Technical Blog Post
Abstract
IBM Tivoli Monitoring Nuggets: KFWITM393E Locked out of the Tivoli Enterprise Portal client with an invalid username or password
Body
It is a Monday morning. You are assigned a heap of work to get through. You cannot log into the Tivoli Enterprise Portal. You are presented with the dreaded "KFWITM393E" error. Do not reach for those painkillers. We explain how to get you back on your feet fast!
When you log on to the Tivoli Enterprise Portal, you are presented with the following error message:
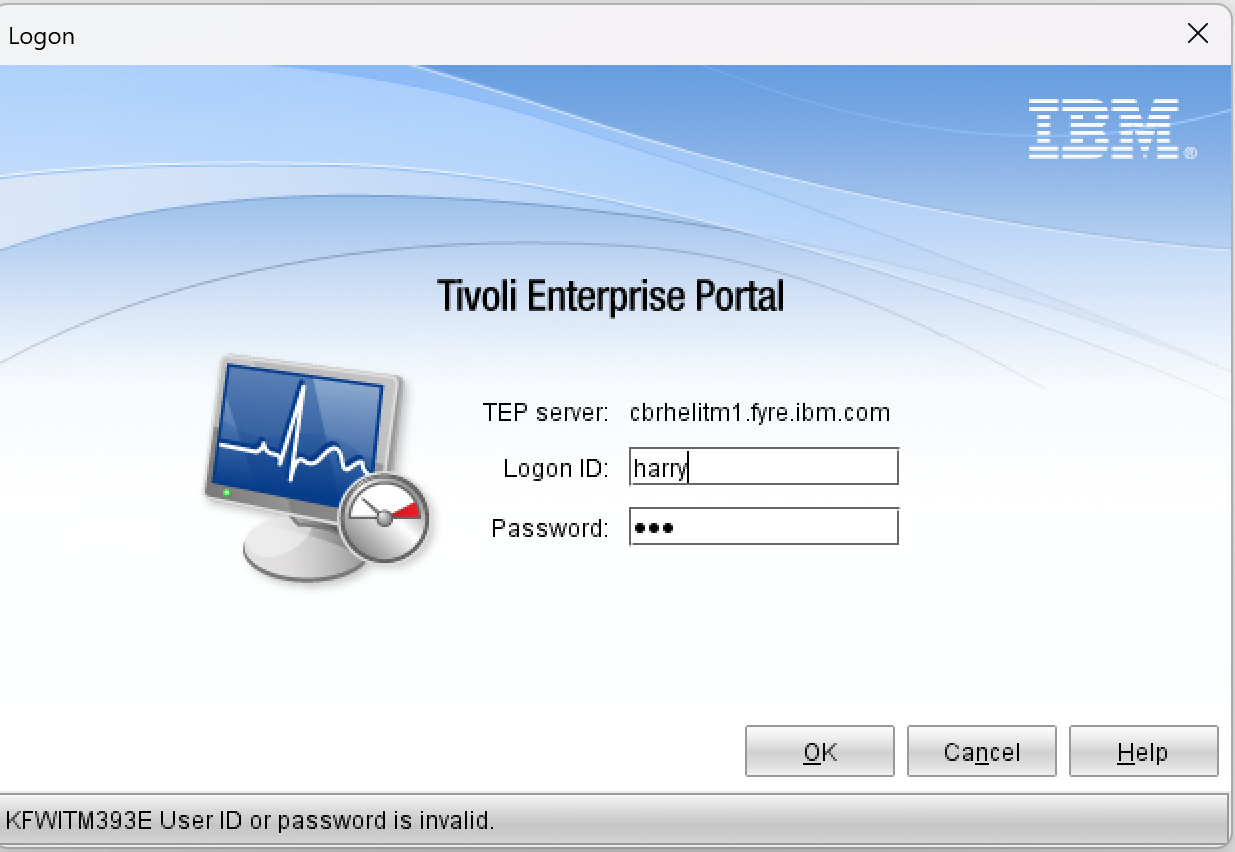
There are several reasons why the KFWITM393E error can occur. We have several solutions to help resolve the most common causes.
Background
First, here is how the authentication process works. There are 3 types of authentication available to users in IBM Tivoli Monitoring:
- Tivoli Enterprise Portal Server Authentication
- Tivoli Enterprise Monitoring Server Operating system - Validate User Authentication
- LDAP Authentication (This option can be enabled on the Tivoli Enterprise Portal Server or Tivoli Enterprise Monitoring Server, but not both.)
