Sample system for data volume encryption
A sample system configuration is used to illustrate most of the tasks documented in this publication.
Hardware components
- Two CEX6C cryptographic coprocessors
- Up to 10 physical SCSI volumes with a capacity of 20 GB each
Alias names disk1, disk2, disk3, ... are assigned to these volumes
- A Trusted Key Entry workstation (TKE) to maintain the cryptographic coprocessors
- A Central Processor Assist for Cryptographic Functions (CPACF) is configured and enabled
- A CPC containing CPs (general purpose processores) or IFLs
Software components
The sample system is running with the following software:
- A Linux® kernel with:
- all required modules loaded: paes_s390 and pkey
- Logical Volume Manager
- device mapper
- dm-crypt
- cryptographic device driver (zcrypt)
- s390-tools: zkey and zkey-cryptsetup
- cryptsetup version 2.0.3
Configuration
The used volumes are configured as SCSI volumes in a multipath setup, using two FCP adapters. For more information about SCSI devices, read How to use FC-attached SCSI devices with Linux on z Systems.
It is assumed that the multipath SCSI volume configuration is transparent to users of the infrastructure for protected volume encryption.
SCSI multipath volumes appear under /dev/mapper/. For ease of use, readable alias names like disk1, disk2, and so on are applied.
The sample system configuration exploits the Logical Volume Manager (LVM). Alternatively, you can set up the infrastructure for protected volume encryption without LVM. In this case, you need to adapt the described procedures accordingly.
An identical AES master key (AES MK) is set on the first and second cryptographic coprocessor (CEX6C I and CEX6C II in Figure 1) in the same domain on both.
Figure 1 shows the configuration of the sample system after you finished the tasks described in Creating a volume for pervasive encryption.
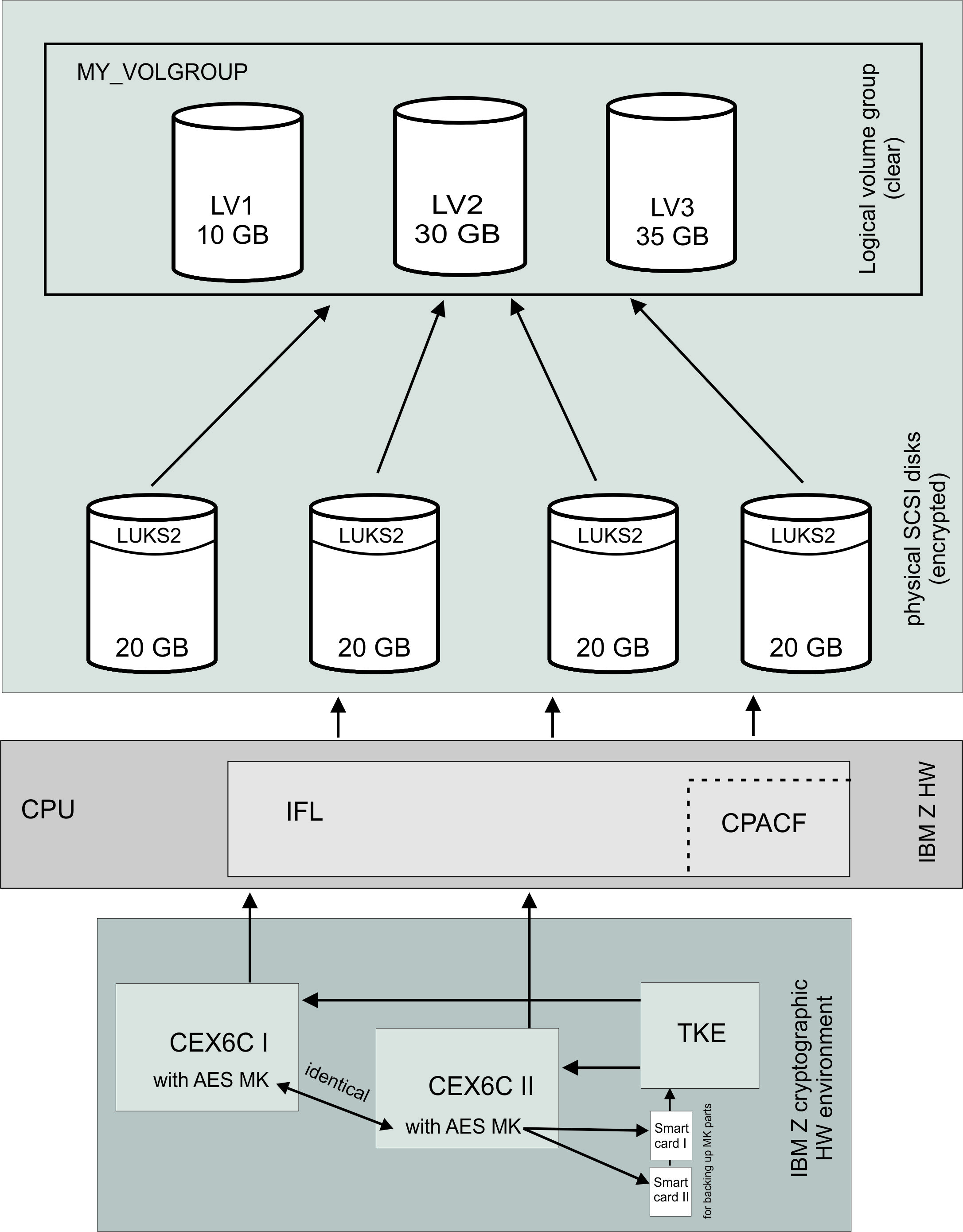
In the logical volume group MY_VOLGROUP, intentionally only 35 GB are allocated instead of the maximum of 40 GB to logical volume LV3. The LUKS2 headers occupy some space that is not available as volume capacity. Also, you can keep some reserve space for defining a small new logical volume LV4 for future use, or to enlarge an existing logical volume (for example, LV1).