ECI calls secured with JSON Web Token (JWT)
CICS® Transaction Gateway can perform authentication and authorization checks at different points during the processing of requests.
CICS Transaction Gateway can validate a Jason Web Token (JWT) and then pass the user security identity information (a distributed identity) across the network to CICS Transaction Server for IBM® z/OS®. The security identity of the user is preserved for use during CICS authorization and for subsequent accountability and trace purposes.
With JWT, CICS Transaction Gateway provides a way of authorizing requests by validating the JWT and then associating the JWT with security information in CICS Transaction Server for IBM z/OS.
CICS Transaction Gateway delivers new APIs to support JWT for authentication for applications written in Java™, JCA, .NET, and .NET Core languages. JWT is supported with IPIC protocol with identity propagation enabled.
Benefits of using JSON Web Token (JWT)
JWT provides the following benefits:
- JWT provide end to end security when Java, JCA, .NET, and .NET Core clients applications are connected to CICS Transaction Server through CICS Transaction Gateway.
- A unified mechanism for authentication with self-contained tokens.
- “Single-sign-on” authentication of users in different set of registries before they are authorized in CICS Transaction Server for IBM z/OS.
Network topology for using JSON Web Token (JWT)
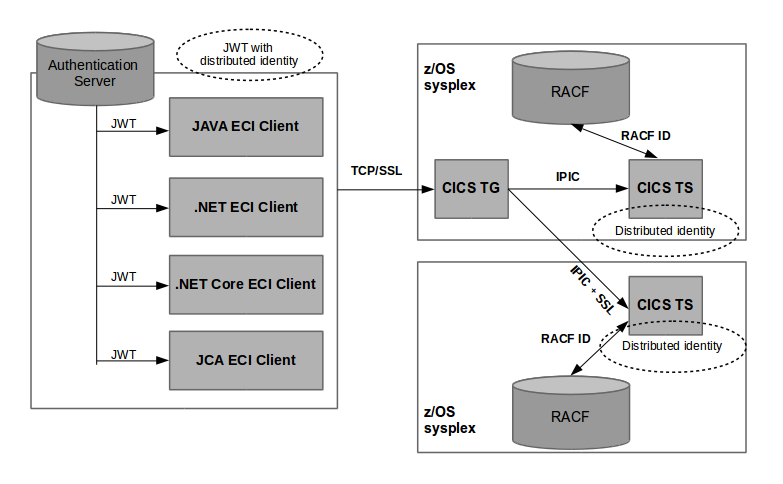
The JWT is self-contained authorization token. The token will have distributed identity as one of the claims. Upon successful validation of the token, the security information is passed as-is to CICS as a distributed identity. The distributed identity is mapped to a RACF® user ID for CICS authorization .
A JWT takes precedence over user IDs that is asserted directly using other mechanisms.