Enabling CipherSpecs
Enable a CipherSpec by using the SSLCIPH parameter in either the DEFINE CHANNEL MQSC command or the ALTER CHANNEL MQSC command.
IBM Crypto for Ccryptographic module. The certificate for this module has been moved to the Historical status. Customers should view the IBM Crypto for C certificate and be aware of any advice provided by NIST. A replacement FIPS 140-3 module is currently in progress and its status can be viewed by searching for it in the NIST CMVP modules in process list.
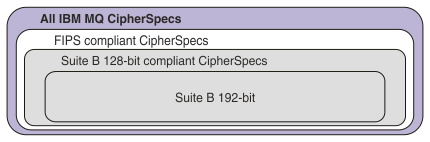
Some of the CipherSpecs that you can use with IBM MQ are FIPS compliant. Some of the FIPS compliant CipherSpecs are also Suite B compliant although others, such as TLS_RSA_WITH_AES_256_CBC_SHA, are not.
All Suite B compliant CipherSpecs are also FIPS compliant. All Suite B compliant CipherSpecs fall
into two groups: 128 bit (for example, ECDHE_ECDSA_AES_128_GCM_SHA256) and 192 bit
(for example, ECDHE_ECDSA_AES_256_GCM_SHA384),
The following diagram illustrates the relationship between these subsets:
From IBM MQ 8.0.0 Fix Pack 3 the number of supported CipherSpecs has been reduced.
![[V9.1.1 Nov 2018]](ng911.gif) For information about configuring the default CipherSpecs, see Default CipherSpec values enabled in IBM MQ. You can also provide an alternative set of CipherSpecs that are enabled
for use with MQ channels. See Providing a custom list of enabled CipherSpecs on Multiplatforms.
For information about configuring the default CipherSpecs, see Default CipherSpec values enabled in IBM MQ. You can also provide an alternative set of CipherSpecs that are enabled
for use with MQ channels. See Providing a custom list of enabled CipherSpecs on Multiplatforms.
For information about enabling the deprecated CipherSpecs, see Enabling deprecated CipherSpecs on Multiplatforms or Enabling deprecated CipherSpecs on z/OS. For a list of CipherSpecs that you can re-enable to use with IBM MQ, see Deprecated CipherSpecs.
![[UNIX, Linux, Windows]](ngulw.gif)
![[V9.1.4 Dec 2019]](ng914.gif) From IBM MQ 9.1.4,
IBM MQ supports the TLS 1.3 security protocol on
UNIX, Linux, and Windows. For information about using these CipherSpecs,
see Using TLS 1.3 in IBM MQ and IBM MQ MQI client and TLS 1.3.
From IBM MQ 9.1.4,
IBM MQ supports the TLS 1.3 security protocol on
UNIX, Linux, and Windows. For information about using these CipherSpecs,
see Using TLS 1.3 in IBM MQ and IBM MQ MQI client and TLS 1.3.
CipherSpecs that you can use with IBM MQ TLS support
Cipher specifications that you can use with the IBM MQ queue manager automatically are listed in the following table. When you request a personal certificate, you specify a key size for the public and private key pair. The key size that is used during the TLS handshake is the size stored in the certificate unless it is determined by the CipherSpec, as noted in the table.
