What's changed in IBM WebSphere MQ Version 7.5 Fix Packs
Changes to functions and resources in Version 7.5 Fix Packs are described in this section.
![[V7.5.0.1 Mar 2013]](ng7501.gif) Version 7.5.0, Fix Pack 1: support for the MQTT over WebSockets
Version 7.5.0, Fix Pack 1: support for the MQTT over WebSockets![[V7.5.0.4 Sep 2014]](ng7504.gif) Version 7.5.0, Fix Pack 4: Disable IBM WebSphere MQ Advanced Message Security at the client by using AMQ_DISABLE_CLIENT_AMS
Version 7.5.0, Fix Pack 4: Disable IBM WebSphere MQ Advanced Message Security at the client by using AMQ_DISABLE_CLIENT_AMS![[V7.5.0.5 May 2015]](ng7505.gif) Version 7.5.0, Fix Pack 5: Disable IBM WebSphere MQ Advanced Message Security at the client by using the mqclient.ini file
Version 7.5.0, Fix Pack 5: Disable IBM WebSphere MQ Advanced Message Security at the client by using the mqclient.ini file
![[V7.5.0.6 Mar 2016]](ng7506.gif) Version 7.5.0, Fix Pack 6: userid and password for managed .NET client applications
Version 7.5.0, Fix Pack 6: userid and password for managed .NET client applications![[V7.5.0.6 Mar 2016]](ng7506.gif) Version 7.5.0, Fix Pack 6: deprecated cipherspecs
Version 7.5.0, Fix Pack 6: deprecated cipherspecs![[V7.5.0.6 Mar 2016]](ng7506.gif) Version 7.5.0, Fix Pack 6: Serviceability enhancements for IBM WebSphere MQ Managed File Transfer
Version 7.5.0, Fix Pack 6: Serviceability enhancements for IBM WebSphere MQ Managed File Transfer![[V7.5.0.6 Mar 2016]](ng7506.gif) Version 7.5.0, Fix Pack 6 New IBM WebSphere MQ Managed File Transfer agent property failTransferOnFirstFailure
Version 7.5.0, Fix Pack 6 New IBM WebSphere MQ Managed File Transfer agent property failTransferOnFirstFailure![[V7.5.0.7 Sep 2016]](ng7507.gif) Version 7.5.0, Fix Pack 7: deprecated cipherspecs
Version 7.5.0, Fix Pack 7: deprecated cipherspecs
![[V7.5.0.7 Sep 2016]](ng7507.gif) Version 7.5.0, Fix Pack 7: support for JDBC connections to an Oracle 12c database
Version 7.5.0, Fix Pack 7: support for JDBC connections to an Oracle 12c database
![[V7.5.0.7 Sep 2016]](ng7507.gif) Version 7.5.0, Fix Pack 7: Removal of restriction on using .NET for MQCNO_CLIENT_BINDING and MQCNO_LOCAL_BINDING
Version 7.5.0, Fix Pack 7: Removal of restriction on using .NET for MQCNO_CLIENT_BINDING and MQCNO_LOCAL_BINDING![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: Restriction on the use of topic alias queues in distribution lists
Version 7.5.0, Fix Pack 8: Restriction on the use of topic alias queues in distribution lists![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: GSKit version updated
Version 7.5.0, Fix Pack 8: GSKit version updated![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: Deprecated CipherSpecs
Version 7.5.0, Fix Pack 8: Deprecated CipherSpecs![[V7.5.0.8 Jun]](ng7508.gif) Version 7.5.0, Fix Pack 8: New constant JMS_IBM_SUBSCRIPTION_USER_DATA added to the JmsConstants interface
Version 7.5.0, Fix Pack 8: New constant JMS_IBM_SUBSCRIPTION_USER_DATA added to the JmsConstants interface![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: JMS exception listener updates
Version 7.5.0, Fix Pack 8: JMS exception listener updates![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: Support for class name allowlisting in IBM WebSphere MQ classes for JMS ObjectMessage
Version 7.5.0, Fix Pack 8: Support for class name allowlisting in IBM WebSphere MQ classes for JMS ObjectMessage![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: New IBM WebSphere MQ Managed File Transfer agent property additionalWildcardSandboxChecking
Version 7.5.0, Fix Pack 8: New IBM WebSphere MQ Managed File Transfer agent property additionalWildcardSandboxChecking![[V7.5.0.8 Jun 2017]](ng7508.gif) Version 7.5.0, Fix Pack 8: Change to behavior of IBM WebSphere MQ Managed File Transfer fteCleanAgent command
Version 7.5.0, Fix Pack 8: Change to behavior of IBM WebSphere MQ Managed File Transfer fteCleanAgent command![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: New environment variable AMQ_SSL_LDAP_SERVER_VERSION
Version 7.5.0, Fix Pack 9: New environment variable AMQ_SSL_LDAP_SERVER_VERSION![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Sample configuration file for IBM WebSphere MQ classes for JMS
Version 7.5.0, Fix Pack 9: Sample configuration file for IBM WebSphere MQ classes for JMS![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Changes to the dmpmqcfg command
Version 7.5.0, Fix Pack 9: Changes to the dmpmqcfg command![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Changes to the strmqm command
Version 7.5.0, Fix Pack 9: Changes to the strmqm command![[V7.5.0.9 Sep 2018]](ng7509.gif) Enhancements to runmqras utility
Enhancements to runmqras utility![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers
Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Resource adapater updates for targetClientMatching property on an activation specification
Version 7.5.0, Fix Pack 9: Resource adapater updates for targetClientMatching property on an activation specification![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: New -caseno parameter for the runmqras command
Version 7.5.0, Fix Pack 9: New -caseno parameter for the runmqras command![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Change to handling of errors relating to corrupted character data within internal MQ command messages used by queue manager clustering component
Version 7.5.0, Fix Pack 9: Change to handling of errors relating to corrupted character data within internal MQ command messages used by queue manager clustering component![[V7.5.0.9 Sep 2018]](ng7509.gif)
 Version 7.5.0, Fix Pack 9: Addition of Microsoft Visual Studio 2013 C/C++ runtimes on Windows
Version 7.5.0, Fix Pack 9: Addition of Microsoft Visual Studio 2013 C/C++ runtimes on Windows![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers
Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers
Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers![[V7.5.0.9 Sep 2018]](ng7509.gif) Version 7.5.0, Fix Pack 9 plus interim fix for APAR IT26482: Change to authorities needed for IBM WebSphere MQ classes for JMS to query the BackoutThreshold and BackoutRequeueQName of a cluster queue
Version 7.5.0, Fix Pack 9 plus interim fix for APAR IT26482: Change to authorities needed for IBM WebSphere MQ classes for JMS to query the BackoutThreshold and BackoutRequeueQName of a cluster queue
![[V7.5.0.1 Mar 2013]](ng7501.gif)
Version 7.5.0, Fix Pack 1: support for the MQTT over WebSockets
- If the parameter is set to MQTTV3, the channel only accepts connections from clients using Version 3 of the MQ Telemetry Transfer protocol. This was the only protocol supported before IBM® WebSphere® MQ Version 7.5.0, Fix Pack 1.
- If the parameter is set to HTTP, the channel only accepts HTTP requests for pages, or WebSockets connections to IBM WebSphere MQ Telemetry.
- If the parameter is set to MQTTV3,HTTP, the channel accepts connections from clients using either protocol. This is the default behavior for new MQTT channels created with IBM WebSphere MQ Version 7.5.0, Fix Pack 1 and later versions.
- REQUIRED means that IBM WebSphere MQ requests a certificate from the client and the client must supply a valid certificate.
- OPTIONAL means that IBM WebSphere MQ will request a certificate from the client but the client does not have to supply one. The client connection is allowed if the client supplies a valid certificate or if the client does not supply a certificate. The client connection is disallowed only if the client supplies an invalid certificate.
In IBM WebSphere MQ Version 7.5.0, Fix Pack 1 and later, the parameter SSLCAUTH can be set to NEVER for MQTT channels. NEVER means that IBM WebSphere MQ never requests a certificate from the client. The new value was added as part of the support for clients using the MQTT messaging client for JavaScript. It accommodates the behavior of some web browsers which treat the request for a client certificate as a protocol error.
![[V7.5.0.4 Sep 2014]](ng7504.gif)
Version 7.5.0, Fix Pack 4: Disable IBM WebSphere MQ Advanced Message Security at the client by using AMQ_DISABLE_CLIENT_AMS
From Version 7.5.0, Fix Pack 4, you use the environment variable AMQ_DISABLE_CLIENT_AMS to disable IBM WebSphere MQ Advanced Message Security (AMS) within IBM WebSphere MQ classes for JMS and IBM WebSphere MQ classes for Java clients to prevent errors when they are connecting to queue managers that are running on earlier versions of the product. Alternatively, and also from Version 7.5.0, Fix Pack 4, you can use the Java system property com.ibm.mq.cfg.AMQ_DISABLE_CLIENT_AMS to disable AMS at the client.
For more information, see Disabling IBM WebSphere MQ Advanced Message Security at the client.
![[V7.5.0.5 May 2015]](ng7505.gif)
Version 7.5.0, Fix Pack 5: Disable IBM WebSphere MQ Advanced Message Security at the client by using the mqclient.ini file
From Version 7.5.0, Fix Pack 4, you can disable IBM WebSphere MQ Advanced Message Security (AMS) at the client to prevent errors when they are connecting to queue managers that are running on earlier versions of the product by setting the configuration variable AMQ_DISABLE_CLIENT_AMS. From Version 7.5.0, Fix Pack 5, you can also disable AMS by using the DisableClientAMS property, under the Security stanza in the mqclient.ini file. For more information, see Disabling IBM WebSphere MQ Advanced Message Security at the client.

