Regenerating collective security certificates
You can regenerate and configure a collective setup so that SSL continues to protect communication between controllers and members. This regeneration is exclusive to certificates signed by a collective root.
Before you begin
Liberty 19.0.0.2 and earlier comes with .jks (format type is JKS) and Liberty 19.0.0.3 and later comes with .p12 (format type is PCKS12)
Here is a diagram about the collective controller and members keystore and truststore details.
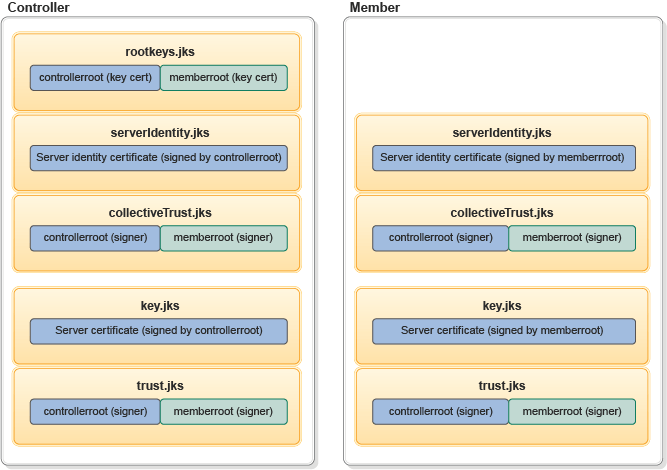
About this task
Default collective self-signed certificates are valid for only 5 years. If these certificates expired, then you need to generate new self-signed certificates using the steps in this procedure.
The regeneration procedure is exclusive to certificates signed by a collective root signer. These instructions do not apply for Certificate Authority (CA) signed certificates.
- The steps in this procedure only apply if you are using a collective environment with default certificates.
- Before proceeding, make sure to create a backup of every keystore in your collective system.
- The connection between the controller and members will be interrupted as you follow the steps in the procedure.
- For public-facing production servers, use only CA-signed certificates, including product-created and your own organization’s CAs. Do not use self-signed certificates for public facing servers.
- To learn how to configure a collective system with third-party CA certificates, review Setting up collectives with third-party certificates.
- As you go through these steps, if you are using JKS [.jks] keystores, replace all references to PKCS12 [.p12].
- Replace every attribute that has the dollar sign [
$] to the actual value for your configuration.
Procedure
Generating controller and member root certificates
-
Run this command to list the certificates inside your rootKeys.p12
keystore.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/collective/rootKeys.p12 -storepass $KEYSTORE_PASSWORD -storetype PKCS12Sample command and output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/collective/rootKeys.p1 2 -storepass password -storetype PKCS12 Alias name: controllerroot Owner: OU=controllerRoot, O=6b66c164-0133-41d8-9f78-913622da530a, DC=com.ibm.ws.collective Alias name: memberroot Owner: OU=memberRoot, O=6b66c164-0133-41d8-9f78-913622da530a, DC=com.ibm.ws.collectiveStore the DN-NAME that gets printed in a text file. The
DN-NAMEin the sample isOU=memberRoot, O=6b66c164-0133-41d8-9f78-913622da530a, DC=com.ibm.ws.collective. -
Run this keytool -genkeypair command to create a new root keystore with the
controllerrootalias.keytool -genkeypair -keyalg RSA -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PASSWORD -storetype PKCS12 -alias controllerroot -validity 7300 -dname "$DN-NAME" -ext BasicConstraints:"critical=ca:true"Sample command and output/root/wlp/java/java/jre/bin/keytool -genkeypair -keyalg RSA - keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias controllerroot -validity 7300 -dname "OU=controllerRoot, O=6b66c164-0133-41d8- 9f78-913622da530a, DC=com.ibm.ws.collective" -ext BasicConstraints:"critical=ca:true" - Run the genkeypair command again and add the
memberrootcertificate to newrootKeys.p12.keytool -genkeypair -keyalg RSA -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PASSWORD -storetype PKCS12 -alias memberroot -validity 7300 -dname "DN-NAME" -ext BasicConstraints:"critical=ca:true"Sample command and output/root/wlp/java/java/jre/bin/keytool -genkeypair -keyalg RSA - keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias memberroot - validity 7300 -dname "OU=memberroot, O=6b66c164-0133-41d8-9f78- 913622da530a, DC=com.ibm.ws.collective" -ext BasicConstraints:"critical=ca:true" - List the keystores to verify their accuracy.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $KEYSTORE_PASSWORD -storetype PKCS12Sample command and output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12The
controllerrootsigner and thememberrootsigner from the newrootKeys.p12 keystore must be added to all collective controllers and members HTTPS SSL truststore, trust.p12 and also need to be added to collectivetrust.p12 from controllers and members. -