With all 3 types of authentication, access to the Tivoli Enterprise Portal is controlled by user accounts defined in the portal server. It is required for every user ID to contain an associated account created in the portal server to gain access. These IDs control which users are authorized to log in to the Tivoli Enterprise Portal and define the permissions for that account. For example, what each user can see, access, and modify. You can check which user IDs you have on the Tivoli Enterprise Portal Server by checking under User Administration.
Tivoli Enterprise Portal Server Authentication
Tivoli Enterprise Portal Server authentication is solely managed by the user ID defined in the Tivoli Enterprise Portal. If a user ID is listed in the repository, that user can log in to the Tivoli Enterprise Portal without any password. Only the user ID is required.
You can check whether this type of authentication is enabled by reviewing the configuration.
First, check the Hub TEMS settings to ensure the monitoring server is not authenticating.
For Unix/Linux/AIX:
Check the settings for the HUB monitoring server in $CANDLEHOME/config/ms.config:
If user validation is not enabled, the value is:
KDS_VALIDATE='NO'
For Windows:
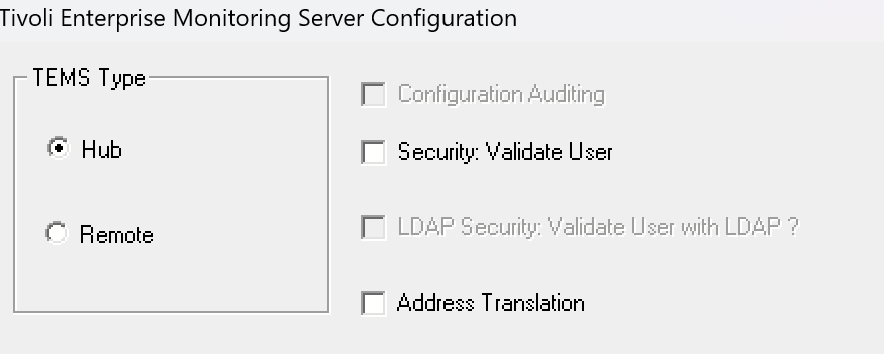
You can determine whether authentication for the monitoring server is enabled by reconfiguring the HUB Tivoli Enterprise Monitoring Server component. Start by checking the settings on the first screen that appears.
Note: If neither options, "Security: Validate User" and "LDAP Security: Validate User with LDAP", are enabled, then Tivoli Enterprise Portal Server's authentication is enabled.
Tivoli Enterprise Monitoring Server operating system - Validate User Authentication
User security is the authentication type enabled on the HUB Tivoli Enterprise Monitoring Server. The type of authentication requires a user ID and a password to log in to the Tivoli Enterprise Portal.
The HUB Tivoli Enterprise Monitoring Server (HUB monitoring server) host controls password authentication. When a user logs in to the Tivoli Enterprise Portal, the Portal Server queries the HUB monitoring server to validate the account and sends the encrypted user ID and password. The HUB monitoring server validates the account by sending a request to the operating system to ensure the user ID and password are correct. The Tivoli Enterprise Portal user ID and associated passwords must be defined on the HUB monitoring server system.
The chart details where the user ID and password need to be set on the HUB Tivoli Enterprise Monitoring Server's operating system for the authentication to work:
| The operating system for the hub monitoring server | Method of password authentication |
|---|---|
| Windows | User operating system accounts |
| Linux and UNIX | Password files |
| z/OS | RACF, CA-ACF2, CA-TOP SECRET, or Network Access Method |
You can check whether this type of authentication is enabled by reviewing the monitoring server's configuration settings.
For Unix/Linux/AIX:
Check the settings for the HUB monitoring server in $CANDLEHOME/config/ms.config:
If user validation is enabled and OS authentication is being used, the values are:
KDS_VALIDATE='YES'
KGL_LDAP_VALIDATE='NO'
For Windows:
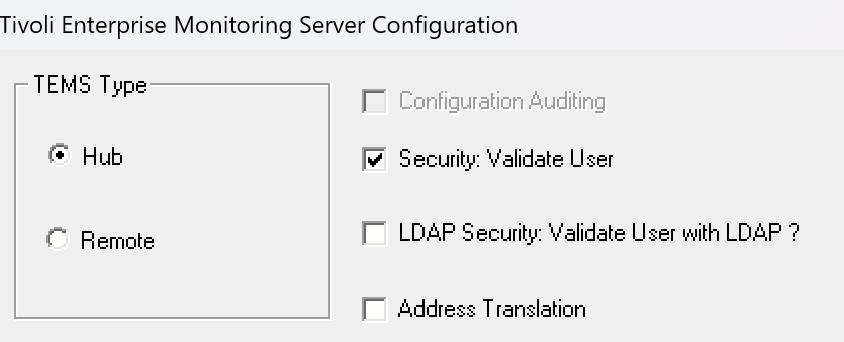
You can check whether the type of authentication is enabled by reconfiguring the HUB Tivoli Enterprise Monitoring Server component.