![[V7.5.0.6 Mar 2016]](ng7506.gif)
Version 7.5.0, Fix Pack 6: userid and password for managed .NET client applications
From IBM WebSphere MQ Version 7.5.0, Fix Pack 6, the userid and password that are specified with the managed .NET client application are set in the IBM WebSphere MQ .NET MQChannelDefinition class that is passed to the client security exit. For more information, see Using channel exits in IBM WebSphere MQ .NET.
Version 7.5.0, Fix Pack 6: deprecated cipherspecs
- DES_SHA_EXPORT


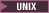 DES_SHA_EXPORT1024
DES_SHA_EXPORT1024

 FIPS_WITH_DES_CBC_SHA
FIPS_WITH_DES_CBC_SHA- NULL_MD5
- NULL_SHA
- TLS_RSA_WITH_DES_CBC_SHA
- ECDHE_ECDSA_NULL_SHA256


 ECDHE_RSA_NULL_SHA256
ECDHE_RSA_NULL_SHA256

 TLS_RSA_WITH_NULL_NULL
TLS_RSA_WITH_NULL_NULL- TLS_RSA_WITH_NULL_SHA256
![[V7.5.0.6 Mar 2016]](ng7506.gif)
Version 7.5.0, Fix Pack 6: Serviceability enhancements for IBM WebSphere MQ Managed File Transfer
- The default value for of the commandMessagePriority property in the installation.properties file has changed to 8. For more information, see The installation.properties file.
- The default value for of the logTransferRecovery property in the agent.properties file has changed to true. For more information, see The agent.properties file.
- The need for the enableFunctionalFixPack property to be set in the installation.properties file when using the -d parameter on the fteShowAgentDetails command is removed. for more information, see fteShowAgentDetails.
- A first failure data capture (FDC) is generated if an agent encounters an unrecoverable error.