Export the
controllerrootsigner andmemberrootsigner from newrootKeys.p12.keytool -exportcert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PASSWORD -storetype PKCS12 -alias controllerroot -rfc >$PATH_CONTROLLER_SERVER/resources/collective/controllerroot.pemkeytool -exportcert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PASSWORD -storetype PKCS12 -alias memberroot -rfc >$PATH_CONTROLLER_SERVER/resources/collective/memberroot.pemSample command and output/root/wlp/java/java/jre/bin/keytool -exportcert -keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias controllerroot -rfc > /root/wlp/usr/servers/controller/resources/collective/controllerr oot.pem /root/wlp/java/java/jre/bin/keytool -exportcert -keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias memberroot -rfc > /root/wlp/usr/servers/controller/resources/collective/memberroot. pem - Verify the accuracy of the content in newrootKeys.p12. If accurate, remove rootKeys.p12 and replace it with the newly generated newrootKeys.p12.
Controller: Replacing the controller and memberroot certificates inside collectiveTrust.p12 and trust.p12
-
As a precaution, rename the existing alias for collectiveTrust.p12 and
trust.p12.
keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore $PATH_CONTROLLER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVETRUST_KEYSTORE_PWD -storetype PKCS12keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore $PATH_CONTROLLER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVETRUST_KEYSTORE_PWD -storetype PKCS12Sample command for collectiveTrust.p12/root/wlp/java/java/jre/bin/keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore /root/wlp/usr/servers/controller/resources/collective/collec tiveTrust.p12 -storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore /root/wlp/usr/servers/controller/resources/collective/collec tiveTrust.p12 -storepass password -storetype PKCS12keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore $PATH_CONTROLLER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore $PATH_CONTROLLER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12Sample command for trust.p12/root/wlp/java/java/jre/bin/keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore /root/wlp/usr/servers/controller/resources/security/trust.p1 2 -storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore /root/wlp/usr/servers/controller/resources/security/trust.p1 2 -storepass password -storetype PKCS12 - Add the
memberrootsigner andcontrollerrootsigner previously created and to the collectiveTrust.p12 and trust.p12.- First, process collectiveTrust.p12.
keytool -importcert -keystore PATH_CONTROLLER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVETRUST_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/resources/collective/controllerroot.pemkeytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVETRUST_KEYSTORE_PWD -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/controller/resources/collective/memberroot.pemSample commands/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/collective/collec tiveTrust.p12 -storepass password -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/contro llerroot.pem /root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/collective/collec tiveTrust.p12 -storepass password -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/member root.pem - Next, process trust.p12.
/root/wlp/java/java/jre/bin/keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/resources/collective/controllerroot.pem/root/wlp/java/java/jre/bin/keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/resources/collective/memberroot.pemSample commands/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/security/trust.p1 2 -storepass password -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/contro llerroot.pem /root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/security/trust.p1 2 -storepass password -storetype PKCS12 -alias memberroot - trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/member root.pem
- First, process collectiveTrust.p12.
Controller: Updating the serverIdentity.p12 file.
