How To
Summary
This document lays out the configuration for MaaS360 Secure Mail to integrate with Azure SSO through Azure Active Directory.
Objective
This will outline the steps needed to create an app in Azure for MaaS360 and configure that app to properly pass SSO authentication through Azure from the MaaS360 Secure Mail app.
Environment
The configuration detailed here is for Azure SSO with MaaS360 Secure Mail on both iOS and Android.
Steps
- Sign in to the Microsoft Azure portal.
- On the home page, select Azure Active Directory.
- On the left navigation pane, click App registrations > New registration.
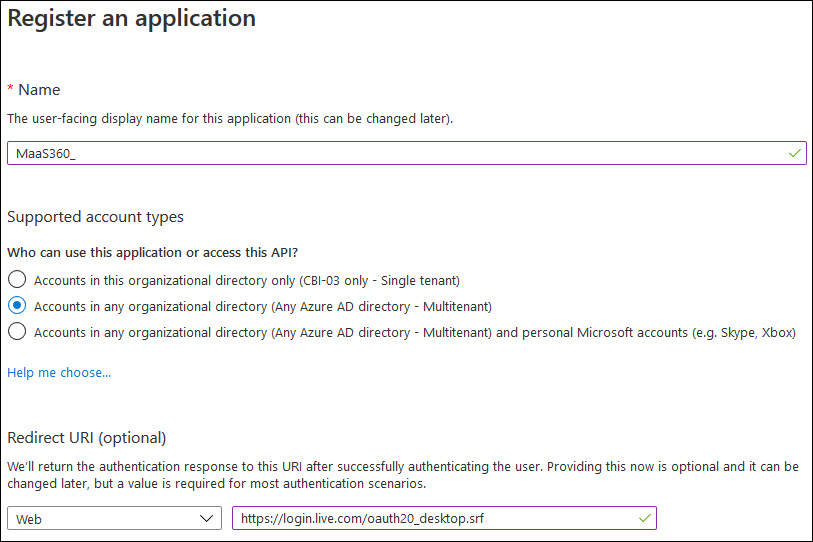
- Provide the following application registration details:
- Name: The display name of the application.
- Supported account types: Select Accounts in any organizational directory (Any Azure AD directory - Multitenant).
- Redirect URI: Select Web and then provide the following redirect URI:
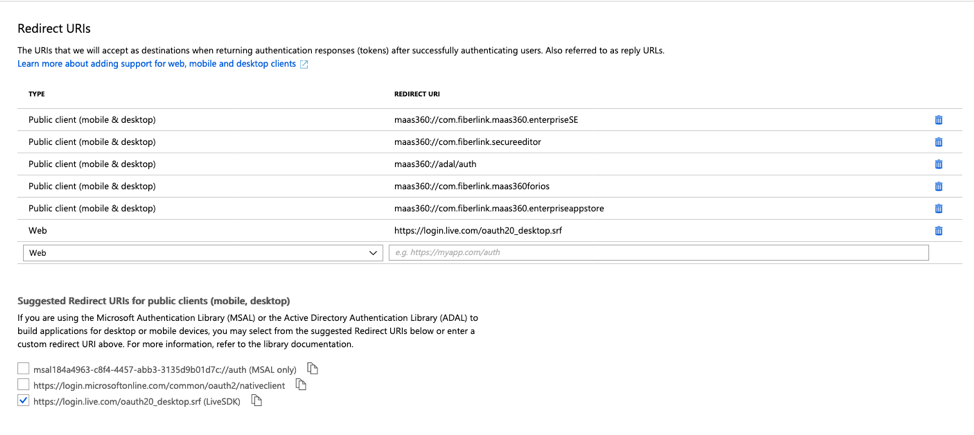
- Go to Authentication and add the following URI's:
o https://login.live.com/oauth20_desktop.srf
o maas360://com.fiberlink.maas360.enterpriseappstore
o maas360://com.fiberlink.maas360forios
o maas360://adal/auth
o maas360://com.fiberlink.secureeditor
o maas360://com.fiberlink.maas360.enterpriseSE
o maas360://com.fiberlink.maas360.enterpriseappstore
o maas360://com.fiberlink.maas360forios
o maas360://adal/auth
o maas360://com.fiberlink.secureeditor
o maas360://com.fiberlink.maas360.enterpriseSE
* Note: You have to change the type from Web to Public Client (mobile & desktop) for the maas360 prefixed URIs
