Troubleshooting
Problem
Some applications require a simple self-signed certificate to use for encrypting communication. The steps in this document will help you accomplish that.
Resolving The Problem
Note:
These steps require that you have already created a local certificate authority (CA) and the *SYSTEM certificate store. If you need to create your own local CA certificate and the *SYSTEM certificate store first, refer to the following documents:
o How to create the *SYSTEM store in DCM:
https://www.ibm.com/docs/en/i/7.5?topic=dcm-setting-up-certificates-first-time
o How to create the Local Certificate Authority (CA) store in DCM:
https://www.ibm.com/support/pages/node/6614757
The four basic steps to create your own certificate are as follows:
- Select the option to create a certificate.
- Select Local CA as the option to sign the certificate.
- Complete the certificate details.
- Assign the certificate to the application(s).
Once these four steps are done, you should have your own self-signed certificate assigned to the application(s) you selected. The details of these steps are explained below:
To access the DCM page use your IBM i system name or IP address in the URL:
http://<IBM i name or IP address>:2006/dcm/mainframe/home
or
https://<IBM i name or IP address>:2007/dcm/mainframe/home
- Step 1
Log in to DCM and click Open Certificate Store and select *SYSTEM, enter the *SYSTEM store password and click Open: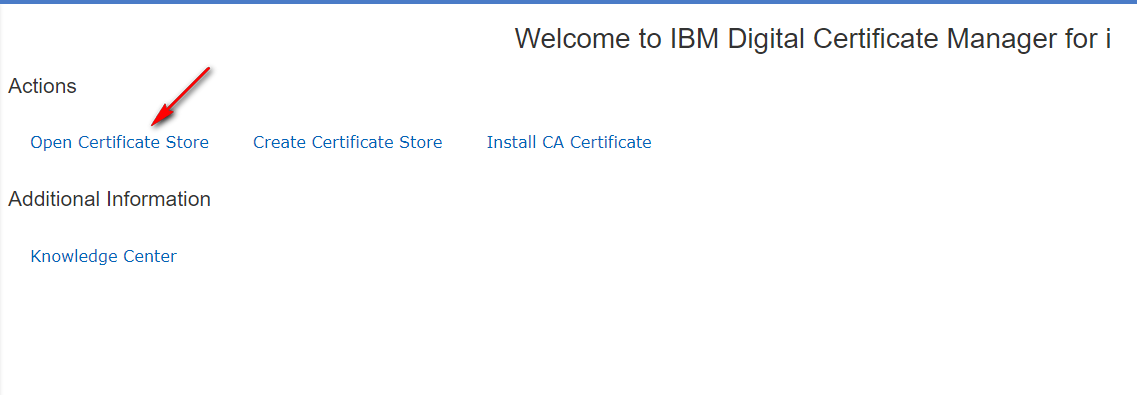

- Step 2
Click Create followed by Local CA: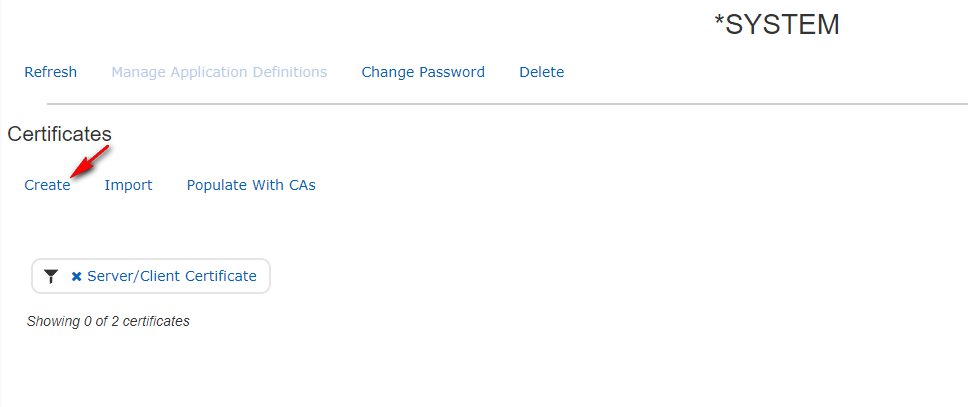
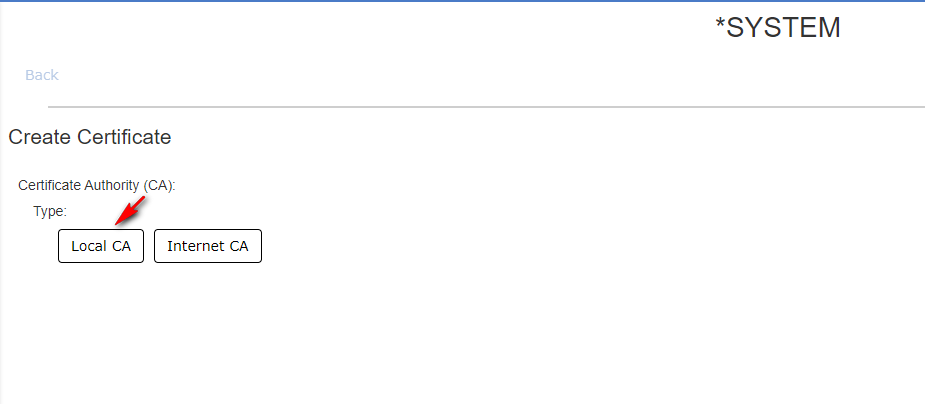
- Step 3
Choose your key size (2048 is the default recommended key size) and complete the required information. Below is a brief description of each required field and a screen capture of what was used in this example. Once these are complete, click Create at the bottom of the page.Certificate Authority (CA): Choose the CA that you would like to sign your certificate.