- List the certificates contained in the serverIdentity.p12
file.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/collective/serverIdentity.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12Sample command and output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/collective/serverIdent ity.p12 -storepass password -storetype PKCS12 Alias name: serveridentity Owner: CN=controller, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=controller, O=6b66c164-0133-41d8- 9f78-913622da530a, DC=com.ibm.ws.collectiveSave the
DN-NAMEof theserveridentitycertificate from the output. For this example, the DN-NAME isCN=controller, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=controller, O=6b66c164-0133-41d8-9f78- 913622da530a, DC=com.ibm.ws.collective. - Generate a new keystore using the
DN-NAMEfrom the previous output.keytool -genkeypair -alias serveridentity -dname $DN-NAME -keysize 2048 -validity 7300 -keyalg rsa -keystore $PATH_CONTROLLER_SERVER/resources/collective/newkeystore.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -ext BasicConstraints:"critical=ca:true"Sample command/root/wlp/java/java/jre/bin/keytool -genkeypair -alias serveridentity -dname "CN=controller, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=controller, O=6b66c164-0133- 41d8-9f78-913622da530a, DC=com.ibm.ws.collective" -keysize 2048 -validity 7300 -keyalg rsa -keystore /root/wlp/usr/servers/controller/resources/collective/newkey store.p12 -storepass password -storetype PKCS12 -ext BasicConstraints:"critical=ca:true" - Generate a new
serveridentitycertificate and extract the .pem file.keytool -certreq -keystore $PATH_CONTROLLER_SERVER/resources/collective/newkeystore.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias serveridentity | keytool -gencert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -rfc -validity 7300 -ext BasicConstraints:"critical=ca:true" >$PATH_CONTROLLER_SERVER/resources/collective/serveridentity.pemSample command/root/wlp/java/java/jre/bin/keytool -certreq -keystore /root/wlp/usr/servers/controller/resources/collective/newkeystore .p12 -storepass password -storetype PKCS12 -alias serveridentity | /root/wlp/java/java/jre/bin/keytool -gencert -keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias controllerroot -rfc -validity 7300 -ext BasicConstraints:"critical=ca:true" > /root/wlp/usr/servers/controller/resources/collective/serverident ity.pem -
Import the
controllerrootsigner andserveridentity.pem files to the newkeystore.p12 keystore.Start the import process with thecontrollerrootsigner.keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newkeystore.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/resources/collective/controllerroot.pemSample command/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/collective/newkeystore .p12 -storepass password -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/controllerr oot.pemNext, perform the import process with the serveridentity.pem file.keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newkeystore.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias serveridentity -file $PATH_CONTROLLER_SERVER/resources/collective/serveridentity.pemSample command/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/collective/newkey store.p12 -storepass password -storetype PKCS12 -alias serveridentity -file /root/wlp/usr/servers/controller/resources/collective/server identity.pem - List all certificates to confirm successful processing.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/collective/newkeystore.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/collective/newkeystore .p12 -storepass password -storetype PKCS12Note: Verify that the certificate that is presented has the new expiration date. - If verification is successful, remove the serveridentity.p12 file and replace it with the newly generated newkeystore.p12 file.
Controller: Updating the key.p12 file.
- List the certificates contained in the key.p12 file using this
command.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/security/key.p12 -storepass $KEY_P12_PWD -storetype PKCS12Sample command with output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/security/key.p12 - storepass password -storetype PKCS12 Alias name: default Owner: CN=mouthing1.fyre.ibm.com, OU=controller, O=ibm, C=usSave the
DN-NAMEof the default certificate. From this sample, the DN-NAME isCN=mouthing1.fyre.ibm.com, OU=controller, O=ibm, C=us. - Use the
DN-NAMEin previous step to generate a new keystore.keytool -genkeypair -alias default -dname "$DN-NAME" -keysize 2048 -validity 7300 -keyalg rsa -keystore $PATH_CONTROLLER_SERVER/resources/security/newkey.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -ext BasicConstraints:"critical=ca:true"Sample command/root/wlp/java/java/jre/bin/keytool -genkeypair -alias default - dname "CN=mouthing1.fyre.ibm.com, OU=controller, O=ibm, C=us" - keysize 2048 -validity 7300 -keyalg rsa -keystore /root/wlp/usr/servers/controller/resources/security/newkey.p12 - storepass password -storetype PKCS12 -ext BasicConstraints:"critical=ca:true" - Generate a new default.pem certificate and extract the
.pem file.
