Troubleshooting
Problem
This document provides required steps to configure custom SSL certifitcates for TM1Web, pmpsvc, and pmhub web applications run with Tomcat.
Environment
IBM Cognos TM1 10.2 and 10.2.2 on Windows, AIX and Linux.
Resolving The Problem
Create the Certificate Requests
Create a working directory named ssl in D:\Program Files\ibm\cognos\tm1_64\
From the D:\Program Files\ibm\cognos\tm1_64\bin directory run the following ThirdPartyCertificateTool commands to generate the encryption and signing certificate requests. The cn value will typically match the fully qualified domain name of the system running TM1Web.
ThirdPartyCertificateTool.bat -java:local -c -e -d cn=tm1web.domain.com -D "D:\Program Files\ibm\cognos\tm1_64\configuration\encryptkeypair" -r "D:\Program Files\ibm\cognos\tm1_64\ssl\encryptrequest.csr" -p NoPassWordSet
ThirdPartyCertificateTool.bat -java:local -c -s -d cn=tm1web.domain.com -D "D:\Program Files\ibm\cognos\tm1_64\configuration\signkeypair" -r "D:\Program Files\ibm\cognos\tm1_64\ssl\signrequest.csr" -p NoPassWordSet
The certificate request files named signrequest.csr and encryptrequest.csr in the D:\Program Files\ibm\cognos\tm1_64\ssl\ directory.
Have the Certificate Requests Signed by a Certificate Authority
The certificate request must be provided to a certificate authority (CA). The CA will respond with issued signing, encryption, and the CA certificates.
It's common for the certificate authority to provide both the issued certificate and CA certificates in a single file. The issued certificate must be copied into it's own file (encryptcert.pem and signcert.pem) and all CA certificates should be placed in a single file (ca.pem). If the issued and CA certificates are provided in single base64 file a text editor can be used to split the certificates into separate files. If the files provided by the CA are not in base64 format the Windows certificate utility or openSSL can be used to convert into base64 format.
For additional information about certificate formats please see: https://support.microsoft.com/en-us/help/216830/how-to-view-the-contents-of-a-certificate
Import the Encryption and CA Certificates
Copy the signcert.pem, encryptcert.pem, and ca.pem files into the D:\Program Files\ibm\cognos\tm1_64\ssl\ directory.
From the .\tm1_64\bin\ directory run the following commands:
ThirdPartyCertificateTool.bat -java:local -i -e -D "D:\Program Files\ibm\cognos\tm1_64\configuration\encryptkeypair" -r "D:\Program Files\ibm\cognos\tm1_64\ssl\encryptcert.pem" -t "D:\Program Files\ibm\cognos\tm1_64\ssl\ca.pem" -p NoPassWordSet
ThirdPartyCertificateTool.bat -java:local -i -s -D "D:\Program Files\ibm\cognos\tm1_64\configuration\signkeypair" -r "D:\Program Files\ibm\cognos\tm1_64\ssl\signcert.pem" -t "D:\Program Files\ibm\cognos\tm1_64\ssl\ca.pem" -p NoPassWordSet
ThirdPartyCertificateTool.bat -java:local -i -T -D "D:\Program Files\ibm\cognos\tm1_64\configuration\signkeypair" -r "D:\Program Files\ibm\cognos\tm1_64\ssl\ca.pem"
-p NoPassWordSet
Setup Cognos Configuration to use the SSL Certificate
Add the following property under the Local Configuration - Advanced Properties section.

Update the TM1 Applications settings in Cognos Configuration to specify https.
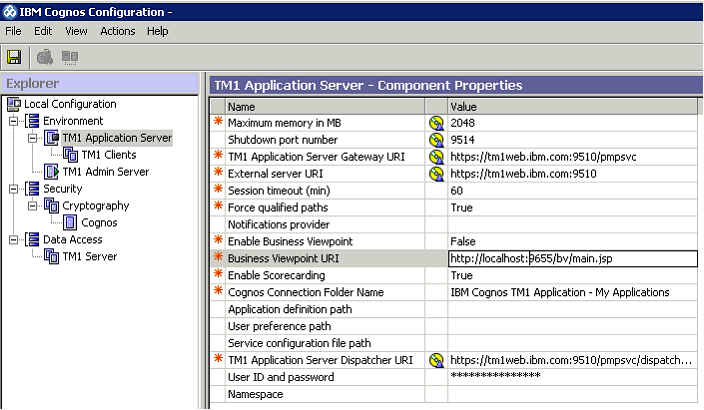
Set use third part CA to true in the Security - Cryptography - Cognos section of Cognos Configuration.

Restart the IBM Cognos TM1 Service from Cognos Configuration and test the TM1Web URL using HTTPS (https://servername.yourdomain.com:9510/tm1web).
At this point it's also strongly recommended to backup the .\tm1_64\configuration\certs\ directory and the .\tm1_64\configuration\cogstartup.xml.
Was this topic helpful?
Document Information
Modified date:
15 June 2018
UID
swg21902547