How To
Summary
Installing the Bouncy Castle JCE may be necessary if any of your devices encounter restrictions with the IBM JCE.
Steps
Go to https://www.bouncycastle.org and locate the latest signed provider JARs for JDK7/JDK1.7. For example:
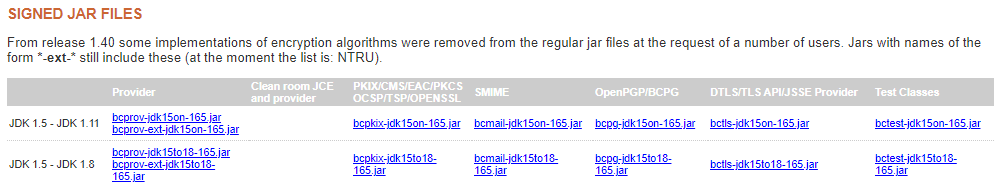
As of writing the URL for the JARs is https://www.bouncycastle.org/latest_releases.html and the files you need to download are:
- bcprov-jdk15on-165.jar
- bcprov-ext-jdk15on-165.jar
Transfer these JARs to the home directory of the user that installed ITNCM. This should be done for all ITNCM servers that process UOWs.
On the ITNCM servers, perform the following commands to copy the JARs to ncm/jre/lib/ext:
netcool$ cd /opt/IBM/tivoli/netcool/ncm/jre/jre/lib/ext
netcool$ cp ~/bcprov-jdk15on-165.jar .
netcool$ cp ~/bcprov-ext-jdk15on-165.jar .
netcool$ cp ~/bcprov-jdk15on-165.jar .
netcool$ cp ~/bcprov-ext-jdk15on-165.jar .
Now that the JARs are in place, we will also have to edit java.security to include them in the list of JCE providers ITNCM will use. Use commands such as the following to begin editing this file:
netcool$ cd /opt/IBM/tivoli/netcool/ncm/jre/jre/lib/security
netcool$ cp java.security java.security.backup
netcool$ vi java.security
netcool$ cp java.security java.security.backup
netcool$ vi java.security
Look for a list of lines with security.provider.X where X is some number, i.e.
security.provider.1=com.ibm.crypto.pkcs11impl.provider.IBMPKCS11Impl
security.provider.2=com.ibm.crypto.provider.IBMJCE
security.provider.3=com.ibm.jsse2.IBMJSSEProvider2
...
security.provider.2=com.ibm.crypto.provider.IBMJCE
security.provider.3=com.ibm.jsse2.IBMJSSEProvider2
...
At the top of the list add the line:
security.provider.1=org.bouncycastle.jce.provider.BouncyCastleProvider
Then for all other lines in the list, increment the X in security.provider.X by 1. The end result should be similar to:
security.provider.1=org.bouncycastle.jce.provider.BouncyCastleProvider
security.provider.2=com.ibm.crypto.pkcs11impl.provider.IBMPKCS11Impl
security.provider.3=com.ibm.crypto.provider.IBMJCE
security.provider.4=com.ibm.jsse2.IBMJSSEProvider2
...
security.provider.2=com.ibm.crypto.pkcs11impl.provider.IBMPKCS11Impl
security.provider.3=com.ibm.crypto.provider.IBMJCE
security.provider.4=com.ibm.jsse2.IBMJSSEProvider2
...
Finally restart ITNCM for the Bouncy Castle provider to take effect.