![[V7.5.0.6 Mar 2016]](ng7506.gif)
Version 7.5.0, Fix Pack 6 New IBM WebSphere MQ Managed File Transfer agent property failTransferOnFirstFailure
From IBM WebSphere MQ Version 7.5.0, Fix Pack 6, you can configure an agent to fail a managed transfer as soon as a transfer item within that managed transfer fails by setting the failTransferOnFirstFailure property in the agent.properties file. For more information, see The agent.properties file.
Version 7.5.0, Fix Pack 7: deprecated cipherspecs
- RC2_MD5_EXPORT
- RC4_MD5_EXPORT
- RC4_MD5_US
- RC4_SHA_US


 RC4_56_SHA_EXPORT1024
RC4_56_SHA_EXPORT1024

 ECDHE_ECDSA_RC4_128_SHA256
ECDHE_ECDSA_RC4_128_SHA256

 ECDHE_RSA_RC4_128_SHA256
ECDHE_RSA_RC4_128_SHA256

 TLS_RSA_WITH_RC4_128_SHA256
TLS_RSA_WITH_RC4_128_SHA256

![[V7.5.0.7 Sep 2016]](ng7507.gif)
Version 7.5.0, Fix Pack 7: support for JDBC connections to an Oracle 12c database
From IBM WebSphere MQ Version 7.5.0, Fix Pack 7, a new file, jdbcora12.dll, is supplied with the IBM WebSphere MQ Windows server installation image to support JDBC connections to an Oracle 12c database (see Configuring JTA/JDBC coordination on Windows).

![[V7.5.0.7 Sep 2016]](ng7507.gif)
Version 7.5.0, Fix Pack 7: Removal of restriction on using .NET for MQCNO_CLIENT_BINDING and MQCNO_LOCAL_BINDING
From IBM WebSphere MQ Version 7.5.0, Fix Pack 7, the IBM WebSphere MQ custom channel for Microsoft Windows Communication Foundation (WCF) has been updated so that the correct client connection configuration is used when running from a client-only installation. For more information, see Connecting to a queue manager using the MQCONNX call.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: Restriction on the use of topic alias queues in distribution lists
Distribution lists do not support the use of alias queues that point to topic objects. From Version 7.5.0, Fix Pack 8, if an alias queue points to a topic object in a distribution list, IBM WebSphere MQ returns MQRC_ALIAS_BASE_Q_TYPE_ERROR.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: GSKit version updated
The GSKit version has been updated. The new version of GSKit alters the stash file format that is used when you generate an .sth file to stash the key database password. Stash files that are generated with this version of GSKit are not readable by earlier versions of GSKit. To ensure that stash files that are generated with Version 7.5.0, Fix Pack 8, or later, are compatible with your applications and other IBM WebSphere MQ installations, you must update to a version of IBM WebSphere MQ that contains a compatible version of GSKit. For IBM WebSphere MQ Version 7.5, this is Version 7.5.0, Fix Pack 8.
If you cannot update your applications or other IBM WebSphere MQ installations, you can request a stash file format
that is compatible with an earlier version. When you use the runmqakm or
runmqckm commands with the -stash or -stashpw
option, include the -v1stash command line parameter. You cannot use the iKeyman GUI
to generate a stash file that is compatible with an earlier version.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: Deprecated CipherSpecs