Check the settings on the first screen that appears. Ensure the checkbox for the "Security: Validate User" option is enabled.
LDAP Authentication
When you enable security on the HUB monitoring server or the portal server, you can select validation to use LDAP instead of the local registry for user authentication. The users you created in the Tivoli Enterprise Portal are then mapped to the LDAP repository usernames and passwords. For the LDAP authentication to function correctly, the username in the Tivoli Enterprise Portal must match a user in the LDAP repository. The passwords are then authenticated against the information on the LDAP server.
NOTE: LDAP is not supported for HUB monitoring servers on z/OS.
NOTE: You can enable LDAP authentication at the HUB monitoring server or the portal server. Do not enable LDAP authentication on both.
You can check whether this type of authentication is enabled by reviewing the configuration settings.
For Unix/Linux/AIX:
For the monitoring server's LDAP authentication, review the settings within the $CANDLEHOME/config/ms.config file.
If user validation for LDAP is enabled, the value is:
KDS_VALIDATE='YES'
KGL_LDAP_VALIDATE='YES'
For the portal server's LDAP authentication, review the settings within the $CANDLEHOME/config/cq.config file.
If user validation for LDAP is enabled, the value is:
KFW_LDAP_ENABLED='YES'
For Windows:
For the monitoring server's LDAP authentication:
You can determine whether the LDAP authentication for the monitoring server is active by reconfiguring the HUB Tivoli Enterprise Monitoring Server component. Start by checking the settings on the first screen that appears. Ensure the checkboxes for both "Security: Validate User" and "LDAP Security: Validate User with LDAP" options are enabled.
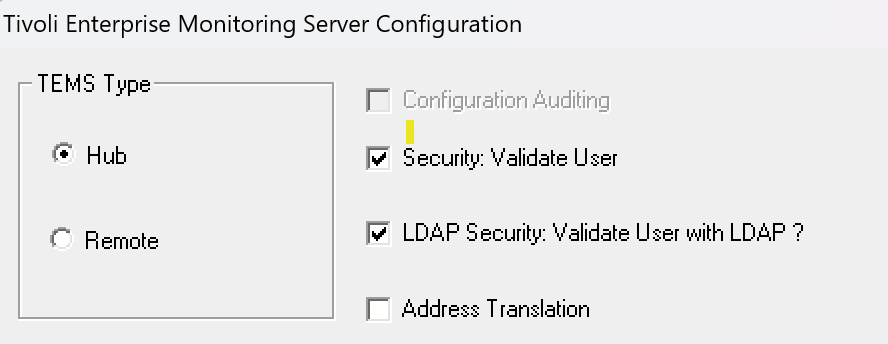
For the portal server's LDAP authentication:
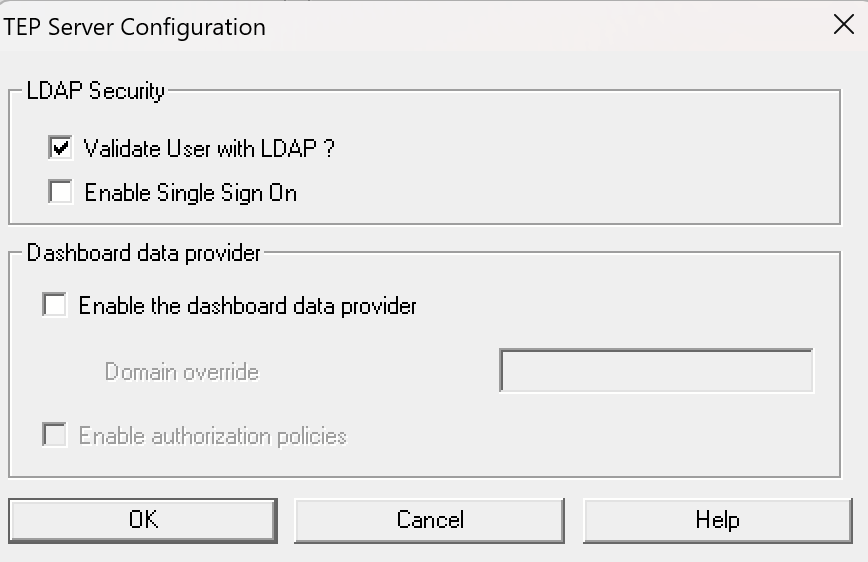
You can determine whether the LDAP authentication for the portal server is active by reconfiguring the Tivoli Enterprise Portal Server component. Start by checking the settings when the following screen appears. Ensure the checkbox for "Validate User with LDAP" option is enabled.