keytool -certreq -keystore $PATH_CONTROLLER_SERVER/resources/security/newkey.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias default | /root/wlp/java/java/jre/bin/keytool -gencert -keystore $PATH_CONTROLLER_SERVER/resources/collective/newrootKeys.p12 -storepass $NEW_ROOT_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -rfc -validity 7300 -ext BasicConstraints:"critical=ca:true" >$PATH_CONTROLLER_SERVER/resources/security/default.pemSample command/root/wlp/java/java/jre/bin/keytool -certreq -keystore /root/wlp/usr/servers/controller/resources/security/newkey.p12 - storepass password -storetype PKCS12 -alias default | /root/wlp/java/java/jre/bin/keytool -gencert -keystore /root/wlp/usr/servers/controller/resources/collective/newrootKeys .p12 -storepass password -storetype PKCS12 -alias controllerroot -rfc -validity 7300 -ext BasicConstraints:"critical=ca:true" > /root/wlp/usr/servers/controller/resources/security/default.pem - Import the
controllerrootsigner and default.pem files to the newkey.p12 keystore.- Start with
controllerrootsigner and use this command.keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/security/newkey.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file $PATH_CONTROLLER_SERVER/resources/collective/controllerroot.pemSample command/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/security/newkey.p12 - storepass password -storetype PKCS12 -alias controllerroot - trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/controllerr oot.pem - Use the default.pem file in this command.
: keytool -importcert -keystore $PATH_CONTROLLER_SERVER/resources/security/newkey.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12 -alias default -file $PATH_CONTROLLER_SERVER/resources/security/default.pemSample command/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/controller/resources/security/newkey.p 12 -storepass password -storetype PKCS12 -alias default - file /root/wlp/usr/servers/controller/resources/security/default. pem
- Start with
- List all certificates to confirm that processing is as expected.
keytool -list -v -keystore $PATH_CONTROLLER_SERVER/resources/security/newkey.p12 -storepass $NEW_KEYSTORE_PWD -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/controller/resources/security/newkey.p12 - storepass password -storetype PKCS12Note: Verify that the certificate that is presented has the new expiration date. - If processing is successful, remove the key.p12 file and replace it with the newly-generated newkey.p12 file.
Controller: Wrapping up
- Before starting the controller, delete the
controllerrot-oldandmemberroot\u0002oldfrom these keystores:- collectiveTrust.p12
- trust.p12
- Run this command
/root/wlp/java/java/jre/bin/keytool -delete -alias "$CONTROLLERROOT_MEMBERROOT-old" -keystore $PATH_CONTROLLER_SERVER/resources/$COLLECTIVE_OR_SECURITY/$COLLECTIVETRUST_OR_TRUST.p12 -storepass password -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool -delete -alias "controllerrootold" -keystore /root/wlp/usr/servers/controller/resources/collective/collectiveTrust. p12 -storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool -delete -alias "memberroot-old"- keystore /root/wlp/usr/servers/controller/resources/collective/collectiveTrust. p12 -storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool -delete -alias "controllerrootold" -keystore /root/wlp/usr/servers/controller/resources/security/trust.p12 - storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool -delete -alias "memberroot-old"- keystore /root/wlp/usr/servers/controller/resources/security/trust.p12 -storepass password -storetype PKCS12 - If all processing is successful, restart the
controller.Note: You have successfully generated thecontrollerserver certificates.
