Prerequisites
These hardware and software components are required for implementing pervasive disk encryption.
Hardware prerequisites
- An IBM® z14 or z13™ with the CPACF feature installed. The use of the CPACF requires the appropriate microcode to be loaded which you can order as no-charge feature code (LIC #3863).
- For redundancy, two IBM Crypto Express5 or Crypto Express6 adapters in CCA coprocessor mode (CEX5C or CEX6C).
- A Trusted Key Entry (TKE) workstation. For non-production environments you can use the utilities from the CCA package instead of the TKE to set master keys.
- SCSI or DASD volumes to be encrypted.
Software Prerequisites
- Any Linux distribution that includes support for the pkey and paes_s390 kernel modules. Linux kernel 4.12 or later includes the required kernel modules.
- The cryptsetup utility used to configure an encrypted volume.
- The zkey utility from the s390-tools package (version 1.39 or later). Use this utility to generate and manage secure keys.
- The CCA package to connect the TKE workstation to the cryptographic coprocessors.
Assumptions
- A Linux instance is installed as a z/VM® guest or in an LPAR.
- Two cryptographic coprocessor domains are configured to the
LPAR or as dedicated adapters to the z/VM guest.
- The two domains have the same domain ID and are loaded on two distinct cryptographic coprocessors.
- The same AES master key is set for the domains of both cryptographic coprocessors.
- The volumes to be encrypted are configured to be persistently available to the Linux instance.
Figure 1. System configuration for pervasive disk encryption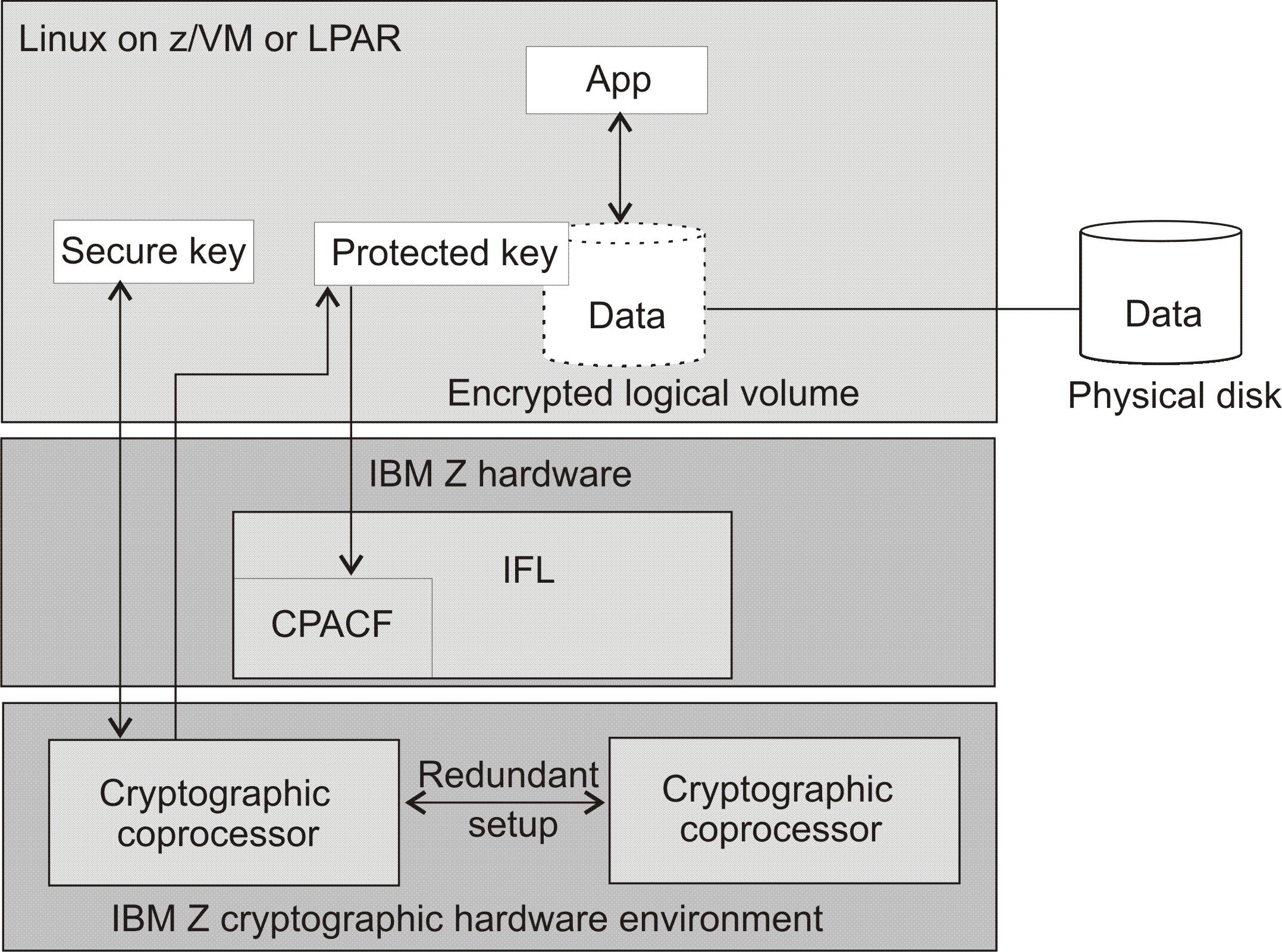

The main characteristics of pervasive disk encryption are:
- An enhanced security achieved by the secure key operations and management in the tamper-proof cryptographic coprocessors.
- A performance advantage of protected key cryptography compared to secure key cryptography. Therefore, the secure key is converted into a protected key. Protected key cryptography is running at processor speed in the CPACF.