Using namespaces with Pod Security Policies
Namespaces are used to isolate groups of resources from one another. The security of a namespace is determined by the ClusterRoleBindings and RoleBindings of the users and service accounts.
As the bindings are created for Service Accounts to Roles and Cluster Roles, any Pod in the namespace can utilize any of the service accounts without any additional permission elevation checks.
To simplify this thought, the strategy is to map a single Pod Security Policy to all Service Accounts in a namespace, or use a small number of Pod Security Policies that have a similar security strategy.
The following diagram shows worker nodes in an un-privileged host group and worker nodes in a privileged host group.
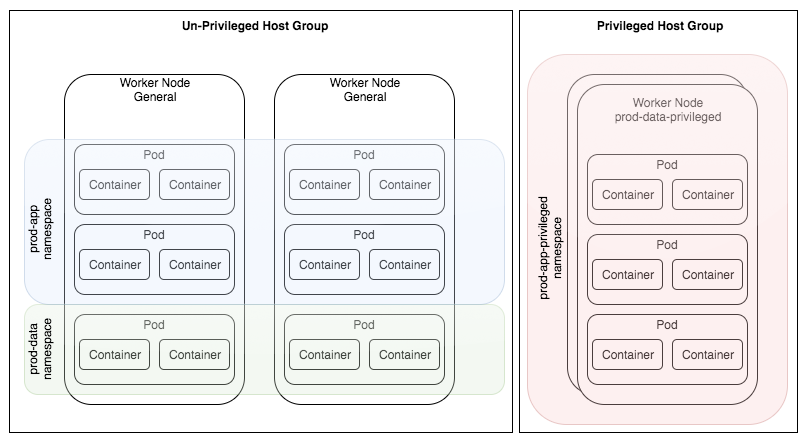
See Pod isolation for more information.