Key algorithm: Choose either RDA or ECDSA (most common is RSA)
Key Size: The default key size is 2048.
Certificate label: This can be whatever you want, mixed case, numbers, letters, hyphens, etc. The only stipulation is that the name you add here must be unique (meaning no other certificates on this system can have the same certificate label).
Organization name: Your business/organization name.
State or province: Your state/province name. Note that this must be 3 characters or more. Two character state abbreviations will not work.
Country or region: Your country/region. Note that this must be 2 characters only. Three characters will not fit.
Subject Alternative Name: Allows the certificate to be used for all hosts in a domain or alternate IP address, this is not required for all TLS connections however many browsers do use this field.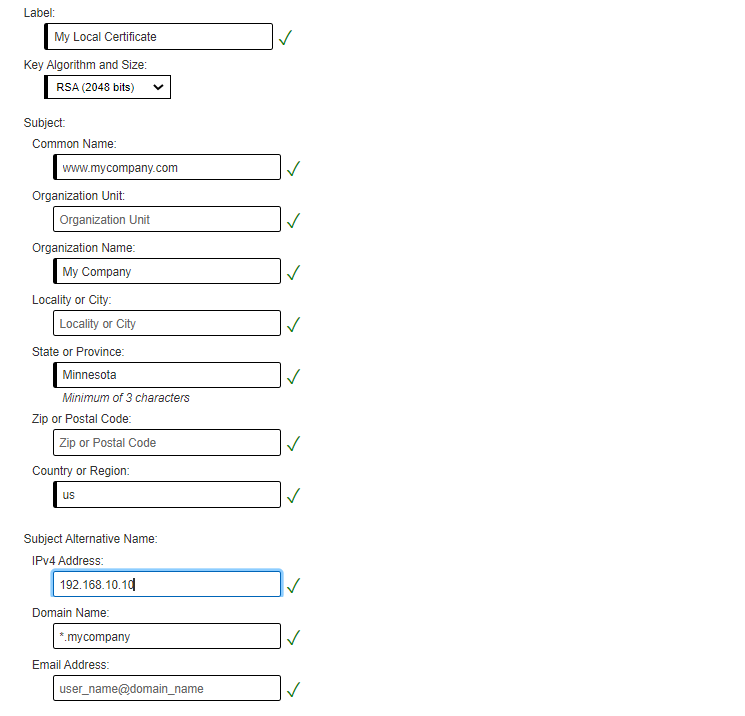
- Step 4
Now you need to select the application (or applications) you want to use this certificate for. Click the plus + sign in the lower right corner of the new certificate then click Assign.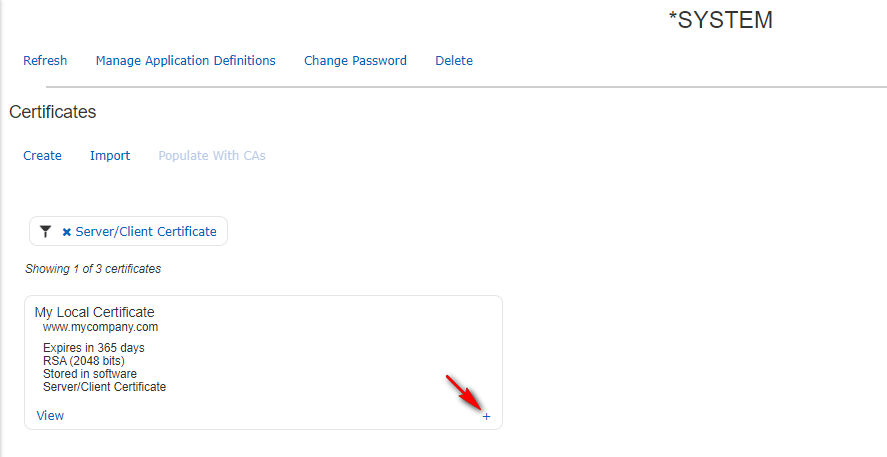
