Designing security
This section contains guidelines to help application developers and systems managers include security as part of the overall design. It also contains examples of techniques that you can use to accomplish security objectives on your system.
Protecting information is an important part of most applications. Security should be considered, along with other requirements, at the time the application is designed. For example, when deciding how to organize application information into libraries, try to balance security requirements with other considerations, such as application performance and backup and recovery.
Some of the examples in this section contain sample programs. These programs are included for illustrative purposes only. Many of them will not compile or run successfully as is, nor do they include message handling and error recovery.
The Plan and set up system security in the information center is intended for the security administrator. It contains forms, examples, and guidelines for planning security for applications that have already been developed. If you have responsibility for designing an application, you might find it useful to review the forms and examples in the Plan and set up system security topic for details. They can help you view your application from the perspective of a security administrator and understand what information you need to provide.
The Plan and set up system security topic in the information center also uses a set of example applications for a fictional company called the JKL Toy Company. This section discusses design considerations for the same set of example applications. Figure 1 shows the relationships between user groups, applications, and libraries for the JKL Toy Company:
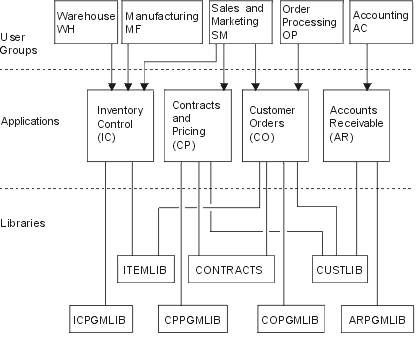
Description of graphic
This graphic shows how five sets of user groups access applications and libraries on the system at JKL Toy Company. The user groups include Warehouse, Manufacturing, Sales and Marketing, Order Processing, and Accounting. These user groups have different accesses to different applications, which are stated in the following list.
- The Warehouse, Manufacturing and Sales and Marketing user groups can all access the Inventory Control applications.
- The Sales and Marketing user group also has access to the Contracts and Pricing application and the Customer Order application.
- The Order Processing user group can also access the Customer Order application.
- The Accounting user group only has access to the Accounts Receivable application.