Planning authentication for a client application
You can apply authentication controls at four levels: at the communications level, in security exits, with channel authentication records, and in terms of the identification that is passed to a security exit.
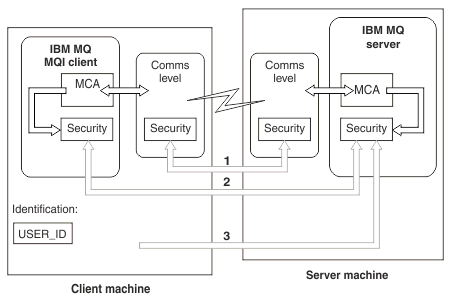
- Communications level
See arrow 1. To implement security at the communications level, use TLS. For more information, see Cryptographic security protocols: TLS
- Channel authentication records
See arrows 2 & 3. Authentication can be controlled by using the IP address or TLS distinguished names at the security level. A user ID can also be blocked or an asserted user ID can be mapped to a valid user ID. A full description is given in Channel authentication records.
- Connection authentication
See arrow 3. The client sends an ID and a password. For more information, see Connection authentication: Configuration.
- Channel security exits
See arrow 2. The channel security exits for client to server communication can work in the same way as for server to server communication. A protocol independent pair of exits can be written to provide mutual authentication of both the client and the server. A full description is given in Channel security exit programs.
- Identification that is passed to a channel security exit
See arrow 3. In client to server communication, the channel security exits do not have to operate as a pair. The exit on the IBM MQ client side can be omitted. In this case, the user ID is placed in the channel descriptor (MQCD) and the server-side security exit can alter it, if required.
Windows clients also send extra information to assist identification.- The user ID that is passed to the server is the currently logged-on user ID on the client.
- The security ID of the currently logged-on user.
The values of the user ID and, if available, the security ID, can be used by the server security exit to establish the identity of the IBM MQ MQI client.
From IBM MQ 8.0, you can send passwords that are included in the MQCSP structure.