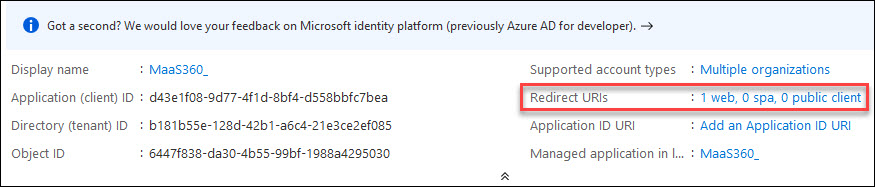
6. Click Register.
- The app is successfully registered.
7. Open the registered application and then click the Redirect URIs link.
-
The Platform configurations page is displayed.
8. Click Add a Platform, select iOS / macOS, and then add the following redirect URIs:
- com.fiberlink.maas360forios
- com.fiberlink.secureeditor
9. Click Add a Platform, select Mobile and desktop applications, and then add the following redirect URIs:
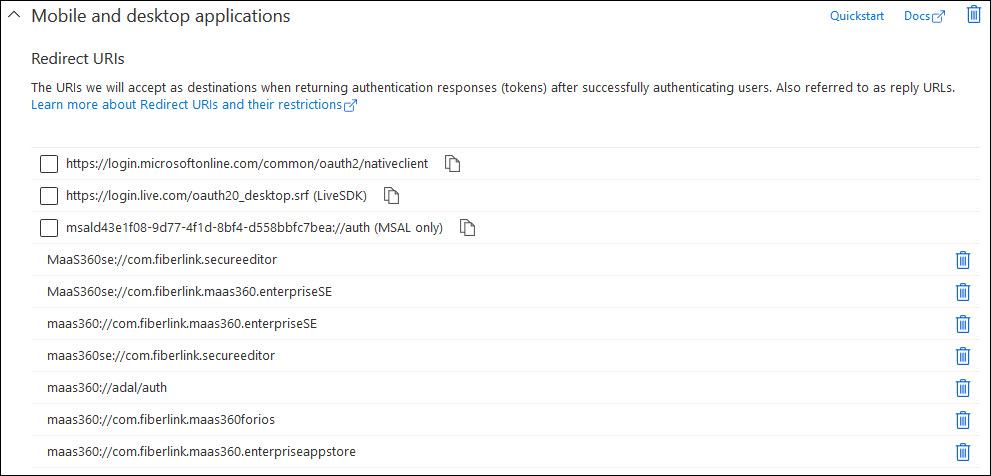
- maas360://com.fiberlink.maas360.enterpriseappstore
- maas360://com.fiberlink.maas360forios
- maas360://adal/auth
- maas360se://com.fiberlink.secureeditor
- maas360://com.fiberlink.maas360.enterpriseSE
- MaaS360se://com.fiberlink.maas360.enterpriseSE
- MaaS360se://com.fiberlink.secureeditor
10. Click Save.
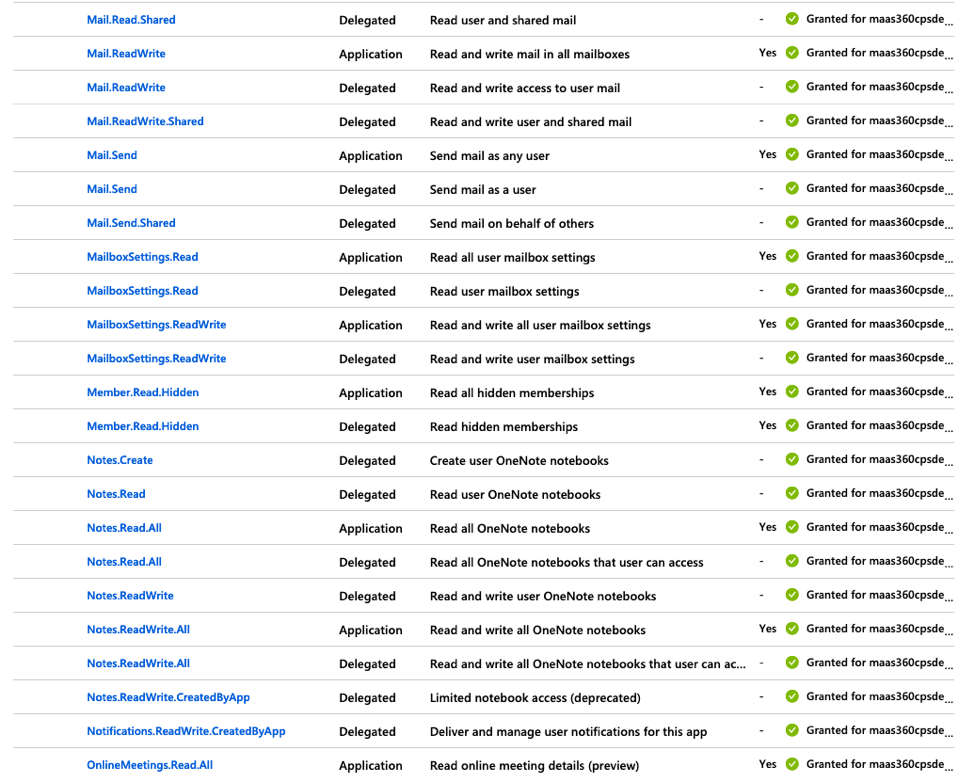
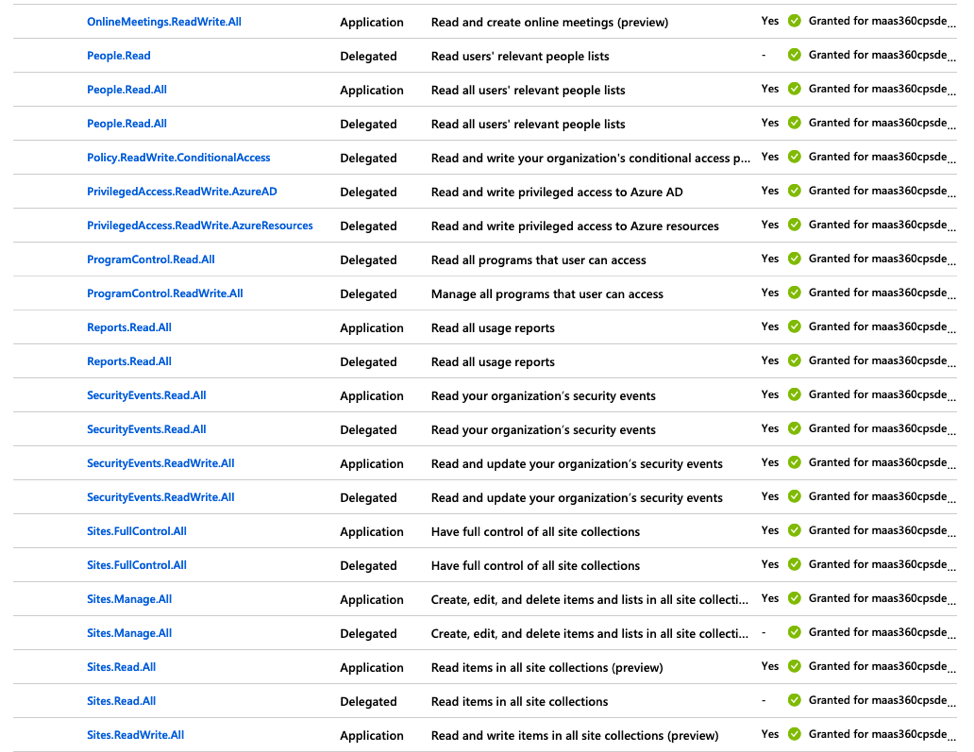
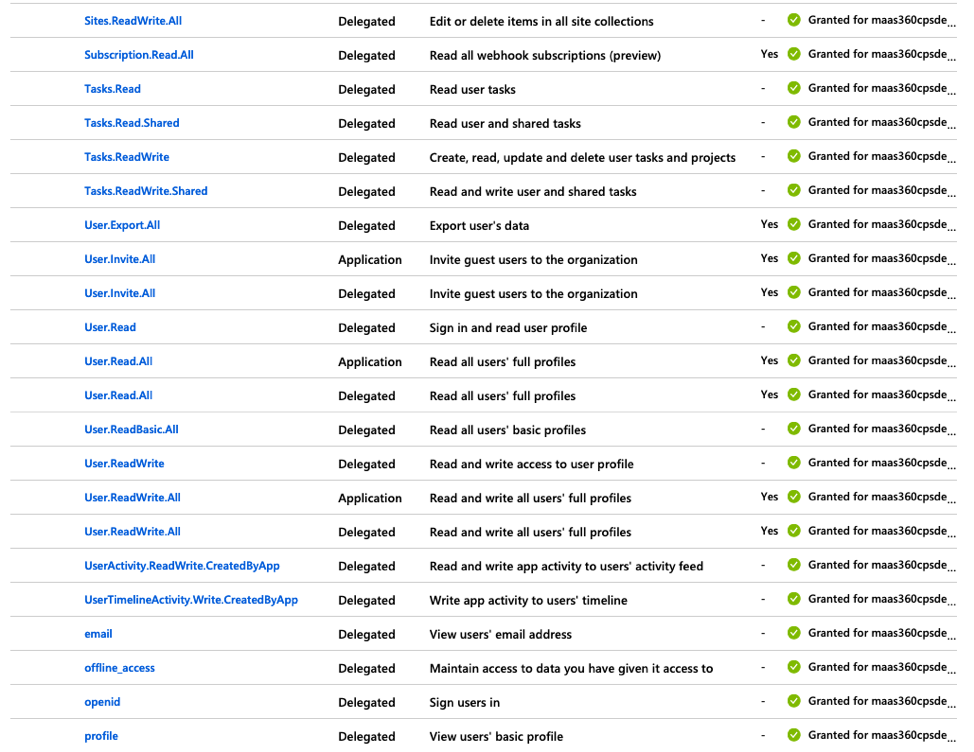
11. Click API Permissions in the left navigation pane and then click Add a permission to grant permissions for the services that are accessed by the MaaS360® app.
The Request API Permissions page is displayed.
- These permissions cover not only the ability for Secure Mail to do all of the necessary EWS functions for mail, but also the necessary SSO assertion permissions to authenticate the user in Azure. Here is a comprehensive list of permissions needed for the process to work end-to-end.
