Linux and UNIX systems: Kerberos-authenticated database traffic
Kerberos is a network authentication protocol that eliminates the transmission of unencrypted passwords across the network. Learn how it functions in Guardium .
It works in a mutual authentication mode, verifying both the identity of the user that is requesting authentication as well as the server providing the requested authentication. The Kerberos authentication mechanism issues tickets for accessing network services. These tickets contain encrypted data, including an encrypted password, that confirms the user's identity to the requested service.
For auditing and alerting, it’s important to know which database user performed an action. When login is done with a Kerberos ticket, determining the database user is not always straightforward.
Guardium S-TAP only sees network traffic and passes it on to the sniffer on the Guardium appliance. When a Kerberos ticket is used for login, S-TAP passes that Kerberos ticket along to the sniffer. For some database server types, the sniffer can determine the database user from the Kerberos login traffic and no additional information is required. For other database server types, the sniffer needs some assistance. That function is performed by the S-TAP Kerberos plugin.
The S-TAP Kerberos plugin is not enabled by default; it requires additional configuration.
If you use Kerberos at all, configure the plugin. There is no performance implication or other downside to configuring the plugin, just in case you need it.
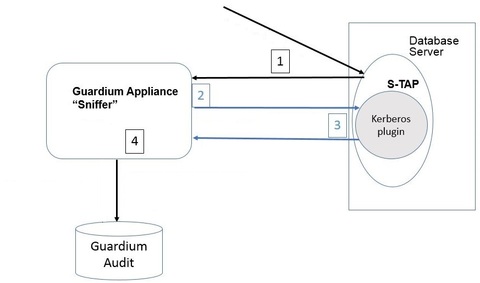
The data flow between the database, the Guardium sniffer and the Guardium audit data is:
- S-TAP captures the Kerberized database login packet (along with other activity) and sends it to the Guardium appliance.
- If the sniffer can determine the user name from the Kerberos ticket, it parses it.
- If the sniffer cannot determine the user name from the Kerberos ticket, it sends the Kerberos ticket, along with a request for the database user, to the S-TAP. S-TAP checks to see if there is a Kerberos plugin configured. If there is a Kerberos plugin configured, S-TAP gives the ticket to the plugin and the plugin attempts to figure out DB_USER from the ticket. It returns the database user name to S-TAP. (If not, then the database user name is not supplied and you do not see database user names in your reports.)
- The sniffer can now populate the database user for that ticket, and correlate it with the rest of the database activity for that user in the Audit.