| Platform support 1 | CipherSpec name | Hex code | MAC algorithm | Data integrity | Encryption algorithm (encryption bits) | FIPS 2 | Suite B |
|---|---|---|---|---|---|---|---|
![[V9.1.4 Dec 2019]](../common/../com.ibm.mq.sec.doc/ng914.gif) Alias CipherSpecs Alias CipherSpecs |
|||||||
|
All |
ANY_TLS13_OR_HIGHER
3
4
5 |
N/A | Negotiated | Negotiated | Negotiated | Negotiated | Negotiated |
|
All |
ANY_TLS134
5
6
|
N/A | TLS 1.3 | Negotiated | Negotiated | Negotiated | Negotiated |
|
All |
ANY_TLS12_OR_HIGHER4
5
7
|
N/A | Negotiated | Negotiated | Negotiated | Negotiated | Negotiated |
|
All |
ANY_TLS12
8 |
N/A | TLS 1.2 | Negotiated | Negotiated | Negotiated | Negotiated |
|
All |
ANY
9
|
N/A | Negotiated | Negotiated | Negotiated | Negotiated | Negotiated |
![[V9.1.4 Dec 2019]](../common/../com.ibm.mq.sec.doc/ng914.gif) CipherSpecs for TLS 1.3 CipherSpecs for TLS 1.3 |
|||||||
|
All |
TLS_AES_128_GCM_SHA256
4 |
1301 | TLS 1.3 | GCM | AES-128 with GCM (128) | Yes | No |
|
All |
TLS_AES_256_GCM_SHA3844
|
1302 | TLS 1.3 | GCM | AES-256 with GCM (256) | Yes | No |
|
All |
TLS_CHACHA20_POLY1305_SHA256 4 |
1303 | TLS 1.3 | POLY1305 | CHACHA20 (256) | No | No |
|
|
TLS_AES_128_CCM_SHA256 |
1304 | TLS 1.3 | CBC-MAC | AES-128 with CTR (128) | Yes | No |
|
|
TLS_AES_128_CCM_8_SHA256
11
|
1305 | TLS 1.3 | CBC-MAC | AES-128 with CTR (128) | Yes | No |
| CipherSpecs for TLS 1.2 | |||||||
| All | TLS_RSA_WITH_AES_128_CBC_SHA25610
|
003C | TLS 1.2 | SHA-256 | AES (128) | Yes | No |
| All | TLS_RSA_WITH_AES_256_CBC_SHA256
10
12
|
003D | TLS 1.2 | SHA-256 | AES (256) | Yes | No |
| All | TLS_RSA_WITH_AES_128_GCM_SHA256
10
13
|
009C | TLS 1.2 | SHA-256 and AEAD GCM | AES (128) | Yes | No |
| All | TLS_RSA_WITH_AES_256_GCM_SHA384
10
12
13
|
009D | TLS 1.2 | SHA-384 and AEAD GCM | AES (256) | Yes | No |
| All | ECDHE_ECDSA_AES_128_CBC_SHA256
10
|
C023 | TLS 1.2 | SHA-256 | AES (128) | Yes | No |
| All | ECDHE_ECDSA_AES_256_CBC_SHA384
10
12 |
C024 | TLS 1.2 | SHA-384 | AES (256) | Yes | No |
| All | ECDHE_RSA_AES_128_CBC_SHA256
10
|
C027 | TLS 1.2 | SHA-256 | AES (128) | Yes | No |
| All | ECDHE_RSA_AES_256_CBC_SHA384
10
12 |
C028 | TLS 1.2 | SHA-384 | AES (256) | Yes | No |
|
|
ECDHE_ECDSA_AES_128_GCM_SHA256
12
13
|
C02B | TLS 1.2 | SHA-256 and AEAD GCM | AES (SHA384) | Yes | 128 bit |
|
|
ECDHE_ECDSA_AES_256_GCM_SHA384
12
13
|
C02C | TLS 1.2 | SHA-384 and AEAD GCM | AES (SHA384) | Yes | 192 bit |
| All | ECDHE_RSA_AES_128_GCM_SHA256
13
|
C02F | TLS 1.2 | SHA-256 and AEAD GCM | AES (128) | Yes | No |
| All | ECDHE_RSA_AES_256_GCM_SHA384
12
13
|
C030 | TLS 1.2 | AEAD AES-128 GCM | AES (SHA384) | Yes | No |
|
Notes:
|
|||||||
![[UNIX, Linux, Windows]](ngulw.gif)
![[V9.1.4 Dec 2019]](ng914.gif)
Using TLS 1.3 in IBM MQ
SSL:
AllowTLSV13=TRUE If the queue manager was created using a version of IBM MQ prior to IBM MQ 9.1.4, but is later started using IBM MQ 9.1.4 or higher, it will not have the AllowTLSV13 property set. If you wish to enable TLS 1.3, you must edit the qm.ini file and add in the property as shown in the example (including the “SSL:” stanza if it does not yet exist).