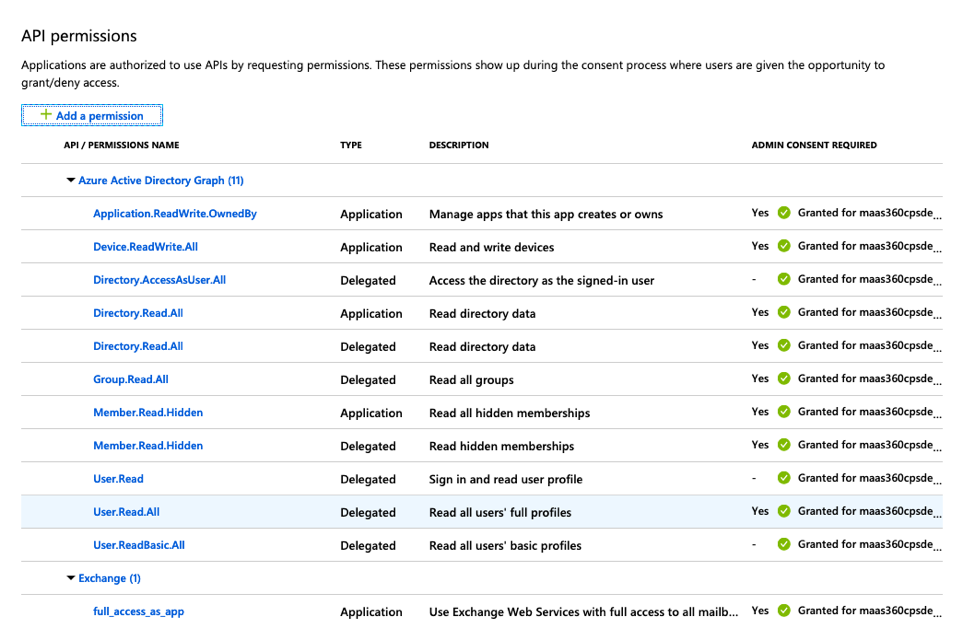
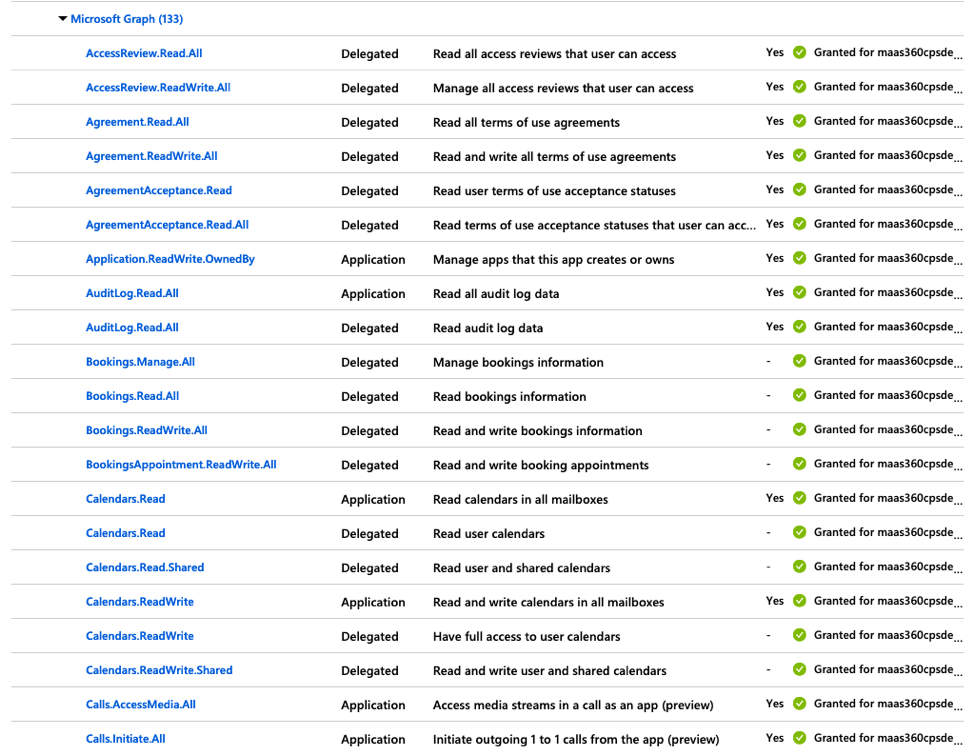
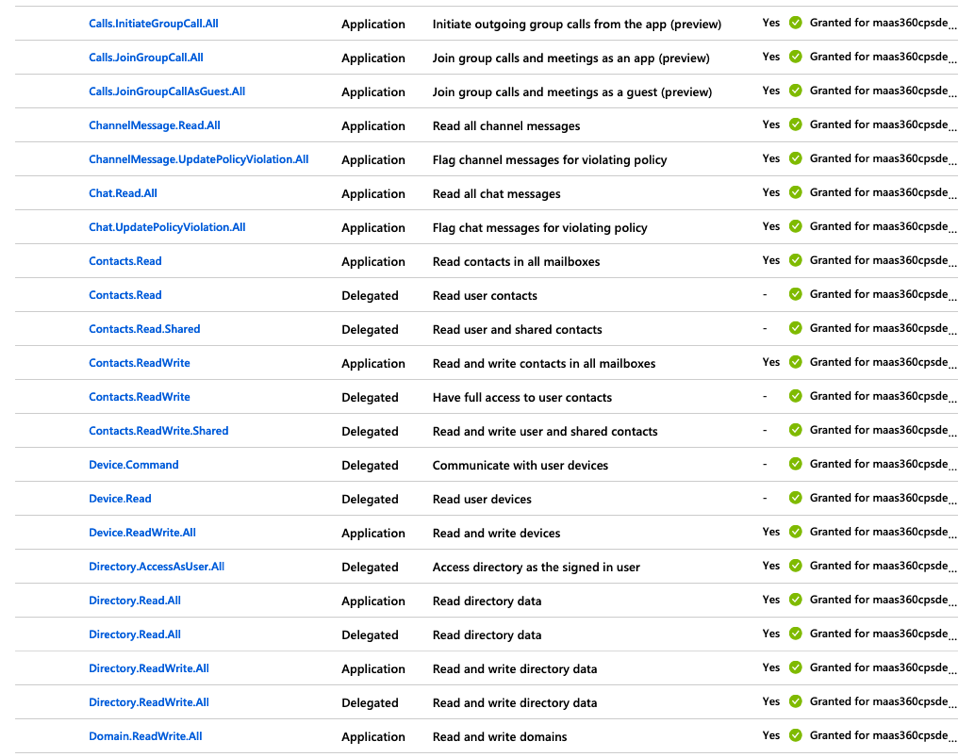
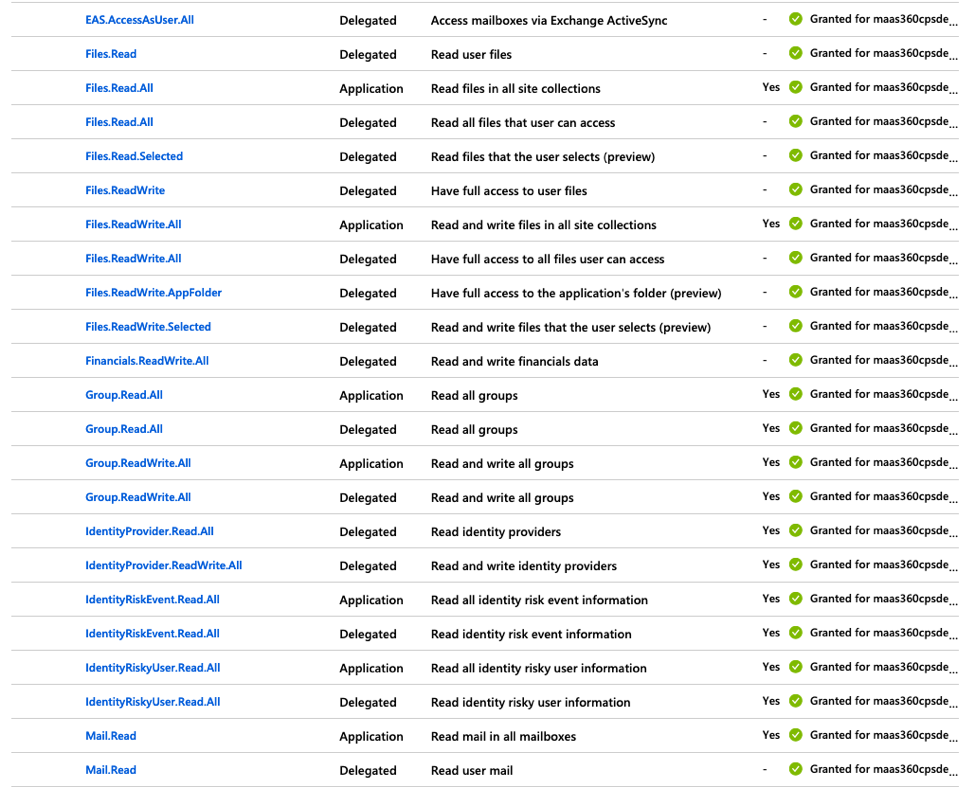