Generating members certificates
- Replace the
controllerrootsigner andmemberrootsigner contained in the collectiveTrust.p12 file and the trust.p12 file.- Rename the existing alias in the collectiveTrust.p12 file and the
trust.p12 file Start with the collectiveTrust.p12 file and use these commands:
- Update the alias names of the existing
controllerrootsigner andmemberrootsigner.keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore $PATH_MEMBER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVE_TRUST_KEYSTORE_PWD -storetype PKCS12 keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore $PATH_MEMBER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVE_TRUST_KEYSTORE_PWD -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore /root/wlp/usr/servers/member/resources/collective/collective Trust.p12 -storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore /root/wlp/usr/servers/member/resources/collective/collective Trust.p12 -storepass password -storetype PKCS12 - Repeat the same commands for the trust.p12
file.
keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore /$PATH_MEMBER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12 keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore $PATH_MEMBER_SERVER/resources/security/trust.p12 -storepass $TRUST_KEYSTORE_PWD -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool --changealias -alias "memberroot" -destalias "memberroot-old" -keystore /root/wlp/usr/servers/member/resources/security/trust.p12 - storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool --changealias -alias "controllerroot" -destalias "controllerroot-old" -keystore /root/wlp/usr/servers/member/resources/security/trust.p12 - storepass password -storetype PKCS12
- Update the alias names of the existing
- Add
controllerrootsigner andmemberrootsigner to the collectiveTrust.p12 file.- Process
collectiveTrust.p12.
keytool -importcert -keystore $PATH_MEMBER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVE_TRUST_KEYSTORE_PWD -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/memberroot.pem keytool -importcert -keystore $PATH_MEMBER_SERVER/resources/collective/collectiveTrust.p12 -storepass $COLLECTIVE_TRUST_KEYSTORE_PWD -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/controllerroot.pemSample command/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/member/resources/collective/collective Trust.p12 -storepass password -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/member root.pem /root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/member/resources/collective/collective Trust.p12 -storepass password -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/contro llerroot.pem - Add
controllerrootsigner andmemberrootsigner to the trust.p12 file./root/wlp/java/java/jre/bin/keytool -importcert -keystore $PATH_MEMBER_SERVER/resources/security/trust.p12 -storepass password -storetype PKCS12 -alias memberroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/memberroot.pem/root/wlp/java/java/jre/bin/keytool -importcert -keystore $PATH_MEMBER_SERVER/resources/security/trust.p12 -storepass password -storetype PKCS12 -alias controllerroot -trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/controllerroot.pemSample commands/root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/member/resources/security/trust.p12 - storepass password -storetype PKCS12 -alias memberroot - trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/member root.pem /root/wlp/java/java/jre/bin/keytool -importcert -keystore /root/wlp/usr/servers/member/resources/security/trust.p12 - storepass password -storetype PKCS12 -alias controllerroot - trustcacerts -noprompt -file /root/wlp/usr/servers/controller/resources/collective/contro llerroot.pem
- Process
collectiveTrust.p12.
- Rename the existing alias in the collectiveTrust.p12 file and the
trust.p12 file
Member: Working with serverIdentity.p12
For example: On the controller side, make sure that you have renamed the newrootkey.p12 file to rootkey.p12 ...etc.
- List the certificates contained in the serverIdentity.p12
keystore
/root/wlp/java/java/jre/bin/keytool -list -v -keystore $PATH_MEMBER_SERVER/resources/resources/collective/serverIdentity.p12 -storepass $KEYSTORE_PWD -storetype PKCS12Sample command and output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/member/resources/collective/serverIdentity. p12 -storepass password -storetype PKCS12 Alias name: serveridentity Owner: CN=member, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=member, O=6b66c164-0133-41d8-9f78- 913622da530a, DC=com.ibm.ws.collectiveSave theDN-NAMEof theserverIdentitycertificate from the output. From the sample command, theDN-NAMEisCN=member, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=member, O=6b66c164-0133-41d8-9f78- 913622da530a, DC=com.ibm.ws.collective. - Run the collective genKey command to generate a new
serverIdentity.p12 keystore
/root/wlp/bin/collective genKey --host=$HOSTNAME --password=$ADMIN_PWD --port=$SECURE_PORT_NUMBER --user=$ADMIN_USER --keystorePassword=KEYSTORE_PWD --autoAcceptCertificates --certificateSubject="$DN-NAME" --certificateValidity=$NUMBER_OF_DAYS_CERT_WILL_BE_VALIDSample command/root/wlp/bin/collective genKey --host=mouthing1.fyre.ibm.com -- password=password --port=9443 --user=admin -- keystorePassword=password --autoAcceptCertificates -- certificateSubject="CN=member, L=%2Froot%2Fwlp%2Fusr, L=mouthing1.fyre.ibm.com, OU=member, O=6b66c164-0133-41d8-9f78- 913622da530a, DC=com.ibm.ws.collective" -- certificateValidity=3600The genKey command generates a key.p12 keystore inside the directory/root/wlp/bin/collectiveyou used to run the genKey command. For more information about the genKey command, see Generating collective controller SSL keys.Avoid Trouble: Make sure that your controller is up and running when you run the genKey command. - Rename the newly-generated key.p12 keystore to
serveridentity.p12 then replace the newly-generated keystore that is renamed to
serveridentity.p12 inside the path as shown,
$PATH_MEMBER_SERVER/resources/collective/serverIdentity.p12.