- Uses the SSL 3.0 protocol.
- Uses RC4 or RC2 as the Encryption algorithm.
- Has a encryption key size (bit) equal to or less than 112.
SSL:
AllowTLSV13=FALSE![[UNIX, Linux, Windows]](ngulw.gif)
![[V9.1.4 Dec 2019]](ng914.gif)
IBM MQ MQI client and TLS 1.3
- If any weak CipherSpecs are enabled, AllowTLSV13 is set to FALSE and no TLS 1.3 CipherSpecs can be used.
- Otherwise, AllowTLSV13 is set to TRUE and the new TLS 1.3 CipherSpecs and alias CipherSpecs may be used.
![[UNIX, Linux, Windows, IBM i]](ngmulti.gif)
![[V9.1.1 Nov 2018]](ng911.gif)
Default CipherSpec values enabled in IBM MQ
In default configuration, IBM MQ provides support for the TLS 1.2 protocol and various cryptographic algorithms using CipherSpecs. For compatibility purposes, IBM MQ can also be configured to use SSL 3.0 and TLS 1.0 protocols and a number of cryptographic algorithms that are known to be weak or susceptible to security vulnerabilities. The list of CipherSpecs that are enabled in default configuration may change by applying maintenance.
- Only permit FIPS 140-2 compliant CipherSpecs using SSLFIPS.
![[UNIX, Linux, Windows]](ngulw.gif) Only permit NSA Suite B compliant CipherSpecs using SUITEB.
Only permit NSA Suite B compliant CipherSpecs using SUITEB.![[UNIX, Linux, Windows]](ngulw.gif) Permit a custom list of CipherSpecs using AllowedCipherSpecs
or the AMQ_ALLOWED_CIPHERS environment variable.
Permit a custom list of CipherSpecs using AllowedCipherSpecs
or the AMQ_ALLOWED_CIPHERS environment variable.![[UNIX, Linux, Windows]](ngulw.gif) Permit the use of deprecated CipherSpecs using
AllowWeakCipher or the AMQ_SSL_WEAK_CIPHER_ENABLE
environment variable.
Permit the use of deprecated CipherSpecs using
AllowWeakCipher or the AMQ_SSL_WEAK_CIPHER_ENABLE
environment variable.![[z/OS]](ngzos.gif) Permit the use of deprecated CipherSpecs using DD statements in the CHINIT
JCL.
Permit the use of deprecated CipherSpecs using DD statements in the CHINIT
JCL.
![[UNIX, Linux, Windows, IBM i]](ngmulti.gif)
![[V9.1.1 Nov 2018]](ng911.gif)
Providing a custom list of enabled CipherSpecs on Multiplatforms
It is possible for you to provide an alternative set of CipherSpecs that are enabled for use with IBM MQ channels, either using the AMQ_ALLOWED_CIPHERS environment variable or the AllowedCipherSpecs SSL stanza attribute of the .ini file. You may wish to use this setting to restrict IBM MQ listeners from accepting incoming channel start requests, unless they use one of the named CipherSpecs. This functionality can be used to control the CipherSpecs that are included in the ANY* CipherSpecs.
- A single CipherSpec name, or
- A comma separated list of IBM MQ CipherSpec names to re-enable, or
- The special value of ALL, representing all CipherSpecs (not recommended).
- IBM MQ listeners will only accept SSL/TLS proposals that use one of the named CipherSpecs.
- IBM MQ channels will only allow a blank SSLCIPH value, or one of the named CipherSpecs.
- runmqsc tab completion of SSLCIPH values restricts the completion values to one of the name CipherSpecs.
SSL:
AllowedCipherSpecs=ECDHE_RSA_AES_128_GCM_SHA256, ECDHE_ECDSA_AES_256_GCM_SHA384
Note that ciphers used by AMQP or MQTT channels can be restricted using java.security file settings.