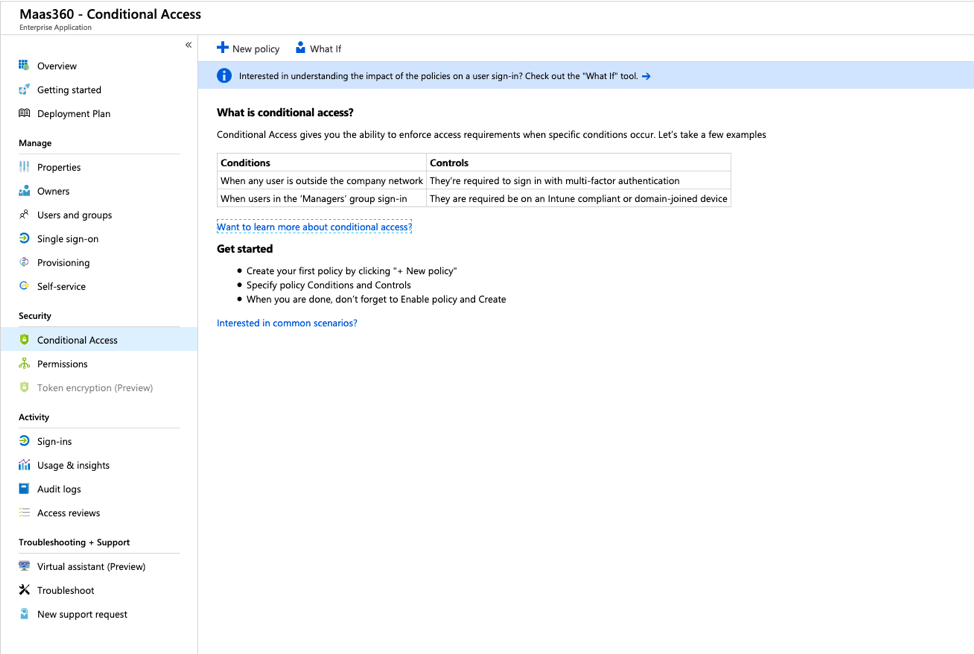
12. Once permissions are granted you will need verify that conditional access policies will not interfere with authentication at the device level. In this instance, the app created in Azure does not have any conditional access policies assigned.
