Securing protocol data
The data cannot be secured only by authenticating and authorizing the users to access the data. You also need to ensure that the communication channel that is used to raise authentication requests and data transfer is secured. The security features associated with the protocols that you use to store and access data also help to provide data in transit security for the protocol data.
- Establishing secured connection between the IBM Spectrum Scale™ system and
the authentication server.
When the client raises an authentication request to access the data, the IBM Spectrum Scale system interacts with the external authentication servers like Active Directory or LDAP based on the authentication configuration. You can configure the security services like TLS and Kerberos with the external authentication server to secure the communication channel between the IBM Spectrum Scale system and the external authentication server.
- Securing the data transfer.
The actual data access wherein the data transfer is made secured with the security features that are available with the protocol that you use to access the data.
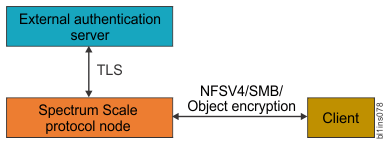
Secured connection between the IBM Spectrum Scale system and the authentication server
- Microsoft Active Directory (AD)
- Lightweight Directory Access Protocol (LDAP)
- Keystone
| Authentication server | Supported protocols | Security features |
|---|---|---|
| Active Directory | File and Object | Kerberos for file and TLS for object. |
| LDAP | File and Object | Both TLS and Kerberos for file and only TLS for object. |
| Keystone | Object | SSL certificate to enable HTTPS connection |
Secured data transfer
The secured data transfer over the network is based on the security features available with the protocols that are used to access the data.
Secured SMB data transfer
- Secured dialect negotiation
- Improved signing
- Secured transmission
- Automatic
- Mandatory
- Disabled
Secured NFS data transfer
- Enabling squashing
Any file requests that are made by the root user on the client system is considered as a potential threat. By default, root user requests are treated as if it is made by the user on the server. If you disable squashing, the root user on the client gets the same level of access to files on the system as the root user on the server. You can disable squashing if, for example, you want to run an administrative task on the client system that has the exported directories that are stored on it.
- Using KerberosKerberos is a network authentication protocol that ensures secure communication over a network. You can use Kerberos instead of local UNIX UIDs and GIDs to authenticate users. Kerberos can operate in the following modes to provide improved security:
- Kerberos v5: Authentication only
- Kerberos v5 with integrity: Authentication and data integrity
- Kerberos v5 with privacy: Authentication and encryption of data traffic between the client and the server. Most secure, but it might cause some performance issues because of the heavy processing required for encryption.
- Enabling port security
You can enable or disable the port security in all communications between the client and the server. When port security is enabled, the system does not allow access to the requests that originate from ports where the port number is greater than the hardcoded threshold value of 1024.
Secured object data access
The IBM Spectrum Scale system provides access to the Object Storage with the help of OpenStack Keystone Identity Service. The Keystone server that is provided by IBM Spectrum Scale is recommended to be used only for IBM Spectrum Scale Object workload.
For secure communication between the clients and the IBM Spectrum Scale Object, the system administrator needs to configure HAProxy for SSL termination, traffic encryption, and load balancing of the requests to IBM Spectrum Scale Object. The HAProxy needs to be set up on an external system that is not a part of the IBM Spectrum Scale cluster. For more information on how to configure HAProxy, see the documentation of the corresponding Linux distribution that you selected.