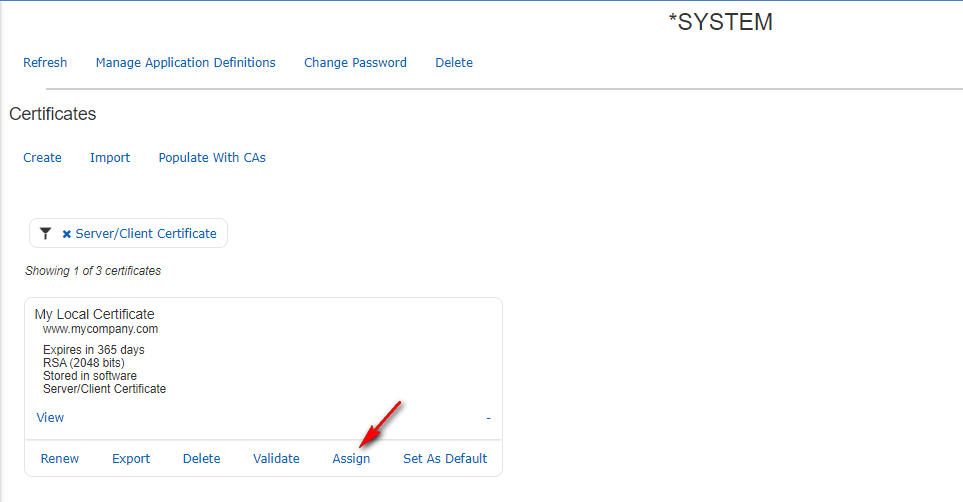
You can check the box for whichever application(s) you want to use the certificate for. If you are wanting to secure Telnet 5250 with ACS select the following Application ID's
- QIBM_OS400_QZBS_SVR_CENTRAL
- QIBM_OS400_QZBS_SVR_DATABASE
- QIBM_OS400_QZBS_SVR_DTAQ
- QIBM_OS400_QZBS_SVR_NETPRT
- QIBM_OS400_QZBS_SVR_RMTCMD
- QIBM_OS400_QZBS_SVR_SIGNON
- QIBM_QTV_TELNET_SERVER
- QIBM_OS400_QZBS_SVR_FILE
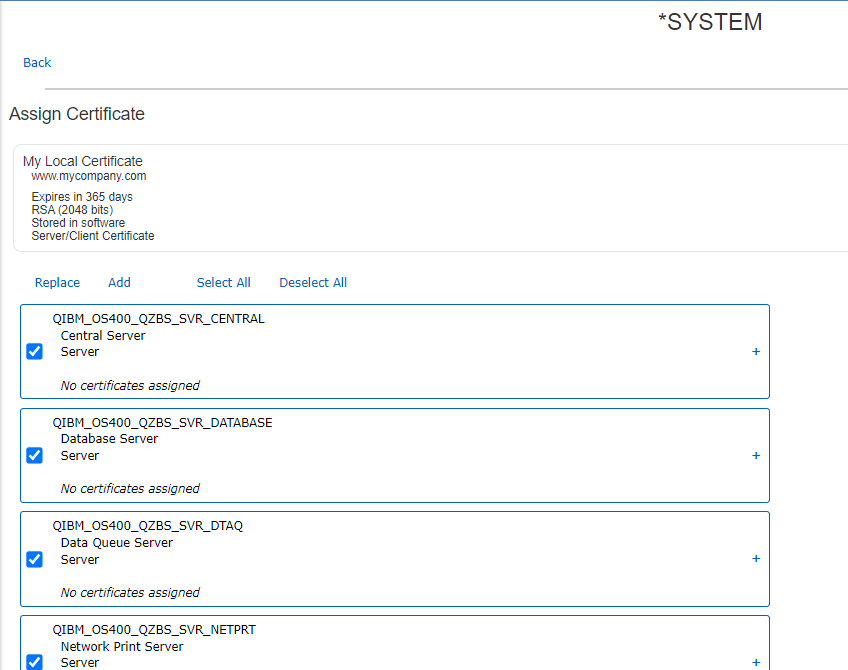
After you have selected your wanted application(s), click Replace at the bottom (Do not select 'Append' unless you are planning to assign an RSA and a ECDSA certificate to the application ID) and your certificate will be assigned.
Note that most server applications require a restart after a certificate assignment has been changed. Telnet, the Host Servers, and FTP have code that allows them to pick up dynamic certificate changes under certain conditions.
Historical Number
677107828
Was this topic helpful?
Document Information
Modified date:
24 August 2022
UID
ibm16615149