White Papers
Abstract
This article provides Remote Authentication Dial-In User Service (RADIUS) client set up and AAA configuration on WebSphere DataPower, which authenticates users with RSA SecurID key fob token codes through the WS-Trust protocol. The article describes how to configure the RADIUS integration in DataPower. Set up for the RSA SecurID and RADIUS servers with credential mapping is not provided in this article. This article assumes that RADIUS and SecurID have already been set up on the backend.
Content
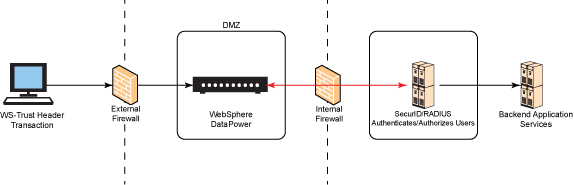
If your organization leverages RADIUS and SecurID authentication for authenticating or authorizing users to consume services externally, outside of your secured enterprise, this article helps you set up a Remote Authentication Dial-In User Service (RADIUS) client and AAA configuration in WebSphere DataPower (hereafter called DataPower). DataPower is positioned as an industry-secured gateway to authenticate users with RSA SecurID key fob token codes through the WS-Trust protocol. This article covers the following: Note: The set up for the RSA SecurID and RADIUS servers with backend credential mapping is not provided in this article. This article assumes that RADIUS and SecurID have has already been set up on the backend. Figure 1 shows the high-level architecture of a WS-Trust client user authentication, which authenticates and authorizes users via RADIUS and SecurID through DataPower. DataPower provides security policy enforcements and transformation for XML and Web services for RADIUS among other security protocols, such as LDAP, Kerberos, Active Directory, and SAML queries. Organizations can choose to use RADIUS and SecurID due to its two-factor authentication security token, utilizing time-synchronous generated token codes only held by the user who is authorized to access exposed services from within the organization. The RSA SecurID hardware-based authenticator contains authentication for a username and a PIN, plus a 60-second, 6-digit generated code. Users need to provide this code to access authorized services from within an organization. At this current time, this article does not provide a RADIUS and SecurID key fob token generator. Therefore, this article assumes that the RADIUS server and SecurID have already been set up for the backend policy enforcement point. If there is a RADIUS and SecurID configuration set up for your environment, you needs cURL installed and configured to execute an end-to-end demonstration test. This section provides the RADIUS client configuration on DataPower. The following RADIUS parameters consist of a short description of the fields found on the RADIUS client configuration on DataPower: Figure 6 shows a sample Juniper Steel-Belted RADIUS server user console. Notice that an IP address is specified on the RADIUS configuration. The RADIUS administrator can choose to input all four Ethernet interfaces. However, if only one Ethernet interface is used, then incoming authentication must be from the enlisted IP address on RADIUS. Due to the specific IP address required by RADIUS, you need to assign static routes on DataPower so that all outbound transactions use the IP address used for RADIUS communication. DataPower dynamically utilizes any of the four Ethernet interfaces that are enabled on the appliance (least weighted connection), and might use one of the three other Ethernet interfaces that are not specified on the RADIUS server. It causes connectivity failure. For example, if IP 192.168.1.52 is given to the RADIUS and SecurID team, then "eth4" (which was assigned IP 192.168.1.52) needs the primary and secondary RADIUS server static route input, so only eth4 communicates to the RADIUS servers. If you do not put a static route in place, then DataPower can choose to use one of the other Ethernet interfaces. This is not allowed to communicate to the RADIUS server, and RADIUS authentication on DataPower fails. Static route assignments to the Ethernet interface being used to communicate to the RADIUS server are set by the following: DataPower provides a testing client to test your RADIUS connection. To test: There are a few things to consider when troubleshooting RADIUS integration for DataPower. There are some preliminary factors that can cause your RADIUS connection to not authenticate your username: After completing the RADIUS client setup, the service can be developed for applications that is authenticating SecurID users. To create a basic level XML firewall with AAA authentication for a RADIUS service: Note: Ensure you select Save Config after you complete this step. Your completed XML firewall with RADIUS AAA authentication looks like Figure 26. The Processing Policy for the AAA Policy looks like Figure 27. After creating the AAA XML firewall, you can conduct an authentication test: Create the In this article, you learned how to configure a RADIUS client on DataPower, test the connectivity for the RADIUS client, and configure a RADIUS AAA firewall gateway. The article also demonstrated a RADIUS authentication attempt by using the SecurID key fob through the AAA firewall. The author (Will Liao) would like to thank Andrew Das for his guidance and support in ensuring the accuracy of the content in this article.Introduction
Requirements
Additional notes
Setting up the RADIUS client
RADIUS connection set up on DataPower




Assigning the static route assignment for the RADIUS connectivity

Ethernet Interface in the search field.



Testing RADIUS
RADIUS in the search field). Click Test RADIUS on the right side of the RADIUS Settings page, as shown in Figure 10.




Troubleshooting RADIUS
Note: You cannot be able to do a Remote Host ping because the firewall opened only allows port 1812 to be opened.Configuring basic XML firewall with RADIUS AAA
XML firewall configuration with RADIUS AAA



0.0.0.0 for the Device Address (which is not advised to be used in production) and choose a port that is opened on the appliance to be used. For the example, we are by using port "1234" as shown in Figure 17.


RADIUS-Demo-AAA-Policy as shown in Figure 19.









Testing the SecurID key fob code


aaa.xml file as shown in Listing 1.
<?xml version="1.0" encoding="UTF-8"?> <soapenv:Envelope xmlns:wsse=http://docs.oasis-open.org/wss/2004/01/ oasis-200401-wss-wssecurity-secext-1.0.xsd xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <wsse:Security> <wsse:UsernameToken> <wsse:Username></wsse:Username> <wsse:Password></wsse:Password> </wsse:UsernameToken> </wsse:Security> </soapenv:Header> <soapenv:Body> <msg>Authentication Passed</msg> </soapenv:Body> </soapenv:Envelope>
curl –data-binary @aaa.xml http://<IP_of_appliance>:1234, a successful authentication returns the full SOAP message as shown in Figure 30.


Conclusion
Acknowledgments
Was this topic helpful?
Document Information
Modified date:
03 July 2023
UID
ibm11109541