Identity propagation and distributed security
Identity propagation provides a mechanism to allow a user identity from an external security realm to be preserved, regardless of where the identity information was created, strengthening accountability across distributed environments.
In an external computing environment, for example, WebSphere® Application Server, the identity of a user is authenticated using a user identification that applies to that environment. Applications like WebSphere Application Server often use a separate, shared external security manager user ID when communicating with a CICS® system. The original identity of the user is not passed to CICS and therefore cannot be passed onto the external security manager, making it difficult to determine the initial user identity and impacting the audit trail of the request.
In the identity propagation topics, RACF® represents the external security manager. If you are not using RACF with CICS, consult your system administrator to configure the settings for your external security manager.
The term distributed identity represents user identity information, for example, an X.500 distinguished name and associated LDAP realm, that originates from a remote system. The distributed identity is created in one system and is passed to one or more other systems over a network. A distributed identity originates outside of CICS only; CICS is never the source of a distributed identity, but is capable of propagating the distributed identity onwards.
The following does not apply to use of identity propagation CICS Liberty. For information on identity propagation mapping in Liberty, see Configuring security for a Liberty JVM server by using distributed identity mapping.
When a distributed identity enters the sysplex over MRO and IPIC connections, it is automatically propagated in the sysplex, regardless of connection settings. CICS security handles the distributed identity as additional information relating to the user ID, and a distributed identity cannot exist without a user ID.
Outside the sysplex, the distributed identity can be propagated on, depending on support. Receipt of a distributed identity by another party depends on whether the party is participating in identity propagation. See Support and requirements for identity propagation.
Identity propagation allows the distributed identity to be preserved, regardless of where the identity information was created, for use during authorization and for auditing purposes. The distributed identity is part of the identity context that is carried with a request from the external client application to the server, and it is incorporated in the access control of the server as part of the authorization process; for example, CICS Transaction Gateway on behalf of WebSphere Application Server.
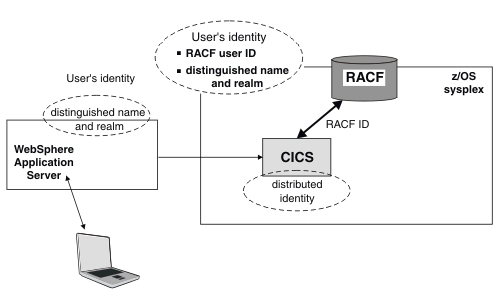
The diagram shows how the X.500 distinguished name and associated LDAP realm which identify the user externally are passed with the request from WebSphere Application Server to a CICS system. The distinguished name and realm, which are known in CICS as a distributed identity when they are transmitted across a network, are propagated into the z/OS® security context and are associated with the RACF user ID. With the z/OS RACF command, RACMAP, you can use mapping filters to correlate the distinguished name and realm to a RACF user ID, preserve the distributed credential information and fulfill governance and auditing requirements. RACF provides information to CICS about the distinguished name and realm, allowing retrieval in CICS of the identity of the initial user.
Sample network topologies for using identity propagation expands on this diagram and shows how different network and product combinations provide support for distributed identities.