Member: Working with the key.p12 file
- List the certificates contained in your key.p12 keystore.
/root/wlp/java/java/jre/bin/keytool -list -v -keystore $PATH_MEMBER_SERVER/resources/collective/key.p12 -storepass $KEYSTORE_PWD -storetype PKCS12Sample command and output/root/wlp/java/java/jre/bin/keytool -list -v -keystore /root/wlp/usr/servers/member/resources/security/key.p12 - storepass password -storetype PKCS12 Alias name: default Owner: CN=mouthing1.fyre.ibm.com, OU=member, O=ibm, C=usSave the
DN-NAMEof the default certificate from the output. In this case, theDN-NAMEisCN=mouthing1.fyre.ibm.com, OU=member, O=ibm, C=us. - Run the collective genKey command to generate a new
serveridentity.p12 keystore.
/root/wlp/bin/collective genKey --host=$HOSTNAME --password=$ADMIN_PWD --port=$SECURE_PORT_NUMBER --user=$ADMIN_USER --keystorePassword=password --autoAcceptCertificates --certificateSubject="$DN-NAME"Sample command/root/wlp/bin/collective genKey --host=mouthing1.fyre.ibm.com -- password=password --port=9443 --user=admin -- keystorePassword=password --autoAcceptCertificates -- certificateSubject="CN=mouthing1.fyre.ibm.com, OU=member, O=ibm, C=us"The genKey command generates a key.p12 keystore inside the directory,/root/wlp/bin/collective, that you used in the previous step. For more information about the genKey command, see Generating collective controller SSL keys.Avoid Trouble: Make sure that your controller is up and running when you run the genKey command.- Replace the original key.p12 file with the newly-generated keystore.
- Place the newly-generated keystore key.p12 inside the path,
$PATH_MEMBER_SERVER/resources/collective/key.p12.
Member: Wrapping up
- Before restarting the member, make sure to delete
controllerroot-oldandmemberroot-oldfrom the following keystores:- collectiveTrust.p12
- trust.p12
- Run this keytool command to make the deletions.
/root/wlp/java/java/jre/bin/keytool -delete -alias "$CONTROLLERROOT_MEMBERROOT-old"-keystore $PATH_MEMBER_SERVER/resources/$COLLECTIVE_OR_SECURITY/$COLLECTIVETRUST_OR_TRUST.p12 -storepass password -storetype PKCS12Sample command/root/wlp/java/java/jre/bin/keytool -delete -alias "controllerrootold"-keystore /root/wlp/usr/servers/member/resources/security/collectiveTrust.p12 - storepass password -storetype PKCS12 /root/wlp/java/java/jre/bin/keytool -delete -alias "memberroot-old"- keystore /root/wlp/usr/servers/member/resources/security/collectiveTrust.p12 - storepass password -storetype PKCS12
- If all the processing is successful, restart the
member.Note: You have finished generating thememberserver certificates.
Final cleanup
- If all processing is as expected after starting the servers, You can remove any remaining .pem files and/or backups.
Results
You have finished generating the member server certificates. You have
regenerated and configured the collective security certificate and maintained communication
protection between controllers and members.