![[UNIX, Linux, Windows, IBM i]](ngmulti.gif)
Enabling deprecated CipherSpecs on Multiplatforms
By default, you are not allowed to specify a deprecated CipherSpec on a channel definition. If you attempt to specify a deprecated CipherSpec on Multiplatforms, you receive message AMQ8242: SSLCIPH definition wrong, and PCF returns MQRCCF_SSL_CIPHER_SPEC_ERROR.
You cannot start a channel with a deprecated CipherSpec. If you attempt to do so with a deprecated CipherSpec, the system returns MQCC_FAILED (2), together with a Reason of MQRC_SSL_INITIALIZATION_ERROR (2393) to the client.
You can re-enable one or more of the deprecated CipherSpecs for defining channels, at runtime on the server, by setting the environment variable AMQ_SSL_WEAK_CIPHER_ENABLE.
- A single CipherSpec name, or
- A comma separated list of IBM MQ CipherSpec names to re-enable, or
- The special value of ALL, representing all CipherSpecs (not recommended).
export AMQ_SSL_WEAK_CIPHER_ENABLE=ECDHE_RSA_RC4_128_SHA256
SSL:
AllowTLSV1=Y
AllowWeakCipherSpec=ECDHE_RSA_RC4_128_SHA256
![[z/OS]](ngzos.gif)
Enabling deprecated CipherSpecs on z/OS
By default, you are not allowed to specify a deprecated CipherSpec on a channel definition. If you attempt to specify a deprecated CipherSpec on z/OS, you receive message CSQM102E or message CSQX674E.
JCL: //CSQXWEAK DD DUMMY JCL: //CSQXSSL3 DD DUMMY ![[V9.1.0 Jul 2018]](ng910.gif) To enable the deprecated TLS 1.0 protocol, you also need to define the following
DD statement in the CHINIT JCL:
To enable the deprecated TLS 1.0 protocol, you also need to define the following
DD statement in the CHINIT JCL:JCL: //TLS10ON DD DUMMY TLS10ON, to signify that TLS 1.0 is turned ON, and not
TLS100N. JCL: //TLS10OFF DD DUMMYJCL: //WCIPSOFF DD DUMMY JCL: //GSKDCIPS DD DUMMY ![[UNIX, Linux, Windows]](ngulw.gif)
![[V9.1.4 Dec 2019]](ng914.gif)
Minimum level versus fixed level CipherSpecs
- Minimum level CipherSpecs are those that do not set an upper bound, for example ANY, ANY_TLS12_OR_HIGHER or ANY_TLS13_OR_HIGHER.
- Fixed level CipherSpecs are those that identify a specific protocol, for example ANY_TLS12 and ANY_TLS13, or a specific algorithm such as ECDHE_ECDSA_3DES_EDE_CBC_SHA256
To maximise simplicity of configuration whilst maintaining security, the use of minimum level CipherSpecs is recommended on both sides of the channel. This allows your communications to automatically support and use a higher TLS protocol version when both sides support a new version without the need for changing either side's configuration.
Using a minimum level CipherSpec on the initiating side, but a fixed level CipherSpec on the receiving side could result in the connection being rejected and messages AMQ9631 and AMQ9641 being issued.
See Relationship between Alias CipherSpec settings for tables containing different outcomes for Alias CipherSpec settings.
![[UNIX, Linux, Windows]](../common/../com.ibm.mq.sec.doc/ngulw.gif)
![[UNIX, Linux, Windows, IBM i]](../common/../com.ibm.mq.sec.doc/ngmulti.gif)
![[z/OS]](../common/../com.ibm.mq.sec.doc/ngzos.gif) To use TLS 1.3, or the ANY CipherSpec, on
To use TLS 1.3, or the ANY CipherSpec, on
![[IBM i]](../common/../com.ibm.mq.sec.doc/ngibmi.gif) To use TLS 1.3, or the ANY CipherSpec, on
To use TLS 1.3, or the ANY CipherSpec, on ![[Linux]](../common/../com.ibm.mq.sec.doc/nglinux.gif)
![[Windows]](../common/../com.ibm.mq.sec.doc/ngwin.gif) Following a recommendation by
Following a recommendation by