Checklist to resolve your issue
- Ensure that the user ID is defined in the IBM Tivoli Monitoring infrastructure
- Validate that the password is correct
- Check the character length of the password for the Tivoli Enterprise Monitoring Server Operating system - Validate User Authentication
Ensure that the user ID is defined in the IBM Tivoli Monitoring infrastructure
The user ID entered must match the user ID on the portal server. If the user ID does not exist, the user is unable to log in. You can validate in two ways:
- Log on to the portal server with a valid user ID and check the user that fails appears in the list. If it does not, you must create it to grant access.
- If no user ID can log on, you can check what users exist by reviewing the contents of the Tivoli Enterprise Portal Server database. All portal users are stored in a table called KFWUSER. When you query the table, the column labeled "ID" matches the user ID you are trying to log in with. If all users are missing, including "sysadmin," then you need to investigate if any recent changes on the Tivoli Enterprise Portal Server or its database caused the contents to be removed.
Validate that the password is correct
The next step is to check that your password is correct.
To verify the password for the monitoring server's operating system authentication, log in to the monitoring server's host operating system. Use the same username and password that is used on the portal client. If the username and password fail to authenticate, then you can try to reset the password for that account from within the operating system where the HUB Tivoli Enterprise Monitoring Server is located.
These steps ensure that the password you are using is correct and the same one listed on the operating system account on the server with HUB Tivoli Enterprise Monitoring Server.
Check the character length of the password for the Tivoli Enterprise Monitoring Server Operating system - Validate User Authentication
If you are using the Tivoli Enterprise Monitoring Server Operating system - Validate User Authentication, there is a 15-character password limit. Due to the restriction, the Tivoli Enterprise Portal Server passes only 15 characters of the password for validation when Tivoli Enterprise Monitoring Server authentication is used. To rectify this issue, you can update the password for the user to a maximum of 15 characters. The user ID can be up to and including 10 characters long.
Next steps
If all the prior steps still do not resolve the issue, you need to enable traces on the Tivoli Enterprise Portal Server server to diagnose this problem further.
The trace level to set:
ERROR (UNIT:ctsql IN ER) (UNIT:ctdata IN ER) (UNIT:ctauth ALL)
This tracing level captures the SQL calls, the data calls, and any information related to the authorization that passes through the Tivoli Enterprise Portal Server. This trace level enables IBM Support to see any errors related to the username and password failure as the request passes through the Tivoli Enterprise Portal Server.
How to set the tracing:
| Using the GUI for monitoring server traces |
Using the Manage Tivoli Enterprise Monitoring Services (MTEMS) utility on Windows:
1. Right-click on Tivoli Enterprise Portal Server
2. Select Advanced -> Edit trace parms... 3. In the box labeled "Enter RAS1 Filters:" enter the following:
4. Select OK (to implement the change) |
| Editing the configuration file |
1. Open the file:
Windows: <ITM_HOME>\CNPS\kfwenv Unix: <ITM_HOME>/config/cq.ini 2. Edit to set the value for KBB_RAS1 and save it.
(Caution: Make sure that the value of KBB_RAS1 is not enclosed in any single or double quotation marks. Remember to backup before we make any modifications).
3. Restart the portal server.
|
If you want to set the tracing dynamically so you don't need to restart the component, then this technote ("Dynamically modify trace settings for an IBM Tivoli Monitoring component") guides you through the steps.
Replicate the issue
After you set the trace, restart the Tivoli Enterprise Portal Server, then attempt to log in and reproduce the error. Restarting the Tivoli Enterprise Portal Server enables the new trace level.
Review the logs
Next, collect then review the most recent *_cq_* log files from the $CANDLEHOME's logs directory on the Tivoli Enterprise Portal Server and the ms.ini from the Tivoli Enterprise Monitoring Server.
If you need to open a Support Ticket, use the pdcollect utility and provide this collection for the Support Ticket. The pdcollect utility captures all the required logs, system, and environmental information to diagnose your problem. Review the technote ("Using pdcollect in an IBM Tivoli Monitoring Environment") for guidance on pdcollect usage.
[{"Line of Business":{"code":"LOB45","label":"Automation"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSR36TS","label":"IBM Tivoli Monitoring"},"ARM Category":[{"code":"a8m3p000000hBWDAA2","label":"Authentication of TEP client\/LDAP"}],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions","Type":"MASTER"},{"Line of Business":{"code":"LOB45","label":"Automation"},"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSTFXA","label":"Tivoli Monitoring"},"ARM Category":[{"code":"a8m3p000000hBWDAA2","label":"Authentication of TEP client\/LDAP"}],"Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions","Type":"MASTER"}]
UID
ibm11082679