You can verify that the Bouncy Castle JCE has taken effect by running an AutoDiscovery against the server ITNCM is installed on. Create a text file 127.0.0.1.txt in directory /opt/IBM/tivoli/netcool/ncm/autodiscovery:
netcool$ cd /opt/IBM/tivoli/netcool/ncm/autodiscovery
netcool$ vi 127.0.0.1.txt
netcool$ vi 127.0.0.1.txt
The contents of 127.0.0.1.txt should be:
a:doesnotmatter
p:doesnotmatter
e:doesnotmatter
d:./bcresults
r:doesnotmatter
127.0.0.1
p:doesnotmatter
e:doesnotmatter
d:./bcresults
r:doesnotmatter
127.0.0.1
Edit ad.properties so that SSH port 22 is used for the Discovery process:
netcool$ cp ad.properties ad.properties.backup
netcool$ vi ad.properties
netcool$ vi ad.properties
Edit connectionType and sshPort so that their values are set as shown below:
connectionType=ssh
sshPort=22
sshPort=22
Edit autodiscover.sh so that MindTerm logs the JCE providers it may use:
netcool$ vi autodiscover.sh
Locate the following line:
/opt/IBM/tivoli/netcool/ncm/jre/bin/java -Dinstall.dir=${INSTALL_DIR} -classpath ${CLASSPATH} com.intelliden.tools.autodiscovery.RunAutoDiscovery ${PARAM1} ${PARAM2}
And add in the command line option -Dmindterm.jce.debug=yes, e.g.
/opt/IBM/tivoli/netcool/ncm/jre/bin/java -Dinstall.dir=${INSTALL_DIR} -Dmindterm.jce.debug=yes -classpath ${CLASSPATH} com.intelliden.tools.autodiscovery.RunAutoDiscovery ${PARAM1} ${PARAM2}
Finally run autodiscover.sh and inspect the additional logging produced on the console to ensure it contains provider=BC, e.g.
netcool$ ./autodiscover.sh 127.0.0.1.txt
...
Added JCE: org.bouncycastle.jce.provider.BouncyCastleProvider
getCipher(AES/CBC/NoPadding): provider=BC version 1.58
getCipher(CAST5/CBC/NoPadding): provider=BC version 1.58
getKeyPairGenerator(DH): provider=BC version 1.58
Initializing PRNG
Using PRNG: java.security.SecureRandom@f86b1aff provider: BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyAgreement(ECDH): provider=BC version 1.58
getSignature(SHA512/ECDSA): provider=BC version 1.58
getMD(SHA-256): provider=BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyFactory(EC): provider=BC version 1.58
getKeyAgreement(ECDH): provider=BC version 1.58
getSignature(SHA256/ECDSA): provider=BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyFactory(EC): provider=BC version 1.58
getCipher(AES/CTR/NoPadding): provider=BC version 1.58
getMac(HmacSHA1): provider=BC version 1.58
getCipher(AES/CTR/NoPadding): provider=BC version 1.58
getMac(HmacSHA1): provider=BC version 1.58
...
...
Added JCE: org.bouncycastle.jce.provider.BouncyCastleProvider
getCipher(AES/CBC/NoPadding): provider=BC version 1.58
getCipher(CAST5/CBC/NoPadding): provider=BC version 1.58
getKeyPairGenerator(DH): provider=BC version 1.58
Initializing PRNG
Using PRNG: java.security.SecureRandom@f86b1aff provider: BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyAgreement(ECDH): provider=BC version 1.58
getSignature(SHA512/ECDSA): provider=BC version 1.58
getMD(SHA-256): provider=BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyFactory(EC): provider=BC version 1.58
getKeyAgreement(ECDH): provider=BC version 1.58
getSignature(SHA256/ECDSA): provider=BC version 1.58
getKeyPairGenerator(EC): provider=BC version 1.58
getKeyFactory(EC): provider=BC version 1.58
getCipher(AES/CTR/NoPadding): provider=BC version 1.58
getMac(HmacSHA1): provider=BC version 1.58
getCipher(AES/CTR/NoPadding): provider=BC version 1.58
getMac(HmacSHA1): provider=BC version 1.58
...
Document Location
Worldwide
[{"Business Unit":{"code":"BU053","label":"Cloud & Data Platform"},"Product":{"code":"SS7UH9","label":"Tivoli Netcool Configuration Manager"},"ARM Category":[],"Platform":[{"code":"PF016","label":"Linux"}],"Version":"All Versions","Edition":"","Line of Business":{"code":"LOB45","label":"Automation"}}]
Was this topic helpful?
Document Information
Modified date:
15 March 2021
UID
ibm16173331