Protected and secure volume encryption
One of the most valuable assets of a modern enterprise is data that is typically stored on storage systems. This data is often referred to as data at-rest. The method of choice to protect such data in storage systems is end-to-end data encryption. Data is encrypted by the Linux® instance applying controlled protected and secure keys. Therefore, the data is protected whenever it leaves the system.
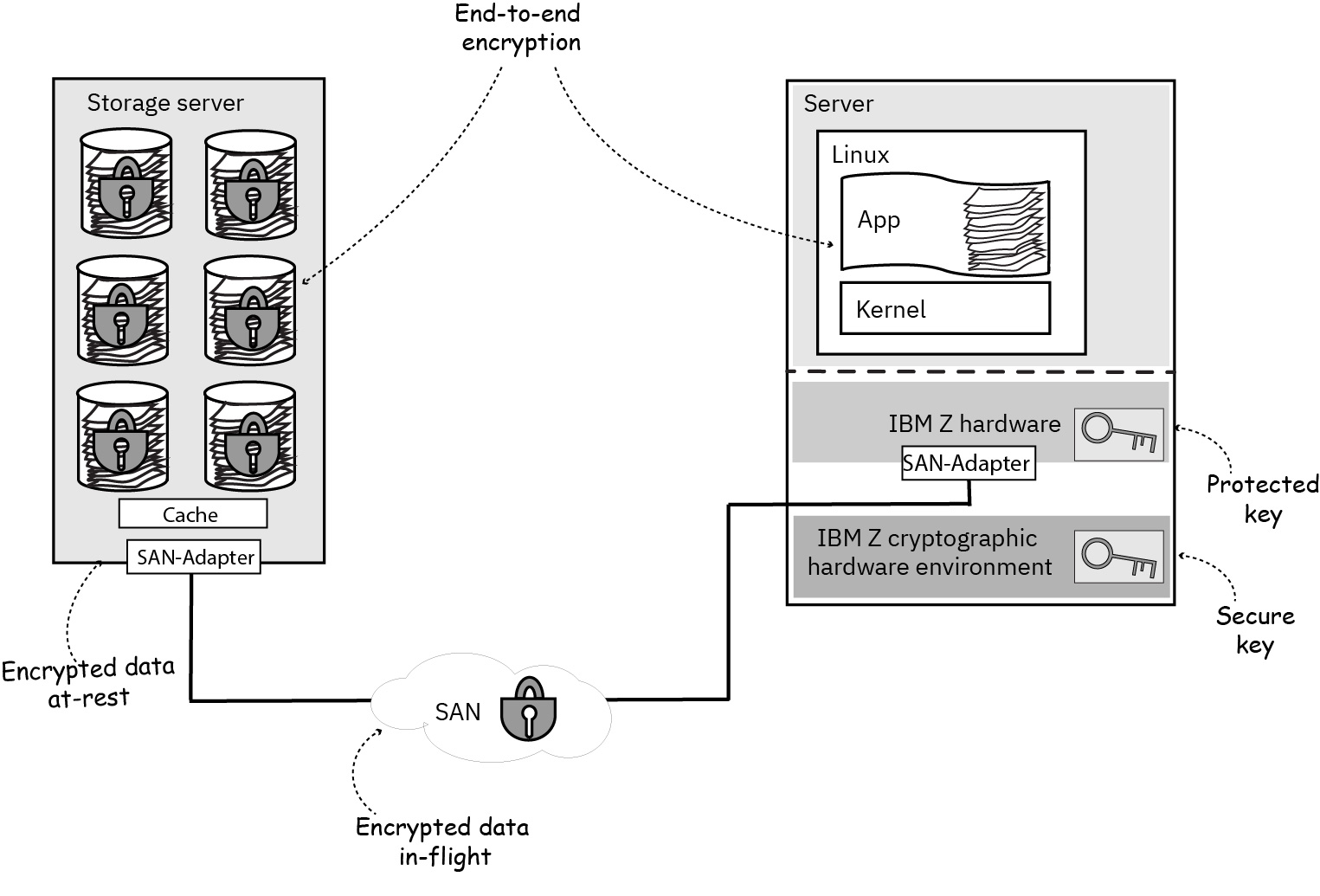
Figure 1 shows that end-to-end encryption protects the data during the complete journey from the operating system on the IBM Z® mainframe through the cryptographic hardware, the SAN cable and the SAN adapters into the storage server cache, and finally on the storage devices.
In Linux, the most popular method for end-to-end data at-rest encryption is full volume encryption using the dm-crypt kernel component. dm-crypt reads encrypted sectors from a block device (disk, partition, or logical volume), decrypts the data in the sector, and writes it to the reading component (for example, into the page cache).
In the opposite direction, dm-crypt reads data from a buffer of the writing component (for example from the page cache), encrypts the data, and writes it into a sector of the block device. The decryption and encryption happens transparently as long as the application uses file I/O to a file system mounted on a dm-crypt device.
The challenge is to manage the cryptographic keys needed to open an encrypted volume:
- How can these keys be stored securely?
- How can these keys be protected from being discovered while they are in use?
- How can these keys be protected from being stolen by an intruder?
- How can these keys be protected from discovery by a service engineer that analyzes a system dump?
To manage the challenge of storing cryptographic keys and associating these keys with the volume they encrypt, the Linux cryptsetup utility applies the Linux Unified Key Setup (LUKS) volume format. This format provides protection by passphrases and stores passphrase-protected volume keys in the header of the volume. The cryptsetup utility uses LUKS to store information (for example about the used cipher and the volume key) for setting up and configuring dm-crypt. On opening a LUKS formatted volume, a passphrase is required. This might be a valid procedure for personnel computers and laptops, but is not a viable solution to manage a server farm with hundreds of volumes.
The purpose of protected volume encryption is to provide end-to-end encryption of data at-rest in a way that the keys needed to decrypt or encrypt your data are inherently secure. That means that the keys must be represented by objects that cannot be used as keys outside of your system. These objects are secure keys and protected keys. How these types of keys cooperate in the infrastructure for protected volume encryption is described in Infrastructure concepts.