 FIPS_WITH_3DES_EDE_CBC_SHA
FIPS_WITH_3DES_EDE_CBC_SHA- TRIPLE_DES_SHA_US
- TLS_RSA_WITH_3DES_EDE_CBC_SHA


 ECDHE_ECDSA_3DES_EDE_CBC_SHA256
ECDHE_ECDSA_3DES_EDE_CBC_SHA256

 ECDHE_RSA_3DES_EDE_CBC_SHA256
ECDHE_RSA_3DES_EDE_CBC_SHA256
![[V7.5.0.8 Jun]](ng7508.gif)
Version 7.5.0, Fix Pack 8: New constant JMS_IBM_SUBSCRIPTION_USER_DATA added to the JmsConstants interface
From Version 7.5.0, Fix Pack 8, the IBM WebSphere MQ classes for JMS are updated so that when a message is consumed from a queue that contains an RFH2 header with the MQPS folder, the value associated with the Sud key, if it exists, is added as a String property to the JMS Message object returned to the IBM WebSphere MQ classes for JMS application. To enable an application to retrieve this property from the message, a new constant, JMS_IBM_SUBSCRIPTION_USER_DATA, is added to the JmsConstants interface. This new property can be used with the method javax.jms.Message.getStringProperty(java.lang.String) to retrieve the subscription user data. For more information, see Retrieval of user subscription data and DEFINE SUB.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: JMS exception listener updates
From IBM WebSphere MQ Version 7.5.0, Fix Pack 8, to maintain behavior for current JMS applications that configure a JMS MessageListener and a JMS ExceptionListener, the default value for the ASYNC_EXCEPTIONS JMS ConnectionFactory property has been changed to ASYNC_EXCEPTIONS_CONNECTIONBROKEN for the IBM WebSphere MQ classes for JMS for Version 7.5. As a result, by default, only exceptions corresponding to broken connection error codes are delivered to an application's JMS ExceptionListener. Connection broken exceptions are delivered to the exception listener when consuming messages synchronously or asynchronously.
The IBM WebSphere MQ classes for JMS for Version 7.5 have also been updated such that JMS exceptions relating to non-connection broken errors that occur during message delivery to asynchronous message consumers, are delivered to a registered ExceptionListener when the JMS ConnectionFactory used by the application has the ASYNC_EXCEPTIONS property set to the value ASYNC_EXCEPTIONS_ALL.
For more information, see JMS: Exception listener changes in Version 7.5 and Exceptions in IBM WebSphere MQ classes for JMS.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: Support for class name allowlisting in IBM WebSphere MQ classes for JMS ObjectMessage
From IBM WebSphere MQ Version 7.5.0, Fix Pack 8, IBM WebSphere MQ classes for JMS supports allowlisting of classes in the implementation of the JMS ObjectMessage interface. The allowlist defines which Java classes might be serialized with ObjectMessage.setObject() and deserialized with ObjectMessage.getObject().
For more information, see Class name allowlisting in JMS ObjectMessage and Running IBM WebSphere MQ classes for JMS applications under the Java Security Manager.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: New IBM WebSphere MQ Managed File Transfer agent property additionalWildcardSandboxChecking
From IBM WebSphere MQ Version 7.5.0, Fix Pack 8, if an agent has been configured with a user or agent sandbox in order to restrict the locations that the agent can transfer files to and from, you can specify that additional checks are to be made on wildcard transfers for that agent by setting the additionalWildcardSandboxChecking property to true. For more information, see Additional checks for wildcard transfers and The agent.properties file.
![[V7.5.0.8 Jun 2017]](ng7508.gif)
Version 7.5.0, Fix Pack 8: Change to behavior of IBM WebSphere MQ Managed File Transfer fteCleanAgent command
From IBM WebSphere MQ Version 7.5.0, Fix Pack 8, the fteCleanAgent command has been updated so that you must specify which IBM WebSphere MQ Managed File Transfer state to clear by passing the appropriate parameters to the command, as well as providing an agent name. This change in behavior ensures that, by default, fteCleanAgent does not clear all in-progress and pending transfers, resource monitor definitions and scheduled transfer definitions for the agent specified.
If required, you can revert to the previous behavior of fteCleanAgent by setting the new failCleanAgentWithNoArguments property in the command.properties file to false.
For more information, see fteCleanAgent (cleans up a Managed File Transfer Agent) and The command.properties file.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: New environment variable AMQ_SSL_LDAP_SERVER_VERSION
From Version 7.5.0, Fix Pack 9, you can set the environment variable AMQ_SSL_LDAP_SERVER_VERSION to ensure that IBM WebSphere MQ passes the required lightweight directory access protocol (LDAP) version, that is LDAP v2 or LDAP v3, to GSKit when a certificate is validated against a higher version of LDAP Certificate Revocation List (CRL) server. For more information, see Environment variables.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Sample configuration file for IBM WebSphere MQ classes for JMS
From Version 7.5.0, Fix Pack 9, a sample configuration file, mqjava.config, is supplied in the bin subdirectory of the IBM WebSphere MQ classes for JMS installation directory. For more information, see The IBM MQ classes for Java configuration file.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Changes to the dmpmqcfg command
From Version 7.5.0, Fix Pack 9, a command line switch -w is added to dmpmqcfg. This switch allows you increase the time, in seconds, that dmpmqcfg waits for a reply message from the command server.
For more information, see dmpmqcfg.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Changes to the strmqm command
From Version 7.5.0, Fix Pack 9, the strmqm command checks the syntax of the CHANNELS and SSL stanzas in the qm.ini file before starting the queue manager fully, which makes it much easier to see what is wrong, and correct it quickly if strmqm finds that the qm.ini file contains any errors. For more information, see strmqm.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Enhancements to runmqras utility


