 z/OS MVS Programming: Extended Addressability Guide
z/OS MVS Programming: Extended Addressability Guide
 z/OS MVS Programming: Extended Addressability Guide
z/OS MVS Programming: Extended Addressability Guide
|
Previous topic |
Next topic |
Contents |
Contact z/OS |
Library |
PDF
How problem state programs with PSW key 8 through F use a hiperspace z/OS MVS Programming: Extended Addressability Guide SA23-1394-00 |
|
|
A problem state program with PSW key 8 - F can use the non-shared hiperspace it created. Figure 1 illustrates this use. Figure 1. A problem state program using a non-shared standard
hiperspace
 By obtaining an ALET, a problem state program with PSW key 8 - F obtains the benefit of the move-page facility and also shares a hiperspace with a subtask. For example, suppose a problem state program obtains an ALET, attaches a subtask using the ALCOPY parameter on the ATTACH macro, and passes the ALET and STOKEN to the subtask. These actions allow the task and its subtask to share the same non-shared hiperspace. Two problem state programs can share a SCOPE=SINGLE data space in the same way. Turn to How problem state programs with PSW key 8 through F use a hiperspace for an such an example. Can an authorized program set up an environment in which an unauthorized
program can share hiperspaces? An authorized program (supervisor
state with PSW key 0 - 7) can set up addressability for an unauthorized
program (problem state with PSW key 8 - F) and increase the use of
hiperspaces by those unauthorized programs. This section contains
two examples of this increased capability.
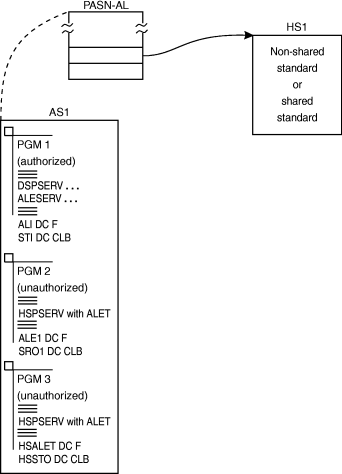
Example 1 shows how an entry on the PASN-AL allows all programs in the address space, including unauthorized programs, to use either non-shared or shared standard hiperspaces. An authorized program obtains the hiperspace, places an entry on the PASN-AL, and obtains the ALET. The program then passes the ALET and STOKEN to other programs in the address space. Even programs that space-switch into the address space can use the hiperspace, providing they receive the ALET and STOKEN. Figure 2 illustrates this case. Figure 2. Example 1: An unauthorized program using a standard
hiperspace
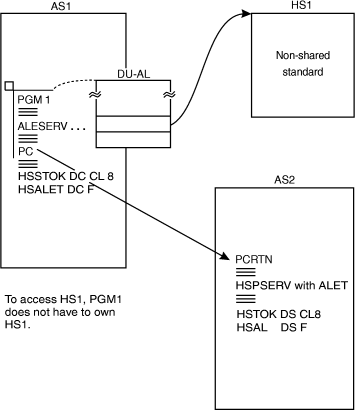
 Example 2 shows how an authorized program can set up a cross memory environment that allows an unauthorized program to space-switch and still have access to a non-shared hiperspace. Having created the non-shared standard hiperspace HS1, PGM1 can obtain an ALET on the DU-AL, space-switch, and use the ALET and STOKEN to access HS1. Figure 3 illustrates this use of a non-shared hiperspace. Figure 3. Example 2: An unauthorized program using a standard
hiperspace


|
 Copyright IBM Corporation 1990, 2014 Copyright IBM Corporation 1990, 2014 |