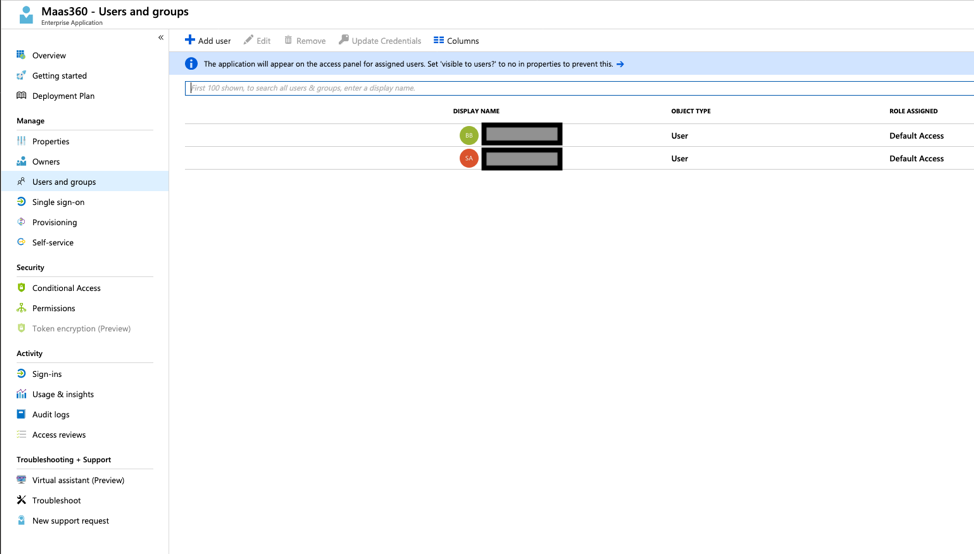
13. The final step in Azure for configuration is verifying that the proper Users and Groups have access to use this Azure app. Go to Enterprise Applications > Your App > Users and Groups > Assign the users or groups you wish to have access to SSO into mail via this app with Secure Mail.
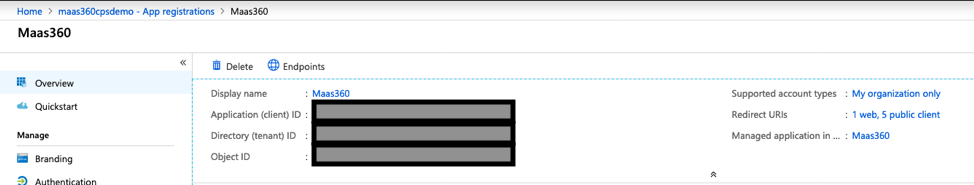
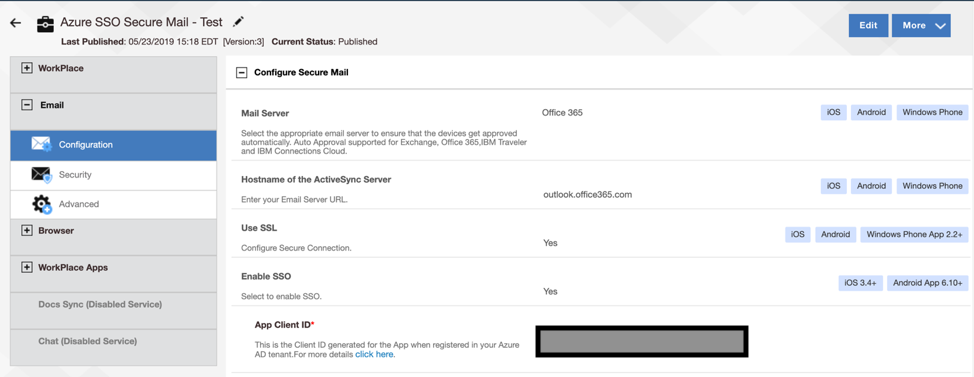
14. Once this configuration has been completed you will need to take the Application ID in Azure and put it in your Workplace Persona policy.
Document Location
Worldwide
[{"Business Unit":{"code":"BU059","label":"IBM Software w\/o TPS"},"Product":{"code":"SSYSXX","label":"IBM MaaS360"},"Component":"","Platform":[{"code":"PF025","label":"Platform Independent"}],"Version":"All Versions","Edition":"","Line of Business":{"code":"LOB24","label":"Security Software"}}]
Was this topic helpful?
Document Information
Modified date:
30 November 2020
UID
ibm10964530