 Environment variable information is retrieved by default.
Environment variable information is retrieved by default. Queue manager data directory listings are retrieved by default.
Queue manager data directory listings are retrieved by default.- The following two sections are added to the runmqras command:

 A
A leaksection to gather IBM WebSphere MQ process resource usage information. An
An mftsection to capture the data obtained by the fteRas command.
For more information, see runmqras.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Resource adapater updates for targetClientMatching property on an activation specification
The IBM WebSphere MQ JCA resource adapter (MQ-RA) has been updated such that the targetClientMatching property can be configured for an activation specification. You can configure the property so that an MQRFH2 header is included on reply messages when request messages do not contain an MQRFH2 header. This means that any message properties that an application defines on a reply message are included when the message is sent. For more information, see Configuring the targetClientMatching property for an activation specification.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: New -caseno parameter for the runmqras command
The -caseno parameter is equivalent to -pmrno, except it allows a valid Salesforce case number to specified. -caseno or -pmrno are both optional parameters, but it is not permitted to supply both together. For more information, see runmqras (collect IBM MQ diagnostic information).
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Change to handling of errors relating to corrupted character data within internal MQ command messages used by queue manager clustering component
From Version 7.5.0, Fix Pack 9, the way in which the queue manager handles errors that relate to corrupted character data within internal MQ command messages that are used by the clustering component of the queue manager is changed. The field(s) that might contain unconvertible characters are blanked out and the conversion is retried. If the conversion succeeds, the update is stored with a blank description and error messages AMQ6174 and AMQ9880 are written, to inform the administrator. If the message is still unconvertible, it is moved to the Dead Letter Queue and an error message is written.
![[V7.5.0.9 Sep 2018]](ng7509.gif)

Version 7.5.0, Fix Pack 9: Addition of Microsoft Visual Studio 2013 C/C++ runtimes on Windows
From Version 7.5.0, Fix Pack 9, some elements of IBM WebSphere MQ require the Microsoft Visual Studio 2013 C/C++ (VS2013) runtimes. These runtimes are installed by any fresh installation of IBM WebSphere MQ Version 7.5.0, Fix Pack 9.
If the VS2013 runtimes are not present on the machine, they are installed when you install a fresh client, update a client to the 7.5.0.9 maintenance level or apply the 7.5.0.9 fix pack. In most cases, this process requires no user action but, should you encounter an installation failure when applying the server fix pack, there is an environment variable that you might need to specify so that you can install the runtimes manually. For more information, see Installation of Microsoft Visual Studio 2013 C/C++ runtimes in a server fix pack.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9: Comparison check of transfer identifier and value of groupId attribute restored for message-to-file transfers
From Version 7.5.0, Fix Pack 9, IBM WebSphere MQ Managed File Transfer is updated to restore the comparison check, previously removed by APAR IT18213 at Version 7.5.0, Fix Pack 6, of the transfer identifier and the value of the groupId attribute within the transfer request XML payload. If these two identifiers are equivalent, the source agent uses the identifier as a message identifier match option (as opposed to a group identifier match option) for the first MQGET attempt that is made on the input queue for the message-to-file transfer. See also Transferring data from messages to files.
![[V7.5.0.9 Sep 2018]](ng7509.gif)
Version 7.5.0, Fix Pack 9 plus interim fix for APAR IT26482: Change to authorities needed for IBM WebSphere MQ classes for JMS to query the BackoutThreshold and BackoutRequeueQName of a cluster queue
For Version 7.5.0, Fix Pack 9 plus an interim fix for APAR IT26482, the IBM WebSphere MQ classes for JMS have been updated so that only inquire access is required to query the BackoutThreshold and BackoutRequeueQName of a cluster queue. For all other versions, browse and get access are also required. For more information, see Handling poison messages in IBM MQ classes for JMS.