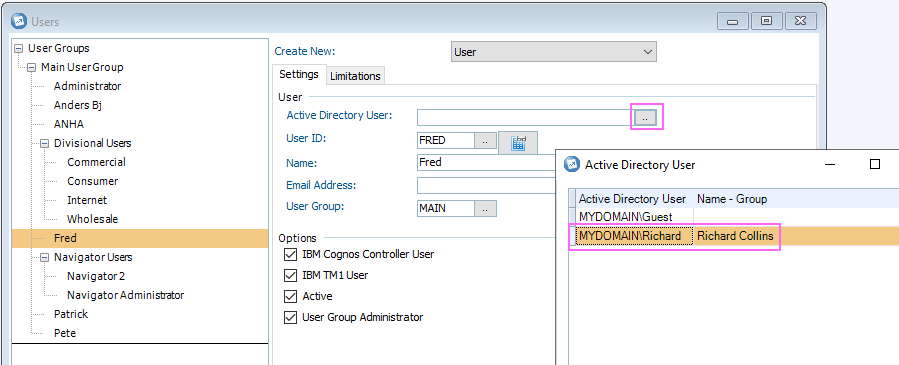
- Choose which Active Directory user (for example 'MYDOMAIN\Richard') that you want mapped to the Controller user (for example 'FRED')
- Change 'Create New' to 'Users'
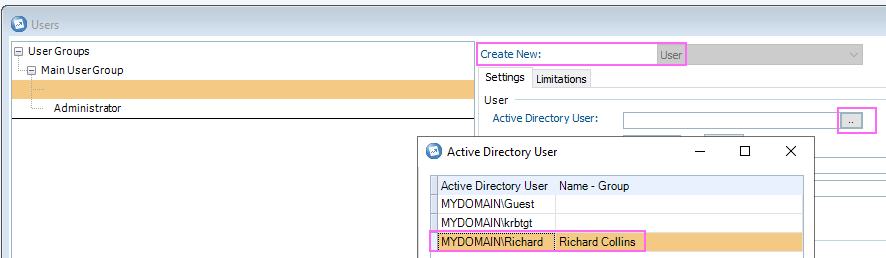
- Click on the browse button (…) in the 'Active Directory User' section
- Select the user which you want to use (for example 'MYDOMAIN\Richard'):
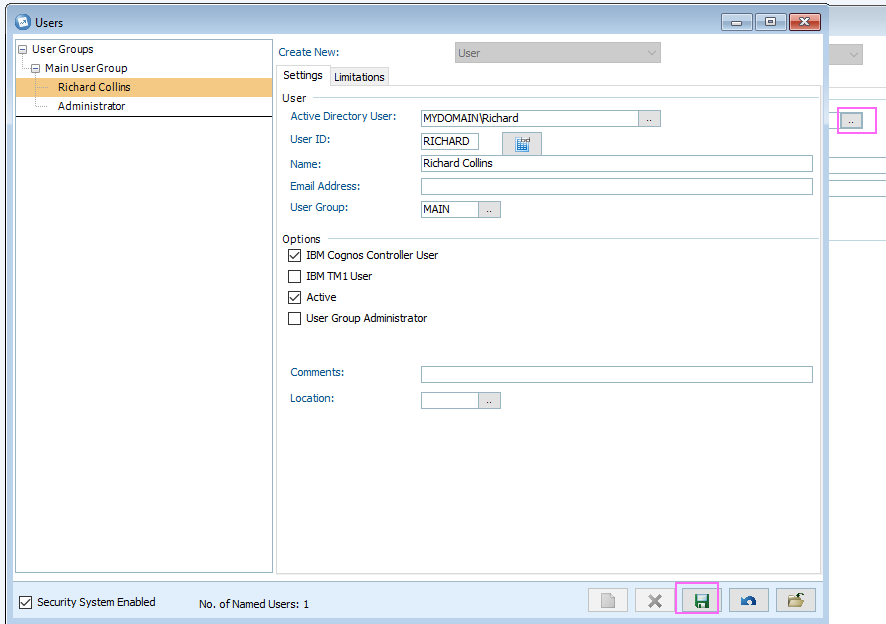
- Complete any other sections/settings (as desired) and press Save:
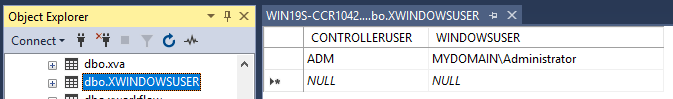
- TIP: You can verify that the users have been mapped, by looking at the Controller database table "XWINDOWSUSER", for example:

- Logon to Windows using the new user's Active Directory user account
- Launch Controller client
- Click "Help - System Info"
- Near the top it should show the user's correct Controller (not Active Directory) username, for example:

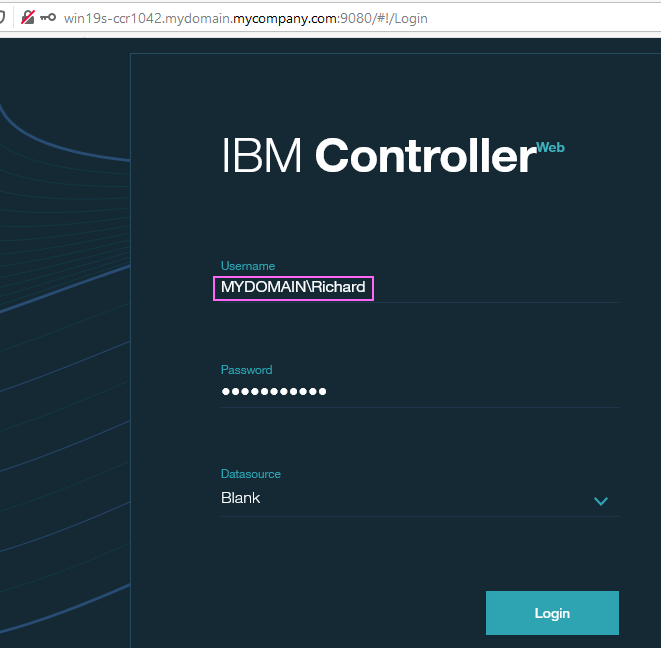
- In your web browser, type the URL (for example: http://<servername>:9080 )
- Ensure your username looks similar to: <domainname>\<username>
- See separate IBM Technote #6243458 for more details.

2. In Server Manager, click the Manage menu, and then click Add Roles and Features
3. In the Add Roles and Features wizard, click Next. Select the installation type and click Next. Select the destination server and click Next.
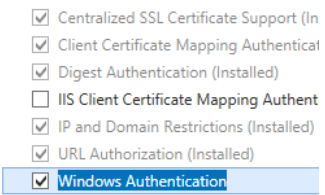
4. On the Server Roles page, expand Web Server (IIS), expand Web Server, expand Security, and then select Windows Authentication:
5. On the Select features page, click Next.
6. On the Confirm installation selections page, click Install.
7. On the Results page, click Close.
Related Information
New features in Cognos Controller 10.4.2
Controller 10.4.2 - Configure Active Directory authentication
Third Party (Microsoft) - Adding Windows Authentication Providers <add>
623043 - How to configure Controller to use Active Directory authentication wit…
6243458 - CCR.CONFIG file not fully populated (missing "LastUser" entry) for br…
Document Location
Worldwide
Was this topic helpful?
Document Information
Modified date:
03 July 2020
UID
ibm16209654