Use IBM Key Management to configure custom certificates
You can generate a certificate request and import a certificate with the IBM® Key Management tool.
About this task
If a signed certificate is already available for the system that is running the Planning Analytics web tier, start at step 3. This signed certificate must be in the form of a pkcs12 or jks file. This file is password-protected.
Procedure
- Use the IBM Key Management tool
(ikeyman.exe) to access the CAMKeystore file and generate a certificate
request. The ikeyman.exe program is found in the <PA_install_directory>\jre\bin directory of the Planning Analytics installation or in the IBM JRE installation if Linux® used. The CAMKeystore file is found in the \configuration\certs\ directory. The default certificate created by the built-in services is issued to CN=CAMUSER and issued by CN=CA
- Click
 to open a key database file
and select the file. The key database file type must be PKCS12. The default password for the CAMKeystore file is NoPassWordSet.
to open a key database file
and select the file. The key database file type must be PKCS12. The default password for the CAMKeystore file is NoPassWordSet. - In the Personal Certificates section, select the certificate
with the label encryption and click
Delete.
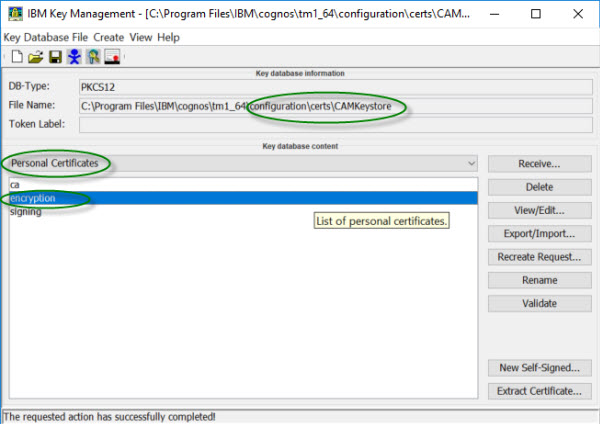
You must replace this certificate with your own certificate that will be issued to the name of the server running TM1Web.
- In the Personal Certificates section and click
Create > New Certificate
Request or click
 in the IBM Key Management toolbar. Fill in the details as
follows:
in the IBM Key Management toolbar. Fill in the details as
follows: 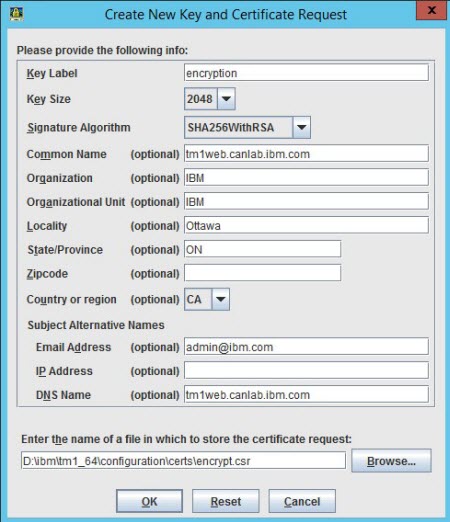
The Key Label must be encryption, Key Size 2048, and Signature Algorithm SHA256WithRSA. Setting a Subject Alternative Name: DNS Name is also strongly recommended because web browsers might require a proper Subject Alternative Name (SAN) to validate the certificate.
- Enter the location and name of the certificate request file and click OK.
- Click
- Get the certificate request signed by a Certificate Authority (CA). The certificate request file must be provided to the CA. The CA will provide one or more files that contain a signed certificate and the CA certificates in the chain.
- Import a server key and certificates from an external keystore or replace the
encryption certificate with one that was created with IBM Key
Management.
- Use IBM Key Management to open the CAMKeystore file. See step 1.
- In the Personal Certificates section, select the encryption certificate and click Delete if it has not been removed yet.
- In the Personal Certificates section, click
Receive to import the new certificate and select the certificate file that
contains the certificate to be used. This file should typically contain the signed certificate and the certificate authority chain certificate (root and intermediate certificates). During the import, IBM Key Management prompts for a label for the signed certificate. This label must be encryption. All certificates will be imported into CAMKeystore during the import action. If the file being imported does not contain the full certificate chain, the CA certificates must be added separately to the Signer Certificates section.
- In the Signer Certificates section, click
Add and select the file or files containing the CA certificates.
If a single file contains multiple CA certificates (for example, a root and multiple intermediate certificates) then multiple certificates can be selected for import. IBM Key Management prompts for a label for these certificate. A specific label is not required for the CA certificates.
- After the CA certificates have been added to the Signer Certificates section, switch back to the Personal Certificates section and click Receive to receive the signed encryption certificate.
When the signed encryption certificate has been received into the keystore, double-click the encryption certificate to see the details and verify that the certificate is issued to the system running TM1Web, and issued by one of the CA certs in the chain.
- Enable TLS in IBM
Cognos® Configuration.
-
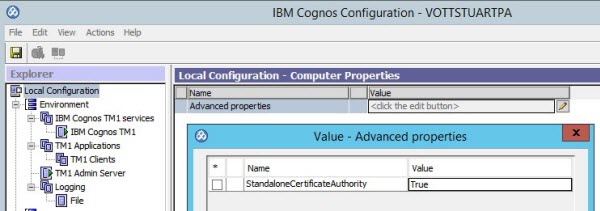
Add the StandaloneCertificateAuthority property under the Local Configuration > Advanced Properties section and set it to True.
-
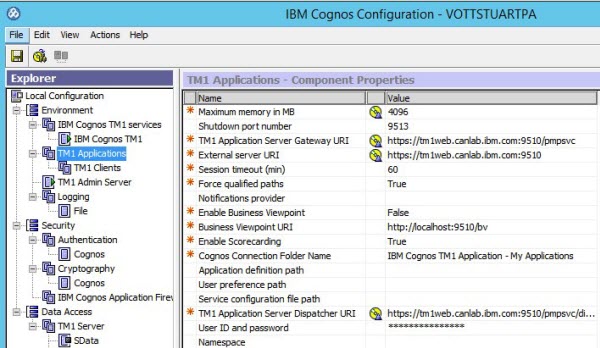
Update the TM1 Applications settings in Cognos Configuration to specify HTTPS.
-
Set Use third party CA? to True in the Security > Cryptography > Cognos section of Cognos Configuration.
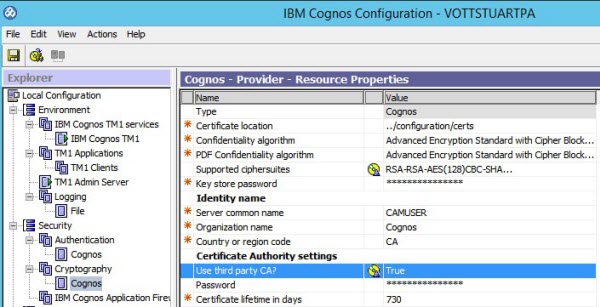
-
Add the StandaloneCertificateAuthority property under the Local Configuration > Advanced Properties section and set it to True.
- Add the TM1®
Server CA
certificate to the CAMKeystore keystore file.
Note: If this step is missed, TM1Web cannot connect to TM1 Server. This step must be completed even if the TM1 Server is not using custom certificates.
- Use IBM Key Management to open the CAMKeystore file, and switch to the Signer Certificates section.
- Click Add and select the
./tm1_64/bin64/ssl/ibmtm1.arm file (assuming the TM1 Server uses the certificate provided by IBM, otherwise select your own file containing your CA certificate). There is no requirement for a specific label for certificates added to the Signer Certificates section of IBM Key Management.
- Restart the IBM Cognos TM1 service from either Cognos Configuration or the list of Windows services.